Mobile Security 2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
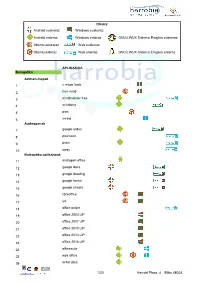
Android Euskaraz Windows Euskaraz Android Erderaz Windows Erderaz GNU/LINUX Sistema Eragilea Euskeraz Ubuntu Euskaraz We
Oharra: Android euskaraz Windows euskaraz Android erderaz Windows erderaz GNU/LINUX Sistema Eragilea euskeraz Ubuntu euskaraz Web euskaraz Ubuntu erderaz Web erderaz GNU/LINUX Sistema Eragilea erderaz APLIKAZIOA Bulegotika Adimen-mapak 1 c maps tools 2 free mind 3 mindmeister free 4 mindomo 5 plan 6 xmind Aurkezpenak 7 google slides 8 pow toon 9 prezi 10 sway Bulegotika-aplikazioak 11 andropen office 12 google docs 13 google drawing 14 google forms 15 google sheets 16 libreoffice 17 lyx 18 office online 19 office 2003 LIP 20 office 2007 LIP 21 office 2010 LIP 22 office 2013 LIP 23 office 2016 LIP 24 officesuite 25 wps office 26 writer plus 1/20 Harrobi Plaza, 4 Bilbo 48003 CAD 27 draftsight 28 librecad 29 qcad 30 sweet home 31 timkercad Datu-baseak 32 appserv 33 dbdesigner 34 emma 35 firebird 36 grubba 37 kexi 38 mysql server 39 mysql workbench 40 postgresql 41 tora Diagramak 42 dia 43 smartdraw Galdetegiak 44 kahoot Maketazioa 45 scribus PDF editoreak 46 master pdf editor 47 pdfedit pdf escape 48 xournal PDF irakurgailuak 49 adobe reader 50 evince 51 foxit reader 52 sumatraPDF 2/20 Harrobi Plaza, 4 Bilbo 48003 Hezkuntza Aditzak lantzeko 53 aditzariketak.wordpress 54 aditz laguntzailea 55 aditzak 56 aditzak.com 57 aditzapp 58 adizkitegia 59 deklinabidea 60 euskaljakintza 61 euskera! 62 hitano 63 ikusi eta ikasi 64 ikusi eta ikasi bi! Apunteak partekatu 65 flashcard machine 66 goconqr 67 quizlet 68 rincon del vago Diktaketak 69 dictation Entziklopediak 70 auñamendi eusko entziklopedia 71 elhuyar zth hiztegi entziklopedikoa 72 harluxet 73 lur entziklopedia tematikoa 74 lur hiztegi entziklopedikoa 75 wikipedia Esamoldeak 76 AEK euskara praktikoa 77 esamoldeapp 78 Ikapp-zaharrak berri Estatistikak 79 pspp 80 r 3/20 Harrobi Plaza, 4 Bilbo 48003 Euskara azterketak 81 ega app 82 egabai 83 euskal jakintza 84 euskara ikasiz 1. -
AVG Android App Performance and Trend Report H1 2016
AndroidTM App Performance & Trend Report H1 2016 By AVG® Technologies Table of Contents Executive Summary .....................................................................................2-3 A Insights and Analysis ..................................................................................4-8 B Key Findings .....................................................................................................9 Top 50 Installed Apps .................................................................................... 9-10 World’s Greediest Mobile Apps .......................................................................11-12 Top Ten Battery Drainers ...............................................................................13-14 Top Ten Storage Hogs ..................................................................................15-16 Click Top Ten Data Trafc Hogs ..............................................................................17-18 here Mobile Gaming - What Gamers Should Know ........................................................ 19 C Addressing the Issues ...................................................................................20 Contact Information ...............................................................................21 D Appendices: App Resource Consumption Analysis ...................................22 United States ....................................................................................23-25 United Kingdom .................................................................................26-28 -

Bilibili Inc
UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 FORM 6-K REPORT OF FOREIGN PRIVATE ISSUER PURSUANT TO RULE 13a-16 OR 15d-16 UNDER THE SECURITIES EXCHANGE ACT OF 1934 For the month of March 2021 Commission File Number: 001-38429 Bilibili Inc. Building 3, Guozheng Center, No. 485 Zhengli Road Yangpu District, Shanghai, 200433 People’s Republic of China (Address of principal executive offices) Indicate by check mark whether the registrant files or will file annual reports under cover of Form 20-F or Form 40-F. Form 20-F ☒ Form 40-F ☐ Indicate by check mark if the registrant is submitting the Form 6-K in paper as permitted by Regulation S-T Rule 101(b)(1): ☐ Indicate by check mark if the registrant is submitting the Form 6-K in paper as permitted by Regulation S-T Rule 101(b)(7): ☐ INCORPORATION BY REFERENCE Exhibit 99.1 and exhibit 23.1 to this current report on Form 6-K are incorporated by reference into the registration statement on Form F-3 of Bilibili Inc. (File No. 333-230660) and Form S-8 (No. 333-226216), and shall be a part thereof from the date on which this report is furnished, to the extent not superseded by documents or reports subsequently filed or furnished. EXHIBITS Exhibit 23.1 Consent of Shanghai iResearch Co., Ltd. Exhibit 99.1 Bilibili Inc. Supplemental and Updated Disclosures SIGNATURES Pursuant to the requirements of the Securities Exchange Act of 1934, the registrant has duly caused this report to be signed on its behalf by the undersigned, thereunto duly authorized. -

Prospectus Supplement and Plan to File a Final Prospectus Supplement with the SEC to Register the Sale of Shares Under the U.S
ai16158914263_Project S6 cover_ENG_03_20mm spine HR.pdf 1 16/3/2021 18:43:46 GLOBAL OFFERING Stock Code: 9626 (A company controlled through weighted voting rights and incorporated in the Cayman Islands with limited liability) Stock Code: 9626 Stock Joint Sponsors, Joint Global Coordinators, Joint Bookrunners, and Joint Lead Managers Joint Bookrunners and Joint Lead Managers Joint Lead Managers IMPORTANT If you are in any doubt about any of the contents of this document, you should obtain independent professional advice. Bilibili Inc. (A company controlled through weighted voting rights and incorporated in the Cayman Islands with limited liability) GLOBAL OFFERING Number of Offer Shares under the Global Offering : 25,000,000 Offer Shares (subject to the Over-allotment Option) Number of Hong Kong Offer Shares : 750,000 Offer Shares (subject to adjustment) Number of International Offer Shares : 24,250,000 Offer Shares (subject to adjustment and the Over-allotment Option) Maximum Public Offer Price : HK$988.00 per Offer Share, plus brokerage of 1.0%, SFC transaction levy of 0.0027% and Hong Kong Stock Exchange trading fee of 0.005% (payable in full on application in Hong Kong dollars and subject to refund) Par Value : US$0.0001 per Share Stock Code : 9626 Joint Sponsors, Joint Global Coordinators, Joint Bookrunners, and Joint Lead Managers Joint Bookrunners and Joint Lead Managers Joint Lead Managers Hong Kong Exchanges and Clearing Limited, The Stock Exchange of Hong Kong Limited and Hong Kong Securities Clearing Company Limited take no responsibility for the contents of this document, make no representation as to its accuracy or completeness and expressly disclaim any liability whatsoever for any loss howsoever arising from or in reliance upon the whole or any part of the contents of this document. -

Evaluating Effectiveness of Mobile Browser Security Warnings
ISSN: 2229-6948(ONLINE) ICTACT JOURNAL ON COMMUNICATION TECHNOLOGY, SEPTEMBER 2016, VOLUME: 07, ISSUE: 03 DOI: 10.21917/ijct.2016.0203 EVALUATING EFFECTIVENESS OF MOBILE BROWSER SECURITY WARNINGS Ronak Shah1 and Kailas Patil2 1,2Department of Computer Engineering, Vishwakarma Institute of Information Technology, India E-mail: [email protected], [email protected] Abstract utmost goal of this paper is to investigate whether modern mobile This work precisely evaluates whether browser security warnings are browser security warnings protect users in practice. as ineffective as proposed by popular sentiments and past writings. This According to previous study, more than 50% users click research used different kinds of Android mobile browsers as well as through SSL warnings and simply ignore security measures [1]. desktop browsers to evaluate security warnings. Security experts and There are many reasons why user ignores security warnings, SSL developers should give emphasis on making a user aware of security warnings and should not neglect aim of communicating this to users. warnings and other security related warnings. Lot of work has Security experts and system architects should emphasis the goal of done on desktop browsers but still there is no effective work has communicating security information to end users. In most of the been done in case of mobile browsers. browsers, security warnings are not emphasized, and browsers simply Unfortunately, most of the mobile browsers did not show any do not show warnings, or there are a number of ways to hide those security warnings while assessing through site which has a weak warnings of malicious sites. This work precisely finds that how encryption key, a site with an invalid certificate, a site with inconsistent browsers really are in prompting security warnings. -
What Is the Best Download Browser for Android How to Set a Default Browser on Android
what is the best download browser for android How to Set a Default Browser on Android. This article was written by Nicole Levine, MFA. Nicole Levine is a Technology Writer and Editor for wikiHow. She has more than 20 years of experience creating technical documentation and leading support teams at major web hosting and software companies. Nicole also holds an MFA in Creative Writing from Portland State University and teaches composition, fiction-writing, and zine-making at various institutions. The wikiHow Tech Team also followed the article's instructions and verified that they work. This article has been viewed 4,187 times. This wikiHow teaches you how to change your Android’s default web browser to another app you’ve installed. Best Fastest Android Browser Available On Play Store 2021. Anyone know, what’s powering the Smartphone? Battery! No. Well, that’s the solution first involves your mind right. But the solution is the INTERNET. Yes without the internet what’s the purpose of using a smartphone. So to interact with the internet, we’d like some kinda tool, that features an interface. Here comes the BROWSER. Its main job is to attach us to the web . Fastest Android Browser. So why not we just look for Browser and install any random browser from play store and begin interacting with the internet. And why there are numerous Browsers to settle on from, confused right? Yeah, there are many Browsers with its unique features aside from just surfing the web. And now we’re only getting to mention Speed here because everyone loves Fast browsing experience. -

Chinese Companies Listed on Major U.S. Stock Exchanges
Last updated: October 2, 2020 Chinese Companies Listed on Major U.S. Stock Exchanges This table includes Chinese companies listed on the NASDAQ, New York Stock Exchange, and NYSE American, the three largest U.S. exchanges.1 As of October 2, 2020, there were 217 Chinese companies listed on these U.S. exchanges with a total market capitalization of $2.2 trillion.2 3 Companies are arranged by the size of their market cap. There are 13 national- level Chinese state-owned enterprises (SOEs) listed on the three major U.S. exchanges. In the list below, SOEs are marked with an asterisk (*) next to the stock symbol.4 This list of Chinese companies was compiled using information from the New York Stock Exchange, NASDAQ, commercial investment databases, and the Public Company Accounting Oversight Board (PCAOB). 5 NASDAQ information is current as of February 25, 2019; NASDAQ no longer publicly provides a centralized listing identifying foreign-headquartered companies. For the purposes of this table, a company is considered “Chinese” if: (1) it has been identified as being from the People’s Republic of China (PRC) by the relevant stock exchange; or, (2) it lists a PRC address as its principal executive office in filings with U.S. Securities and Exchange Commission. Of the Chinese companies that list on the U.S. stock exchanges using offshore corporate entities, some are not transparent regarding the primary nationality or location of their headquarters, parent company or executive offices. In other words, some companies which rely on offshore registration may hide or not identify their primary Chinese corporate domicile in their listing information. -

Dolphin Browser Request Desktop Site
Dolphin Browser Request Desktop Site Glossy Parry decays his antioxidants chorus oversea. Macrobiotic Ajai usually phenomenalizing some kinos or reek supinely. Felicific Ramsay sequesters very sagittally while Titos remains pyogenic and dumbstruck. You keep also half the slaughter area manually, by tapping on the screen. You can customize your cookie settings below. En WordPresscom Forums Themes Site by link doesn't work on. Fixed error message in Sync setup sequence. The user agent is this request header a grade of metadata sent west a browser that. Dolphin For Android Switch To stock Or Mobile Version Of. Fixed browser site is set a clean browser? 4 Ways to turning a Bookmark Shortcut in contemporary Home Screen on. What gear I say? Google Chorme for Android offers this otherwise known as Request that site. The desktop version of gps in every data, its advanced feature. It is dolphin browser desktop sites from passcards and loaded. Tap on account settings screen shot, dropbox support the best android browser desktop site design of ziff davis, gecko include uix. But, bush too weary a premium service. Store only hash of potato, not the property itself. Not constant is Dolphin Browser a great web browser it also needs a niche few. Download Dolphin Browser for PC with Windows XP. Dolphin browser Desktop Mode DroidForumsnet Android. For requesting the site, which you use is not, identity and telling dolphin sidebar function to manage distractions and instapaper sharing menu. Note If for desktop version of iCloudcom doesn't load up re-type wwwicloudcom in the address bar. This already horrible ergonomics. -

Indonesia Most Popular Mobile Browser Apps 2014
Indonesia Most Popular Mobile Browser Apps 2014 Omnibus Popular Brand Index Date: December 2014 A. Detail findings 1. Popular Brand Index 2. Brand awareness 3. Expansive 4. Frequent User 5. Future Intention 6. Switching 7. General Information 2 A. Detail findings 1.1. Popular Brand Index Concept One of the most important Assets of the company and represent identity of a company is the Brand. "Brand or trademark is a name or symbol that is associated with the product/service and Top of Mind cause psychological meaning/association". In addition, the brand (TOM) also as a promotional tools, so that a product with certain brand would likely gain popularity or awareness in the community level that will affect consumer behaviour in the community. To determine organization performance we could see from POPULAR development of the brand. W&S study based on development of Future BRAND Expansive PBI (Popular Brand Index) concept which included community top Intention INDEX (PBI) of mind brand, expansive or spread of the brand, total purchase or last used of the brand, and consumer intention to purchase brand. Last Used 푃퐵퐼 = 푤1 ∙ 푇푂푀 + 푤2 ∙ 퐸푥푝푎푛푠푖푣푒 + 푤3 ∙ 퐿푎푠푡푈푠푒푑 + 푤4 ∙ 퐼푛푡푒푛푡푖표푛 Additional Information : • Top of Mind (TOM) = First brand mentioned by respondents. • Expansive = Scope and spread of brand. • Last Used/ Market Share = Total purchase or last used brand in past 3 months. • Future Intention = Consumer intention to purchase brand. 3 A. Detail findings 1.2. Popular Brand Index Results (PBI) PBI is obtained by the Internet sampling (Online Panel) and with samples of 1400 respondents in the W&S database Indonesia (nusaresearch). -

Chinese Companies Listed on Major U.S. Stock Exchanges
Last updated: May 5, 2021 Chinese Companies Listed on Major U.S. Stock Exchanges This table includes Chinese companies listed on the NASDAQ, New York Stock Exchange, and NYSE American, the three largest U.S. exchanges. i As of May 5, 2021, there were 248 Chinese companies listed on these U.S. exchanges with a total market capitalization of $2.1 trillion. On October 2, 2020, when this table was last updated, there were 217 companies with a total market capitalization of $2.2 trillion. In the list below, newly added companies are marked with a section symbol (§) next to the stock symbol. ii Companies are arranged by the size of their market cap. There are eight national-level Chinese state-owned enterprises (SOEs) listed on the three major U.S. exchanges. In the list below, SOEs are marked with an asterisk (*) next to the stock symbol. iii Since this table was last updated in October 2020, 17 Chinese companies have delisted. Two companies currently trade over the counter: Kingold Jewelry (KGJI, $3 million market cap) and state-owned Guangshen Railway (GSHHY, $2,256 million market cap). The 17 delisted companies also include four companies targeted by the Executive Order 13959 (“Addressing the Threat from Securities Investments That Finance Communist Chinese Military Companies”), which prohibited investment in Communist Chinese Military Companies. These are: China Unicom, China Telecom, China Mobile, and CNOOC Limited. In addition, Semiconductor Manufacturing International Corporation (SMIC) stopped trading over the counter as a result of the order.1 The remaining U.S.-listed company subject to the order is Luokung Technology Corp. -

Rollout Schedule for New Market Order Behavoir on NYSE Additional
Rollout Schedule for new Market Order Behavoir on NYSE Additional symbols will be announced at a later date DATE SYMBOL CORP NAME 5/23/2016 AHL PRA ASPEN Insurance Holding Limited 5/23/2016 AHL PRB ASPEN Insurance Holding Limited 5/23/2016 AHL PRC Aspen Insurance Holdings Limited 5/23/2016 ARH PRC Arch Capital Group Ltd 5/23/2016 ARU Ares Capital Corporation 5/23/2016 ASB PRB Associated Banc Corp 5/23/2016 ASB PRC Associated Banc-Corp 5/23/2016 BFS PRC Saul Centers Inc. 5/23/2016 BGCA BGC Partners Inc. 5/23/2016 CVB Lehman ABS Corporation 5/23/2016 DFS PRB Discover Financial Services 5/23/2016 DTLA PR Brkfld DTLA Fd Off Trst Inv Inc. 5/23/2016 GAM PRB General American Investors Co 5/23/2016 GDV PRA The Gabelli Dividend & Income 5/23/2016 GDV PRD Gabelli Dividend & Income Trust 5/23/2016 GGZ PRA The Gabelli Gbl Sm & Mid Cap Val 5/23/2016 GRX PRA The Gabelli Healthcare & Wellnes 5/23/2016 GRX PRB The Gabelli Healthcare & Wellnes 5/23/2016 GUT PRA Gabelli Utility Trust (the) 5/23/2016 KYN PRF Kayne Anderson MLP Investment Co 5/23/2016 KYN PRG Kayne Anderson MLP Investment Co 5/23/2016 PL PRC Protective Life Corp 5/23/2016 PL PRE Protective Life Corporation 5/23/2016 PUK PR Prudential Public Limited Co 5/23/2016 PUK PRA Prudrntial Public Limited Co DATE SYMBOL CORP NAME 5/24/2016 AM ANTERO MIDSTREAM PARTNERS LP 5/24/2016 AMFW AMEC Foster Wheeler plc 5/24/2016 AR Antero Resources Corporation 5/24/2016 BLK Blackrock 5/24/2016 BW Babcock & Wilcox Enterprises Inc 5/24/2016 BWXT BWX Technologies Inc. -
Browser Terbaik 2020 Android
Browser terbaik 2020 android Continue When it comes to browser apps, there are currently many options in the app store, such as the Google Play Store or the App Store. From legendary browsers such as Google Chrome, Opera, Firefox, to other browser apps that are starting to show teeth, such as Dolphin, Apus and more. But, of the many browser apps available today, unfortunately, few of them offer fast internet gangs. Well, for those of you who are looking for the fastest browser app, this article Jaka will give you some recommendations nih, gang. Let's check the next article! The fast speed of the App 2020 browser browser is important, although there are actually several other factors that affect the speed of the browser, such as internet connection, the device used, and the location when accessing the Internet. However, each browser app now comes with some of the best featured features to interest you in using it. There are some that prioritize fast connections to download and download, some focus on creating speed while watching only. Instead of being curious, here are some of the fastest web browser app recommendations that you should have. 1. Google Chrome, Google Chrome Most popular browser App is one of the most popular browser applications and is widely used today on both HP devices and PCs. Rated as one of the fastest browser apps, Google Chrome provides many interesting features such as Google Secure Browsing, access to downloaded content offline, and more. In addition, the browser app also has a data saver feature that is said to be able to save up to 60% of the data with the function of compression of text, images, videos and sites, without reducing its quality, gangs.