Tele V13 N34 2020 Paged.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Termination Rates at European Level January 2021
BoR (21) 71 Termination rates at European level January 2021 10 June 2021 BoR (21) 71 Table of contents 1. Executive Summary ........................................................................................................ 2 2. Fixed networks – voice interconnection ..................................................................... 6 2.1. Assumptions made for the benchmarking ................................................................ 6 2.2. FTR benchmark .......................................................................................................... 6 2.3. Short term evolution of fixed incumbents’ FTRs (from July 2020 to January 2021) ................................................................................................................................... 9 2.4. FTR regulatory model implemented and symmetry overview ............................... 12 2.5. Number of lines and market shares ........................................................................ 13 3. Mobile networks – voice interconnection ................................................................. 14 3.1. Assumptions made for the benchmarking .............................................................. 14 3.2. Average MTR per country: rates per voice minute (as of January 2021) ............ 15 3.3. Average MTR per operator ...................................................................................... 18 3.4. Average MTR: Time series of simple average and weighted average at European level ................................................................................................................. -

Orange Romania
Seller: .................................................... Orange TV The minimal Condition for granting the benefits of the Orange Family offer is to have at least 2 mobile voice subscriptions plus a Phone no: .................................................... third subscription for any Service (mobile or fixed voice, fixed or mobile internet, TV, Orange Smart Home) which are active and Installation address: Package Fax: .................................................... included in the current commercial offer. Street: ............................................................................ No.: ..... Bl.: ....... Sc.: ...... Ap.: ..... Locality: ...................................... If the Customer has additionally requested a change of tariff plan on his current numbers and thereby meets the minimal Offer code: .................................................... County/Sector: ................... Phone no.: ............................. Fax: .......................... E-mail: ........................................................ Condition for being eligible for the benefits of the Orange Family offer, these will be allocated once all the changes on the Client’s .................................................... subscriber account have been applied. 422 verification no: .................................................... Home TV Subscription: Local HD World HD Universe HD Family HD If at any time the Customer’s subscriber account is suspended, disconnected or there is change of owner, thus no longer fulfilling Local -

WELCOME to the WORLD of ETSI an Overview of the European Telecommunication Standards Institute
WELCOME TO THE WORLD OF ETSI An overview of the European Telecommunication Standards Institute © ETSI 2016. All rights reserved © ETSI 2016. All rights reserved European roots, global outreach ETSI is a world-leading standards developing organization for Information and Communication Technologies (ICT) Founded initially to serve European needs, ETSI has become highly- respected as a producer of technical standards for worldwide use © ETSI 2016. All rights reserved Products & services Technical specifications and standards with global application Support to industry and European regulation Specification & testing methodologies Interoperability testing © ETSI 2016. All rights reserved Membership Over 800 companies, big and small, from 66 countries on 5 continents Manufacturers, network operators, service and content providers, national administrations, ministries, universities, research bodies, consultancies, user organizations A powerful and dynamic mix of skills, resources and ambitions © ETSI 2016. All rights reserved Independence Independent of all other organizations and structures Respected for neutrality and trustworthiness Esteemed for our world-leading Intellectual Property Rights (IPR) Policy © ETSI 2016. All rights reserved Collaboration Strategic collaboration with numerous global and regional standards-making organizations and industry groupings Formally recognized as a European Standards Organization, with a global perspective Contributing technical standards to support regulation Defining radio frequency requirements for -

Internal and External Security Compliance at Adobe
Internal and External Staff CASE STUDY Control at Leading Telecom Operator Safeguard for Privileged Sessions The Challenge Protection of Critical Telecom Assets Like any major telecom provider, Orange Romania also operates sensitive front-end applications, service-delivery platforms and specific network devices. As usual in the telecom sector, such info-communication systems are accessed by privileged employees, consultants and suppliers, as well. Auditing the activities of this internal and external workforce was a key technical challenge for Orange. Therefore, Orange’s IT experts started to search for a device capable to audit remote access over commonly used France Telecom-Orange is one of the protocols, such as SSH, SFTP, SCP, RDP, Telnet and VNC. world’s leading telecommunications operators with annual sales of 43.5 billion euros and has 170,000 employees worldwide. Present in 32 countries, The IT experts specified the following the group has a total customer base of key expectations about the new solution: approximately 231 million customers, including 172 million mobile customers Transparency – users do not have to change their usual client and 15 million broadband internet applications to connect to remote systems (ADSL, fiber) customers worldwide. Orange is one of the main European operators for mobile and broadband Scalability – the product must adapt to increasing enterprise internet services and, under the needs both in user number and working load brand Orange Business Services, is one of the world leaders in providing telecommunication services to OCR-ing and indexing the content of graphical protocols to multinational companies. completely audit RDP-based accesses from security reasons File transfer control and Ease of configurability and use. -

2017 Registration Document
2017 Registration document Annual financial report Table of contents 1. Overview of the Group 5. Corporate, social and and of its business environmental responsibility 1.1 Overview 4 5.1 Social commitments 311 1.2 Market and strategy 7 5.2 Employee information 316 1.3 Operating activities 12 5.3 Environmental information 328 1.4 Networks and real- estate 38 5.4 Duty of care 337 1.5 Innovation at Orange 40 5.5 Report by one of the Statutory Auditors 338 1.6 Regulation of telecom activities 43 6. Shareholder Base 2. Risk factors and activity and Shareholders’ Meeting management framework 6.1 Share capital 342 2.1 Risk factors 64 6.2 Major shareholders 343 2.2 Activity and risk management framework 69 6.3 Draft resolutions to be submitted to the Combined Ordinary and Extraordinary Shareholders’ Meeting of May 4, 2018 345 3. Financial report 6.4 Report of the Board of Directors on the resolutions submitted to the Combined Ordinary and 3.1 Analysis of the Group’s financial position and earnings 78 Extraordinary Shareholders’ Meeting of May 4, 2018 350 3.2 Recent events and Outlook 131 6.5 Statutory Auditors’ report on resolutions 3.3 Consolidated financial statements 133 and related party agreements 357 3.4 Annual financial statements Orange SA 240 3.5 Dividend distribution policy 278 7. Additional information 4. Corporate Governance 7.1 Person responsible 362 7.2 Statutory Auditors 362 4.1 Composition of management and supervisory bodies 280 7.3 Statutory information 363 4.2 Functioning of the management 7.4 Factors that may have an impact in the event and supervisory bodies 290 of a public offer 365 4.3 Reference to a Code of Corporate Governance 298 7.5 Regulated agreements and related party transactions 366 4.4 Compensation and benefits paid to Directors, 7.6 Material contracts 366 Officers and Senior Management 298 8. -
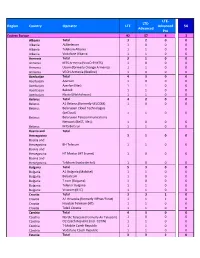
Prepared for Upload GCD Wls Networks
LTE‐ LTE‐ Region Country Operator LTE Advanced 5G Advanced Pro Eastern Europe 92 57 4 3 Albania Total 32 0 0 Albania ALBtelecom 10 0 0 Albania Telekom Albania 11 0 0 Albania Vodafone Albania 11 0 0 Armenia Total 31 0 0 Armenia MTS Armenia (VivaCell‐MTS) 10 0 0 Armenia Ucom (formerly Orange Armenia) 11 0 0 Armenia VEON Armenia (Beeline) 10 0 0 Azerbaijan Total 43 0 0 Azerbaijan Azercell 10 0 0 Azerbaijan Azerfon (Nar) 11 0 0 Azerbaijan Bakcell 11 0 0 Azerbaijan Naxtel (Nakhchivan) 11 0 0 Belarus Total 42 0 0 Belarus A1 Belarus (formerly VELCOM) 10 0 0 Belarus Belarusian Cloud Technologies (beCloud) 11 0 0 Belarus Belarusian Telecommunications Network (BeST, life:)) 10 0 0 Belarus MTS Belarus 11 0 0 Bosnia and Total Herzegovina 31 0 0 Bosnia and Herzegovina BH Telecom 11 0 0 Bosnia and Herzegovina HT Mostar (HT Eronet) 10 0 0 Bosnia and Herzegovina Telekom Srpske (m:tel) 10 0 0 Bulgaria Total 53 0 0 Bulgaria A1 Bulgaria (Mobiltel) 11 0 0 Bulgaria Bulsatcom 10 0 0 Bulgaria T.com (Bulgaria) 10 0 0 Bulgaria Telenor Bulgaria 11 0 0 Bulgaria Vivacom (BTC) 11 0 0 Croatia Total 33 1 0 Croatia A1 Hrvatska (formerly VIPnet/B.net) 11 1 0 Croatia Hrvatski Telekom (HT) 11 0 0 Croatia Tele2 Croatia 11 0 0 Czechia Total 43 0 0 Czechia Nordic Telecom (formerly Air Telecom) 10 0 0 Czechia O2 Czech Republic (incl. CETIN) 11 0 0 Czechia T‐Mobile Czech Republic 11 0 0 Czechia Vodafone Czech Republic 11 0 0 Estonia Total 33 2 0 Estonia Elisa Eesti (incl. -
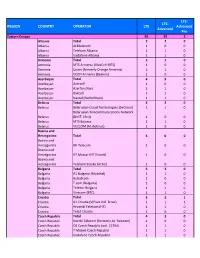
Ready for Upload GCD Wls Networks
LTE‐ LTE‐ REGION COUNTRY OPERATOR LTE Advanced Advanced Pro Eastern Europe 92 55 2 Albania Total 320 Albania ALBtelecom 100 Albania Telekom Albania 110 Albania Vodafone Albania 110 Armenia Total 310 Armenia MTS Armenia (VivaCell‐MTS) 100 Armenia Ucom (formerly Orange Armenia) 110 Armenia VEON Armenia (Beeline) 100 Azerbaijan Total 430 Azerbaijan Azercell 100 Azerbaijan Azerfon (Nar) 110 Azerbaijan Bakcell 110 Azerbaijan Naxtel (Nakhchivan) 110 Belarus Total 420 Belarus Belarusian Cloud Technologies (beCloud) 110 Belarusian Telecommunications Network Belarus (BeST, life:)) 100 Belarus MTS Belarus 110 Belarus VELCOM (A1 Belarus) 100 Bosnia and Herzegovina Total 300 Bosnia and Herzegovina BH Telecom 100 Bosnia and Herzegovina HT Mostar (HT Eronet) 100 Bosnia and Herzegovina Telekom Srpske (m:tel) 100 Bulgaria Total 530 Bulgaria A1 Bulgaria (Mobiltel) 110 Bulgaria Bulsatcom 100 Bulgaria T.com (Bulgaria) 100 Bulgaria Telenor Bulgaria 110 Bulgaria Vivacom (BTC) 110 Croatia Total 321 Croatia A1 Croatia (VIPnet incl. B.net) 111 Croatia Hrvatski Telekom (HT) 110 Croatia Tele2 Croatia 100 Czech Republic Total 430 Czech Republic Nordic Telecom (formerly Air Telecom) 100 Czech Republic O2 Czech Republic (incl. CETIN) 110 Czech Republic T‐Mobile Czech Republic 110 Czech Republic Vodafone Czech Republic 110 Estonia Total 330 Estonia Elisa Eesti (incl. Starman) 110 Estonia Tele2 Eesti 110 Telia Eesti (formerly Eesti Telekom, EMT, Estonia Elion) 110 Georgia Total 630 Georgia A‐Mobile (Abkhazia) 100 Georgia Aquafon GSM (Abkhazia) 110 Georgia MagtiCom -

APSCC Monthly E-Newsletter
APSCC Monthly e‐Newsletter February 2018 The Asia‐Pacific Satellite Communications Council (APSCC) e‐Newsletter is produced on a monthly basis as part of APSCC’s information services for members and professionals in the satellite industry. Subscribe to the APSCC monthly newsletter and be updated with the latest satellite industry news as well as APSCC activities! To renew your subscription, please visit www.apscc.or.kr/sub4_5.asp. To unsubscribe, send an email to [email protected] with a title “Unsubscribe.” News in this issue has been collected from January 1 to January 31. INSIDE APSCC APSCC 2018 Satellite Conference & Exhibition, 2‐4 October, Jakarta, Indonesia The APSCC Satellite Conference and Exhibition is Asia’s must‐attend executive conference for the satellite and space industry, where business leaders come together to gain market insight, strike partnerships and conclude business deals. The APSCC 2018 Satellite Conference & Exhibition will incorporate industry veterans and new players into the program to reach out to a broader audience. Mark your calendar for the APSCC 2018 and expand your business network while hearing from a broad range of thought provoking panels and speakers representing visionary ideas and years of business experience in the industry. Contact [email protected] for general inquiries to the APSCC 2018. APSCC Supports Community Connect Initiative APSCC supports a new initiative (click here for full Community Connect Paper) aimed at facilitating global broadband with satellite’s role highlighted. The goals of -

Tele2 Iot Roaming Reach List Release 6.3 20180611 Web Draft.Xlsx
Roaming PLMNId MCCMNC Region Country ISO country Nw name restrictions 6.3 PZ Comments SE 2G SE 3G SE 4G EE 2G EE 3G EE 4G 2G Freq 3G Freq 4G Freq AFGAR 41240 Asia Afghanistan AFG MTN 4 TRUE TRUE FALSE FALSE FALSE FALSE 900/1800 AFGAW 41201 Asia Afghanistan AFG Afghan Wireless 4 TRUE TRUE FALSE TRUE TRUE FALSE 900/1800 2100 AFGEA 41250 Asia Afghanistan AFG Etisalat 6 TRUE TRUE FALSE TRUE TRUE FALSE 900/1800 2100 AFGTD 41220 Asia Afghanistan AFG Roshan 4 TRUE TRUE FALSE TRUE TRUE FALSE 900 ALBAM 27601 Europe Albania ALB AMC / T-mobile 3 TRUE TRUE FALSE TRUE TRUE FALSE 900/1800 2100 1800/2600 ALBEM 27603 Europe Albania ALB Eagle Mobile 3 TRUE TRUE FALSE TRUE TRUE FALSE 900/1800 2100 1800 ALBVF 27602 Europe Albania ALB Vodafone Albania 2 TRUE TRUE TRUE TRUE TRUE TRUE 900/1800 DZAOT 60302 Africa Algeria DZA Djezzy 5 TRUE TRUE FALSE FALSE TRUE FALSE 900/1800 2100 DZAWT 60303 Africa Algeria DZA Wataniya Telecom Algerie 5 TRUE TRUE FALSE FALSE FALSE FALSE 900/1800 DZAA1 60301 Africa Algeria DZA ATM Mobilis 5 Added 2G and 3G for SE/EE TRUE TRUE FALSE TRUE TRUE FALSE 900/1800 ANDMA 21303 Europe Andorra AND Mobiland SC4 TRUE TRUE FALSE TRUE TRUE FALSE AIACW 365840 Central AmericaAnguilla IslandAIA Cable & Wireless 6 TRUE TRUE FALSE TRUE TRUE FALSE ATGCW 344920 Central AmericaAntigua ATG Cable & Wireless 6 TRUE TRUE FALSE TRUE TRUE FALSE ARGCM 722310 South AmericaArgentina ARG Claro 5 Added 4G for SE TRUE TRUE TRUE TRUE TRUE FALSE ARGTM 72207 South AmericaArgentina ARG Telefonica 5 TRUE TRUE FALSE TRUE TRUE FALSE 850/1900 ARGTP 72234 South AmericaArgentina -

Federal Communications Commission DA 12-1334 Before the Federal
Federal Communications Commission DA 12-1334 Before the Federal Communications Commission Washington, D.C. 20554 In the Matter of ) ) International Comparison Requirements Pursuant ) IB Docket No. 10-171 to the Broadband Data Improvement Act ) GN Docket 11-121 ) International Broadband Data Report ) THIRD REPORT Adopted: August 13, 2012 Released: August 21, 2012 By the Chief, International Bureau: I. INTRODUCTION 1. This is the Commission’s third annual International Broadband Data Report (IBDR or Report). The IBDR is required by the Broadband Data Improvement Act (BDIA) and provides comparative international information on broadband services.1 Through the presentation of this data, we have the opportunity to evaluate the United States’ rates of broadband adoption, speeds, and prices in comparison to the international community. International data can serve as useful benchmarks for progress in fixed and mobile broadband accessibility. 2. In the past year, both fixed and mobile broadband providers have made significant progress in their efforts to expand broadband networks and improve service quality. As noted in the Eighth 706 Report released today, the market is responding to the needs of Americans for increased broadband capabilities.2 In 2011, U.S. investment in wired and wireless network infrastructure rose 24%.3 Some recent trends show that providers are offering higher speeds, more data under their usage limits, and more advanced technology in both fixed and mobile broadband. For example, cable operators have increased their deployment of DOCSIS 3.0-based data networks, which are capable of providing 100 megabits per second or faster (Mbps) speeds. In the last three years, the percentage of households passed by DOCSIS 3.0 broadband infrastructure has risen from 20% to 82%.4 Advances in broadband technology and initiatives to promote greater deployment and adoption of broadband services have led to broadband- enabled innovation in other fields such as health care, education, and energy efficiency. -

Press Release
PRESS RELEASE SES 2013 FIRST HALF RESULTS SHOW GROWTH IN ALL MARKETS Luxembourg, 26 July 2013 – SES S.A. (NYSE Euronext Paris and Luxembourg Stock Exchange: SESG) reports financial results for the six months ended 30 June 2013. FINANCIAL HIGHLIGHTS • Revenue of EUR 910.5 million (+2.1%) ° Revenue at constant exchange rate (FX) grew by 7.2%, excluding German analogue impact • EBITDA of EUR 662.0 million (-0.5%) ° EBITDA at constant FX grew by 6.4%, excluding German analogue impact ° EBITDA margin of 72.7% (H1 2012: 74.6%) ° Infrastructure EBITDA margin of 83.2% (2012: 83.6%) H1 2013 growth compared to As Reported and at Excluding German analogue prior year period constant FX* impact, at constant FX Revenue +2.1% +7.2 % EBITDA -0.5% +6.4% * Revenue and EBITDA comparisons for the period are the same as reported and at constant FX due to similarity of exchange rates • Operating profit was flat at EUR 408.6 million (H1 2012: EUR 411.5 million) • Profit of the group EUR 268.0 million (H1 2012: EUR 298.7 million) • Earnings per A-share of EUR 0.67 (H1 2012: EUR 0.74) • Closing net debt / EBITDA multiple of 3.07 (H1 2012: 3.07) • Contract backlog of EUR 7.1 billion (H1 2012: EUR 6.8 billion) Romain Bausch, President and CEO, commented: “SES is growing in all markets. Although the German analogue switch-off in April 2012 limits the comparison with the prior year period, the underlying growth has accelerated. We launched, and will shortly bring into service, SES-6, an important satellite supporting our future growth. -

2013-06-11 SES Orange Romania E
Press release ORANGE ROMANIA LAUNCHES TV-SERVICE WITH GLOBECAST ON ASTRA Luxembourg/ Paris, 11 June 2013 – GlobeCast and SES (NYSE Euronext Paris and Luxembourg Stock Exchange: SESG) announced today that they are providing services to Orange Romania for the launch of a high quality satellite Direct-to-Home TV package this month. The package will use multiple transponders on ASTRA’s 31.5 degrees East orbital position and will be broadcast in the DVB-S2 and MPEG4 technical standards. GlobeCast will provide contribution, encryption and encoding for Standard Definition and High Definition channels in the package. Orange Romania will launch the new TV package to complement its existing mobile service, enabling the company to offer full multi-device communication services to its customers. Orange Romania booked this service through GlobeCast, which is providing a complete solution to bring Orange Romania’s channels to the point of uplink and prepare them for broadcast on capacity that GlobeCast has leased from SES. Jean-Francois Fallacher, Chief Executive Officer of Orange Romania, said: “Today Orange Romania is ready to provide high quality television services and to offer our Romanian customers truly attractive packages. Orange TV means the highest number of HD TV channels, the best satellite beam strength and coverage, dedicated customer care, multiscreen access, a smaller and efficient dish and other remarkable features that will allow us to offer an amazing TV experience. All these were brought to life with Orange Group’s expertise and solid partnerships we developed with world renowned companies in the TV industry.” Philippe Fort, Chief Operating Officer of GlobeCast, said: “Our offices worldwide collaborated to ensure a full technical solution for GlobeCast’s customer, Orange Romania, beginning with reception of the channels from Bucharest and ending with handoff to our partner SES for uplink to their powerful satellite.