SCREWED DRIVERS— SIGNED, SEALED, DELIVERED Common Design Flaw in Dozens of Device Drivers Allows Widespread Windows Compromise
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
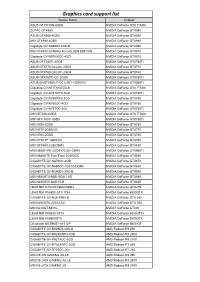
Graphics Card Support List
Graphics card support list Device Name Chipset ASUS GTXTITAN-6GD5 NVIDIA GeForce GTX TITAN ZOTAC GTX980 NVIDIA GeForce GTX980 ASUS GTX980-4GD5 NVIDIA GeForce GTX980 MSI GTX980-4GD5 NVIDIA GeForce GTX980 Gigabyte GV-N980D5-4GD-B NVIDIA GeForce GTX980 MSI GTX970 GAMING 4G GOLDEN EDITION NVIDIA GeForce GTX970 Gigabyte GV-N970IXOC-4GD NVIDIA GeForce GTX970 ASUS GTX780TI-3GD5 NVIDIA GeForce GTX780Ti ASUS GTX770-DC2OC-2GD5 NVIDIA GeForce GTX770 ASUS GTX760-DC2OC-2GD5 NVIDIA GeForce GTX760 ASUS GTX750TI-OC-2GD5 NVIDIA GeForce GTX750Ti ASUS ENGTX560-Ti-DCII/2D1-1GD5/1G NVIDIA GeForce GTX560Ti Gigabyte GV-NTITAN-6GD-B NVIDIA GeForce GTX TITAN Gigabyte GV-N78TWF3-3GD NVIDIA GeForce GTX780Ti Gigabyte GV-N780WF3-3GD NVIDIA GeForce GTX780 Gigabyte GV-N760OC-4GD NVIDIA GeForce GTX760 Gigabyte GV-N75TOC-2GI NVIDIA GeForce GTX750Ti MSI NTITAN-6GD5 NVIDIA GeForce GTX TITAN MSI GTX 780Ti 3GD5 NVIDIA GeForce GTX780Ti MSI N780-3GD5 NVIDIA GeForce GTX780 MSI N770-2GD5/OC NVIDIA GeForce GTX770 MSI N760-2GD5 NVIDIA GeForce GTX760 MSI N750 TF 1GD5/OC NVIDIA GeForce GTX750 MSI GTX680-2GB/DDR5 NVIDIA GeForce GTX680 MSI N660Ti-PE-2GD5-OC/2G-DDR5 NVIDIA GeForce GTX660Ti MSI N680GTX Twin Frozr 2GD5/OC NVIDIA GeForce GTX680 GIGABYTE GV-N670OC-2GD NVIDIA GeForce GTX670 GIGABYTE GV-N650OC-1GI/1G-DDR5 NVIDIA GeForce GTX650 GIGABYTE GV-N590D5-3GD-B NVIDIA GeForce GTX590 MSI N580GTX-M2D15D5/1.5G NVIDIA GeForce GTX580 MSI N465GTX-M2D1G-B NVIDIA GeForce GTX465 LEADTEK GTX275/896M-DDR3 NVIDIA GeForce GTX275 LEADTEK PX8800 GTX TDH NVIDIA GeForce 8800GTX GIGABYTE GV-N26-896H-B -

Manual, Chapter 1 and 2 Contains the Introduction of the Motherboard and Step-By-Step Installation Guides
Version 1.0 Published June 2018 Copyright©2018 ASRock INC. All rights reserved. Copyright Notice: No part of this documentation may be reproduced, transcribed, transmitted, or translated in any language, in any form or by any means, except duplication of documentation by the purchaser for backup purpose, without written consent of ASRock Inc. Products and corporate names appearing in this documentation may or may not be registered trademarks or copyrights of their respective companies, and are used only for identification or explanation and to the owners’ benefit, without intent to infringe. Disclaimer: Specifications and information contained in this documentation are furnished for informational use only and subject to change without notice, and should not be constructed as a commitment by ASRock. ASRock assumes no responsibility for any errors or omissions that may appear in this documentation. With respect to the contents of this documentation, ASRock does not provide warranty of any kind, either expressed or implied, including but not limited to the implied warranties or conditions of merchantability or fitness for a particular purpose. In no event shall ASRock, its directors, officers, employees, or agents be liable for any indirect, special, incidental, or consequential damages (including damages for loss of profits, loss of business, loss of data, interruption of business and the like), even if ASRock has been advised of the possibility of such damages arising from any defect or error in the documentation or product. This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. -

View Annual Report
2007 ANNUAL REPORT TSE:2303 NYSE:UMC Corporate Information Spokesperson Fab 8C ADR Depositary and Registrar Chitung Liu No.6 Li-Hsin 3rd Rd., Hsinchu Science Citibank, N.A. Chief Financial Officer Park, Hsinchu, Taiwan 30078, R.O.C. Depositary Receipt Services 886 (2) 2700 6999 886 (3) 578 2258 14F, 388 Greenwich Street, [email protected] New York, NY 10013, U.S.A. Fab 8D 1 (877) 248 4237 (Toll-free) Deputy Spokesperson(s) No.8 Li-Hsin 3rd Rd., Hsinchu Science Stockholder Service Representatives are Sandy Yen Park, Hsinchu, Taiwan 30078, R.O.C. available Monday through Friday, The Chairman and CEO Office 886 (3) 578 2258 8:30a.m. to 6:00p.m., Eastern Time. Senior Manager http://wwss.citissb.com/adr/www/ 886 (2) 2700 6999 Fab 8E [email protected] [email protected] No.17 Li-Hsin Rd., Hsinchu Science Park, Hsinchu, Taiwan 30078, R.O.C. ADR Exchange Marketplace Bowen Huang 886 (3) 578 2258 New York Stock Exchange, Inc. Finance Division 11 Wall Street Senior Manager Fab 8F New York, NY 10005, U.S.A. 886 (2) 2700 6999 No.3 Li-Hsin 6th Rd., Hsinchu Science 1 (212) 656 3000 [email protected] Park, Hsinchu, Taiwan 30078, R.O.C. www.nyse.com 886 (3) 578 2258 Ticker/Search Code: UMC Headquarters No.3 Li-Hsin 2nd Rd., Hsinchu Science Fab 8S Exchangeable Bond Exchange Park, Hsinchu, Taiwan 30078, R.O.C. No.16 Creation 1st Rd., Hsinchu Science Marketplace 886 (3) 578 2258 Park, Hsinchu, Taiwan 30077, R.O.C. -

K10n78hsli-Wifi / K10n78hsli-1394
K10N78hSLI-WiFi / K10N78hSLI-1394 User Manual Version 1.0 Published April 2008 Copyright©2008 ASRock INC. All rights reserved. 1 Copyright Notice: No part of this manual may be reproduced, transcribed, transmitted, or translated in any language, in any form or by any means, except duplication of documentation by the purchaser for backup purpose, without written consent of ASRock Inc. Products and corporate names appearing in this manual may or may not be regis- tered trademarks or copyrights of their respective companies, and are used only for identification or explanation and to the owners’ benefit, without intent to infringe. Disclaimer: Specifications and information contained in this manual are furnished for informa- tional use only and subject to change without notice, and should not be constructed as a commitment by ASRock. ASRock assumes no responsibility for any errors or omissions that may appear in this manual. With respect to the contents of this manual, ASRock does not provide warranty of any kind, either expressed or implied, including but not limited to the implied warran- ties or conditions of merchantability or fitness for a particular purpose. In no event shall ASRock, its directors, officers, employees, or agents be liable for any indirect, special, incidental, or consequential damages (including damages for loss of profits, loss of business, loss of data, interruption of business and the like), even if ASRock has been advised of the possibility of such damages arising from any defect or error in the manual or product. This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. -

K10N78-1394.Pdf
K10N78-1394 / K10N78 User Manual Version 1.1 Published August 2008 Copyright©2008 ASRock INC. All rights reserved. 1 Copyright Notice: No part of this manual may be reproduced, transcribed, transmitted, or translated in any language, in any form or by any means, except duplication of documentation by the purchaser for backup purpose, without written consent of ASRock Inc. Products and corporate names appearing in this manual may or may not be regis- tered trademarks or copyrights of their respective companies, and are used only for identification or explanation and to the owners’ benefit, without intent to infringe. Disclaimer: Specifications and information contained in this manual are furnished for informa- tional use only and subject to change without notice, and should not be constructed as a commitment by ASRock. ASRock assumes no responsibility for any errors or omissions that may appear in this manual. With respect to the contents of this manual, ASRock does not provide warranty of any kind, either expressed or implied, including but not limited to the implied warran- ties or conditions of merchantability or fitness for a particular purpose. In no event shall ASRock, its directors, officers, employees, or agents be liable for any indirect, special, incidental, or consequential damages (including damages for loss of profits, loss of business, loss of data, interruption of business and the like), even if ASRock has been advised of the possibility of such damages arising from any defect or error in the manual or product. This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. -

R.C.S. Luxembourg B-104.413
R.C.S. Luxembourg B-104.413 Audited Annual Report as at 31 January 2018 No subscription can be accepted on the basis of the financial reports. Subscriptions are only valid if they are made on the basis of the latest published prospectus accompanied by the latest annual report and the most recent semi-annual report, if published thereafter. DB Platinum Table of contents Page Management and Administration 3 Directors’ Report 5 Independent Auditor’s Report 14 Statement of Net Assets 17 Key Figures as at 31 January 2018 21 Statement of Operations and Changes in Net Assets 26 Statistics 30 Statement of Investments DB Platinum Commodity Euro 37 DB Platinum CROCI Branchen Stars 38 DB Platinum Commodity USD 40 DB Platinum CROCI World 41 DB Platinum PWM CROCI Multi Fund 45 DB Platinum CROCI Sectors Fund 46 DB Platinum CROCI Global Dividends 48 DB Platinum CROCI US Dividends 51 DB Platinum Chilton Diversified 53 DB Platinum Ivory Optimal 55 DB Platinum CROCI World ESG 57 DB Platinum Chilton European Equities 60 DB Platinum MCP Terra Grove Pan Asia 62 DB Platinum MidOcean Absolute Return Credit 63 Notes to the Financial Statements 68 Information to Shareholders (unaudited) 164 DB Platinum Management and Administration Registered Office DB Platinum 11-13, boulevard de la Foire L-1528 Luxembourg Grand-Duchy of Luxembourg Board of Directors - Alexander McKenna (chairman of the Board of Directors), Head of Product Platform Engineering, Deutsche Asset Management (UK) Limited, Winchester House, 1 Great Winchester Street, London EC2N 2DB, United Kingdom. - Freddy Brausch, Independent director, Linklaters LLP, 35, avenue John F. -

Z590 Pro4.Pdf
Version 1.0 Published February 2021 Copyright©2021 ASRock INC. All rights reserved. Copyright Notice: No part of this documentation may be reproduced, transcribed, transmitted, or translated in any language, in any form or by any means, except duplication of documentation by the purchaser for backup purpose, without written consent of ASRock Inc. Products and corporate names appearing in this documentation may or may not be registered trademarks or copyrights of their respective companies, and are used only for identification or explanation and to the owners’ benefit, without intent to infringe. Disclaimer: Specifications and information contained in this documentation are furnished for informational use only and subject to change without notice, and should not be constructed as a commitment by ASRock. ASRock assumes no responsibility for any errors or omissions that may appear in this documentation. With respect to the contents of this documentation, ASRock does not provide warranty of any kind, either expressed or implied, including but not limited to the implied warranties or conditions of merchantability or fitness for a particular purpose. In no event shall ASRock, its directors, officers, employees, or agents be liable for any indirect, special, incidental, or consequential damages (including damages for loss of profits, loss of business, loss of data, interruption of business and the like), even if ASRock has been advised of the possibility of such damages arising from any defect or error in the documentation or product. This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. -

COST to COST CORRSAIR 2590 106-107, Meghdoot Building, Nehru Place TRANSCEND I-3---4290 2GB--700 4GB--1142
DUAL CORE DDR3 3.0GHZ-- COST TO COST CORRSAIR 2590 106-107, Meghdoot Building, Nehru Place TRANSCEND I-3---4290 2GB--700 4GB--1142 Rate List Date: 8/27/2011 FREE USB MOUSE (MOSERBAER) WITH ANY LED/LCD MONITOR 35 GIGABYTE / ASUS G41 2325 71 DDR2-2GB simmtronics (5 YEAR) 928 110 NVIDEA 9500GS/512/HDMI/DVI/V 2900 36 INTEL DX 58 OG SATA/USB 3 10500 72 DDR 3 KINGSTON 2GB 738 111 NVIDEA 9600/DDR3/512 HYPER 2750 CPU INTEL 37 GIGABYTE H55M-D2H 3900 73 DDR1 512MB HYNIX LAPTOP 714 112 XFX/ZOTAC 210 NVIDIA 1GB DD 1900 1 INTEL DUAL CORE 3.06 ASK 38 GIGABYTE P55-US3L 6350 74 DDR1 1GB HYNIX LAPTOP 1323 113 ATI 6870 1GB DDR5 SAPPHIRE 9800 2 INTEL (I-5 /2310) ASK 39 INTEL G43RK (OEM) 2750 75 DDR2 2GB TRANSCEND/KINGST 1100 114 ATI 5670 1GB DDR3 SAPPHIRE 3333 3 INTEL (I-5 /2500K) 9740 40 INTEL DG41 WV (BOX) 2675 76 DDR1 1GB HYNIX 976 115 5670 1GB DDR3 SAPPHIRE 3333 4 INTEL (I-5 /2500) 9190 41 INTEL H55TC (OEM) 3950 77 DDR2 1GBTRANS/KING LAPTOP 714 116 5450 1GB DDR3 SAPPHIRE 1900 5 INTEL (I-7 /2600) 13400 42 GIGABYTE X58A-USB3 (1366) 10700 78 DDR2 2GB KINGSTON LAPTOP 1200 117 NVIDEA 9300GE /512MB 1800 6 INTEL I-7/960 4 CORE 8 MB CAS 13700 43 GIGABYTE /ASUS H55M 3600 79 DDR 3 4GB TRANSCEND (1333) 1142 118 NVIDEA 9600GS 768MB (192BIT 3000 7 INTEL I-3 540/3.06GHZ 4290 44 INTEL H55TC BOX 4050 80 DDR2 2GB TRANSCEND LAPTO 1100 119 AGP ATI 9200 1200 8 INTEL CORE 2 QUAD 2.66 GHZ ASK 45 ASUS G41 COMBO 2400 81 DDR3 GSKILL 4GB 1333 1200 120 PCI-E ATI X200SE 1250 9 INTEL CORE 2 DUO 2.93 GHZ 4990 82 DDR1 512MB HYNIX 428 10 INTEL (I-5 /2400) 8240 83 4GB TWINMOS DDR3 1333 -

Emerging Markets Small Cap Portfolio-Institutional Class As of July 31, 2021 (Updated Monthly) Source: State Street Holdings Are Subject to Change
Emerging Markets Small Cap Portfolio-Institutional Class As of July 31, 2021 (Updated Monthly) Source: State Street Holdings are subject to change. The information below represents the portfolio's holdings (excluding cash and cash equivalents) as of the date indicated, and may not be representative of the current or future investments of the portfolio. The information below should not be relied upon by the reader as research or investment advice regarding any security. This listing of portfolio holdings is for informational purposes only and should not be deemed a recommendation to buy the securities. The holdings information below does not constitute an offer to sell or a solicitation of an offer to buy any security. The holdings information has not been audited. By viewing this listing of portfolio holdings, you are agreeing to not redistribute the information and to not misuse this information to the detriment of portfolio shareholders. Misuse of this information includes, but is not limited to, (i) purchasing or selling any securities listed in the portfolio holdings solely in reliance upon this information; (ii) trading against any of the portfolios or (iii) knowingly engaging in any trading practices that are damaging to Dimensional or one of the portfolios. Investors should consider the portfolio's investment objectives, risks, and charges and expenses, which are contained in the Prospectus. Investors should read it carefully before investing. This fund operates as a feeder fund in a master-feeder structure and the holdings listed below are the investment holdings of the corresponding master fund. Your use of this website signifies that you agree to follow and be bound by the terms and conditions of use in the Legal Notices. -

Sis Accelerated Graphic Port Driver
Sis accelerated graphic port driver Click on the following links for the driver package readme info: /AGP/ This package supports the following driver models:SiS Accelerated Graphics. This package supports the following driver models:SiS Accelerated Graphics Port. Download the latest drivers for your SiS Accelerated Graphics Port to keep your Computer up-to-date. Update your computer's drivers using DriverMax, the free driver update tool - Chipset - Silicon Integrated Systems - SiS Accelerated Graphics Port Computer. SiS Accelerated Graphics Port Free Driver Download for Windows XP - World's most popular driver download site. SiS Accelerated Graphics Port Free Driver Download for Windows , XP, , NT4, ME, 98SE, 98, 95 - uvga3_zip. World's most popular driver. SiS Accelerated Graphics Port Free Driver Download for Windows , XP, , NT4, ME, 98SE, 98, 95 - World's most popular driver download. This page contains the driver installation download for SiS Accelerated Graphics Port in supported models (Positivo Mobile) that are running a supported. Windows device driver information for SiS Accelerated Graphics Port. The SiS Accelerated Graphics Port, otherwise called the Advanced Graphics Port, is a. Sis Accelerated Graphics Port Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Uploaded on 4/15/, downloaded times, receiving a. SiS Accelerated Graphics Port driver was found and is available for download at Download driver for SiS Mirage Graphics, SiS Accelerated Graphics Port, SIS Processor AGP Controller, XPx File Information Released By: ANOTE. SiS Accelerated Graphics Port - Driver Download. Updating your drivers with Driver Alert can help your computer in a number of ways. From adding new. -

B450 Steel Legend.Pdf
Version 1.1 Published November 2020 Copyright©2020 ASRock INC. All rights reserved. Copyright Notice: No part of this documentation may be reproduced, transcribed, transmitted, or translated in any language, in any form or by any means, except duplication of documentation by the purchaser for backup purpose, without written consent of ASRock Inc. Products and corporate names appearing in this documentation may or may not be registered trademarks or copyrights of their respective companies, and are used only for identification or explanation and to the owners’ benefit, without intent to infringe. Disclaimer: Specifications and information contained in this documentation are furnished for informational use only and subject to change without notice, and should not be constructed as a commitment by ASRock. ASRock assumes no responsibility for any errors or omissions that may appear in this documentation. With respect to the contents of this documentation, ASRock does not provide warranty of any kind, either expressed or implied, including but not limited to the implied warranties or conditions of merchantability or fitness for a particular purpose. In no event shall ASRock, its directors, officers, employees, or agents be liable for any indirect, special, incidental, or consequential damages (including damages for loss of profits, loss of business, loss of data, interruption of business and the like), even if ASRock has been advised of the possibility of such damages arising from any defect or error in the documentation or product. This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. -
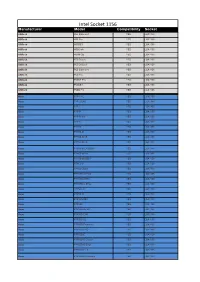
Intel Socket 1156 Manufacturer Model Compatibility Socket
Intel Socket 1156 Manufacturer Model Compatibility Socket ASRock H55 Extreme3 YES LGA1156 ASRock H55 Pro YES LGA1156 ASRock H55DE3 YES LGA1156 ASRock H55iCafe YES LGA1156 ASRock H55M-GE YES LGA1156 ASRock P55 Deluxe YES LGA1156 ASRock P55 Deluxe3 YES LGA1156 ASRock P55 Extreme4 YES LGA1156 ASRock P55 Pro YES LGA1156 ASRock P55DE Pro YES LGA1156 ASRock P55DE3 YES LGA1156 ASRock P55M Pro YES LGA1156 Asus P7F-C/4L YES LGA1156 Asus P7F-C/SAS YES LGA1156 Asus P7F-E YES LGA1156 Asus P7F-M YES LGA1156 Asus P7F-M WS YES LGA1156 Asus P7F-X YES LGA1156 Asus P7H55 YES LGA1156 Asus P7H55-M YES LGA1156 Asus P7H55-M LE YES LGA1156 Asus P7H55-M LX YES LGA1156 Asus P7H55-M LX/USB3 YES LGA1156 Asus P7H55-M Pro YES LGA1156 Asus P7H55-M/USB3 YES LGA1156 Asus P7H55-V YES LGA1156 Asus P7H55/USB3 YES LGA1156 Asus P7H55D-M EVO YES LGA1156 Asus P7H55D-M Pro YES LGA1156 Asus P7H57D-V EVO YES LGA1156 Asus P7P55 LX YES LGA1156 Asus P7P55-M YES LGA1156 Asus P7P55/USB3 YES LGA1156 Asus P7P55D YES LGA1156 Asus P7P55D Deluxe YES LGA1156 Asus P7P55D EVO YES LGA1156 Asus P7P55D LE YES LGA1156 Asus P7P55D Premium YES LGA1156 Asus P7P55D PRO YES LGA1156 Asus P7P55D-E YES LGA1156 Asus P7P55D-E Deluxe YES LGA1156 Asus P7P55D-E EVO YES LGA1156 Asus P7P55D-E LX YES LGA1156 Asus P7P55D-E Premium YES LGA1156 Asus P7P55D-E Pro YES LGA1156 Asus P7Q57-M DO YES LGA1156 Asus SABERTOOTH 55i YES LGA1156 Biostar H55A+ YES LGA1156 Biostar T5XE CFX-SLI YES LGA1156 Biostar TH55 HD YES LGA1156 Biostar TH55 XE YES LGA1156 Biostar TH55B HD YES LGA1156 Biostar TP55 YES LGA1156 Biostar TPower