NEURAL COMPUTING 17 Sailee Chitre – T.Y.B.Sc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Firefox 1.1 for Nokia N900 Reviewer's Guide
Firefox 1.1 for Nokia N900 Reviewer’s Guide Firefox 1.1 for Nokia N900 Reviewer’s Guide Table of Contents What’s new in Firefox 1.1 for the Nokia N900 1 1. About Mozilla 2 2. Firefox for Mobile 2 3. Mozilla’s Mobile Vision 3 4. Getting Started 4 5. New & Improved 6 6. Do More With Your Web 7 7. Firefox Mobile and Desktop Browsing 9 8. A Summary of Firefox Features 11 9. Under the Hood 12 Firefox 1.1 for Nokia N900 Reviewer’s Guide What’s new in Firefox 1.1 for the Nokia N900 Highlights: tFirefox lets you browse in landscape and portrait mode tVolume rocker lets you zoom in and out tPersonalized Start page helps you pick up where you left off tAdd-ons auto-update and you can view the full add-on gallery tFill out forms more easily with autocomplete improvements tSmart Tapping lets you tap on links, widgets and other Web content with accuracy tContext Menu lets you Open in New Tab and Save Image by long tapping and holding a link tSave to PDF in the Site Menu lets you capture important content, like a receipt or boarding pass, to view offline or access quickly tForget Password in the Site Menu tells a website you no longer trust to forget your private data tAdd Search Engine in the Site Menu lets you quickly add a new search engine to your Awesome Screen tAnd many more Firefox features on page 11 Page 1 Firefox for Nokia N900 Reviewer’s Guide Firefox 1.1 for Nokia N900 Reviewer’s Guide 1. -

The Technology That Brings Together All Things Mobile
NFC – The Technology That Brings Together All Things Mobile Philippe Benitez Wednesday, June 4th, 2014 NFC enables fast, secure, mobile contactless services… Card Emulation Mode Reader Mode P2P Mode … for both payment and non-payment services Hospitality – Hotel room keys Mass Transit – passes and limited use tickets Education – Student badge Airlines – Frequent flyer card and boarding passes Enterprise & Government– Employee badge Automotive – car sharing / car rental / fleet management Residential - Access Payment – secure mobile payments Events – Access to stadiums and large venues Loyalty and rewards – enhanced consumer experience 3 h h 1996 2001 2003 2005 2007 2014 2014 2007 2005 2003 2001 1996 previous experiences experiences previous We are benefiting from from benefiting are We Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed 256 handset models now in market worldwide Gionee Elife E7 LG G Pro 2 Nokia Lumia 1020 Samsung Galaxy Note Sony Xperia P Acer E320 Liquid Express Google Nexus 10 LG G2 Nokia Lumia 1520 Samsung Galaxy Note 3 Sony Xperia S Acer Liquid Glow Google Nexus 5 LG Mach Nokia Lumia 2520 Samsung Galaxy Note II Sony Xperia Sola Adlink IMX-2000 Google Nexus 7 (2013) LG Optimus 3D Max Nokia Lumia 610 NFC Samsung -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 20 | July through December, 2015 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2016 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors Charlie Anthe Dana Kaufman Anthony Penta Cloud and Enterprise Security Azure Active Directory Team Safety Platform Nir Ben Zvi Nasos Kladakis Ina Ragragio Enterprise and Cloud Group Azure Active Directory Team Windows and Devices Group Patti Chrzan Daniel Kondratyuk Tim Rains Microsoft Digital Crimes Unit Azure Active Directory Team Commercial Communications Bulent Egilmez Andrea Lelli Paul Rebriy Office 365 - Information Windows Defender Labs Bing Protection Geoff McDonald Stefan Sellmer Elia Florio Windows Defender Labs Windows Defender Labs Windows Defender Labs Michael McLaughlin Mark Simos Chad Foster Identity Services Enterprise Cybersecurity Bing Group Nam Ng Roger Grimes Enterprise Cybersecurity Vikram Thakur Microsoft IT Group Windows Defender Labs Paul Henry Niall O'Sullivan Alex Weinert Wadeware LLC Microsoft Digital Crimes Unit Azure Active Directory Team Beth Jester Daryl Pecelj Terry Zink Windows Defender Microsoft IT Information -
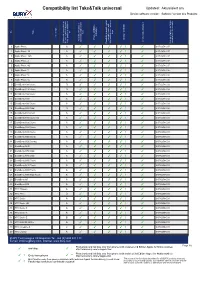
BURY Compatibility List Generator
Compatibility list Take&Talk universal Updated: Aktualisiert am: Device software version: Software Version des Produkts: on No key keys Type activation Set of tips Phone s REDIAL Charger available / private mode with Activation Bluetooth Article code (Charger) connection with device Bluetooth connection to used to test/ Comments after ignition is switched the last connected phone Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 2 Apple iPhone 3G A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 3 Apple iPhone 3GS A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 4 Apple iPhone 4 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 5 Apple iPhone 4S A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 6 Apple iPhone 5 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7 Apple iPhone 5c A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 8 Apple iPhone 5s A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 9 BlackBerry 8300 Curve D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 10 BlackBerry 8310 Curve D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 11 BlackBerry 8520 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 12 BlackBerry 8800 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 13 BlackBerry 8900 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 14 BlackBerry 9000 Bold D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 15 BlackBerry 9105 Pearl A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 16 BlackBerry 9300 Curve 3G A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 17 BlackBerry 9320 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 18 BlackBerry 9360 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 19 BlackBerry 9380 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 20 BlackBerry 9500 Storm A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 21 BlackBerry 9520 Storm2 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 22 BlackBerry 9630 A ✓ ✓ -

Files: Cpan/Test-Harness/* Copyright: Copyright (C) 2007-2011
Files: cpan/Test-Harness/* Copyright: Copyright (c) 2007-2011, Andy Armstrong <[email protected]>. All rights reserved. License: GPL-1+ or Artistic Comment: This module is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Harness/lib/TAP/Parser.pm Copyright: Copyright 2006-2008 Curtis "Ovid" Poe, all rights reserved. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Harness/lib/TAP/Parser/YAMLish/Reader.pm Copyright: Copyright 2007-2011 Andy Armstrong. Portions copyright 2006-2008 Adam Kennedy. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Simple/* Copyright: Copyright 2001-2008 by Michael G Schwern <[email protected]>. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Simple/lib/Test/Builder.pm Copyright: Copyright 2002-2008 by chromatic <[email protected]> and Michael G Schwern E<[email protected]>. License: GPL-1+ or Artistic 801 Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Simple/lib/Test/Builder/Tester/Color.pm Copyright: Copyright Mark Fowler <[email protected]> 2002. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. -

Android-X86 Project Marshmallow Porting
Android-x86 Project Marshmallow Porting https://drive.google.com/open?id=1mND8K-AXbMMl8- wOTe75NOpM0xOcJbVy8UorryHOWsY 黃志偉 [email protected] 2015/11/28 http://www.android-x86.org Agenda ●Introduction: what, why, how? ●History and milestones ●Current status ●Porting procedure ●Develop android-x86 ●Future plans android-x86.org About Me ●A free software and open source amateur and promoter from Taiwan ■ CLDP / CLE ■ GNU Gatekeeper ■ Android-x86 Open Source Project ●https://zh.wikipedia.org/wiki/Cwhuang android-x86.org Introduction ●What's Android-x86? ●Why needs Android-x86? ●How can we do it? android-x86.org What's Android-x86 ? ●An open source project aimed to provide a complete solution for Android on x86 devices ●Android BSP (Board support Package) for x86 platform ●At first we use ASUS Eee PC and Virtualbox as the reference platform. ●Some vendors donate tablets, like Tegatech Tegav2, 4tiitoo AG WeTab and AMD android-x86.org Why needs Android-x86? ●Android is an open source operating-system originally designed for arm platform ●It's open source, we can port it to other platforms, like mips, PowerPC and x86 ●AOSP officially supports x86 now ● AOSP doesn’t have specific hardware components ● Still a lot of work to do to make it run on a real device android-x86.org But what are the benefits? ●Understanding Android porting process ●The x86 platform is widely available ●A test platform much faster than SDK emulator ●Android-x86 on vbox / vmware ●Suitable for tablet apps android-x86.org Android architecture android-x86.org How to do that? ●Toolchains – already in AOSP, but old.. -

Investigating Choices of Appropriate Devices for One-To-One Computing Initiatives in Schools Worldwide
International Journal of Information and Education Technology, Vol. 6, No. 10, October 2016 Investigating Choices of Appropriate Devices for One-to-One Computing Initiatives in Schools Worldwide M. Sirajul Islam and Annika Andersson schools should be governed by “creating an environment in Abstract—The use of technology in schools is rapidly which the child will become highly involved in experience of increasing – today most notably through the one-to-one (1:1) a kind to provide rich soil for the growth in intuitions and programs that are being implemented all around the world. concepts for dealing with thinking, learning, playing, and so Considering how new technologies are emerging fast and obsoleting others in schools, there is a need to continuously on” [5]. In this direction, one of the first practical initiatives monitor and understand the features of various devices in terms on implementing constructionist learning for children with of embedded technology and interaction with users. This paper computers was the development of programming language therefore presents the nature of computing devices used in 1:1 called „Logo‟ in 1967. Following such initiatives, Alan C. computing programs in schools around the world, including Kay, who was closely associated with Papert for promoting investigating the benefits and drawbacks, by means of a and implementing computer based educational constructivism, systematic literature review and a survey conducted in some schools in Sweden. The paper also presents findings based on developed a laptop computer for children in 1970 based on how the various uses of technology affect cooperation practices the sketches of the KiddiComp called „Daynabook‟ as well as personal exploration. -

Recenze: Ubuntu 10.04 Lucid Lynx
2 PodPodíílele j jíí se se 3 Co se děě j je ve svěěttěě L Liinuxu a open source 7 Freedroiid Classiic – klasiika z C64 9 Google Chrome 5 beta – j jako kdyžž st střřelelíí (bramboru) 12 Mobiilnlníí noviinkynky 14 Reportáážž: Openmobiilliity 2010 16 Open source a liinuxovéé prohlíížžeečče v dubnu 2010 18 Zpravoda j j TeXiiststůů pod drobnohledem 21 KDE 4: Vrchol desktopovéé evoluce? 27 Recenze mobiilnlníího telefonu Nokiia N900 31 Recenze ThiinkPad Edge 13 35 Recenze: Ubuntu 10.04 Luciid Lynx openMagaziinn j jee j jedediineneččnnýý elektroniickckýý č časopiis, kterýý v váám kažžddýý m měěssííc ppc řřiinnááššíí to ne j jleplepššíí,, 41 Softwarovéé l liicence vhodnéé pro použžiittíí ve ve š školníím prostřřededíí co vyššlo na portáálech zaměěřřenenýých na volněě š šiiřřiitelntelnýý software. Můžůžete se těěššiit na náávody, 43 Amarok1.4 j je zpzpe ěět ––t j jmenu j je se Clementiinene recenze, noviinky, tiipy aapy trtriiky, kteréé s sii m můžůžete přřeečíčíst na svéém netbooku nebo ji jinnéémm 46 MMůů j j software v Mandriiva LLva iinuxu 5 – Jiiřříí Doskoččiill ppřřenosnéém zařříízenzeníí. Douf ááme,me, ž že vve áás obsah zau j jme a taktakéé v váás prosííme, abyste PDF 50 Noviinky ze svěěta apliikackacíí Moziillalla soubor š šíířřiillii, kam to j jenen j jde. Kopííruru j jte nnte áás, posíílele j jte, sdíílele j jte. A napnapiiššte nnte áám,m, j jak se váámm 52 Rozhovor s Adamem Rambouskem, koordiinnáátorem č českeskééhoho magazíín lln íí b bíí. Neodmííttááme anii dary č čii momožžnou obchodníí spoluprááccii. D. Děěkuku j jeme za přříízezeňň.. ppřřekladatelskéého tho týýmumu 54 Adam Rambousek: Č Českeskýý lokaliizazaččnníí t týým nutněě pot potřřebuebu j jee redakce openMagaziinunu spolupracovnííkyky [email protected] 56 SprSpriievodca dáátamtamii – usporiiadaada j jte sste ii v tabuľ ľ kkáách ddch áátata 60 StStřřednedníí š škola obchodu, ř řemesel a služžeb použžíívváá kanceláářřskskýý bal balíík OpenOff iice.org 61 Společčnost ViiddíímeVáás, s. -

ASUS Eee PC 1015BX - Unprecedented Performance for Excellent Multimedia Enjoyment
Eee PC 1015BX ASUS Eee PC 1015BX - Unprecedented performance for excellent multimedia enjoyment • Thin and light AMD Brazos platform with Accelerated Processing Unit (APU) combines high performance with low power consumption • AMD Radeon™ HD 6250 integrated graphics, DirectX® 11 and Unified Video Decoder 3 for high definition visuals • Enjoy Full HD 1080p on a HDTV or big display via a HDMI connection • USB Charger+ allows USB mobile devices to be charged anytime without booting up Superior performance with the AMD dual core USB Charger+* for instant charging anytime processor Need to charge your mobile phone, but aren’t using the netbook at the moment? The latest AMD Brazos C50* processor provides users an unprecedented No problem. Charge your mobile device through the USB port without the need experience of the all new Accelerated Processing Unit (APU). The APU to boot up your notebook. (*USB Charger+ is only available in the USB3.0 SKU) combines a high performance CPU and discrete GPU giving users the best in multimedia enjoyment. With the super low power consumption that the Eee PC 1015BX draws, you can have fun anytime, anywhere. Unbelievable HD multimedia experience With the embedded AMD Radeon™ HD 6250 graphics, the Eee PC 1015BX provides users the best portable multimedia enjoyment for its size. DirectX® 11 support – exceptional 3D performance allows users to play games and video smoother than ever before. Users can enjoy smooth, Full HD 1080p content through the HDMI port to an HD display without any latency. Connect it to a home theater system to enjoy true 7.1 Surround sound playback alongside the Full HD content for the ultimate viewing experience No compromise with the battery life Thanks to the ASUS exclusive Super Hybrid Engine technology, power consumption can be saved up to 15%, providing up to 8.5** hours of battery life. -

The GNOME Census: Who Writes GNOME?
The GNOME Census: Who writes GNOME? Dave Neary & Vanessa David, Neary Consulting © Neary Consulting 2010: Some rights reserved Table of Contents Introduction.........................................................................................3 What is GNOME?.............................................................................3 Project governance...........................................................................3 Why survey GNOME?.......................................................................4 Scope and methodology...................................................................5 Tools and Observations on Data Quality..........................................7 Results and analysis...........................................................................10 GNOME Project size.......................................................................10 The Long Tail..................................................................................11 Effects of commercialisation..........................................................14 Who does the work?.......................................................................15 Who maintains GNOME?................................................................17 Conclusions........................................................................................22 References.........................................................................................24 Appendix 1: Modules included in survey...........................................25 2 Introduction What -

KREATIVE GRAFIK Xargs • GRAFIK-TOOLS Logo-Design Mit Inkscape S
Qubes OS: Mehr Sicherheit COMMUNITY-EDITIONXargs: Praktischer Helfer durch Xen-Virtualisierung S. 6 für Befehlsverkettungen S. 92 Frei kopieren und beliebig weiter verteilen ! 02.2015 02.2015 Malen, zeichnen, animieren: Die besten Programme für Pixel- und Vektorgrafik TOOLS GRAFIK- • KREATIVE GRAFIK Xargs • GRAFIK-TOOLS Logo-Design mit Inkscape S. 30 Pixart-Künstler mtPaint S. 27 • Swiss File Knife Illustrationen mit Draw, SSD-Tuning Screencasts mit SSR S. 18, 22 Grafiktabletts optimal konfigurieren S. 36 • Qubes OS Semplice Dreimal Fedora 21: Fit fürs nächste Jahrzehnt S. 14 Spezialisierte Versionen für jeden Einsatzzweck, neue Tools, optionales Wayland, mehr Systemd: Wie sich Red Hats Community-Distribution für die Zukunft rüstet Gimp-Plugins Hollywoodreifer Schnitt S. 70 SSDs voll ausreizen S. 84 So zaubert Lightworks 12 beeindruckende Wie Sie den letzten Rest Leistung Effekte und Übergänge in Ihre Videoclips aus dem Flash-Speicher quetschen • Fedora 21 • • Fedora Top-Distris E-Books • auf zwei Heft-DVDs FEDORA 21 • LIGHTWORKS • SLAP • SYSTEMBACK • XARGS • • XARGS • SYSTEMBACK • LIGHTWORKSSLAP • 21 FEDORA EUR 8,50 EUR 9,35 sfr 17,00 EUR 10,85 EUR 11,05 EUR 11,05 2 DVD-10 02 www.linux-user.de Deutschland Österreich Schweiz Benelux Spanien Italien 4 196067 008502 02 001-001_titel_LU_02.indd 1 22.12.14 12:59 Editorial Zahlenspiele Sehr geehrte Leserinnen und Leser, mit schöner Regelmäßigkeit überschlu sammenstellungen überlebt also lang gen sich in den vergangenen Jahren vor fristig. Trotzdem stehen heute gut allem USComputermedien darin, zu Jah 260 Distributionen zur Auswahl, da resbeginn das „Jahr des LinuxDesktops“ von 166 explizit für den Desktop. auszurufen. 2015 allerdings sucht man Anders, als man denken könnte, han entsprechende Schlagzeilen vergeblich, delt es sich bei Ubuntu und Co. -
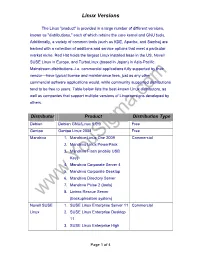
Linux Versions
Linux Versions The Linux "product" is provided in a large number of different versions, known as "distributions," each of which retains the core kernel and GNU tools. Additionally, a variety of common tools (such as KDE, Apache, and Samba) are backed with a collection of additions and service options that meet a particular market niche. Red Hat holds the largest Linux installed base in the US, Novell SUSE Linux in Europe, and TurboLinux (based in Japan) in Asia-Pacific. Mainstream distributions--i.e. commercial applications fully supported by their vendor—have typical license and maintenance fees, just as any other commercial software applications would, while community supported distributions tend to be free to users. Table below lists the best-known Linux distributors, as well as companies that support multiple versions of Linux versions developed by others. Distributor Product Distribution Type Debian Debian GNU/Linux 5.0.0 Free Gentoo Gentoo Linux 2008 Free Mandriva 1. Mandrive Linux One 2009 Commercial 2. Mandriva Linux PowerPack 3. Mandriva Flash (mobile USB Key) 4. Mandriva Corporate Server 4 5. Mandriva Corporate Desktop 6. Mandriva Directory Server 7. Mandriva Pulse 2 (tools) 8. Linbox Rescue Server (backup/restore system) Novell SUSE 1. SUSE Linux Enterprise Server 11 Commercial Linux 2. SUSE Linux Enterprise Desktop 11 3. SUSE Linux Enterprise High Page 1 of 4 Linux Versions Availability Extension 4. SUSE Linux Enterprise Mono Extension 5. SUSE Linux Enterprise Server for System z 6. SUSE Linux Enterprise Real Time Extension 7. SUSE Linux Enterprise Server Priority Support for 8. SAP Applications 9. SUSE Linux Enterprise Point of Service 10.