A Study of Bluetooth Low Energy Performance for Human Proximity Detection in the Workplace
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Survey of Smartwatch Platforms from a Developer's Perspective
Grand Valley State University ScholarWorks@GVSU Technical Library School of Computing and Information Systems 2015 A Survey of Smartwatch Platforms from a Developer’s Perspective Ehsan Valizadeh Grand Valley State University Follow this and additional works at: https://scholarworks.gvsu.edu/cistechlib ScholarWorks Citation Valizadeh, Ehsan, "A Survey of Smartwatch Platforms from a Developer’s Perspective" (2015). Technical Library. 207. https://scholarworks.gvsu.edu/cistechlib/207 This Project is brought to you for free and open access by the School of Computing and Information Systems at ScholarWorks@GVSU. It has been accepted for inclusion in Technical Library by an authorized administrator of ScholarWorks@GVSU. For more information, please contact [email protected]. A Survey of Smartwatch Platforms from a Developer’s Perspective By Ehsan Valizadeh April, 2015 A Survey of Smartwatch Platforms from a Developer’s Perspective By Ehsan Valizadeh A project submitted in partial fulfillment of the requirements for the degree of Master of Science in Computer Information Systems At Grand Valley State University April, 2015 ________________________________________________________________ Dr. Jonathan Engelsma April 23, 2015 ABSTRACT ................................................................................................................................................ 5 INTRODUCTION ...................................................................................................................................... 6 WHAT IS A SMARTWATCH -

Smartwatch Security Research TREND MICRO | 2015 Smartwatch Security Research
Smartwatch Security Research TREND MICRO | 2015 Smartwatch Security Research Overview This report commissioned by Trend Micro in partnership with First Base Technologies reveals the security flaws of six popular smartwatches. The research involved stress testing these devices for physical protection, data connections and information stored to provide definitive results on which ones pose the biggest risk with regards to data loss and data theft. Summary of Findings • Physical device protection is poor, with only the Apple Watch having a lockout facility based on a timeout. The Apple Watch is also the only device which allowed a wipe of the device after a set number of failed login attempts. • All the smartwatches had local copies of data which could be accessed through the watch interface when taken out of range of the paired smartphone. If a watch were stolen, any data already synced to the watch would be accessible. The Apple Watch allowed access to more personal data than the Android or Pebble devices. • All of the smartwatches we tested were using Bluetooth encryption and TLS over WiFi (for WiFi enabled devices), so consideration has obviously been given to the security of data in transit. • Android phones can use ‘trusted’ Bluetooth devices (such as smartwatches) for authentication. This means that the smartphone will not lock if it is connected to a trusted smartwatch. Were the phone and watch stolen together, the thief would have full access to both devices. • Currently smartwatches do not allow the same level of interaction as a smartphone; however it is only a matter of time before they do. -

Samsung, LG Launch Smartwatches with New Google Software 26 June 2014
Samsung, LG launch smartwatches with new Google software 26 June 2014 largest smartphone maker, respectively. A typical smartwatch allows users to make calls, receive texts and e-mails, take photos and access apps. G Watch opened Thursday for online pre-order in 12 countries including the United States, France and Japan before hitting stores in 27 more including Brazil and Russia in early July. Gear Live was also available for online pre-order Thursday. Visitors check out Samsung Gear Live watches during the Google I/O Developers Conference at Moscone Center in San Francisco, California, on June 25, 2014 South Korea's Samsung and LG on Thursday launched rival smartwatches powered by Google's new software as they jostle to lead an increasingly competitive market for wearable devices seen as the mobile industry's next growth booster. Samsung's "Gear Live" and LG's "G Watch"—both powered by Android Wear—are the first devices to adopt the new Google software specifically A LG G watch is seen on display during the Google I/O designed for wearables. Developers Conference at Moscone Center in San Francisco, California, on June 25, 2014 G Watch—LG's first smartwatch—is also equipped with Google's voice recognition service and can perform simple tasks including checking email, sending text messages and carrying out an online The launches come as global handset and software search at users' voice command. makers step up efforts to diversify from the saturated smartphone sector to wearable devices. The two devices cannot make phone calls by themselves but can be connected to many of the Samsung introduced its Android-based Galaxy latest Android-based smartphones, the South Gear smartwatch last year but it was given a Korean companies said in separate statements. -

Wearable Haptic Systems for the Fingertip and the Hand: Taxonomy, Review, and Perspectives
IEEE TRANSACTIONS ON HAPTICS, VOL. XX, NO. X, XX 20XX 1 Wearable Haptic Systems for the Fingertip and the Hand: Taxonomy, Review, and Perspectives Claudio Pacchierotti, Member, IEEE, Stephen Sinclair, Member, IEEE, Massimiliano Solazzi, Member, IEEE, Antonio Frisoli, Member, IEEE, Vincent Hayward, Fellow, IEEE, Domenico Prattichizzo, Fellow, IEEE Abstract—In the last decade, we have witnessed a drastic change in the form factor of audio and vision technologies, from heavy and grounded machines to lightweight devices that naturally fit our bodies. However, only recently, haptic systems have started to be designed with wearability in mind. The wearability of haptic systems enables novel forms of communication, cooperation, and integration between humans and machines. Wearable haptic interfaces are capable of communicating with the human wearers during their interaction with the environment they share, in a natural and yet private way. This paper presents a taxonomy and review of wearable haptic systems for the fingertip and the hand, focusing on those systems directly addressing wearability challenges. The paper also discusses the main technological and design challenges for the development of wearable haptic interfaces, and it reports on the future perspectives of the field. Finally, the paper includes two tables summarizing the characteristics and features of the most representative wearable haptic systems for the fingertip and the hand. Index Terms—wearable haptics, fingertip haptics, hand exoskeletons, wearable devices, wearable interfaces, cutaneous force feedback, tactile force feedback, taxonomy, review F 1 INTRODUCTION Technology for touching remote objects has typically been the Apple Watch. They are easy and comfortable to wear, used in teleoperation. A robot is controlled as a slave in they often feature a touch screen, and they have functions the remote scenario and a haptic interface feeds back the similar to smartphones. -

Smart Watch OS Mobile OS Supported by Komoot Tours
Tours (Link for Detailed Description) Navigation Speedometer Average & Current Speed, Time Smart Watch OS Mobile OS Supported by Komoot Smart Tour Arrows, Street Name & Saved/Offline Notifications Average & Current Speed & Distance Traveled & Progress / Recommendations Distance Updates Position on Tour Apple Watch iOS App - Video with Details 1 3 yes yes yes Android Wear Moto 360 LG G Watch R Sony Smart Watch 3 Android 4.3 App - Video with Details yes yes yes LG G Watch Samsung Gear Live ...further Android Wear Tizen 2.3 Gear S3 Android (only Gear S2 with Samsung New App with Tizen 2.3 5 3 yes yes yes yes Gear S Phone) Gear 2 OS that supports Notifications iOS & Android Notifications Pebble iOS & Android Notifications Fenix 3 iOS & Android Notifications Vivo Active iOS & Android Notifications yes (as shown on linked Forerunner 920XT iOS & Android Notifications picture during testing) Epix iOS & Android Notifications iOS Android Android Wear Notifications Wear App Other not supported Sony Smart Watch 2 Android 4.0 not supported Samsung Gear Fit (RTOS) Samsung not supported Other Devices Navigation via linked bike computer, demo video Ciclo HAC 1, HAC 2.1 iOS & Android BLE Connect via app settings linked here Navigation via linked Yamaha Display C iOS & Android Bluetooth Connect via app settings Yamaha display Navigation via linked Wahoo Elemnt, Elemnt Bolt iOS & Android Profile Connect Elemnt Navigation via linked Sigma Sigma Rox 12.0 iOS & Android komoot Profile Connect Rox COBI iOS & Android Navigation via linked COBI Garmin D2™ Charlie -
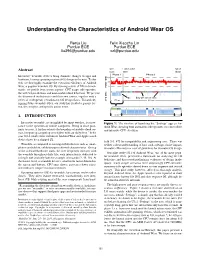
Understanding the Characteristics of Android Wear OS
Understanding the Characteristics of Android Wear OS Renju Liu Felix Xiaozhu Lin Purdue ECE Purdue ECE [email protected] [email protected] User Launch action App UI Abstract touch starts shown Interactive wearable devices bring dramatic changes to apps and Phase 1 Phase 2 1000 hardware, leaving operating system (OS) design in the mist. To this mW end, we thoroughly examine the execution efficiency of Android 500 0 Wear, a popular wearable OS. By running a suite of fifteen bench- Power / marks, we profile four system aspects: CPU usage, idle episodes, thread-level parallelism, and microarchitectural behaviors. We present the discovered inefficiencies and their root causes, together with a Idle Busy with various tasks series of widespread, yet unknown OS design flaws. Towards de- Exec. CPU 177 ms 810 ms signing future wearable OSes, our study has yielded a generic les- son, key insights, and specific action items. 1. INTRODUCTION 28 ms 130 ms 19 ms Interactive wearable, as exemplified by smart watches, is a new- Figure 1: The timeline of launching the “Settings” app on An- comer to the spectrum of mobile computers. Being in close prox- droid Wear, showing both anomalous idle episodes (not due to I/O) imity to users, it further extends the boundary of mobile-cloud ser- and intensive CPU execution vice, integrating computing even tighter with our daily lives.1 In the year 2014, nearly three million of Android Wear and Apple watch devices have been shipped [7]. held [10, 47] for compatibility and engineering ease. There was Wearable, as compared to existing mobile devices such as smart- neither a clear understanding of how such a design choice impacts phones and tablets, exhibits unprecedented characteristics. -

Samsung Gear Live Teardown Guide ID: 27038 - Draft: 2014-07-29
Samsung Gear Live Teardown Guide ID: 27038 - Draft: 2014-07-29 Samsung Gear Live Teardown Teardown of the Samsung Gear Live on July 7, 2014. Written By: Sam Goldheart This document was generated on 2020-11-20 01:17:58 AM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 1 of 11 Samsung Gear Live Teardown Guide ID: 27038 - Draft: 2014-07-29 INTRODUCTION The first of the Android Wear teardowns are here: Say hello to our little Samsung Gear Live and LG G Watch friends! Join us as we journey inside two of the newest smartwatches. Can't get your fix fill from the teardowns? Come say hello on Facebook, see iFixit's internal workings on Instagram, or learn about repair on Twitter! [video: https://www.youtube.com/watch?v=Kw3di0v04wQ] TOOLS: T5 Torx Screwdriver (1) iFixit Opening Tools (1) Spudger (1) Tweezers (1) Phillips #000 Screwdriver (1) This document was generated on 2020-11-20 01:17:58 AM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 2 of 11 Samsung Gear Live Teardown Guide ID: 27038 - Draft: 2014-07-29 Step 1 — Samsung Gear Live Teardown We could very well be witnessing the birth of the smartwatch revolution. Google has unleashed not one, not two, but three smartwatches onto the battlefield. We have before us the Gear Live of those three fabled smartwatches. The official tech specs: 1.63” Super AMOLED display with a resolution of 320 x 320 pixels (278 ppi) 1.2 GHz processor 300 mAh Battery (rated at max 1 day of usage) 4 GB internal flash storage with 512 MB RAM Digital compass, accelerometer, gyroscope, heart rate monitor Bluetooth 4.0 Low Energy This document was generated on 2020-11-20 01:17:58 AM (MST). -

Utilizing Smartwatches for Supporting the Wellbeing of Elderly People
HEALTHINFO 2017 : The Second International Conference on Informatics and Assistive Technologies for Health-Care, Medical Support and Wellbeing Utilizing Smartwatches for Supporting the Wellbeing of Elderly People Rainer Lutze Klemens Waldhör Dr.-Ing. Rainer Lutze Consulting FOM University of Applied Sciences Langenzenn, Germany Essen / Nuremberg, Germany email: [email protected] email: [email protected] Abstract — We present a new approach for securing the condensed sensor data and suitable comparisons with data wellbeing of elderly people via a smartwatch based personal acquired, learned from the past. A common approach is to health assistant. On the smartwatch, an app featuring an artifi- recognize - using the smartwatch sensors - those activities of cial neuronal network (ANN) analyzes the activity patterns of daily living (ADLs) which are present in a healthy life of the smartwatch wearer. The ANN recognizes health relevant everyone and structure the days and nights. The conclusions events and activities of daily living (EDLs, ADL). Especially activities associated with body care tasks are considered. From about the wellbeing will then be based on the presence, du- the sequence and timing of recognized EDLs, ADLs, an indi- ration and intervals between those recognized activities of vidual wellbeing function will be continuously calculated, daily living. Direct health hazards – like tumbles/falls, heart summarizing the specific personal health state. If the wellbeing palpitations – need to be considered and recognized by the function value falls below a defined threshold, external alerts smartwatch sensors (as events of daily living, EDLs). will be issued by the smartwatch. Such alerting will be done automatically, if the smartwatch wearer is not able to respond. -
Thesis Paper.Docx
CALIFORNIA STATE UNIVERSITY, NORTHRIDGE Utilizing Smart Watch Motion Sensors in Human Computer Interaction via Pattern Detection A thesis submitted in partial fulfillment of the requirements For the degree of Master of Science in Computer Science By Danial Moazen May 2015 1 The thesis of Danial Moazen is approved: SIGNATURE PAGE ___________________________________ ____________ Professor Vahab Pournaghshband Date ___________________________________ ____________ Professor Gloria Melara Date ___________________________________ ____________ Professor Ani Nahapetian, Chair Date California State University, Northridge ii Contents SIGNATURE PAGE .......................................................................................................... ii LIST OF TABLES .............................................................................................................. v LIST OF FIGURES .......................................................................................................... vii ABSTRACT ..................................................................................................................... viii 1. INTRODUCTION .......................................................................................................... 1 2. RELATED WORK ......................................................................................................... 3 2.1. Wearable Computing ............................................................................................... 3 2.1.1. Smart Watch..................................................................................................... -
Mole: Motion Leaks Through Smartwatch Sensors
MoLe: Motion Leaks through Smartwatch Sensors Yi Mao, Ruoxi Li Introduction Question: can we mine accelerometer and gyroscope data from smart watches to infer what words a user is typing? Introduction - Challenges ● Absence of data from the right hand (which is not wearing the watch) ● Issue of inferring which finger executed the key-press ● For a given watch position, a shortlist of keys could have been pressed ● Different users’ habits and keyboard devices Introduction - Opportunities ● the watch motion is mostly confined to the 2D keyboard plane ● The orientation of the watch is relatively uniform across various users ● knowing spelling priors from English dictionary further helps in developing Bayesian decisions. Introduction - Work Motion Leaks (MoLe) ● Device: Samsung Gear Live smartwatch ● Input: ○ 2 authors (attacker) - each typed 500 words for training ○ 8 volunteers (attackee) - each typed 300 words for testing ● Output: K words (ranked in decreasing probability) short-list for each word Introduction - Contributions ● Identifying the possibility of leakage - required building blocks ○ key-press detection ○ hand-motion tracking ○ cross-user data matching ○ Bayesian inference ● Developing the system on Samsung Gear Live ○ experimenting with real users ○ reasonable accuracy ○ Sense of alarm A first look at smart watch data A first look at smart watch data A first look at smart watch data System Overview System Overview System Overview - Assumptions ● The evaluation is performed in a controlled environment where volunteers type one word at a time (as opposed to free-flowing sentences). ● We assume valid English words – passwords that contain interspersed digits, or non-English character-sequences, are not decodable as of now. ● We have used the same Samsung smart watch model for both the attacker and the user – in reality the attacker can generate the CPC for different watch models and use the appropriate one based on the user’s model. -

Apple Watch (A) – the Launch
For the exclusive use of m. algoblan, 2021. BAB344 / JULY 2017 Apple Watch (A) – The Launch "In the beginning was Apple. All things were made by it; and without it was not anything made that was made." If technophiles were to write their own Testament, these might be the opening lines. Apple's ability to redefine the appeal of whole categories of computing has attracted the unerring faith of millions of followers. Apple has popularised existing technologies four times: with the Macintosh computer in 1984, the iPod in 2001, the iPhone in 2007 and the iPad in 2010. Recently the faithful have prayed that Apple will pull it off again with its smartwatch. Many firms already make wrist-based devices that measure sleep patterns and exercise, but so far the category has remained a niche plaything for geeks and athletes.1 On September 9, 2014, Apple announced its entry into the wearable computing market with the introduction of the Apple Watch, marking its first new hardware product since the death of Steve Jobs, and since introducing the iPad four years prior. Along with the excitement of typical Apple fans, there was anticipation from other players in the smartwatch industry who wondered how Apple’s entrance would help or hurt their own success. From competitors to component suppliers to application developers, many firms had a stake in Apple’s pricing and promotion strategies for the Apple Watch. Background: The Smartwatch Industry A smartwatch gained much functionality and versatility from connection to a mobile phone which it used for wireless communication and interaction with a variety of applications or apps. -

The Hring: a Wearable Haptic Device to Avoid Occlusions in Hand Tracking
The hRing: a Wearable Haptic Device to Avoid Occlusions in Hand Tracking Claudio Pacchierotti1, Gionata Salvietti2, Irfan Hussain2, Leonardo Meli1,2 and Domenico Prattichizzo1,2 Abstract— The wearable electronics business has powered over $14 billion in 2014 and it is estimated to power over $70 Servo motors billion by 2024. However, commercially-available wearable de- vices still provide very limited haptic feedback, mainly focusing on vibrotactile sensations. Towards a more realistic feeling of interacting with virtual and remote objects, we propose a novel wearable cutaneous device for the proximal finger phalanx, Velcro called “hRing”. It consists of two servo motors that move a support band belt placed in contact with the user’s finger skin. When the motors spin in opposite directions, the belt presses into the Belt user’s finger, while when the motors spin in the same direction, the belt applies a shear force to the skin. Its positioning on the proximal finger phalanx improves the capability of this device to be used together with unobtrusive hand tracking systems, such as the LeapMotion controller and the Kinect sensor. The viability of the proposed approach is demonstrated through a pick-and-place experiment involving seven human subjects. Providing cutaneous feedback through the proposed Fig. 1. The proposed 2-DoF cutaneous device. It consists of two servo device improved the performance and perceived effectiveness motors that move a belt placed in contact with the user’s finger skin. It is of the considered task of 20% and 47% with respect to not able to provide both normal and shear forces to the finger.