Smart Grid Last-Mile Communications Model and Its Application to The
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Last-Mile Guide
LAST-MILE GUIDE Leveraging KentuckyWired for local broadband deployment Phone: 606-677-6000 Address: Email: [email protected] 2292 South Highway 27 Web: www.centertech.com Suite 300 Social Media: facebook.com/CRDbroadband Somerset, KY 42501 This Page Intentionally Left Blank The Center for Rural Development’s Fiber Infrastructure Project - Phase 3 is funded by grant KY-18984-17 from the Appalachian Regional Commission and is administered by The Center for Rural Development. Page 3 of 20 OVERVIEW The Last-Mile Action team was formed to help your community with the task of solving the “Last- Mile” dilemma that faces most of rural America. The team was created as a partnership between The Center for Rural Development, which works to positively impact the communities within 45 counties of Southern and Eastern Kentucky, and SOAR, part of whose mission it is to enhance opportunity and innovation in Appalachian Kentucky. The last-mile is the final bit of fiber optic cable, copper wire or radio transmission that goes from a home, business, school or hospital and connects into the “middle-mile” infrastructure. The middle-mile is typically an intra-state web of high-speed, high-capacity fiber optic cable that consolidates thousands of last-mile connections and gets them access to the national tier 1 internet providers. There have been numerous discussions with telecommunications providers over the years regarding improving service and widening availability of broadband access, but little to no improvement had taken place until the KentuckyWired initiative. The fiber infrastructure that exists in the service area is dated and is being used, for the most part, at capacity. -

The Changing Route to the Last Mile
White paper The changing route to the last mile www.commscope.com 1 In most European countries telecommunications service providers have rolled out either copper or fiber networks as far as the street cabinets or drop points from which connections are made to customer premises. These connections cover what is referred to as the ‘last mile’—the final route taken by a cable from the street to the subscriber. The last mile to the customer is, in most European countries, a copper network, but replacing copper with fiber—or fiber to the home (FTTH)—is being actively considered across the continent. In particular, the so-called Digital Agenda, presented by the European Commission as one of the seven pillars of the Europe 2020 Strategy, suggests that new services such as high definition television or video conferencing need much faster internet access than is generally available in Europe. It proposes that Europe needs download rates of 30 Mbps for all of its citizens and at least 50% of European households subscribing to Internet connections above 100 Mbps by 2020. FTTH is seen as a way of achieving this. This, however, may be easier said than done. Fiber is replacing Fiber, meanwhile, is also coming closer to the home. In fact not just copper in many networks but the closer you bring fiber cable to the fiber to the curb (FTTC) but fiber to the drop point or distribution customer the more expensive it gets, partly because you eventually point (FTTDP) allow fiber terminations within very close range of have to penetrate the customer’s premises. -

Powerline and Coax Adapters
Powerline and Coax Adapters Powerline Ethernet Adapters Powerline Wireless Extenders HomePNA Ethernet Bridges Powerline and Coax Adapters Powerline and Coax Adapters Introduction Introduction ZyXEL Powerline and Coax Adapters Powerline Home Network NSA325 2-Bay Power Plus Turn Your Power Lines or Coaxial Cables into a Smart Home Network Media Server NWD2205 Wireless N ZyXEL’s broad line of Powerline adapters allow you to use your existing power outlets to create a fast and secure home network. You won’t need USB Adapter Study Room to install new cables, which saves you time, money and effort. Your Powerline network will enable you to share your Internet connection as well PLA4231 as all your digital media content, so you can enjoy Broadband content anywhere in your home. In fact, Powerline extends your network to areas 500 Mbps Powerline PLA4211 500 Mbps Mini Powerline even wireless signals may not reach. Wireless N Extender STB2101-HD Pass-Thru Ethernet Adapter HD IP Set-Top Box Game Wired LAN Adapter Product Portfolio Console Internet Blu-ray HDTV xDSL/Cable Player Modem PLA4201 PLA4225 500 Mbps 500 Mbps Mini Powerline Powerline 4-Port Power Line NBG5615 Ethernet Adapter Gigabit Switch Living Room Wireless N Ethernet Simultaneous AV/HDMI Cable Dual-Band Wireless HD Powerline PLA4231 N750 Media Router Extender 500 Mbps Powerline Wireless N Extender Power Line Benefits of Wired LAN Adapter 500 Mbps Mini Powerline Plug-and-Play Design Oce Room Ethernet Adapter 500 Mbps Mini Powerline Pass-Thru Simply plug a ZyXEL Powerline Adapter into an outlet near your Ethernet Adapter IEEE 1901 router and plug your router into it. -

Bringing Broadband Over the Last Mile
TELECOM Interactive 97 Infrastructure - Session [GII.9] BROADBAND TECHNOLOGIES - CRASHING THE BANDWIDTH BOTTLENECK BRINGING BROADBAND OVER THE LAST MILE Implementation Issues for ADSL By Mark Huntzinger Director, 3Com ADSL System Product Management Introduction This paper covers some business and technical implementation issues of extending the broadband network to the end user, using Asymmetrical Digital Subscriber Line (ADSL) to send multi-megabit data over ordinary subscriber loops, the “last mile” of the installed copper plant, to end-users. In order for a mass-market, broadband-access network to develop, it requires low costs and flexible services for market segments. Key issues of ADSL service are how to configure and manage concurrent connections from end-users to their multiple service destinations, end-to-end. 3Com sees three implications: · ATM is the key back-end infrastructure needed to build a broadband-access network over the last mile, because it best accommodates end-to-end connections. For the ADSL end user, who is a telecommuter, Internet enthusiast, or small office, ATM does wonderful things. But the carriers must hide the complexity of ATM from the end user; this is a lesson learned from ISDN experience worldwide. · Renovation of the Element Management System and the configuration process are key to making the business case for mass deployment. Management systems will have to learn to look end-to-end, not just at a collection of elements. · Open standards are the key to lowering costs, protecting customers’ investments, and achieving interoperability. ADSL equipment vendors and customers that are slow to adopt open standards endanger their ADSL business. -

MLKHN1500 Fully Compliant IEEE 1901 HD-PLC Power Line Communications (PLC) IC
MLKHN1500 Fully compliant IEEE 1901 HD-PLC Power line Communications (PLC) IC Datasheet KDS-HANFF02EAA Rev. 1.00 MegaChips’ Proprietary and Confidential This information shall not be shared or distributed outside the company and will be exchanged based on the signed proprietary information exchange agreement. MegaChips reserves the right to make any change herein at any time without prior notice. MegaChips does not assume any responsibility or liability arising out of application or use of any product or service described herein except as explicitly agreed upon. MegaChips’ Proprietary Information – Strictly Confidential Page 1 of 68 MLKHN1500 Datasheet Rev.1.0.0 Contents 1. Product Overview ....................................................................................................................................... 6 1.1. Functional Overview ............................................................................................................................ 6 1.1.1. Key Features ................................................................................................................................ 6 1.1.2. Applications .................................................................................................................................. 7 1.2. Block Diagram ..................................................................................................................................... 7 2. Pins ............................................................................................................................................................ -

Last-Mile Agility Streamlines Rural Connectivity in Multi-Locale Oil & Gas Project
Last-Mile Agility Streamlines Rural Connectivity in Multi-Locale Oil & Gas Project Agile Networks Agile Networks is the premier provider of hybrid fiber wireless broadband data networks, provides connectivity to empower individuals and transform organizations. Agile Networks’ hybrid network - The Agile Network - utilizes vertical infrastructure along with the latest in fiber-optic and wireless technologies to provide world-class data solutions. Engineered to the stringent specifications required to support public safety, The Agile Network boasts carrier-grade performance and military-grade security. Agile’s Last-Mile Agility makes delivering solutions to rural areas just as feasible as major cities. Customer Profile M3 Midstream LLC (“Momentum”) is an independent midstream energy company that provides oil and gas producers with flexible, responsive and reliable midstream services linking the Gas Gathering NGL Storage Cryogenic Processing Rail Loading wellhead to the market. Their core focus is the development of high quality green field projects Fractionation that meet the emerging needs of their customers. Situation Result Situation Lack of IT infrastructure stymies Improved operational efficiency, • Need for IT infrastructure for newly constructed plant operation product delivery and application plants in rural area void of traditional connectivity options Momentum constructed a multi-billion dollar opportunities natural gas refining plant with multiple Momentum provides customers with rich gas Solution locations throughout southeastern Ohio; gathering, cryogenic processing, fractionation, • Agile leverages a vertical infrastructure and fiber however, the rural landscape did not offer the NGL storage, rail loading and multiple gas assets necessary IT infrastructure to support the and NGL redelivery options through the newly • Agile develops a reliable and efficient security and plant. -
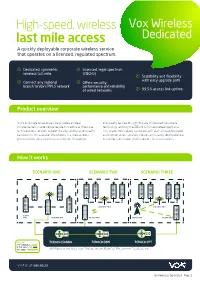
Last Mile Access Dedicated a Quickly Deployable Corporate Wireless Service That Operates on a Licensed, Regulated Spectrum
High-speed, wireless Vox Wireless last mile access Dedicated A quickly deployable corporate wireless service that operates on a licensed, regulated spectrum. Dedicated, symmetric Licensed, legal spectrum wireless last mile (28GHz) Scalability and flexibility with easy upgrade path Connect any regional Offers security, branch to Vox’s MPLS network performance and reliability of wired networks 99.5% access link uptime Product overview Vox‘s corporate wireless service provides an ideal and quality service through the use of licensed microwave complementary or alternative service to traditional, fixed-line, technology, utilising the 28GHz ICASA-allocated spectrums. last mile access services. A great standby solution when quality This proven technology, combined with Vox’s discounted voice bandwidth is not available. Vox Wireless is a fixed-wireless, and internet access services, creates an instantly deployable and point-to-point data solution boasting high throughput cost-effective product that is perfect for your business. How it works SCENARIO ONE SCENARIO TWO SCENARIO THREE HIGH SITE ONLY HIGH SITE ONLY .. ..OR CLIENT SITE ME & HIGH SITE ME SITE ONLY REPEAT SITE ME SITE ONLY LEGEND TERACO ISANDO TERACO DBN TERACO CPT PTP WIRELESS: PTMP WIRELESS: ME FIBRE: (ME Fibre connectivity from Telkom, Neotel, FibreCo, DFA, Internet Solutions, etc.) Visit us at vox.co.za Vox Wireless Dedicated - Page 1 Features and benefits • Metro ethernet architecture • Dedicated service Vox Wireless is easier to manage and upgrade. No contention. Last mile speeds are guaranteed and managed with controlled contention ratios providing • Wireless dedicated end-to-end capacity. No fixed lines required. Vox Wireless provides similar security, performance and reliability of • Fixed pricing irrespective of distance, wired networks. -

Broadband: the Last Mile
11/30/2016 Last-Mile Network Broadband and Last Mile Networks Design Concerns History: Dial-up • Infrastructure Cost • First public Internet service used telephone lines • Throughput: Upstream and Downstream • Telephone lines: broadly available, low infrastructure cost • Packet or Circuit Switching • Phone modem encoded/decoded data in voiceband • Congestion Control • Dial-up: call a phone number, get Internet • Latency • Result: different networks used in different scenarios 1 11/30/2016 History: DSL History: Cable Broadband • Digital Subscriber Line: improvement on dial-up • Growth of Internet required greater throughput • Used extra bandwidth on telephone line • Use extra bandwidth in existing cable TV networks • Always on, circuit-switched • Higher throughput, but along shared medium • Allowed concurrent use of phones • Primary standard is DOCSIS • Faster than dial-up, but slower with distance • Still used in rural areas due to low infrastructure cost DOCSIS DOCSIS Architecture (DOCSIS 3.0) • Data Over Cable Service Interface Specifications • Formed by industry consortium, maintained by CableLabs • Combined 2 earlier, proprietary standards • Physical layer from Motorola CDLP • MAC layer from LANcity 2 11/30/2016 Physical Infrastructure Transmission • Coaxial cable or hybrid fiber-coaxial (HFC) network • Radio frequency transmission • Fiber for trunk network, coaxial (RF) for client access • Downstream bandwidth: 108 MHz – 1002 MHz • Coaxial cables easy to install near metal objects • Upstream bandwidth: 5 MHz – 42 MHz or 85 MHz selectable • Cable Modem Termination System (CMTS) • Bandwidth divided into 6 MHz channels (NTSC) • Evolved from headend for cable TV distribution • 38 Mbps downstream throughput per channel • Handles the MAC layer and content distribution for an area • 9 Mbps (DOCSIS 1.0) or 27 Mbps (2.0) upstream throughput per channel • Interface to wide area network • Quadrature amplitude modulation (QAM) • Client Cable Modem • 2 carrier signals: phase difference encodes data • Performs demodulation of RF signal into usable data. -

Mobile Access — the Last Mile
GSMA Intelligence Mobile access ANALYSIS Mobile access — the last mile July 2014 © GSMA Intelligence gsmaintelligence.com/m4d • [email protected] • @GSMAi Mobile for 1 Development Impact GSMA Intelligence Mobile access Contents Executive summary ............................................................................................................................ 3 Mobile and the internet — a coalescence in adoption ............................................................... 6 Alternative connectivity 101 — what are these technologies targeting? .............................. 9 Aerial networks .............................................................................................................................................11 TV white space ............................................................................................................................................12 Potential for wider scale disruption ..............................................................................................14 Scale and cost ..............................................................................................................................................14 Licensing and regulatory .........................................................................................................................16 Quality of service ........................................................................................................................................17 Regardless, innovation is a good thing -

A Proposal for a Bluetooth Low Energy (BLE) Autoconfigurable Mesh Network Routing Protocol Based on Proactive Source Routing / Julio Humberto León Ruiz
UNIVERSIDADE ESTADUAL DE CAMPINAS Faculdade de Engenharia Elétrica e de Computação Julio Humberto León Ruiz A proposal for a Bluetooth Low Energy (BLE) autoconfigurable mesh network routing protocol based on Proactive Source Routing (Proposta de um protocolo de roteamento autoconfigurável para redes mesh em Bluetooth Low Energy (BLE) baseado em Proactive Source Routing) Campinas 2016 UNIVERSIDADE ESTADUAL DE CAMPINAS Faculdade de Engenharia Elétrica e de Computação Julio Humberto León Ruiz A proposal for a Bluetooth Low Energy (BLE) autoconfigurable mesh network routing protocol based on Proactive Source Routing (Proposta de um protocolo de roteamento autoconfigurável para redes mesh em Bluetooth Low Energy (BLE) baseado em Proactive Source Routing) Thesis presented to the School of Electrical and Computer Engineering of the Univer- sity of Campinas in partial fulfilment of the requirements for the degree of Doctor, in the area of Telecommunications and Telematics. Tese apresentada à Faculdade de Engen- haria Elétrica e Computação da Universi- dade Estadual de Campinas como parte dos requisitos exigidos para a obtenção do título de Doutor em Engenharia Elétrica na área de Telecomunicações e Telemática. Supervisor: Prof. Dr. Yuzo Iano ESTE EXEMPLAR CORRESPONDE À VER- SÃO FINAL DA TESE DEFENDIDA PELO ALUNO JULIO HUMBERTO LEÓN RUIZ, E ORIENTADA PELO PROF.DR.YUZO IANO Campinas 2016 Agência(s) de fomento e nº(s) de processo(s): CAPES Ficha catalográfica Universidade Estadual de Campinas Biblioteca da Área de Engenharia e Arquitetura Rose Meire da Silva - CRB 8/5974 León Ruiz, Julio Humberto, 1985- L553p Le_A proposal for a Bluetooth Low Energy (BLE) autoconfigurable mesh network routing protocol based on proactive source routing / Julio Humberto León Ruiz. -

Fiber-Based Last-Mile Delivery Is Changing the Telecom Industry
Fiber-Based Last-Mile Delivery is more. In addition, new hardware may be necessary to Changing the Telecom Industry bond the additional T1s and hand them off to the company’s equipment. The concept of huge quantities of voice and data If a fiber-based Ethernet had been installed in the last traveling vast distances almost instantaneously over a mile, the situation would have been much better. Fiber beam of light is still awe-inspiring, even for those who has vastly greater capacity than copper. While only a understand the depths of fiber optic technology. For very small part of that capacity would have been used the rest of us, fiber-based telecom is an incredible to deliver the original 1.5 mbps, the speed could very opportunity to increase capabilities, enhance security easily be scaled up to 10 mbps just by making a re- and improve cost-effectiveness. It has many benefits quest to the carrier – and the cost would have been over copper, from bandwidth capacity and signal about the same as the traditional 4.5 mbps example reliability to security and longevity. With dropping above. The carrier would simply “turn up the port” re- prices, the value advantage is clear. Copper has served motely, without scheduling a service call, running new us well over the past century plus, and it still has a role cable or installing new equipment. This would typically today, but there is little question that fiber is changing happen in 2-3 days at a very low cost. There would still our industry and lighting the future of telecom and IT. -

Redalyc.Efficient Hardware Implementation of a Full COFDM
Revista Facultad de Ingeniería Universidad de Antioquia ISSN: 0120-6230 [email protected] Universidad de Antioquia Colombia López Parrado, Alexander; Velasco Medina, Jaime; Ramírez Gutiérrez, Julián Adolfo Efficient hardware implementation of a full COFDM processor with robust channel equalization and reduced power consumption Revista Facultad de Ingeniería Universidad de Antioquia, núm. 68, febrero-septiembre, 2013, pp. 48- 60 Universidad de Antioquia Medellín, Colombia Available in: http://www.redalyc.org/articulo.oa?id=43029811005 How to cite Complete issue Scientific Information System More information about this article Network of Scientific Journals from Latin America, the Caribbean, Spain and Portugal Journal's homepage in redalyc.org Non-profit academic project, developed under the open access initiative Rev. Fac. Ing. Univ. Antioquia N.° 68 pp. 48-60. Septiembre, 2013 Efficient hardware implementation of a full COFDM processor with robust channel equalization and reduced power consumption Implementación eficiente en hardware de un procesador COFDM completo con ecualización de canal robusta y reducción de consumo de potencia Alexander López Parrado*1,2, Jaime Velasco Medina1, Julián Adolfo Ramírez Gutiérrez2 1Bionanoelectronics Research Group, Universidad del Valle. Edificio 354, Espacio 1011, Ciudad Universitaria Meléndez. Calle 13 No 100-00. C. P. 760033. Santiago de Cali, Colombia. 2GDSPROC Research Group, Bloque de Ingeniería, Tercer Piso, CEIFI. Universidad del Quindío. Carrera 15 Calle 12 Norte. C. P. 630004. Armenia, Colombia. (Recibido el 29 de enero de 2013. Aceptado el 5 de agosto de 2013) Abstract This work presents the design of a 12 Mb/s Coded Orthogonal Frequency Division Multiplexing (COFDM) baseband processor for the standard IEEE 802.11a.