Load Balancing Microsoft Skype for Business V1.1.2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
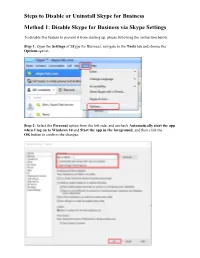
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center
VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center Table of Contents Click on any of the titles below to be navigated to that section SLI POLICIES ........................................................................................................................... 1 USING TIGERZONE TO YOUR ADVANTAGE .............................................................................. 1 ONLINE MEETING PLATFORMS ............................................................................................... 2 ONLINE BROADCASTING PLATFORMS ..................................................................................... 3 ONLINE CHAT PLATFORMS ..................................................................................................... 3 VIDEO CONFERENCE TIPS (for Zoom) ...................................................................................... 4 VIRTUAL ENGAGEMENT IDEAS ............................................................................................... 5 VIRTUAL ENTERTAINMENT ..................................................................................................... 6 SLI POLICIES During Phase 1 there are to be NO IN PERSON STUDENT EVENTS. This applies to events both ON and OFF campus. If your organization is found to be hosting in person events you will be given ONE warning from Student Leadership & Involvement. If your organization is found to be hosting student events a second time your organization will be suspended for the remainder of the 2020-2021 -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

CCIA Comments in ITU CWG-Internet OTT Open Consultation.Pdf
CCIA Response to the Open Consultation of the ITU Council Working Group on International Internet-related Public Policy Issues (CWG-Internet) on the “Public Policy considerations for OTTs” Summary. The Computer & Communications Industry Association welcomes this opportunity to present the views of the tech sector to the ITU’s Open Consultation of the CWG-Internet on the “Public Policy considerations for OTTs”.1 CCIA acknowledges the ITU’s expertise in the areas of international, technical standards development and spectrum coordination and its ambition to help improve access to ICTs to underserved communities worldwide. We remain supporters of the ITU’s important work within its current mandate and remit; however, we strongly oppose expanding the ITU’s work program to include Internet and content-related issues and Internet-enabled applications that are well beyond its mandate and core competencies. Furthermore, such an expansion would regrettably divert the ITU’s resources away from its globally-recognized core competencies. The Internet is an unparalleled engine of economic growth enabling commerce, social development and freedom of expression. Recent research notes the vast economic and societal benefits from Rich Interaction Applications (RIAs), a term that refers to applications that facilitate “rich interaction” such as photo/video sharing, money transferring, in-app gaming, location sharing, translation, and chat among individuals, groups and enterprises.2 Global GDP has increased US$5.6 trillion for every ten percent increase in the usage of RIAs across 164 countries over 16 years (2000 to 2015).3 However, these economic and societal benefits are at risk if RIAs are subjected to sweeping regulations. -

IM Security Documentation on Page Vi
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release notes, and/or the latest version of the applicable documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/trend-micro-im-security.aspx Trend Micro, the Trend Micro t-ball logo, Control Manager, MacroTrap, and TrendLabs are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2016. Trend Micro Incorporated. All rights reserved. Document Part No.: TIEM16347/140311 Release Date: September 2016 Protected by U.S. Patent No.: Pending This documentation introduces the main features of the product and/or provides installation instructions for a production environment. Read through the documentation before installing or using the product. Detailed information about how to use specific features within the product may be available at the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Privacy and Personal Data Collection Disclosure Certain features available in Trend Micro products collect and send feedback regarding product usage and detection information to Trend Micro. Some of this data is considered personal in certain jurisdictions and under certain regulations. -

Windows Messenger Live Msn Download
Windows messenger live msn download Windows Live Messenger latest version: See. Hear. Share. Instantly.. Windows Live Messenger previously known as MSN Messenger, was renamed as part of. MSN Messenger is an instant messaging program that lets you send instant messages to your friends, and much more. Previously known as MSN Messenger, Windows Live Messenger is Microsoft's answer to instant messaging. While largely the same as its predecessor. Windows Live Messenger free download. on their MSN or Hotmail account, as the integration with the email accounts can be. Mobile and web: Using a public computer without Messenger? No problem! You can chat on the web from Windows Live Hotmail or use. Share photos: Look at photos together, right in the conversation window and Messenger tells you when people you know post new photos on Windows Live. Microsoft Windows live messenger free Download Link: Latest Version. Old Version of MSN (Live) Messenger. Website. Developer. Microsoft Corporation. Latest Version. Windows. Messenger, which offers the user the same functionalities as Windows Live Messenger. Windows Live Messenger Final Deutsch: Der Windows Live Messenger, Nachfolger des MSN Messenger, in der Version: - vom How to Download and Install Windows Live Messenger. Windows Live Messenger is a great way to talk to people online. You can now have a personal picture. Windows 7 by default is installed without Windows Live Messenger. So to get it, we will need to download and install it. select, like setting Bing as the default search provider and setting MSN as your browser home page. is a free, personal email service from Microsoft. -
Skype Buys Messaging Startup Groupme 22 August 2011
Skype buys messaging startup GroupMe 22 August 2011 messaging experience that works across mobile devices and platforms, making this a perfect addition to the voice, video and text products in the Skype family." Founded in 2003 and based in Luxembourg, Skype is in the process of being acquired by US software giant Microsoft after being spun off by eBay. Microsoft said recently it hopes to close the deal for purchase of the Internet voice and video leader by October, once it gets the green light from European Skype, the Internet communications group set to be regulators. acquired by Microsoft, announced plans to buy the mobile messaging startup firm GroupMe for undisclosed (c) 2011 AFP terms. Skype, the Internet communications group set to be acquired by Microsoft, announced plans to buy the mobile messaging startup firm GroupMe for undisclosed terms. GroupMe was founded in 2010 at the Techcrunch Disrupt Hackathon and is headquartered in New York. The deal, coupled with the acquisition of mobile video provider Qik earlier this year, "augments Skype's role as an innovator in driving unique mobile user experiences," the company said in a statement. "Through the acquisition of GroupMe, Skype continues its drive to provide a global multi-modal and multi-platform communications experience. The acquisition of GroupMe complements Skype's leadership in voice and video communications by providing best in class text-based communications and innovative features that enable users to connect, share locations and photos and make plans with their closest ties." Tony Bates, Skype's chief executive, said GroupMe "has created an incredibly sticky group 1 / 2 APA citation: Skype buys messaging startup GroupMe (2011, August 22) retrieved 24 September 2021 from https://phys.org/news/2011-08-skype-messaging-startup-groupme.html This document is subject to copyright. -
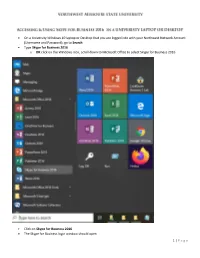
Getting Start with Skype
On a University Windows 10 laptop or Desktop that you are logged into with your Northwest Network Account (Username and Password), go to Search Type Skype for Business 2016 o OR click on the Windows icon, scroll down to Microsoft Office to select Skype for Business 2016 Click on Skype for Business 2016 The Skype for Business login window should open 1 | P a g e Type in your Northwest Network Account email address o Example: [email protected] Click the Sign In button Skype should open for you. o If Skype doesn’t open for you, then you will need to Install Skype via your online Northwest Email account (Office 365). See Supplemental Install instructions. If Skype opened for you, then proceed to Using Skype – The Basics. 2 | P a g e __________________________________________________________________________________________________ Supplemental Install Instructions – Only need if the above method to install did not work for you. Login to your online Northwest Email (Office 365), which can be accessed at https://www.nwmissouri.edu/login Once logged in, click on your My Account avatar (top, right hand corner of screen). A drop-down menu will appear. Click on My Account. Click on Office apps & devices. The apps and devices window will open. Select Skype for Business 2015 and not Office 365 in the dropdown menu 3 | P a g e Make sure 64-bit is selected if you are using Windows 10 o If using an older version of Windows like Windows 7, select 32-bit. Click the Install Skype button. A security warning may appear. Click Run Click Yes to “Do You want to allow the following program to make changes to this computer?” It will ask you to please wait while Office installs. -

Skype Broadcast Guidelines
Skype broadcast guidelines Version 1.2 August 15, 2014 Skype Broadcast Guidelines v1.2 08/15/2014 1 Contents Introduction 3 The Skype brand 4 Logo overview Our logo 6 Clear space and minimum sizes 7 Don’t do this 8 Logo in the lower third 9 UI Look like Skype 12 Watermark logo 13 Watermark size and position 14 Using a PIP 16 Sounds 18 Editorial Verbal mentions of Skype 20 Technical advice System requirements 22 Video 23 Audio 24 Contact us Contact us 26 Skype Broadcast Guidelines v1.2 08/15/2014 Contents 2 Introduction Welcome to Skype. These are our guidelines for broadcast and film. With Skype, you can make free voice and video calls with anyone else on Skype for free, no matter where they are. That means, broadcasters and studios can introduce live face to face video calls to TV and film. Skype can also be used for free Skype to Skype calls during radio programming. Use Skype for live on-air feeds from remote locations, interviewing viewers in their homes, engaging experts from around the world, and even for connecting with correspondents in the field. Skype is a great complement to traditional production methods – with free, voice and video calls, you can get rich new content, go places you’ve never considered and save costs. Skype can be weaved into feature film and TV drama narratives. This allows characters to use current technology and makes scenes feel true to life. These guidelines – and the associated resources available on request by emailing [email protected] – will provide you will the tools you need to brand your calls correctly (and consistently) with the Skype experience. -

SPC210NC/00 Philips Webcam
Philips Webcam CIF CMOS SPC210NC Start Video Chatting Stay in touch with friends and family for free with this superbly simple webcam. It is the best combination of quality and price and is perfect for using with Skype, MSN or any other free instant messenger service. High-quality photos and video • Smooth image with 30 frames per second video • VGA resolution (640x480) for sharp images • Automatic Picture Optimiser for super image quality • Rotating lens for perfect aiming and natural images • Standalone external microphone gives you recording freedom Perfectly user-friendly • Installation manager for easy setup • Stable mount on any monitor, laptop or desk • Snapshot button lets you take great instant photos • Compatible with MSN, Skype and other free messaging services • Compatible with all available imaging software Webcam SPC210NC/00 CIF CMOS Specifications Highlights Video & snapshot capturing • RAM memory: 128 MB RAM 30 frames per second video •Sensor: CMOS •Sound card Sit back and enjoy superior viewing with 30 frames • Sensor resolution: QVGA • USB: Free USB port per second video. This gives you smoother video • Video resolution: QVGA • Internet connection images and a better all-round video chatting • Snapshot resolution: QVGA • Hard disk space: 200 MB experience. • Interpolated snapshot res.: VGA • CD-ROM or DVD-ROM Drive • Max. frame rate: 30 fps VGA resolution • Lens: f: 6 mm, F2.8, D42° Connectivity VGA (640 x 480) means around 300,000 pixels are • White balance: 2600 – 7600 k • Cable length: 1.5 m used to create the total image. This VGA resolution • Min. illuminance: < 10 lux • PC Link: USB 1.1 ensures sharp images for use in documents, • Colour depth: 24 bit webpages and e-mails. -

Skype Facetime
Solution Bandwidth Multi-point Screen Share OS Platform/ Record Video Software Resolution Protocol Cost System Option ------------ Requirements Audio Webcam/Camera Resolution Skype 1.5Mbps up/down 10 participants Yes Mac OSX 10.5+, Yes - via Yes Up to 720p30 max Non- Basic - Free for HD quality max; must have Win 7/Vista/XP, 3rd party ----------------------------- standard/ 1 Skype One to one; (32/64 bit), Linux, programs Video one to HD webcam required VP8 Premium - 500kbps Premium Group screen iPad, iPhone, one only via for HD quality Pay up/down minimum account sharing must Android mobile for SD quality have 1 Skype devices For best quality, Premium Core 2 Duo Group Calling only up to 5 account 1.8Ghz+ Audio only in 2Mbps down/ participants 1GB RAM group calls 512Mbps up recommended Desktop/ Win – DirectX minimum File sharing v9.0+, Mac-QuickTime File/Photo sharing only via mobile FaceTime 1Mbps up/down No No Mac OSX 10.6.6+ No Yes Up to 720p max Based on Free on newer for HD quality iOS 6.0.1+ ----------------------------- H.264, Apple iPhone 4+, iPad FaceTime HD camera AAC, SIP, products 384Kbps for SD 2+, iPod Touch 4th (720p) on newest RTP, quality Gen+ iMacs/ SRTP Available at Macbook Pros/ App Store for Via Wi-Fi or Intel processors iPhone5 $0.99 Cellular data only connection if 1 GB RAM Both participants supported by need FaceTime HD carrier Requires Apple ID camera for HD quality and FT client side certificate 1280 X 1024 or 640 X 480 with iSight Mac OSX 10.5.8+, Microsoft 1.2Mbps up / Up to 250 Yes Yes Yes Up to 720p30 with -

SPC325NC/27 Philips Webcam
Philips Webcam CIF CMOS SPC325NC Start chatting on Skype The perfect Skype webcam! It’s easy to use, takes great images and has a headset for echo- free chatting. You can also email, manage and archive snapshots and video clips with a couple of clicks. Video chatting has never been so easy. One-to-one video chatting on Skype • Multimedia headset and head mic for best sound quality • 30 frames per second video at Skype resolutions • VGA resolution (640x480) for sharp images • Automatic Picture Optimizer for super image quality • Rotating lens for perfect aiming and natural images Perfectly user-friendly • Stable mount on any monitor laptop or desk • Installation manager for easy set-up • Perfectly compatible with Skype and other messaging services • Compatible with all available imaging software • Snapshot button lets you take great instant photos • Take, archive and manage images & V-mails with VLounge • VLounge QuickLaunch button for instant operation Webcam SPC325NC/27 CIF CMOS Specifications Product highlights Video & snapshot capturing • Hard disk space: 200 MB Multimedia headset included • Sensor: CMOS • CD-ROM or DVD-ROM Drive Included with your webcam is a Philips multimedia headset. • Sensor resolution: QVGA The head mic ensures optimum sound quality and • Video resolution: QVGA Connectivity comfortable use. • Snapshot resolution: QVGA • Cable length: 1.5 m • Interpolated snapshot res.: VGA • PC Link: USB 1.1 30 frames per second skype • Max. frame rate: 30 fps With a 30 frames per second you will enjoy natural-looking • Lens: f: 6 mm, F2.8, D42° Dimensions and full motion video calls without jumpy images. This is the • White balance: 2600 – 7600 k • Product dimensions (W x H x D): same refresh rate that Skype uses and makes video • Min.