IM Security Documentation on Page Vi
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
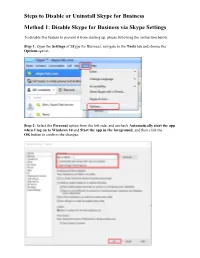
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

Symmetric Asynchronous Ratcheted Communication with Associated Data
Symmetric Asynchronous Ratcheted Communication with Associated Data B Hailun Yan( ) and Serge Vaudenay Ecole´ Polytechnique F´ed´erale de Lausanne (EPFL), Lausanne, Switzerland {hailun.yan,serge.vaudenay}@epfl.ch Abstract. Following up mass surveillance and privacy issues, modern secure communication protocols now seek strong security, such as forward secrecy and post-compromise security, in the face of state exposures. To address this problem, ratcheting was thereby introduced, widely used in real-world messaging protocols like Signal. However, ratcheting comes with a high cost. Recently, Caforio et al. proposed pragmatic construc- tions which compose a weakly secure “light” protocol and a strongly secure “heavy” protocol, in order to achieve the so-called ratcheting on demand. The light protocol they proposed has still a high complexity. In this paper, we prove the security of the lightest possible proto- col we could imagine, which essentially encrypts then hashes the secret key. We prove it without any random oracle by introducing a new secu- rity notion in the standard model. Our protocol composes well with the generic transformation techniques by Caforio et al. to offer high security and performance at the same time. 1 Introduction A classic communication model usually assumes that the endpoints are secure while the adversary is on the communication channel. However, protocols in recent messaging applications are secured with end-to-end encryption due to the prevalence of malware and system vulnerabilities. They attempt to enable secure communication services by regularly updating (ratcheting) the encryption key. One notable example of ratcheting is the Signal protocol [14] by Open Whisper Systems with its double-ratchet algorithm. -

2012 07 26 Letter to Skype
! Privacy International 46 Bedford Row London WC1R 4LR United Kingdom +44 (0) 20 7242 2836 @privacyint UK Charity No. 1147471 Friday, 27 July 2012 Dear Mr Bates, I am writing to request further information about the privacy implications of recent developments at Skype, as reported in the Washington Post.1 We were delighted to read that you believe these reports are “inaccurate” and“could mislead the Skype community”, and that you want to “clear this up”. 2 The growth of Skype since its launch in 2003 to become the world's leading VoIP provider has been driven by service that is affordable, high quality and, above all, secure. From an early stage in its development, Skype has assured its customers of the security of their communications. Press releases and product descriptions from 2005 boast of "end-to-end encryption for superior privacy" that "nobody can intercept".3 In 2008, a spokesperson reassured users that “[w]e have not received any subpoenas or court orders asking us to perform a live interception or wiretap of Skype-to-Skype communications” and “[i]n any event, because of Skype's peer-to-peer architecture and encryption techniques, Skype would not be able to comply with such a request”.4 In short, a promise was made to Skype customers that the privacy of their conversations and file transfers would be protected. As I'm sure you know, among Skype's 663 million registered users across the world are human rights defenders and pro-democracy activists living under autocratic regimes. In an environment where most channels of communication -

Secure Messaging1
SoK: Secure Messaging1 Nik Unger∗, Sergej Dechandy Joseph Bonneauzx, Sascha Fahl{, Henning Perl{ Ian Goldberg∗, Matthew Smithy ∗ University of Waterloo, y University of Bonn, z Stanford University, x Electronic Frontier Foundation, { Fraunhofer FKIE Abstract—Motivated by recent revelations of widespread state insecure ways. However, as will become clear over the course surveillance of personal communication, many products now of this paper, the academic research community is also failing claim to offer secure and private messaging. This includes both a to learn some lessons from tools in the wild. large number of new projects and many widely adopted tools that have added security features. The intense pressure in the past two Furthermore, there is a lack of coherent vision for the future years to deliver solutions quickly has resulted in varying threat of secure messaging. Most solutions focus on specific issues models, incomplete objectives, dubious security claims, and a lack and have different goals and threat models. This is com- of broad perspective on the existing cryptographic literature on pounded by differing security vocabularies and the absence of secure communication. a unified evaluation of prior work. Outside of academia, many In this paper, we evaluate and systematize current secure messaging solutions and propose an evaluation framework for products mislead users by advertising with grandiose claims their security, usability, and ease-of-adoption properties. We con- of “military grade encryption” or by promising impossible sider solutions from academia, but also identify innovative and features such as self-destructing messages [7]–[10]. The recent promising approaches used “in the wild” that are not considered EFF Secure Messaging Scorecard evaluated tools for basic by the academic literature. -

VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center
VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center Table of Contents Click on any of the titles below to be navigated to that section SLI POLICIES ........................................................................................................................... 1 USING TIGERZONE TO YOUR ADVANTAGE .............................................................................. 1 ONLINE MEETING PLATFORMS ............................................................................................... 2 ONLINE BROADCASTING PLATFORMS ..................................................................................... 3 ONLINE CHAT PLATFORMS ..................................................................................................... 3 VIDEO CONFERENCE TIPS (for Zoom) ...................................................................................... 4 VIRTUAL ENGAGEMENT IDEAS ............................................................................................... 5 VIRTUAL ENTERTAINMENT ..................................................................................................... 6 SLI POLICIES During Phase 1 there are to be NO IN PERSON STUDENT EVENTS. This applies to events both ON and OFF campus. If your organization is found to be hosting in person events you will be given ONE warning from Student Leadership & Involvement. If your organization is found to be hosting student events a second time your organization will be suspended for the remainder of the 2020-2021 -

Microsoft Skype for Business Deployment Guide
Microsoft Skype for Business Deployment Guide Multimedia Connector for Skype for Business 8.5.0 3/8/2020 Table of Contents Multimedia Connector for Skype for Business Deployment Guide 4 Architecture 6 Paired Front End Pools 9 Federation Platform with Microsoft Office 365 Cloud 12 Managing T-Server and UCMA Connectors 14 Prerequisites 16 Provisioning for UCMA Connectors 22 Using Telephony Objects 24 Managing UCMA Connectors 28 Managing T-Server 33 Upgrading Multimedia Connector for Skype For Business 36 Configuring Skype for Business Application Endpoints 37 Configuring Skype for Business User Endpoints 38 High-Availability Deployment 39 Performance 45 Managing Workspace Plugin for Skype for Business 46 Using Workspace Plugin for Skype for Business 51 Handling IM Transcripts 60 Supported Features 61 Alternate Routing 62 Call Monitoring 63 Call Supervision 64 Calling using Back-to-Back User Agent 70 Conference Resource Pools 77 Disable Lobby Bypass 80 Emulated Agents 82 Emulated Ringing 85 Handling Direct Calls 86 Handling Pass-Through Calls 89 Hiding Sensitive Data 91 IM Treatments 93 IM Suppression 94 Music On Hold 97 No-Answer Supervision 98 Presence 99 Remote Recording 103 Remote Treatments 110 Transport Layer Security 112 UTF-8 Encoding 114 Supported Media Types 116 T-Library Functionality 120 Attribute Extensions 124 Hardware Sizing Guidelines and Capacity Planning 130 Error Messages 132 Known Limitations and Workarounds 134 Multimedia Connector for Skype for Business Deployment Guide Multimedia Connector for Skype for Business Deployment Guide Welcome to the Multimedia Connector for Skype for Business Deployment Guide. This Deployment Guide provides deployment procedures and detailed reference information about the Multimedia Connector for Skype for Business as a product, and its components: T-Server, UCMA Connector, and Workspace Plugin. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

CCIA Comments in ITU CWG-Internet OTT Open Consultation.Pdf
CCIA Response to the Open Consultation of the ITU Council Working Group on International Internet-related Public Policy Issues (CWG-Internet) on the “Public Policy considerations for OTTs” Summary. The Computer & Communications Industry Association welcomes this opportunity to present the views of the tech sector to the ITU’s Open Consultation of the CWG-Internet on the “Public Policy considerations for OTTs”.1 CCIA acknowledges the ITU’s expertise in the areas of international, technical standards development and spectrum coordination and its ambition to help improve access to ICTs to underserved communities worldwide. We remain supporters of the ITU’s important work within its current mandate and remit; however, we strongly oppose expanding the ITU’s work program to include Internet and content-related issues and Internet-enabled applications that are well beyond its mandate and core competencies. Furthermore, such an expansion would regrettably divert the ITU’s resources away from its globally-recognized core competencies. The Internet is an unparalleled engine of economic growth enabling commerce, social development and freedom of expression. Recent research notes the vast economic and societal benefits from Rich Interaction Applications (RIAs), a term that refers to applications that facilitate “rich interaction” such as photo/video sharing, money transferring, in-app gaming, location sharing, translation, and chat among individuals, groups and enterprises.2 Global GDP has increased US$5.6 trillion for every ten percent increase in the usage of RIAs across 164 countries over 16 years (2000 to 2015).3 However, these economic and societal benefits are at risk if RIAs are subjected to sweeping regulations. -

Investigating Mobile Messaging Security
Technische Universitat¨ Munchen¨ Department of Informatics Interdisciplinary Project in Electrical Engineering Investigating Mobile Messaging Security Elias Hazboun Technische Universitat¨ Munchen¨ Department of Informatics Interdisciplinary Project in Electrical Engineering Investigating Mobile Messaging Security Untersuchung von Mobile Messaging Sicherheit Author Elias Hazboun Supervisor Prof. Dr.-Ing. Georg Carle Advisor Dr. Matthias Wachs, Quirin Scheitle Date April 27, 2016 Informatik VIII Chair for Network Architectures and Services Abstract In this report we document our work in analyzing the security of a selection of mobile messaging apps. Focusing on network based security, we studied traffic generated by the apps to gain an understanding of the current state of applying encryption and authentication protocols. Our findings show a positive trend in security with developers steadily improving security with newer app updates partly due to the increased scrutiny from the community and academia. Although not all apps analyzed had perfect state of the art security properties, none have shown any major vulnerabilities exploited by normal adversaries. It was also evident that only one app - namely TextSecure - is using the industry standard TLS for server-client authentication and security while others have opted for custom made protocols and algorithms. I Contents 1 Introduction 1 1.1 Research Question . .2 1.2 Outline . .2 2 Background and Related Work 3 2.1 Methodology . .3 2.1.1 App Selection . .3 2.1.2 Approach . .3 2.2 Definition of Security Concepts . .4 2.2.1 Layers of Encryption . .4 2.2.2 Transport Layer Security Protocol (TLS) . .5 2.2.3 Perfect Forward Secrecy (PFS) . .5 2.2.4 Asynchronous Messaging Security . -

Windows Messenger Live Msn Download
Windows messenger live msn download Windows Live Messenger latest version: See. Hear. Share. Instantly.. Windows Live Messenger previously known as MSN Messenger, was renamed as part of. MSN Messenger is an instant messaging program that lets you send instant messages to your friends, and much more. Previously known as MSN Messenger, Windows Live Messenger is Microsoft's answer to instant messaging. While largely the same as its predecessor. Windows Live Messenger free download. on their MSN or Hotmail account, as the integration with the email accounts can be. Mobile and web: Using a public computer without Messenger? No problem! You can chat on the web from Windows Live Hotmail or use. Share photos: Look at photos together, right in the conversation window and Messenger tells you when people you know post new photos on Windows Live. Microsoft Windows live messenger free Download Link: Latest Version. Old Version of MSN (Live) Messenger. Website. Developer. Microsoft Corporation. Latest Version. Windows. Messenger, which offers the user the same functionalities as Windows Live Messenger. Windows Live Messenger Final Deutsch: Der Windows Live Messenger, Nachfolger des MSN Messenger, in der Version: - vom How to Download and Install Windows Live Messenger. Windows Live Messenger is a great way to talk to people online. You can now have a personal picture. Windows 7 by default is installed without Windows Live Messenger. So to get it, we will need to download and install it. select, like setting Bing as the default search provider and setting MSN as your browser home page. is a free, personal email service from Microsoft. -

Zfone: a New Approach for Securing Voip Communication
Zfone: A New Approach for Securing VoIP Communication Samuel Sotillo [email protected] ICTN 4040 Spring 2006 Abstract This paper reviews some security challenges currently faced by VoIP systems as well as their potential solutions. Particularly, it focuses on Zfone, a vendor-neutral security solution developed by PGP’s creator, Phil Zimmermann. Zfone is based on the Z Real-time Transport Protocol (ZRTP), which is an extension of the Real-time Transport Protocol (RTP). ZRTP offers a very simple and robust approach to providing protection against the most common type of VoIP threats. Basically, the protocol offers a mechanism to guarantee high entropy in a Diffie- Hellman key exchange by using a session key that is computed through the hashing several secrets, including a short authentication string that is read aloud by callers. The common shared secret is calculated and used only for one session at a time. However, the protocol allows for a part of the shared secret to be cached for future sessions. The mechanism provides for protection for man-in-the-middle, call hijack, spoofing, and other common types of attacks. Also, this paper explores the fact that VoIP security is a very complicated issue and that the technology is far from being inherently insecure as many people usually claim. Introduction Voice over IP (VoIP) is transforming the telecommunication industry. It offers multiple opportunities such as lower call fees, convergence of voice and data networks, simplification of deployment, and greater integration with multiple applications that offer enhanced multimedia functionality [1]. However, notwithstanding all these technological and economic opportunities, VoIP also brings up new challenges. -

Cryptographic Control Standard, Version
Nuclear Regulatory Commission Office of the Chief Information Officer Computer Security Standard Office Instruction: OCIO-CS-STD-2009 Office Instruction Title: Cryptographic Control Standard Revision Number: 2.0 Issuance: Date of last signature below Effective Date: October 1, 2017 Primary Contacts: Kathy Lyons-Burke, Senior Level Advisor for Information Security Responsible Organization: OCIO Summary of Changes: OCIO-CS-STD-2009, “Cryptographic Control Standard,” provides the minimum security requirements that must be applied to the Nuclear Regulatory Commission (NRC) systems which utilize cryptographic algorithms, protocols, and cryptographic modules to provide secure communication services. This update is based on the latest versions of the National Institute of Standards and Technology (NIST) Guidance and Federal Information Processing Standards (FIPS) publications, Committee on National Security System (CNSS) issuances, and National Security Agency (NSA) requirements. Training: Upon request ADAMS Accession No.: ML17024A095 Approvals Primary Office Owner Office of the Chief Information Officer Signature Date Enterprise Security Kathy Lyons-Burke 09/26/17 Architecture Working Group Chair CIO David Nelson /RA/ 09/26/17 CISO Jonathan Feibus 09/26/17 OCIO-CS-STD-2009 Page i TABLE OF CONTENTS 1 PURPOSE ............................................................................................................................. 1 2 INTRODUCTION ..................................................................................................................