For Establishment of Haridwar Kumbh Mela
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Monthly Current Affairs Consolidation (March 2021) – Part II
Current Affairs (CONSOLIDATION) MARCH 2021 (PART – II) Drishti, 641, First Floor, Dr. Mukherjee Nagar, Delhi-110009 Phone: 87501 87501, WhatsApp: 92058 85200, IVR: 8010-440-440 Email: [email protected] Contents Polity and Governance ........................................................................................................1 zz Pradhan Mantri Awaas Yojana-Gramin .................................................................................................................. 1 zz Shifting Health to the Concurrent List ................................................................................................................... 2 zz Electoral Bonds ....................................................................................................................................................... 4 zz Anti-Corruption Strategies ...................................................................................................................................... 5 zz MPLAD Scheme ...................................................................................................................................................... 6 zz Government of NCT of Delhi (Amendment) Bill, 2021 .......................................................................................... 7 zz Damages Recovery Bill ........................................................................................................................................... 8 zz Supplementary Demand for Grants .................................................................................................................... -

Office of Mela Adhikari Kumbh, Mela Control Bhawan, C.C.R., Har Ki Pauri, Haridwar
Office of Mela Adhikari Kumbh, Mela Control Bhawan, C.C.R., Har Ki Pauri, Haridwar COMPETITION FOR LOGO DESIGN OF KUMBH MELA 2021 Haridwar 24th December 2019 The Government of Uttarakhand proposes to have a Logo for the Kumbh Mela- 2021 to be selected through open public competition. Accordingly, all Interested persons / parties (both Professional artists and Non-professionals) are hereby invited to participate in a Competition for design of the ‘Logo for Kumbh Mela-2021’. Winner will be awarded with appropriate prize money. Submission of Entries: Interested persons may send their entries via E-mail latest by 1800 hours on 25th January 2020. Entries received via any other medium and after the stipulated time shall not be entertained. The entries should be sent with subject line in submission E-Mail “Haridwar Kumbh Mela-2021 Logo Competition”. The entry should be accompanied by a brief explanation of the Design in Hindi & English Both and how it best symbolizes the Kumbh Mela-2021 and also the bio-data of the applicant. The guidelines for preparing entries, other conditions are available on the website of the Mela Adhikari (Kumbh), Haridwar https://haridwarkumbhmela2021.com & NIC Haridwar https://haridwar.nic.in Deepak Rawat, Mela Adhikari (Kumbh), Haridwar Kumbh Mela, 2021 Logo Design Competition Overview The Kumbh Mela is one of the world's largest religious gatherings. The next Kumbh Mela is scheduled to be held in Haridwar from January 2021 to April 2021. Nearly 15 crore Pilgrims are expected to visit the holy city of Haridwar during the Mela. In addition to Indian Pilgrims, the Kumbh Mela receives visitors from across the globe. -

At Season Cover Page 2019
Treasures of India Dear Associate, Greetings from A. T. Seasons & Vacations Travel Pvt. Ltd.! We are New Delhi, India based Govt. of India, Ministry of Tourism recognized Destination Management Company and are committed to offer you a wide range of services at the best prices, starting from arrival to your safe departure from India! We are also well equipped to facilitate you with the Meet & AMARESH TIWARI Assistance services at Airport, Airport transfers, Accommoda- Managing Director tions, Transportations, Multi-language guides, Interpreter, sightseeing options, Exciting Tours of most exotic and sought after destinations, Foreign Exchange Facilities, etc. We well understand that customers look up to us to obtain the best value for their money spent – to be available if any problem arises, to ensure quality accommodations and transportations for best comfort and conveniences. And, we deliver what we promise with no compromise to our commitments made! Our philosophy is to make journey of our travelers a memorable one for lifetime, keeping in mind there purpose of travel. On behalf of my team, I assure you of the highest services standards in serving all the segments of the travelers. Thank you. Amaresh Tiwari Managing Director Colourful Rajasthan Rajasthan is a colorful mixture of forts, palaces, diverse cultures, delicious cuisines and warm people, set amidst a rugged yet inviting landscape. It is a land that has inspires countless visitors. In Rajasthan you will ind every hue in Nature's colour - the red sands, the blue of royalty, the pink cities or the amber sunsets. Sight and sounds that are far removed from any city. -

Gidni 57 Kumbh Mela 2013. Religious Rituals And
Section – Political Sciences GIDNI KUMBH MELA 2013. RELIGIOUS RITUALS AND PERFORMANCE FACING MEDIA COLONIALISM. Traian Penciuc, Assist. Prof., PhD, University of Arts, Târgu-Mureș Abstract: Kumbh Mela is a pan-Indian religious gathering. It is considered by Hindus to be the oldest religious festival known in the World History. Undoubted, it is the biggest: according to the Indian officials more than 100 millions people attended the 2013 Kumbh Mela. The devotee’s main purpose is to acquire a strong purification of karma through bathing in the Ganges River in some auspicious days. But Kumbh Mela has been always a religious fair also, a place where believers are searching for their gurus and “holy men” are gathering their followers flock. Anything goes here and everything is transformed in a performance: lepers, fakirs laying on barbed wire, sadhus reciting the puranas by hard, yogis meditating – all are performing in public forming what BBC has named “the greatest show on Earth”. In the last two decades, media attention and aggression on the Mela festival has raised, due to his exotic potential to the Western audience, but also because of the increased usage of media means by the religious leaders and organisations in their communication and advertising. Today Kumbh Mela is under media siege. Televisions, documentary producers, and tourists, eager to capture every moment, aggress pilgrims’ privacy. Monastic congregations’ use media for advertising and, even the pilgrims and sadhus themselves, capture memorable religious moments on their smart phones. The paper is presenting the influence of the global media intrusion on this archaic event in the purpose to appreciate in what aspects, and how far, the deep religious mentality and mind of the Hindu believer has been changed. -

A Counterview to Lancet's Editorial “India's COVID-19 Emergency
!"#$%&'()*+,,'-#."/0) !"#$%&'()*+(,"'$"-.&#('/0"12+'$)+.3"45&2+.60"7895:;<="(>()?(&#@AB" C%D3+0E(2"$&"F.@"GB"HIH<" !"#$%&'"()$*#+( ! "#$$%&'%(!)%*%)%+,%-!! 1'#2$3)45)67879:5)!)%+;-#'"<$'=)#+)>.-%'#?@)AB$#+"$.&)CD-B$.E@)*FGDHI9J)','"K'-%/L5)) HFD0)2##M@0((B+$5+"K(9859N7OJ(B'M+@$#+-%'I99JP8)) ) .%/01)(&-!! *FGDHI9J3)B'.#2@3)@'%+-B)=.<'D-B$.3)@;M'"@M"'.B'"3)K+<'"-,'-#)"'@M+-@'3)K'-+,$%)%+B$-K) ) 23&')4,'-! !"#"$%&'()*+$#"%),-.&/01"2)+$)"2/%34/+&()56$2/+70)89:6;<=>)"?"4@"$#'AB)C$)"2/%34/+&)/0) "$%/%&"2)%3).")3,/$/3$+%"2().-%)/%)/0)"D,"#%"2)%3).").+0"2)3$)$-+$#"2)+$+&'0/0)3E)0#/"$%/E/#) E+#%0)%1+$)?"4"&')%3F/$@)%3)+),3,-&+4)?"2/+)$+44+%/G"B)H+G/$@).""$)%4+#I/$@)89:6;<=>)/$) -4.+$)#"$%4"0)+$2)."/$@)3$)@43-$2)J"43)2-4/$@)6$2/+K0)/$%4+<F+G"),"4/32()6)$3%/#")0"G"4+&) /$+##-4+#/"0)+$2)/$#3$0/0%"$#/"0)1"4"B)L')+4%/#&")/0).+0"2)3$)+22/%/3$+&)E+#%0)+$2)0,+%/3< %"?,34+&)+00"00?"$%)3E)89:6;<=>)-$E3&2/$@)/$)6$2/+)%3)3EE"4)#3-$%"4)+4@-?"$%0)3$)E/G")I"') +00"4%/3$0)/$)%1")*+$#"%K0)"2/%34/+&()$+?"&')M=N)O1")?'%1)+.3-%)4","+%"2)F+4$/$@0)3E)%1") 0"#3$2)F+G"()MPN)%1")Q-,"40,4"+2"4)"G"$%)%1"34')MRN)*"%1+&/%')+$2)@"$3?/#)#32/$@)3E)%1") 0"#3$2)F+G")G+4/+$%()MSN)T3G"4$?"$%K0)#3?,&+#"$#')+$2)/&&),4",+4"2$"00()+$2)MUN)8&+/?0)3E) -$2"4<4",34%/$@)3E)2"+%10B)6)F3-&2)"$#3-4+@")%1")4"+2"40)%3)%1"?0"&G"0)4"+2()E+#%<#1"#I) #&+/?0)+$2)#3-$%"4#&+/?0)%3)E34?)+$)/$E34?"2)3,/$/3$B) ) !<.$&.Q&')<$.)RS)T'"&$-)"'M+@$#+"/0)2##M@0((B+$5+"K(9859N7OJ(B'M+@$#+-%'I99JP8) R2$@)=+"U)$@)&$%'-@'B);-B'").)*"'.#$<')*+,,+-@)!##"$Q;#$+-)N58)D-#'"-.#$+-.&)>$%'-@')6**) TV)N58:)2##M@0((%"'.#$<'%+,,+-@5+"K(&$%'-@'@(Q/(N585) -

3.Hindu Websites Sorted Country Wise
Hindu Websites sorted Country wise Sl. Reference Country Broad catergory Website Address Description No. 1 Afghanistan Dynasty http://en.wikipedia.org/wiki/Hindushahi Hindu Shahi Dynasty Afghanistan, Pakistan 2 Afghanistan Dynasty http://en.wikipedia.org/wiki/Jayapala King Jayapala -Hindu Shahi Dynasty Afghanistan, Pakistan 3 Afghanistan Dynasty http://www.afghanhindu.com/history.asp The Hindu Shahi Dynasty (870 C.E. - 1015 C.E.) 4 Afghanistan History http://hindutemples- Hindu Roots of Afghanistan whthappendtothem.blogspot.com/ (Gandhar pradesh) 5 Afghanistan History http://www.hindunet.org/hindu_history/mode Hindu Kush rn/hindu_kush.html 6 Afghanistan Information http://afghanhindu.wordpress.com/ Afghan Hindus 7 Afghanistan Information http://afghanhindusandsikhs.yuku.com/ Hindus of Afaganistan 8 Afghanistan Information http://www.afghanhindu.com/vedic.asp Afghanistan and It's Vedic Culture 9 Afghanistan Information http://www.afghanhindu.de.vu/ Hindus of Afaganistan 10 Afghanistan Organisation http://www.afghanhindu.info/ Afghan Hindus 11 Afghanistan Organisation http://www.asamai.com/ Afghan Hindu Asociation 12 Afghanistan Temple http://en.wikipedia.org/wiki/Hindu_Temples_ Hindu Temples of Kabul of_Kabul 13 Afghanistan Temples Database http://www.athithy.com/index.php?module=p Hindu Temples of Afaganistan luspoints&id=851&action=pluspoint&title=H indu%20Temples%20in%20Afghanistan%20. html 14 Argentina Ayurveda http://www.augurhostel.com/ Augur Hostel Yoga & Ayurveda 15 Argentina Festival http://www.indembarg.org.ar/en/ Festival of -
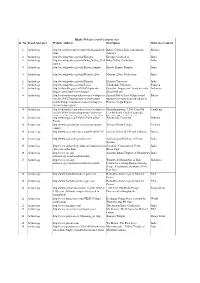
2.Hindu Websites Sorted Category Wise
Hindu Websites sorted Category wise Sl. No. Broad catergory Website Address Description Reference Country 1 Archaelogy http://aryaculture.tripod.com/vedicdharma/id10. India's Cultural Link with Ancient Mexico html America 2 Archaelogy http://en.wikipedia.org/wiki/Harappa Harappa Civilisation India 3 Archaelogy http://en.wikipedia.org/wiki/Indus_Valley_Civil Indus Valley Civilisation India ization 4 Archaelogy http://en.wikipedia.org/wiki/Kiradu_temples Kiradu Barmer Temples India 5 Archaelogy http://en.wikipedia.org/wiki/Mohenjo_Daro Mohenjo_Daro Civilisation India 6 Archaelogy http://en.wikipedia.org/wiki/Nalanda Nalanda University India 7 Archaelogy http://en.wikipedia.org/wiki/Taxila Takshashila University Pakistan 8 Archaelogy http://selians.blogspot.in/2010/01/ganesha- Ganesha, ‘lingga yoni’ found at newly Indonesia lingga-yoni-found-at-newly.html discovered site 9 Archaelogy http://vedicarcheologicaldiscoveries.wordpress.c Ancient Idol of Lord Vishnu found Russia om/2012/05/27/ancient-idol-of-lord-vishnu- during excavation in an old village in found-during-excavation-in-an-old-village-in- Russia’s Volga Region russias-volga-region/ 10 Archaelogy http://vedicarcheologicaldiscoveries.wordpress.c Mahendraparvata, 1,200-Year-Old Cambodia om/2013/06/15/mahendraparvata-1200-year- Lost Medieval City In Cambodia, old-lost-medieval-city-in-cambodia-unearthed- Unearthed By Archaeologists 11 Archaelogy http://wikimapia.org/7359843/Takshashila- Takshashila University Pakistan Taxila 12 Archaelogy http://www.agamahindu.com/vietnam-hindu- Vietnam -

Great Mahayogi Devraha Baba's Biography-His Divine Sports and Lilas
SHRI DEVRAHA BABA LILA DARSHAN GREAT MAHAYOGI DEVRAHA BABA’S BIOGRAPHY-HIS DIVINE SPORTS AND LILAS ORIGINALLY WRITTEN IN HINDI BY COMPILED AND PUBLISHED ON THE INTERNET BY TRANSLATED INTO ENGLISH BY MS/ HEENA A. KAPADIA (M.Sc., M.Phil) 1/168 SHRI DEVRAHA BABA LILA DARSHAN INDEX INDIA’S FUTURE SEER SAINT SHRI DEVRAHA BABA SARKAR ........................................................................ 7 BHAKTI BHAKT BHAGWANT GURU CHATURNAM VAPU EK ....................................................................... 10 INKE PADA VANDAN KIYE NASAI VIGHAN ANEK ......................................................................................... 10 CHAPTER 1 .................................................................................................................................................. 20 AN EPISODE RELATED TO INDIA’S FIRST PRESIDENT-DR RAJENDRA PRASAD ............................................ 20 CHAPTER 2 .................................................................................................................................................. 22 SPIRITUAL MESSAGE GIVEN BY HH MAHAYOGI DEVRAHA BABA TO INDIA’S FIRST MUSLIM PRESIDENT . 22 CHAPTER 3 .................................................................................................................................................. 25 THE OMNISCIENT MAYAYOGI HH DEVRAHA BABA AND A BRITISH SPY ..................................................... 25 CHAPTER 4 ................................................................................................................................................. -

SAMVAD संवाद Vasant Panchami Vik
SAMVAD संवाद Vasant Panchami Vik. Samvat 2077, Yugabda 5122 : 1 6February, 2021 : SM2022 (For Private Circulation only) 1. FESTIVALS: HARIDWAR KUMBH MELA 2021 Haridwar Kumbh Mela , the largest religious gathering of pilgrims on the earth witnesses millions of people including saints, sadhus, kalpavasis and people from all walks of life irrespective of their background, caste, creed and gender taking holy bath in the river. Generally it is held from Makar Sankranti to Chaitra Purnima (14 Jan – 27 April 2021 ) but the this year the period may be restricted due to Covid-19. Kumbh Mela is held every 4 years in rotation at the four holy places namely: Haridwar, Prayagraj, Ujjain and Nasik. The last Kumbh Mela at Haridwar in 2010 had witnessed approximately 8 crores pilgrims. This year , with all Covid-19 regulations in place, about 1 million pilgrims are expected to visit Haridwar daily. Kumbh 2021 is unique due to its astrological significance and will be organized one year earlier. 2. MOHAN BHAGWAT LAYS FOUNDATION OF SEWA SADAN PATNA RSS Sarsanghachalak Dr Mohan Bhagwat laid the humanity as foundation stone of ‘Sewa Sadan' that will his/her family. provide accommodation to patients visiting the The objective of premiere hospital AIIMS Patna on service should 11th February. The 'Sewa Sadan' will be con- be to make the structed by Dr Hedgewar Smarak Samiti, Bihar. society strong Union minister of state for health Ashwini and robust, so Choubey and Bihar health minister Mangal that others can also be able to do service." Pandey attended the function at Keshav Nagar Noted saint Jeeyar Swamy also addressed the on the outskirts of the city. -
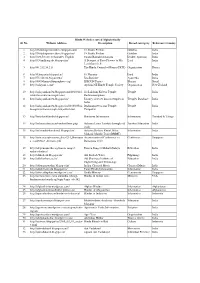
Hindu Websites Sorted Alphabetically Sl
Hindu Websites sorted Alphabetically Sl. No. Website Address Description Broad catergory Reference Country 1 http://18shaktipeetasofdevi.blogspot.com/ 18 Shakti Peethas Goddess India 2 http://18shaktipeetasofdevi.blogspot.in/ 18 Shakti Peethas Goddess India 3 http://199.59.148.11/Gurudev_English Swami Ramakrishnanada Leader- Spiritual India 4 http://330milliongods.blogspot.in/ A Bouquet of Rose Flowers to My Lord India Lord Ganesh Ji 5 http://41.212.34.21/ The Hindu Council of Kenya (HCK) Organisation Kenya 6 http://63nayanar.blogspot.in/ 63 Nayanar Lord India 7 http://75.126.84.8/ayurveda/ Jiva Institute Ayurveda India 8 http://8000drumsoftheprophecy.org/ ISKCON Payers Bhajan Brazil 9 http://aalayam.co.nz/ Ayalam NZ Hindu Temple Society Organisation New Zealand 10 http://aalayamkanden.blogspot.com/2010/11/s Sri Lakshmi Kubera Temple, Temple India ri-lakshmi-kubera-temple.html Rathinamangalam 11 http://aalayamkanden.blogspot.in/ Journey of lesser known temples in Temples Database India India 12 http://aalayamkanden.blogspot.in/2010/10/bra Brahmapureeswarar Temple, Temple India hmapureeswarar-temple-tirupattur.html Tirupattur 13 http://accidentalhindu.blogspot.in/ Hinduism Information Information Trinidad & Tobago 14 http://acharya.iitm.ac.in/sanskrit/tutor.php Acharya Learn Sanskrit through self Sanskrit Education India study 15 http://acharyakishorekunal.blogspot.in/ Acharya Kishore Kunal, Bihar Information India Mahavir Mandir Trust (BMMT) 16 http://acm.org.sg/resource_docs/214_Ramayan An international Conference on Conference Singapore -

Haridwar 2021 Kumbh Mela.Cdr
HaHaridwaridwarr 2021 Kumbh Mela Haridwar 2 Kumbh Mela HaHaridwaridwarr 22002211 KKumbhumbh MelaMela 14 JANUARY - 26 MAY There is no better occasion to visit India than during Kumbh Mela which is not only the greatest Indian Festival but is also the largest gathering of people for the spiritual benefit and attracts millions of devotees from all over the world who assemble at Haridwar, once of the most sacred places for Hindus which literally means Gateway to God situated in foothills of Himalayas. In Rishikesh (the nearby town), Ganges emerges from mighty Himalayas and flows through Gangetic plains for rest of its journey. The place is also famous in the world for Beatles Ashram where the world-famous rock bank group stayed to learn Transcendental Meditation. The festival is once-in-a-lifetime experience for every visitor who is curious about Hindu religion and philosophy. The whole atmosphere during Kumbh Mela is bursting with sounding bells, chanting of Vedic hymns and mantras, procession of Naga Sadhus and other Akhaaras on camels and elephants in their gold and silver chariots being pulled by devotees, as they display their strength and skills is a pure enchantment for the soul. Kumbh has different significance for different people. It depends on how one wants to perceive it. For those, looking for spirituality, it is a place which is divine with all spiritual gurus around you. For the travellers, it is an experience to come across the largest gathering of like-minded people not only from India but around the world. For photographers, it offers an opportunity to capture images of various moods, attires and faith of people which they cannot find anywhere else. -
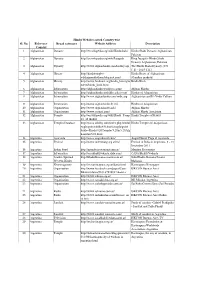
3.Hindu Websites Sorted Country Wise
Hindu Websites sorted Country wise Sl. No. Reference Broad catergory Website Address Description Country 1 Afghanistan Dynasty http://en.wikipedia.org/wiki/Hindushahi Hindu Shahi Dynasty Afghanistan, Pakistan 2 Afghanistan Dynasty http://en.wikipedia.org/wiki/Jayapala King Jayapala -Hindu Shahi Dynasty Afghanistan, Pakistan 3 Afghanistan Dynasty http://www.afghanhindu.com/history.asp The Hindu Shahi Dynasty (870 C.E. - 1015 C.E.) 4 Afghanistan History http://hindutemples- Hindu Roots of Afghanistan whthappendtothem.blogspot.com/ (Gandhar pradesh) 5 Afghanistan History http://www.hindunet.org/hindu_history/m Hindu Kush odern/hindu_kush.html 6 Afghanistan Information http://afghanhindu.wordpress.com/ Afghan Hindus 7 Afghanistan Information http://afghanhindusandsikhs.yuku.com/ Hindus of Afaganistan 8 Afghanistan Information http://www.afghanhindu.com/vedic.asp Afghanistan and It's Vedic Culture 9 Afghanistan Information http://www.afghanhindu.de.vu/ Hindus of Afaganistan 10 Afghanistan Organisation http://www.afghanhindu.info/ Afghan Hindus 11 Afghanistan Organisation http://www.asamai.com/ Afghan Hindu Asociation 12 Afghanistan Temple http://en.wikipedia.org/wiki/Hindu_Temp Hindu Temples of Kabul les_of_Kabul 13 Afghanistan Temples Database http://www.athithy.com/index.php?modul Hindu Temples of Afaganistan e=pluspoints&id=851&action=pluspoint &title=Hindu%20Temples%20in%20Afg hanistan%20.html 14 Argentina Ayurveda http://www.augurhostel.com/ Augur Hostel Yoga & Ayurveda 15 Argentina Festival http://www.indembarg.org.ar/en/ Festival of