Defense Suppression: Building Some Operational Concepts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

+P+-+K+- +-+-+-+- B -+-+P+-+ W -+-+-+-+ Zlw-+P+R +-+-+-Z- P+-+N+Q+ P+-+-+-+ +-+-+-+- Z-+K+-+- -+-+-TP+ Kwqs-Z-S +-+-+RM- +-+-+-+
Contents Symbols 4 Introduction 5 Part 1: The Basics 1 Pin 7 2 Deflection 16 3 Overload 23 4 Decoy 28 5 Double Attack 36 6 Knight Fork 44 7 Discovered Attack 50 8 Clearance 56 9 Obstruction 64 10 Removing the Defender 71 11 The Power of the Pawn 77 12 Back-Rank Mate 85 13 Stalemate 91 14 Perpetual Check and Fortresses 96 Part 2: Advanced Tactics 15 f7: Weak by Presumption 103 16 The Vulnerable Rook’s Pawn 111 17 Attacking the Fianchetto 118 18 The Mystery of the Opposite-Coloured Bishops 125 19 Chess Highways: Open Files 131 20 Trapping a Piece 141 21 Practice Makes Perfect 149 Solutions 158 Index of Players 188 Index of Composers 191 KNIGHT FORK 6 Knight Fork The knight is considered to be the least powerful White is now a queen and two rooks down – piece in chess (besides the pawn, of course). As a deficit of approximately 19 ‘pawns’. His only the great world champion Jose Raul Capablanca remaining piece is a knight. But a brave one... taught us, the other minor piece, the bishop, is 3 Ìe3+ Êf6 4 Ìxd5+ Êf5 5 Ìxe7+ Êf6 6 better in 90% of cases. However, due to its spe- Ìxg8+ (D) cific qualities the knight is a tremendously dan- gerous piece. It is nimble and its jumps can be -+-+-+N+ quite shocking. That is why a double attack by a +-+-+p+- knight is usually distinguished from other dou- B ble attacks and called a fork. -+-+nm-M +-+-z-+- A single knight may cause incredible dam- age in the right circumstances: -+-+-+-+ +-+-+PZ- -+-+-+q+ -+-+-+-+ +-+r+p+- +-+-+-+- W -+N+nm-M +-+rz-+- The knight has managed to remove most of Black’s army. -

The Wangling Wizards the Chess Problems of the Warton Brothers
The Wangling Wizards The chess problems of the Warton brothers Compiled by Michael McDowell ½ û White to play and mate in 3 British Chess Problem Society 2005 The Wangling Wizards Introduction Tom and Joe Warton were two of the most popular British chess problem composers of the twentieth century. They were often compared to the American "Puzzle King" Sam Loyd because they rarely composed problems illustrating formal themes, instead directing their energies towards hoodwinking the solver. Piquant keys and well-concealed manoeuvres formed the basis of a style that became known as "Wartonesque" and earned the brothers the nickname "the Wangling Wizards". Thomas Joseph Warton was born on 18 th July 1885 at South Mimms, Hertfordshire, and Joseph John Warton on 22 nd September 1900 at Notting Hill, London. Another brother, Edwin, also composed problems, and there may have been a fourth composing Warton, as a two-mover appeared in the August 1916 issue of the Chess Amateur under the name G. F. Warton. After a brief flourish Edwin abandoned composition, although as late as 1946 he published a problem in Chess . Tom and Joe began composing around 1913. After Tom’s early retirement from the Metropolitan Police Force they churned out problems by the hundred, both individually and as a duo, their total output having been estimated at over 2600 problems. Tom died on 23rd May 1955. Joe continued to compose, and in the 1960s published a number of joints with Jim Cresswell, problem editor of the Busmen's Chess Review , who shared his liking for mutates. Many pleasing works appeared in the BCR under their amusing pseudonym "Wartocress". -

Шахматных Задач Chess Exercises Schachaufgaben
Всеволод Костров Vsevolod Kostrov Борис Белявский Boris Beliavsky 2000 Шахматных задач Chess exercises Schachaufgaben РЕШЕБНИК TACTICAL CHESS.. EXERCISES SCHACHUBUNGSBUCH Шахматные комбинации Chess combinations Kombinationen Часть 1-2 разряд Part 1700-2000 Elo 3 Teil 1-2 Klasse Русский шахматный дом/Russian Chess House Москва, 2013 В первых двух книжках этой серии мы вооружили вас мощными приёмами для успешного ведения шахматной борьбы. В вашем арсенале появились двойной удар, связка, завлечение и отвлечение. Новый «Решебник» обогатит вас более изысканным тактическим оружием. Не всегда до короля можно добраться, используя грубую силу. Попробуйте обхитрить партнёра с помощью плаща и кинжала. Маскируйтесь, как разведчик, и ведите себя, как опытный дипломат. Попробуйте найти слабое место в лагере противника и в нужный момент уничтожьте защиту и нанесите тонкий кинжальный удар. Кстати, чужие фигуры могут стать союзниками. Умелыми манёврами привлеките фигуры противника к их королю, пускай они его заблокируют так, чтобы ему, бедному, было не вздохнуть, и в этот момент нанесите решающий удар. Неприятно, когда все фигуры вашего противника взаимодействуют между собой. Может, стоить вбить клин в их порядки – перекрыть их прочной шахматной дверью. А так ли страшна атака противника на ваши укрепления? Стоит ли уходить в глухую оборону? Всегда ищите контрудар. Тонкий промежуточный укол изменит ход борьбы. Не сгрудились ли ваши фигуры на небольшом пространстве, не мешают ли они друг другу добраться до короля противника? Решите, кому всё же идти на штурм королевской крепости, и освободите пространство фигуре для атаки. Короля всегда надо защищать в первую очередь. Используйте это обстоятельство и совершите открытое нападение на него и другие фигуры. И тогда жернова вашей «мельницы» перемелют всё вражеское войско. -
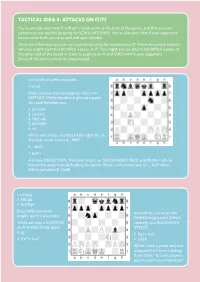
TACTICAL IDEA 4: ATTACKS on F7/F2
TACTICAL IDEA 4: ATTACKS ON f7/f2 You’ve already seen that f7 is Black’s weak point at the start of the game, and that you can sometimes win quickly by going for SCHOLAR’S MATE. You’ve also seen that if your opponent knows what to do you may well end up in trouble. There are other ways you can win quickly by using the weakness on f7. There are several reasons why you might want to SACRIFICE a piece on f7. You might also be able to SACRIFICE a piece at the other end of the board in order to capture on f7 and CHECKMATE your opponent. Some of the tactics are quite complicated. Let’s look at a few examples. 1. e4 c5 Black chooses the very popular SICILIAN DEFENCE. White decides to give up a pawn for rapid development. 2. d4 cxd4 3. c3 dxc3 4. Nxc3 d6 5. Bc4 Nf6 6. e5 White sets a trap, and Black falls right into it. The best move now is 6… Nfd7 6… dxe5 7. Bxf7+ A simple DEFLECTION. The black king is an OVERWORKED PIECE and White’s bishop forces him away from defending the queen. Black’s only move now is 7… Kxf7 when White just plays 8. Qxd8. 1. e4 Nc6 2. Nf3 d6 3. Bc4 Bg4 Black PINS the white Now White can move the knight, but it’s a mistake. PINNED knight with CHECK, White can play a SACRIFICE opening up a DISCOVERED on f7 to DECOY the black ATTACK. king. 5. -

Scholar'smate
SCHOLAR'S MATE SAMPLE ARTICLES CANADA'S CHESS MAGAZINE FOR KIDS CONTENTS Sample Articles Excerpts from different issues Actual magazines are 48 to 60 pages each. DEVELOPING ROOKS part 3 2 Kiril’s Klass June 2008 Make The Most Of Your 5 Point Pieces SPECIAL ED & SMART ALEC 3 Meet The Dudes February 2008 MATES 4 Mates In 1 & 2 Moves June 2008 LILY’S PUZZLER 5 Unusual Chess Problems June 2008 Switcheroos COMBO MOMBO 5 Spotlight On Decoys February 2008 Tactics With Rocky The Rook ADVENTURES OF CAPTAIN BEMO 6 Kiril's Korner February 2008 Voyage To The Top Of The World VOYAGE TO THE TOP OF THE WORLD SOLUTIONS 11 COMBO MOMBO ORDERING BACK ISSUES 11 DEVELOPING ROOKS part 3 Castling is the normal way to free a rook from the corner, but there are some positions where it is better to simply move the king up to the second rank. This DEVELOPING usually happens when the queens have been traded and the endgame is near. Then the king doesn’t need to ROOKS hide anymore. He can come out and fight like a man! PART 3 In this position, 1.O-O? frees the rook on h1 but leaves the white king out of play. 1...Rbc8! To get the advantage, the king must stay in the middle This lesson concludes our of the board and help the other series on activating rooks. white pieces challenge black’s 8 w4wdwdwd control of the open c-file. 7 dwdbiw0p 1.Kd2! Rbc8 2.Rhc1 6 wdw0w0wd One goal of good opening play is to “connect your The game might go 2...Rc3 5 0w4P0wdw rooks”. -

A Beginner's Guide to Coaching Scholastic Chess
A Beginner’s Guide To Coaching Scholastic Chess by Ralph E. Bowman Copyright © 2006 Foreword I started playing tournament Chess in 1962. I became an educator and began coaching Scholastic Chess in 1970. I became a tournament director and organizer in 1982. In 1987 I was appointed to the USCF Scholastic Committee and have served each year since, for seven of those years I served as chairperson or co-chairperson. With that experience I have had many beginning coaches/parents approach me with questions about coaching this wonderful game. What is contained in this book is a compilation of the answers to those questions. This book is designed with three types of persons in mind: 1) a teacher who has been asked to sponsor a Chess team, 2) parents who want to start a team at the school for their child and his/her friends, and 3) a Chess player who wants to help a local school but has no experience in either Scholastic Chess or working with schools. Much of the book is composed of handouts I have given to students and coaches over the years. I have coached over 600 Chess players who joined the team knowing only the basics. The purpose of this book is to help you to coach that type of beginning player. What is contained herein is a summary of how I run my practices and what I do with beginning players to help them enjoy Chess. This information is not intended as the one and only method of coaching. In all of my college education classes there was only one thing that I learned that I have actually been able to use in each of those years of teaching. -

Glossary of Chess
Glossary of chess See also: Glossary of chess problems, Index of chess • X articles and Outline of chess • This page explains commonly used terms in chess in al- • Z phabetical order. Some of these have their own pages, • References like fork and pin. For a list of unorthodox chess pieces, see Fairy chess piece; for a list of terms specific to chess problems, see Glossary of chess problems; for a list of chess-related games, see Chess variants. 1 A Contents : absolute pin A pin against the king is called absolute since the pinned piece cannot legally move (as mov- ing it would expose the king to check). Cf. relative • A pin. • B active 1. Describes a piece that controls a number of • C squares, or a piece that has a number of squares available for its next move. • D 2. An “active defense” is a defense employing threat(s) • E or counterattack(s). Antonym: passive. • F • G • H • I • J • K • L • M • N • O • P Envelope used for the adjournment of a match game Efim Geller • Q vs. Bent Larsen, Copenhagen 1966 • R adjournment Suspension of a chess game with the in- • S tention to finish it later. It was once very common in high-level competition, often occurring soon af- • T ter the first time control, but the practice has been • U abandoned due to the advent of computer analysis. See sealed move. • V adjudication Decision by a strong chess player (the ad- • W judicator) on the outcome of an unfinished game. 1 2 2 B This practice is now uncommon in over-the-board are often pawn moves; since pawns cannot move events, but does happen in online chess when one backwards to return to squares they have left, their player refuses to continue after an adjournment. -

Volume 33 Number Four—Fall 2006 Issue
Missouri Chess Association www.mochess.org Volume 33 Number Four—Fall 2006 Issue Serving Missouri Chess Since 1973 2005-2006 MCA Officers and Board of Directors Region 1 (St. Louis) Treasurer William H. Wright, 449 W. Jefferson Ave., Apt. B, St. Louis, MO 63122 Ed Baur, 7138 Lindenwood, St. Louis, MO 63109 Vice President Tony Rich, 6423 Towne Wood Drive, St. Louis, MO 63017 Region 2 (Kansas City) President Ken Fee, Jr., 1537 Baker, Liberty, MO 64068 Wayne Bartlett, P.O. Box 417, Oak Grove, MO 64075 Bryon McLaughlin, 836 NE Colleen Drive, Lee’s Summit, MO 64086 Region 3 (Rest of State) Secretary Charles Ward, 2400 Cimarron Drive, Columbia, MO 65203 Thomas Rehmeier, 5217 Denice Street, Jefferson City, MO 65109 Mike Clark, 1499 Summit View Drive, Holts Summit, MO 65043 Membership and Subscriptions The Missouri Chess Bulletin is the official quarterly publication of the Missouri Chess Association. MCA membership includes a subscription to the MCB. E-members receive their MCB via the internet (no printed copy). Include e-mail address with dues. Annual Membership Rates Regular $12 E-Member $5 Scholastic $8 Affiliate $10 Patron $25 Please send address changes and memberships to Charles Ward, 2400 Cimarron Dr., Columbia, MO 65203 Layout and design by Ken Fee and Bryon McLaughlin Missouri Chess Bulletin Fall 2006 Page 1 Missouri Chess - Fall 2006 3 Missouri Champions and Ratings 4 From the Editor Ken Fee 6 Board of Directors Minutes 7 Missouri Chess Festival Report Ken Fee 8 Ron Luther Wins 2006 MO Championship 9 Games from MO Invitational 10 2006 Missouri Open 11 Crosstables for Missouri Reserve, Quick, Blitz, Bughouse Championships 14 2006 MCA Scholastic and Crosstables 17 Steinitz in St. -

Sample Pages
CHESSONE - A COMPLETE INTRODUCTION TO THE ROYAL GAME Vassilis Aristotelous CYPRUS CHESS CHAMPION - FIDE INSTRUCTOR - FIDE ARBITER CONTENTS Preface .............................................................................................................. 11 Introduction ........................................................................................................ 13 The ELO Rating System.................................................................................... 16 History of Chess ................................................................................................ 18 World Chess Champions .................................................................................... 23 Grains on the Chessboard .................................................................................. 24 The Basics ......................................................................................................... 27 How the Pieces Move ....................................................................................... 29 The Value of the Pieces ..................................................................................... 33 The Relevant Value of the Pieces ..................................................................... 37 Piece Mobility .................................................................................................... 39 Pawn War .......................................................................................................... 40 Zugzwang ......................................................................................................... -

A Decoy Library Uncovers U-Box E3 Ubiquitin Ligases That Regulate Flowering Time
Genetics: Early Online, published on May 20, 2020 as 10.1534/genetics.120.303199 1 1 A Decoy Library Uncovers U-box E3 Ubiquitin Ligases that Regulate Flowering Time 2 in Arabidopsis 3 4 Authors: Ann M. Feke*, Jing Hong*†, Wei Liu*, Joshua M. Gendron* 5 6 Affiliations: *Department of Molecular, Cellular, and Developmental Biology, Yale 7 University, New Haven, CT 06511, USA. 8 †School of Food Science and Engineering, South China University of Technology, 9 Guangzhou, China Copyright 2020. 2 10 Running Title: E3 Ubiquitin Ligases in Flowering Time 11 Key Words: Protein degradation, flowering time, dominant negative strategies, plant 12 biology 13 Corresponding Author: Joshua Gendron; YSB 424, 260 Whitney Avenue, New Haven, CT 14 06511; 203-432-7317; [email protected] 3 15 ABSTRACT 16 Targeted degradation of proteins is mediated by E3 ubiquitin ligases and is 17 important for the execution of many biological processes. Redundancy has prevented the 18 genetic characterization of many E3 ubiquitin ligases in plants. Here, we performed a 19 reverse genetic screen in Arabidopsis using a library of dominant negative U-box type E3 20 ubiquitin ligases in order to identify their roles in flowering time and reproductive 21 development. We identified five U-box decoy transgenic populations that have defects in 22 flowering time or the floral development program. We used additional genetic and 23 biochemical studies to validate PLANT U-BOX 14 (PUB14), MOS4-ASSOCIATED COMPLEX 3A 24 (MAC3A), and MAC3B as bona fide regulators of flowering time. This work demonstrates the 25 widespread importance of E3 ubiquitin ligases in floral reproductive development. -

The Chinese People's Liberation Army in 2025
The Chinese People’s Liberation Army in 2025 The Chinese People’s The Chinese People’s Liberation Army in 2025 FOR THIS AND OTHER PUBLICATIONS, VISIT US AT http://www.carlisle.army.mil/ U.S. ARMY WAR COLLEGE David Lai Roy Kamphausen Editors: Editors: UNITED STATES Roy Kamphausen ARMY WAR COLLEGE PRESS David Lai This Publication SSI Website USAWC Website Carlisle Barracks, PA and The United States Army War College The United States Army War College educates and develops leaders for service at the strategic level while advancing knowledge in the global application of Landpower. The purpose of the United States Army War College is to produce graduates who are skilled critical thinkers and complex problem solvers. Concurrently, it is our duty to the U.S. Army to also act as a “think factory” for commanders and civilian leaders at the strategic level worldwide and routinely engage in discourse and debate concerning the role of ground forces in achieving national security objectives. The Strategic Studies Institute publishes national security and strategic research and analysis to influence policy debate and bridge the gap between military and academia. The Center for Strategic Leadership and Development CENTER for contributes to the education of world class senior STRATEGIC LEADERSHIP and DEVELOPMENT leaders, develops expert knowledge, and provides U.S. ARMY WAR COLLEGE solutions to strategic Army issues affecting the national security community. The Peacekeeping and Stability Operations Institute provides subject matter expertise, technical review, and writing expertise to agencies that develop stability operations concepts and doctrines. U.S. Army War College The Senior Leader Development and Resiliency program supports the United States Army War College’s lines of SLDR effort to educate strategic leaders and provide well-being Senior Leader Development and Resiliency education and support by developing self-awareness through leader feedback and leader resiliency. -

The Puzzling Side of Chess
TTHHEE PPUUZZZZLLIINNGG SSIIDDEE OOFF CCHHEESSSS Jeff Coakley INDEX updated August 30, 2021 I. Common Puzzles (through column 202) II. Problem Types & Topics III. Composers IV. Side Themes & Miscellanea I. Common Puzzles bold = column number Board Domination 06: 5Q, 3Q+2R, 2Q+4R, 1Q+5R 15: 8 Officers 24: 4R+4B+4N 71: BBNN 82: 7B 86: 4R+4N, 5R+5N 93: 6Q 97: 4B+4N (each attack 8 squares) 100: 4Q (attack total of 100 squares) 106: 6Q 107: 8R, 11R 110: 4Q 111: 8B (each attack 8 squares) 135: 6B (each attack 11 squares) 142: 4R+4B 178: 8 Officers Construction Task 15: 1,2 QRRBBNN 24: 3ab RBN, 4ab RRBBNN (most #1) 37: 5ab QRBN 59: 6 multi-Qs 67: 5ab QRBN 70: 7 BBNN 86: 8 RRNN 94: 9 RBNN 116: 10 QQRRBBNN 135: 12 BBB 138: most by R 142: 13 RRBB 143: 14 QQNN 153: most by B 161: most by N 167: most by P 185: KQQ, KQQQ Construction Task 93: K+9Q vs. K+9Q no captures (other) 106: no mate, max Qs 110: K+maxQs vs K, unique mate in 1 116: 11 no mate, max pieces 127: 11 no mate, max pieces 145: 11 149: DR longest inevitable stalemate 176: DR max moves 178: DR max moves 185: max get out of check 190: max disco checks 193: max consecutive disco checks 195: max consecutive disco checks Cyclotron 55: 1-6 61: 7 74: 8-15 89: 16-22 92: 23-29 94: 37 95: 30-36 98: 38 119: 39-42 126: 43-47 128: 48-52 130: 53-57 132: 58-62 138: 63 174: 64 177: 65-70 178: 71-72 180: 73-78 183: 79-84 195: helpmate 196: 85-92 Defensive Loop 15: 1 eight officers 18: 2 eight officers 24: 4R+4B+4N 36: 16 pieces 59: 14Q 67: KQRBN (non-loop) 70: BBNN 71: 4B+4N 82: 12B 86: 8R+8N 140: 32N