Magdeburger Journal Zur Sicherheitsforschung
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BIOS EPOX, Motherboard 4PCA HT ======Change Optimized Defaults Are Marked !!! Změny Oproti DEFAULT Jsou Označeny !!! ======
BIOS EPOX, motherboard 4PCA HT =================================================== Change Optimized Defaults are marked !!! Změny oproti DEFAULT jsou označeny !!! =================================================== Standard CMOS Features ====================== Halt On [All, But Keyboard] !!! Advanced BIOS Features ====================== CPU Feature-Delay Prior to Termal [16 Min] Limit CPUID MaxVal [Disabled] Hard Disk Boot Priority Bootovani disku CPU L1 & L2 Cache [Enabled] Hyper-Threading Technology [Enabled] !!! First Boot Device [HDD] !!! Second Boot Device [Disabled] !!! Third Boot Device [Disabled] !!! Boot Other Device [Disabled] !!! Boot Up Floppy Seek [Disabled] !!! Boot Up NumLock Status [On] Security Option [Setup] x APIC Mode (zasedle) [Enabled] HDD S.M.A.R.T .... [Disabled] Advanced Chipset Features ========================= DRAM Timing Selectable [By SPD] x x x x Agresive Memory Mode [Standard] x x x System BIOS Cacheable [Enabled] VIDEO BIOS Cacheable [Disabled] AGP Aperture ... [128] Init Display First [AGP] DRAM DATA Inregrity Mode [ECC] Integrated Peripherals ====================== On Chip IDE Device: IDE HDD [Enabled] IDE DMA [Enabled] On-Chip Primary [Enabled] IDE Primary MASTER PIO [Auto] ... [Auto] On-Chip Secondary [Enabled] IDE Secondary MASTER PIO[Auto] ... [Auto] On Chip Serial ATA [Disabled] (ostatni sede) OnBoard Device: USB Controller [Enabled] USB 2.0 [Enabled] USB Keyboard [Auto] USB Mouse [Disabled] !!! AC97 Audio [Disabled] !!! Game Port [Disabled] !!! Midi Port [Disabled] !!! On Board LAN Device [Enabled] -

CSR Volume 3 #3, April 1992
COMMUNICATIONS STANDARDS REVIEW Volume 3, Number 3 April, 1992 IN THIS ISSUE The following reports of recent standards meetings represent the view of the reporter and are not official, authorized minutes of the meetings. TR-45.3 Digital Cellular Standards, February 3 - 7, 1992, East Rutherford, NJ...................................................................2 TR-45.3.A Ad Hoc Authentication Group....................................................................................................................2 TR-45.3.1 — User Needs and Services.........................................................................................................................2 TR-45.3.2 — Dual-Mode Standards..............................................................................................................................2 TR-45.3.2.5 — Circuit Data Services............................................................................................................................3 TR-45.3.2.6 — Authentication Performance.................................................................................................................4 TR-45.3.2.8 — Packet Data Services............................................................................................................................4 TR-45.3.3 — Digital Standards.....................................................................................................................................4 TR-45.3.3.2 — Half-Rate Voice Coder.........................................................................................................................4 -

Full Partner List
Full Partner List Partnerships: Spyder Digital SIIG Franklin Electronic Solidtek SIIG BenQ America HIVI Acoustics PC Treasures Electronics) Bags & Carry Cases Research Inc. StarTech.com Gear Head Standzout StarTech.com Blue Microphones HMDX Peerless Withings Inc 3Dconnexion STM Bags Symtek Gefen StarTech.com Thermaltake BodyGuardz Honeywell Home Pentax Imaging Xavier Professional Cable Acer Symtek Targus Genius USA Targus TRENDnet Boom HP Inc. Phiaton Corp. Yamaha Adesso Inc. Targus Thermaltake Gigabyte Technology Thermaltake Turtle Beach Braven IAV Lightspeaker Philips Zagg-iFrogz AIRBAC The Joy Factory TRENDnet Griffin Technology TRENDnet U.S. Robotics BTI-Battery Tech. iHome Philips Electronics Zalman USA Aluratek Thermaltake Tripp Lite Gripcase Tripp Lite Visiontek BUQU Incipio Technologies Planar Systems zBoost American Weigh Scales Twelve South Visiontek Gyration Twelve South XFX C2G InFocus Plantronics Zmodo Technology Corp ASUS Urban Armor Gear VOXX Electronics Hawking Technologies TX Systems Zalman USA CAD Audio Innovative Office Products PNY Technologies Belkin Verbatim weBoost (Wilson HP Inc. U.S. Robotics Zotac Canon Interworks Polk Audio Data Storage Products Victorinox (Wenger) Electronics) HYPER by Sanho Verbatim Case-Mate Inwin Development Q-See BodyGuardz Aleratec Inc Zagg-iFrogz Xavier Professional Cable Corporation Viewsonic Casio IOGear QFX Canon Computers & Tablets Aluratek Incipio Technologies Visiontek Centon iON Camera Reticare inc CaseLogic Acer ASUS Computer & AV Cables Computer Accessories InFocus VisTablet -
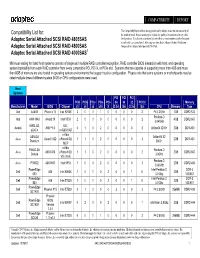
Compatibility List For: Adaptec Serial Attached SCSI RAID 4805SAS Adaptec Serial Attached SCSI RAID 4800SAS Adaptec Serial Atta
COMPATIBILITY REPORT This Compatibility Report reflects testing performed by Adaptec to test the interoperability of Compatibility List for: the products listed. It does not attempt to validate the quality of or preference for any of the Adaptec Serial Attached SCSI RAID 4805SAS listed products. It is also not an inclusive list and reflects a representative sample of products in each of the categories listed. All testing was done by the Adaptec Product Verification Adaptec Serial Attached SCSI RAID 4800SAS Group and the Adaptec InterOperability Test Lab. Adaptec Serial Attached SCSI RAID 4000SAS1 Minimum testing for listed host systems consists of single and multiple RAID controller recognition, RAID controller BIOS interaction with host, and operating system bootability from each RAID controller from every compatible PCI, PCI-X, or PCIe slot. Systems that are capable of supporting more than 4GB and more then 8GB of memory are also tested in operating system environments that support such a configuration. Please note that some systems or motherboards may be listed multiple times if different system BIOS or CPU configurations were used. Host Systems PCI PCI PCI PCIe PCIe PCIe PCIe PCI- 64 64 32 PCI 32 Memory Manufacturer Model BIOS Chipset x1 x4 x8 x16 X (3.3v) (5v) (3.3v) (5v) CPU Memory Type Abit AA8XE Phoenix 16 Intel 925XE 3 0 0 1 0 0 0 0 2 P4 3.2GHz 1GB DDR2-533 Pentium-D Abit AW8-MAX Award 19 Intel 955X 2 0 0 0 0 0 0 0 2 4GB DDR2-667 3.04GHz 939SLI32- ULI - Asrock AMI P1.0 0 1 0 2 0 0 0 0 3 Athlon64 3200+ 2GB DDR-400 eSATA m1695/1697 -

Electronics System Coordinator
Electronics System Coordinator RYOSAN CO., LTD. CORPORATE PROFILE 2020 Since its founding, Ryosan has conducted corporate activities based on the strong conviction that “a corporation is a public institution.” This phrase means that corporations are founded in order to benefit society in both the present and the future. Corporations are allowed to exist only if they are needed by society. In other words, corporations lose their meaning when they are no longer needed by society. Ryosan will continue its corporate activities with this strong conviction and firm resolution. “A corporation is a public institution.” Ryosan keeps this phrase firmly in its heart as the Company moves forward into the future. Ryosan History ~1960 1970 1980 1990 2000 2010~ 1953 1974 1981 1996 2000 2012 Ryosan Denki Co., Ltd. is established Hong Kong Ryosan Limited is The company name is changed to Ryosan Technologies USA Inc. The head office is moved to the current Ryosan Europe GmbH is established. in Kanda-Suehirocho, Chiyoda-ku, established. Ryosan Co., Ltd. is established. Head Office Building. Tokyo. Consolidated net sales exceed 300 2014 1976 1982 1997 billion yen. Ryosan India Pvt. Ltd. is established. 1957 Singapore Ryosan Private Limited Consolidated net sales exceed Zhong Ling International Trading The Company is reorganized as is established. 100 billion yen. (Shanghai) Co.,Ltd. is established. 2001 2016 a stock company as Korea Ryosan Corporation and Ryosan Engineering Headquarters obtain Ryosan Denki Co., Ltd. 1979 1983 1999 (Thailand) Co.,Ltd. are established. ISO9001 certification. Ryotai Corporation is established. Stock is listed on the Second Section Kawasaki Comprehensive Business 1963 of the Tokyo Stock Exchange. -

Who Pays Soundexchange: Q1 - Q3 2017
Payments received through 09/30/2017 Who Pays SoundExchange: Q1 - Q3 2017 Entity Name License Type ACTIVAIRE.COM BES AMBIANCERADIO.COM BES AURA MULTIMEDIA CORPORATION BES CLOUDCOVERMUSIC.COM BES COROHEALTH.COM BES CUSTOMCHANNELS.NET (BES) BES DMX MUSIC BES ELEVATEDMUSICSERVICES.COM BES GRAYV.COM BES INSTOREAUDIONETWORK.COM BES IT'S NEVER 2 LATE BES JUKEBOXY BES MANAGEDMEDIA.COM BES MEDIATRENDS.BIZ BES MIXHITS.COM BES MTI Digital Inc - MTIDIGITAL.BIZ BES MUSIC CHOICE BES MUSIC MAESTRO BES MUZAK.COM BES PRIVATE LABEL RADIO BES RFC MEDIA - BES BES RISE RADIO BES ROCKBOT, INC. BES SIRIUS XM RADIO, INC BES SOUND-MACHINE.COM BES STARTLE INTERNATIONAL INC. BES Stingray Business BES Stingray Music USA BES STORESTREAMS.COM BES STUDIOSTREAM.COM BES TARGET MEDIA CENTRAL INC BES Thales InFlyt Experience BES UMIXMEDIA.COM BES SIRIUS XM RADIO, INC CABSAT Stingray Music USA CABSAT MUSIC CHOICE PES MUZAK.COM PES SIRIUS XM RADIO, INC SDARS 181.FM Webcasting 3ABNRADIO (Christian Music) Webcasting 3ABNRADIO (Religious) Webcasting 8TRACKS.COM Webcasting 903 NETWORK RADIO Webcasting A-1 COMMUNICATIONS Webcasting ABERCROMBIE.COM Webcasting ABUNDANT RADIO Webcasting ACAVILLE.COM Webcasting *SoundExchange accepts and distributes payments without confirming eligibility or compliance under Sections 112 or 114 of the Copyright Act, and it does not waive the rights of artists or copyright owners that receive such payments. Payments received through 09/30/2017 ACCURADIO.COM Webcasting ACRN.COM Webcasting AD ASTRA RADIO Webcasting ADAMS RADIO GROUP Webcasting ADDICTEDTORADIO.COM Webcasting ADORATION Webcasting AGM BAKERSFIELD Webcasting AGM CALIFORNIA - SAN LUIS OBISPO Webcasting AGM NEVADA, LLC Webcasting AGM SANTA MARIA, L.P. -

Putnam DMV Branch to Close Due to Budget Cuts QUOTE “It Is Better to Suffer AUG
Mailed free to requesting homes in Eastford, Pomfret & Woodstock Vol. VI, No. 43 Complimentary to homes by request (860) 928-1818/e-mail: [email protected] FRIDAY, JULY 22, 2011 THIS WEEK’S Putnam DMV branch to close due to budget cuts QUOTE “It is better to suffer AUG. 11 SLATED AS FINAL DAY OF OPERATION wrong than to do it, and happier to be BY JACK MELTZER unfortunate that we don’t have a full-service DMV. sometimes cheated VILLAGER STAFF WRITER A lot of people including myself, if we have a lot than not to trust.” PUTNAM — Quiet Corner residents will have of work to do, [now have to] jump in the car and to find a new place to handle their motor vehicle run to Norwich.” issues due to the recent attempts by Gov.Dannel P. Viens said that at one time Putnam had a full Malloy to trim the state budget. service DMV in town, located in the northern Malloy put forth a proposal that will close many part of Riverfront Commons. After the state made INSIDE statewide Department of Motor Vehicle (DMV) some changes many years ago, Putnam offered up stations, including the Putnam satellite office, some free space from the town for what is now the A8-9 — OPINION Jack Meltzer photo which is set to shut its doors on Aug. 11. satellite station. “It’s frustrating, first and foremost,” said “It makes you wonder, if the money in the A10 — SPORTS The DMV satellite office in Putnam will be closing in Putnam Mayor Robert Viens. -

2005 Ranking Results
2005 Information Transparency and Disclosure Ranking Results in Taiwan Conducted by Securities and Futures Institute Entrusted by Taiwan Stock Exchange Corporation & GreTai Securities Market Despite all reasonable care given in the screening process to ensure objectivity, the SFI bears no responsibility in case of any damage or loss incurred from use of the ranking results. June 8, 2006 2005 Information Transparency and Disclosure Ranking Results in Taiwan About “Information Disclosure and Transparency Ranking System” The recent media focus on corporate governance has prompted calls for greater transparency and disclosure on companies around the globe. As a result, several leading financial-information providers have launched disclosure rankings, evaluations, and research related to how companies disclose information to rely on market force and mechanisms to encourage voluntary disclosures of companies. However, the evaluation criteria selected by those rankings, to some degree, could not provide an overall evaluation of disclosure practices in local market. In additions, there have been calls for standard setters and regulators to expand disclosure requirements according to international standards. Therefore, the Securities and Futures Institute (“SFI”), entrusted by the Taiwan Stock Exchange Corporation (“TSEC”) and the Gre Tai Securities Market (“GTSM”), currently launched “Information Transparency and Disclosure Rankings System”(ITDRS) to evaluate the level of transparency for all listed companies in Taiwan since 2003. For the third time, the 2005 full-year ranking results were released on June 8, 2006. It’s the first time that the full ranking results released. In the 1,032 listed companies of TSEC and GTSM, 12 companies were ranked as “Grade A+”, 183 companies were ranked as “Grade A”, 583 companies were ranked as “Grade B”, and 254 companies were ranked as “Grade C”. -
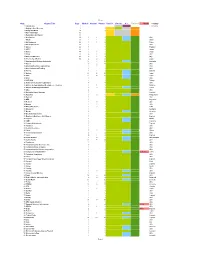
Sheet1 Page 1 Chap. Chapter Title Page Models Variants Photos
Sheet1 Chap. Chapter Title Page Models Variants Photos David C. Vincent A.C. Finished Needs Country 1 Introduction 1 V: 6/07/2014 2 Buying A Used Receiver 6 1 3 Using This Book 13 2 4 More Information 31 5 Restoration and Repair 35 6 AeroStream 39 1 1 1 USA 7 Afedri 39 1 1 1 Israel 8 Air Equipment 40 1 1 2 France 9 Air King Products 41 1 1 USA 10 Airmec 42 1 1 England 11 AITEC 43 1 1 Japan 12 Alinco 44 1 1 1 Japan 13 Allied 45 6 1 6 USA 14 Allocchio Bacchini 48 9 1 9 Italy 15 Alsetac (ApexRadio) 50 2 2 2 Japan 16 Amalgamated Wireless Australasia 15 7 15 Australia 17 Ameco 3 2 5 USA 18 American Electronic Laboratories 1 1 1 USA 19 American General Trading 1 1 USA 20 Andrus 1 1 1 Estonia 21 Anritsu 27 16 29 Japan 22 AOR 12 15 12 Japan 23 Arvin 1 1 USA 24 ASELSAN 1 1 Turkey 25 Astro Communications Laboratory 4 4 USA 26 Ateliers de Constructions Électriques de Charleroi 1 1 1 Belgium 27 Ateliers de Montages Electrique 7 6 7 France 28 Atlas 2 3 USA 29 Australian Sound Systems 1 1 Australia 30 Autophon 5 5 5 Switzerland 31 Bearcat 1 1 USA 32 BEH 1 1 Argentina 33 Belmont 4 5 4 USA 34 Bendix 1 1 1 USA 35 Bharat Electronics 1 4 1 India 36 Blaupunkt 2 1 2 Germany 37 Bonito 1 1 Germany 38 Boulevard Electronics 1 1 USA 39 Brookes & Gatehouse Ltd. -

Cisco Unified Computing System Pricing
Data Center In A Box Event Management Size Matters Liquid delivers a total Prism provides high-end But there’s more package p.34 features on a budget p.39 to choosing hardware p.42 A SPECIAL ALL-DIGITAL ISSUE November 2009 Unified systems combine servers, networking, storage, and management and put IT back in control. p.12 Green Dreams High efficiency is good Sponsored by for business, provides stellar PR —and is within reach p.26 << Previous C Network For IT, By IT C Network CONTENTS For IT, By IT >> Network Computing’s second all-digital issue Cover Story NEXT-GEN DATA CENTER, DELIVERED The unified computing platforms of today promise to consolidate everything and anything into a single chassis. And the vendors with the biggest R&D budgets are succeeding at this task.p.12 ENERGY-EFFICIENT INSIGHTS DATA CENTERS News Bits And Bytes Was your data center designed HP trades punches with Cisco; Juniper in the last five years? If not, has a new software platform, hardware, it’s not as efficient as it could and partners; businesses stumble on be. Brush up on the basics encryption; Q&A with HP’s Paul Congdon.p.8 of effective designs.p.26 REVIEWS A True Data Center In A Box Early adopters of the LiquidIQ virtual server say it’s reduced setup and reconfigure time, and let them cut back on high-priced staff.p.34 EventTracker Adds Much-Needed Monitoring The latest version of Prism’s security incident and event management offering makes up for old shortcomings.p.39 2 November 2009 networkcomputing.com << Previous Next >> ENTS NetworkComputing.com AROUND THE WEB Open Source You Can Use Two ways to browse the Web, and one great way to find everything scattered across all your storage media. -

Corporate Social Responsibility & Sustainability Report 2019
Corporate Social Responsibility & Sustainability Report 2019 AOC International (Europe) B.V. MMD-Monitors and Displays Nederland B.V. Prins Bernhardplein 200 1097 JB Amsterdam, The Netherlands CSR & Sustainability Report 2019 About this report This report describes our approach to sustainability and CSR practices and the relevant performance and achievements for the year that ended 31 December 2019. The report is prepared citing GRI and other international sustainability reporting frameworks. Your feedback on this report is welcomed. Any suggestions may be sent to Stefan van Sabben: [email protected]. 2 CSR & SustainabilityPresentation Report 2019 Contents ABOUT US 4 FOREWORD 5 OUR STRUCTURE 6 FINANCIAL PERFORMANCE 7 STRATEGY & OUTLOOK 8 CORPORATE GOVERNANCE 9 STAKEHOLDER ENGAGEMENT 12 OUR PEOPLE 13 COMMUNITY ENGAGEMENT 18 SUSTAINABLE PRODUCTS 19 SUSTAINABLE DEVELOPMENT GOALS 21 CORPORATE FOOTPRINT 24 DATA COLLECTION 28 APPENDIX 29 3 CSR & Sustainability Report 2019 About us AOC INTERNATIONAL (EUROPE) B.V. (AOC) MMD-MONITORS AND DISPLAYS NEDERLAND B.V. (MMD) The company was incorporated on 11th April 2011 as The company was incorporated on 27th November 2008 a private limited liability company and is 100% owned as a private limited liability company and is 100% owned by Coöperatie MMD Meridian U.A. On 24 October 2017 by MMD Monitors & Displays Holding B.V. which is in the legal form of Coöperatie MMD Meridian U.A. has turn ultimately 100% owned by TPV Technology Limited. changed from a Coöperatie to a Besloten Vennootschap under the new name TPV Europe Holding B.V. AOC is a Principal Activities limited liability company incorporated under the law of MMD purchases monitors and computer displays from The Netherlands. -

Recommended East Asian Core Collections for Children's, High
DOCUMENT RESUME ED lfb 021 IR002289 AUTHOF. Scott, William H.p 0., Ed,. TITLE s Recommended EastALsian Core Collections for Children's, High School, Public, CommunityCollege .,. and tndergraduate College Libraries. INSTITUTION East Asian Bibliographic Group. PUB DATE 74 L, NOTE 19615 EDPS PRICE t6-$0.76 HC-$9.51 Hips POSTAGE DESCRIPTORS *Audiovisual Aids; *BibliogFaphies; Books; College Libraries;'Films; Filmstrips;. Fine Arts; Junior College Libraries; *Library Collections;Library Material Selection; Periodicals; PublicLibrries; School libraries; University Libraries IDENT:FIERS China; *East Asia; Japan; Korea; Mongolia ABSTRACT A basic buying list forlibraries seeking to develop their Far East holdings is given in thisbibliography. Over 1700 items include published material up to1973--books, periodicals, films, filmstrips, tapes, and phonographrecotds"pertaining to China, Formosa, Japan, Korea, Mongoliaand Tibet. 'The items are 'arranged geographically with topicalsubdivisions. (Author/DS) *********************************************************************** unpublished *' * Documents acquired by ERIC include many informal * materials not available fromother sources. ERIC makes everyeffort * * to obtain the best copyavailable. nevertheless, items of marginal * * 'reproducibility are ofte encountered and this affects the quality * * of the microfiche and haIicopy reproductions EPIC makesavailable * * via the EPIC DocumentReproduction Service (EDRS). EDRS'is not * * responsible for the qualityof the originAl document. Reproductions*