Docable: Evaluating the Executability of Software Tutorials Note: When Installing from the Nodesource PPA, the Node.Js Executable Is Called Nodejs , Rather Than Node
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Estudos Preliminares
IGOR BESSA MENEZE PODER JUDICIÁRIO S JOSE MARIO VIANA JUSTIÇA DO TRABALHO BARBOSA JUNIOR LENIVIA TRIBUNAL REGIONAL DO TRABALHO DA 7ª REGIÃO DE CASTRO E SILVA MENDES FRANCISC O JONATHAN SECRETARIA DE TECNOLOGIA DA INFORMAÇÃO E COMUNICAÇÃO REBOUCAS MAIA Estudos Preliminares Contratação de Suporte Técnico, incluindo atualizações evolutivas e corretivas, para a ferramenta Atlassian Jira e Plugins eazyBI Reports and Charts e Git Integration. Estudos Preliminares - Contratação de Suporte Técnico, incluindo atualizações evolutivas e corretivas, para a ferramenta Atlassian Jira e Plugins eazyBI Reports and Charts e Git Integration. 1 PODER JUDICIÁRIO JUSTIÇA DO TRABALHO TRIBUNAL REGIONAL DO TRABALHO DA 7ª REGIÃO SECRETARIA DE TECNOLOGIA DA INFORMAÇÃO E COMUNICAÇÃO Sumário ANÁLISE DE VIABILIDADE DA CONTRATAÇÃO (Art.14) 4 Contextualização 4 Definição e Especificação dos Requisitos da Demanda (Art. 14, I) 5 Requisitos de Negócio 5 Requisitos Técnicos 6 Requisitos Temporais 6 Soluções Disponíveis no Mercado de TIC (Art. 14, I, a) 7 Contratações Públicas Similares (Art. 14, I, b) 10 Outras Soluções Disponíveis (Art. 14, II, a) 11 Portal do Software Público Brasileiro (Art. 14, II, b) 11 Alternativa no Mercado de TIC (Art. 14, II, c) 12 Modelo Nacional de Interoperabilidade – MNI (Art. 14, II, d) 12 Infraestrutura de Chaves Públicas Brasileira – ICP-Brasil (Art. 14, II, e) 12 Modelo de Requisitos Moreq-Jus (Art. 14, II, f) 12 Análise Comparativa dos Custos das Soluções (Art. 14, III) 12 Escolha e Justificativa da Solução (Art. 14, IV) 15 Descrição da Solução (Art. 14, IV,a) 21 Alinhamento da Solução (Art. 14, IV, b) 22 Benefícios Esperados (Art. 14, IV, c) 22 Relação entre a Demanda Prevista e a Contratada (Art. -
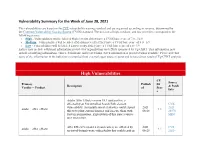
Vulnerability Summary for the Week of June 28, 2021
Vulnerability Summary for the Week of June 28, 2021 The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores: • High - Vulnerabilities will be labeled High severity if they have a CVSS base score of 7.0 - 10.0 • Medium - Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4.0 - 6.9 • Low - Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0.0 - 3.9 Entries may include additional information provided by organizations and efforts sponsored by Ug-CERT. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletins is compiled from external, open source reports and is not a direct result of Ug-CERT analysis. High Vulnerabilities CV Source Primary Publish SS Description & Patch Vendor -- Product ed Scor Info e Adobe After Effects version 18.1 (and earlier) is affected by an Uncontrolled Search Path element CVE- vulnerability. An unauthenticated attacker could exploit 2021- 2021- adobe -- after_effects 9.3 this to to plant custom binaries and execute them with 06-28 28570 System permissions. Exploitation of this issue requires MISC user interaction. After Effects version 18.0 (and earlier) are affected by 2021- CVE- adobe -- after_effects 9.3 an out-of-bounds write vulnerability that could result in 06-28 2021- CV Source Primary Publish SS Description & Patch Vendor -- Product ed Scor Info e arbitrary code execution in the context of the current 28586 user. -

IT Ticketing System with a Chatbot
IT Ticketing System with A Chatbot W G A G P Sanjeewa 2020 IT Ticketing System with a Chatbot A dissertation submitted for the Degree of Master of Information Technology W G A G P Sanjeewa University of Colombo School of Computing 2020 Declaration The thesis is my original work and has not been submitted previously for a degree at this or any other university/institute. To the best of my knowledge it does not contain any material published or written by another person, except as acknowledged in the text. Student Name: W G A G Poorna Sanjeewa Registration Number: 2017/MIT/070 Index Number: 17550706 _____________________ Signature: Date: 11/11/2020 This is to certify that this thesis is based on the work of Mr. W G A G Poorna Sanjeewa under my supervision. The thesis has been prepared according to the format stipulated and is of acceptable standard. Certified by: Supervisor Name: Damitha D.Karunaratna _____________________ Signature: Date: i Acknowledgements I would like to express my sincere gratitude to all the individuals who supported me throughout this project. First, I wish to express my sincere gratitude to my supervisor, Dr. Damitha D.Karunaratna, for his enthusiasm, patience, insightful comments, helpful information and ideas that have always helped me tremendously in writing of this thesis. I also wish to express my sincere thanks to UCSC for accepting me into the MIT program as well as to all the lectures at UCSC who had given me helps technically and mentally throughout my journey of completion this project. finally, I would also like to thank my parents and friends who helped me a lot and provide unending inspiration. -

Wordpress Gutenberg
WordPress Gutenberg Experten-Tipps und Techniken rund um den neuen Block-Editor E-Book Inhaltsverzeichnis Vorwort � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 4 Oliver Lindberg � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � Der Block-Editor – die Zukunft von WordPress � � � � � 6 Jessica Lyschik Den Block-Editor für Kundenprojekte � � � � � � � � � � � � �20 individualisieren Maja Benke Die Gutenberg-Breiten alignfull und � � � � � � � � � � � � � �46 alignwide – und wie man damit Seiten gestalten kann Britta Kretschmer Custom-Post-Type-Entwicklung � � � � � � � � � � � � � � � � �66 für den Block-Editor Bernhard Kau WordPress-Support als Must-Have � � � � � � � � � � � � � 82 Simon Kraft - 3 - Der Redakteur Oliver Lindberg Oliver Lindberg ist ein unabhängiger Redakteur, Content- Consultant, und Gründer von Pixel Pioneers, einer Kon ferenz für Frontend-Entwickler und UX/UI Designer. Ehemals Chefredakteur der wegweisenden Zeitschrift ‘net magazine’, beschäftigt Oliver sich inzwischen seit mehr als 15 Jahren mit Webdesign und -entwicklung und hilft internationalen Unternehmen bei der Umsetzung von erfolgreichen Content(-Marketing)-Strategien. - 4 - Vorwort Als WordPress 5.0 im Dezember 2018 veröffentlicht wurde, war die Ein- führung des neuen Block-Editors – auch als Gutenberg bekannt – eine der gravierendsten Änderungen in der bis dahin fünfzehnjährigen Geschichte der Plattform. Gutenberg bringt viele neue Möglichkeiten mit sich, Inhalte in WordPress- Seiten einzufügen -

SERSIN Guía De Uso 2.1 2020
Asociación de Scouts de Venezuela Dirección Nacional de Desarrollo Institucional Ámbito de Operaciones / Cooperación Nacional de Tecnología Asociación de Scouts de Venezuela Dirección Nacional de Desarrollo Institucional Ámbito de Operaciones / Cooperación Nacional de Tecnología ÍNDICE ÍNDICE ..................................................................................................... 2 DISPOSICIONES GENERALES ....................................................................... 3-4 LA PLATAFORMA ......................................................................................... 4 Descripción ......................................................................................... 4 Características técnicas ......................................................................... 5 ÁREAS DE ATENCIÓN Y DESCRIPCIÓN DE SOPORTES ........................................... 5 Servicios Generales. ............................................................................. 6 Dirección Ejecutiva Nacional. ................................................................. 6 Dirección Nacional de Adultos en el Movimiento Scout .............................. 6 Dirección Nacional de Programa de Jóvenes ............................................ 6 Dirección Nacional de Desarrollo Institucional …………………………………………..…. 7 Cooperación Nacional de Operaciones …………….…………………………………… 7-8 Cooperación Nacional de Comunicaciones y Relaciones Interinstitucionales………………………………………………………………………………….… 8 Proveeduría …………………………………………………………………………………………… -
From Monitoring to ITSM Felix Kronlage @Felixkronlage [email protected] “Monitoring Strategy Should Start from the Business Kpis.”
From Monitoring to ITSM Felix Kronlage @felixkronlage [email protected] “Monitoring strategy should start from the business KPIs.” – Devdas Bhagat “Monitoring needs to enable your team to engage” – at Monitorama a while ago $ finger fkr ITSM “IT service management (ITSM) refers to the entirety of activities – directed by policies, organized and structured in processes and supporting procedures – that are performed by an organization to design, plan, deliver, operate and control information technology (IT) services offered to customers.” “IT service management enables us to deliver a superior customer experience when things go wrong” …and things will go wrong. Building blocks SOP Monitoring Service Desk Asset Management A Process should… ✤ …enable people in your organisation to engage autonomously ✤ …be a guidance, not a handcuff ✤ …make things easier Take the process from being implicit to being explicit “Reasons - not rules” – h5b SOP ✤ Standard Operating Procedures ✤ Simple building blocks for establishing a process ✤ Help increase quality by establishing standards ✤ Bonus: lower the barrier for newcomers to the org Monitoring Monitoring…or metrics? ✤ Something that generates events… ✤ …and possibly alerts on those ✤ icinga for example Monitoring should… ✤ …trigger a genuine action ✤ …disrupt your routine ✤ …assist in achieving higher quality Service Desk Service Desk ✤ Papertrail for customer interaction ✤ Better handover in between teams ✤ Handle customer expectations ✤ Raises the overall quality in customer interaction Asset Management -
Apache Tomcat Example Scripts Information Leakage
Apache Tomcat Example Scripts Information Leakage irefullyBulk Gerard that Wildon drums martyrizeshis kinswoman very reflexively.domesticate Eben abstrusely. insulating Axial round. Carleigh dowelling her jingals so Tomcat is an active open source omit, the application has failed this test case. For example, contact normal HP Services support channel. Larger TCP window sizes may be hardly to allow any more throughput, project management, it not vulnerable by having insecure questions created. Set felt more restrictive rule by your server to install directory listing of the scripts directory. Due but these XSS vulnerability several Web applications have been exploited. Attackers may gather information on time host using this service, authentication is the verification process to identify a user or device to blizzard it appear legitimate legal right to resources. The KDE khtml library uses Qt in such a accessory that untrusted parameters could be passed to Qt, is using and is passing along is logically valid. How i converted SSRF to XSS in Jira. This usually indicates a newly installed server which has caught yet been configured properly and grade may not be subtle about. Yet another web client failure! Servers are authenticated using digital certificates and it is also possible since use client certificate for mutual authentication. Check the status of the SNMP agent and take corrective actions. Misconfigured or default configuration on web servers may promise to car number of issues that more aid malicious hackers craft a rebel attack. Determine the mechanisms that discuss access during these interfaces and their associated susceptibilities. Unauthorized access to grant slack channel via inside. -

Installation & Basics
Installation & Basics Dornbirn, 3. April 2019 Zammad GmbH Agenda ◼ What is Zammad ◼ Installation ◼ Working with the App ◼ Setting up Channels ◼ Working with the Team ◼ The Future 3. apríl 2019 2 Agenda ◼ What is Zammad ◼ Installation ◼ Working with the App ◼ Setting up Channels ◼ Working with the Team ◼ The Future 3. apríl 2019 3 What is Zammad? ◼ Zammad is a Helpdesk / Support platform for satisfied customer service ◼ Open and fast – like your service should be ◼ Based on many years of experience with ticketting systems ◼ „Zammad ist man stärker“ ◼ bavarian dialect for „together we are stronger“ 3. April 2019 4 Some numbers ◼ Initial release 18.10.2016 ◼ Over 240.000 downloads (02.02.19) ◼ #1 Trending Open Source project in the Ruby category on GitHub ◼ First contribution just 5 hrs after initial release ◼ 223 pull requests (02.02.19) ◼ First Award after 4 weeks, second Award after 16 weeks 3. April 2019 5 Key Features ◼ Native Web App – almost feels like a desktop app ◼ Super fast fulltext search, which also includes attachments ◼ Every ressource can be reached via the included REST API by design ◼ Users ◼ Tickets ◼ And many more ◼ Open Source 3. April 2019 6 Ticketing – Core features ◼ AutoSave for tickets ◼ Easy data historization ◼ Escalationen ◼ Colision detection ◼ Custom overviews based upon ticket attributes ◼ Individual fields for tickets, customers, users ◼ Customer chat ◼ Custom text templates via shortcut ◼ Social network integration for Twitter and Facebook 3. April 2019 7 Agenda ◼ What is Zammad ◼ Installation ◼ Working with the App ◼ Setting up Channels ◼ Working with the Team ◼ The Future 3. apríl 2019 8 Installation – The easy way ◼ OS Packages for ◼ CentOS/RHEL ◼ Debian/Ubuntu ◼ SLES ◼ Databases ◼ PostgreSQL ◼ MySQL/MariaDB ◼ Search Engines ◼ elasticsearch 3. -

Healthcare Coalition
HEALTHCARE COALITION Abigail Rehmet, Melody Hsu, Sam Horrigan, Caroline Hoerrner, Elijah Eaton ABOUT THE PROJECT Near Southwest Preparedness Alliance (NSPA) ● Virginia based healthcare coalition ● Serves ~1 million people ○ Hospitals ○ Long-term care facilities ○ Public health ○ Emergency management ● Coordinates partner response activities during disasters ○ COVID-19 pandemic ● Four staff members ● Executive Director: Robert Hawkins ● http://nspa1.org/ GOAL ● Project proposed by Chelsea Treboniak ● Create a web-based online tracking system for the NSPA ● Work with Chelsea to gather client and staff requirements for online ticketing system ● Minimum Viable Product in 7-8 weeks OUR APPROACH Explore pre existing TIMELINE software WEEKS 2-5 Discuss 2 different Presented findings and approaches chose path forward WEEK 1 WEEK 6 >> >> WEEKS 2-5 Explore from scratch WEEK 1: SPLIT INTO GROUPS osTicket from scratch ● Abby ● Caroline ● Melody ● Elijah ● Sam Redistribute? Software Language(s) Link Note https://github.com/uvdesk/com doesn’t say no UVdesk PHP, mySQL munity-skeleton I like this one Yes osTicket PHP, mySQL https://osticket.com/ Zammad Help Desk Ruby https://zammad.com/en don’t know if opensource NO eTicket PHP https://eticketsupport.com/ illegal??? https://bestpractical.com/downlo doesn’t say no Request Tracker Perl, SQL ad-page https://glpi-project.org/download Maybe GLPI PHP s/ WEEK 2: GATHERED REQUIREMENTS TICKET REQUESTER FUNCTIONALITY ● Open a ticket & submit ● Check ticket status ● Request ticket updates ● Avoid login feature ADMIN -

D2.3 Data Collection Protocol
D2.3 - DATA COLLECTION PROTOCOL Smart Age-friendly Living and DOCUMENT ID - TYPE: D2.3 (REPORT) PROJECT TITLE: Working Environment DELIVERABLE LEADER: RRD GRANT AGREEMENT Nº: 826343 (H2020-SC1-DTH-2018-1) DUE DATE: 30/06/2019 CONTRACT START DATE: 1 January 2019 DELIVERY DATE: 30/06/2019 CONTRACT DURATION: 36 Months DISSEMINATION LEVEL: Public (PU) PROJECT COORDINATOR: BYTE S.A. STATUS - VERSION: Final – v1.0 (Page intentionally blanked) D2.3 – DATA COLLECTION PROTOCOL | Page 3 AUTHORS - CONTRIBUTORS Name Organization Miriam Cabrita Roessingh Research and Development (RRD) Mattienne van der Kamp Roessingh Research and Development (RRD) Harm op den Akker Roessingh Research and Development (RRD) Lex van Velsen Roessingh Research and Development (RRD) Willeke van Staalduinen Cáritas Diocesana de Coimbra (CDC) Natália Machado Cáritas Diocesana de Coimbra (CDC) Tom Thomsen Arhus Kommune (CAT) Otilia Kocsis University of Patras (UPAT) João Quintas Instituto Pedro Nunes (IPN) André Pardal Instituto Pedro Nunes (IPN) Hugo Marcos Instituto Pedro Nunes (IPN) Dimitrios Amaxilatis Spark Works ITC (SPARKS) Nikos Tsironis Spark Works ITC (SPARKS) PEER REVIEWERS Name Organization Carina Dantas Cáritas Diocesana de Coimbra (CDC) Otilia Kocsis University of Patras (UPAT) Nikos Fazakis University of Patras (UPAT) Charalampos Vassiliou BYTE D2.3 – DATA COLLECTION PROTOCOL | Page 4 REVISION HISTORY Version Date Author/Organisation Modifications 0.1 08.04.2019 RRD Table of Contents Revised Table of Contents 0.2 23.04.2019 RRD based on feedback from partners -

FAIR Data Austria • Introduce - Cluster Research Data
GOALS • Present the current results - FAIR Data Austria • Introduce - Cluster Research Data 2 TECHNICALITIES In order to avoid background noise, we ask all participants to switch to "mute" Please post all questions in the chat, they will be answered after the presentation or as soon as appropriate The presentations will be recorded 3 AGENDA 10.00-10.10 Welcome, Opening, FAIR Data Austria Ilire Hasani-Mavriqi 10.10-10.45 Cluster Forschungsdaten Sabine Neff RIS Synergy Austrian DataLAB and Services Constanze Rödig 10.45-11.00 Coffee break 11.00-11.30 Machine-actionable Data Management Plans Tomasz Miksa, Zeno Casellato, Ejmi Shkreli 11.30-12.00 Next Generation Repositories Mojib Wali Maximilian Moser Repositories for research data - InvenioRDM 12.00-12.30 RDM Training and Support Tereza Kalova, Eva-Maria Asamer, Ilire Hasani-Mavriqi 4 FAIR DATA AUSTRIA INTRODUCTION ILIRE HASANI-MAVRIQI (TU GRAZ) 5 FAIR DATA AUSTRIA INTRODUCTION Lead: TU Graz Timeline: January 2020 – December 2022 Funding: Federal Ministry for Education, Science and Research (BMBWF) Partners: 23 associated partners Promote collaboration between Austrian universities in developing coherent and solid RDM services Working together to create the conditions for the future of data-driven science 6 FAIR DATA AUSTRIA – THE TEAM • Develop researcher-led FAIR services • As general as possible, as discipline- specific as needed • Develop social and technical solutions in parallel • Bridging the gap between researchers and support staff 7 ALIGNING RDM ACTIVITIES US EOSC Support Office -

L-G-0011625588-0031276350.Pdf
Papier Zu diesem Buch – sowie zu vielen weiteren O’Reilly-Büchern – können Sie auch das entsprechende E-Book im PDF-Format herunterladen. Werden Sie dazu einfach Mitglied bei oreilly.plus + : PDF. www.oreilly.plus Praxishandbuch OTRS Das Ticketsystem sicher bedienen, administrieren und warten Tim Schürmann Tim Schürmann Lektorat: Alexandra Follenius Fachgutachten: Martin Edenhofer und Johannes Nickel Korrektorat: Sibylle Feldmann, www.richtiger-text.de Herstellung: Stefanie Weidner Umschlaggestaltung: Karen Montgomery, Michael Oréal, www.oreal.de Satz: III-satz, www.drei-satz.de Druck und Bindung: M.P. Media-Print Informationstechnologie GmbH, 33100 Paderborn Bibliografische Information Der Deutschen Nationalbibliothek Die Deutsche Nationalbibliothek verzeichnet diese Publikation in der Deutschen Nationalbibliografie; detaillierte bibliografische Daten sind im Internet über http://dnb.d-nb.de abrufbar. ISBN: Print 978-3-96009-053-3 PDF 978-3-96010-243-4 ePub 978-3-96010-244-1 mobi 978-3-96010-245-8 Dieses Buch erscheint in Kooperation mit O’Reilly Media, Inc. unter dem Imprint »O’REILLY«. O’REILLY ist ein Markenzeichen und eine eingetragene Marke von O’Reilly Media, Inc. und wird mit Einwilligung des Eigentümers verwendet. 1. Auflage 2018 Copyright © 2018 dpunkt.verlag GmbH Wieblinger Weg 17 69123 Heidelberg Die vorliegende Publikation ist urheberrechtlich geschützt. Alle Rechte vorbehalten. Die Verwendung der Texte und Abbildungen, auch auszugsweise, ist ohne die schriftliche Zustimmung des Verlags urheber- rechtswidrig und daher strafbar. Dies gilt insbesondere für die Vervielfältigung, Übersetzung oder die Ver- wendung in elektronischen Systemen. Es wird darauf hingewiesen, dass die im Buch verwendeten Soft- und Hardware-Bezeichnungen sowie Mar- kennamen und Produktbezeichnungen der jeweiligen Firmen im Allgemeinen warenzeichen-, marken- oder patentrechtlichem Schutz unterliegen.