A Practical Meet-In-The-Middle Attack on SIGABA
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Enigma Encryption Machine and Its Electronic Variant
The Enigma Encryption Machine and its Electronic Variant Michel Barbeau, VE3EMB What is the Enigma? possible initial settings, making the total number of initial settings in the order of 10 power 16. The The Enigma is a machine devised for encrypting initial setting, taken from a code book, indicates plain text into cipher text. The machine was which pairs of letters (if any) are switched with each invented in 1918 by the German engineer Arthur other. The initial setting is called the secret key. Scherbius who lived from 1878 to 1929. The German Navy adopted the Enigma in 1925 to secure World War II was fought from 1939 to 1945 their communications. The machine was also used between the Allies (Great Britain, Russia, the by the Nazi Germany during World War II to cipher United States, France, Poland, Canada and others) radio messages. The cipher text was transmitted in and the Germans (with the Axis). To minimize the Morse code by wireless telegraph to the destination chance of the Allies cracking their code, the where a second Enigma machine was used to Germans changed the secret key each day. decrypt the cipher text back into the original plain text. Both the encrypting and decrypting Enigma The codes used for the naval Enigmas, had machines had identical settings in order for the evocative names given by the germans. Dolphin decryption to succeed. was the main naval cipher. Oyster was the officer’s variant of Dolphin. Porpoise was used for The Enigma consists of a keyboard, a scrambling Mediterranean surface vessels and shipping in the unit, a lamp board and a plug board. -

The Mathemathics of Secrets.Pdf
THE MATHEMATICS OF SECRETS THE MATHEMATICS OF SECRETS CRYPTOGRAPHY FROM CAESAR CIPHERS TO DIGITAL ENCRYPTION JOSHUA HOLDEN PRINCETON UNIVERSITY PRESS PRINCETON AND OXFORD Copyright c 2017 by Princeton University Press Published by Princeton University Press, 41 William Street, Princeton, New Jersey 08540 In the United Kingdom: Princeton University Press, 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press.princeton.edu Jacket image courtesy of Shutterstock; design by Lorraine Betz Doneker All Rights Reserved Library of Congress Cataloging-in-Publication Data Names: Holden, Joshua, 1970– author. Title: The mathematics of secrets : cryptography from Caesar ciphers to digital encryption / Joshua Holden. Description: Princeton : Princeton University Press, [2017] | Includes bibliographical references and index. Identifiers: LCCN 2016014840 | ISBN 9780691141756 (hardcover : alk. paper) Subjects: LCSH: Cryptography—Mathematics. | Ciphers. | Computer security. Classification: LCC Z103 .H664 2017 | DDC 005.8/2—dc23 LC record available at https://lccn.loc.gov/2016014840 British Library Cataloging-in-Publication Data is available This book has been composed in Linux Libertine Printed on acid-free paper. ∞ Printed in the United States of America 13579108642 To Lana and Richard for their love and support CONTENTS Preface xi Acknowledgments xiii Introduction to Ciphers and Substitution 1 1.1 Alice and Bob and Carl and Julius: Terminology and Caesar Cipher 1 1.2 The Key to the Matter: Generalizing the Caesar Cipher 4 1.3 Multiplicative Ciphers 6 -

Historical Ciphers Systems Top 10 Open Problems May 5, 2016 George Lasry [email protected] Open Problems - Criteria
Historical Ciphers Systems Top 10 Open Problems May 5, 2016 George Lasry [email protected] Open Problems - Criteria • Generic method vs. deciphering a document • System details are known – For many there are simulators • Published methods vs. classified • General vs. special case solutions – Ciphertext only vs. known plaintext – Single message vs. in-depth messages – Short vs. long messages – Long vs. short keys • Brute force not feasible – But computer most likely required George Lasry May 2016 2 Top 10 Open Problems 1. SIGABA 2. KL-7 3. Siemens T52D “Sturgeon” 4. Hagelin CX-52 5. Fialka 6. Lorenz SZ42 “Tunny” – Ψ1 limitation 7. Hagelin M-209 – short messages 8. Double Transposition – long random keys 9. Enigma – short message 10. Chaocipher – single message George Lasry May 2016 3 Problem 1: SIGABA (US) • Possible keys (WWII): 2 96 = 10 29 • Best published: known-plaintext 2 60 = 10 18 steps George Lasry May 2016 4 Problem 2: KL-7 (US) • Details of the machine known (+ simulator) • Best published cryptanalytic method: None! George Lasry May 2016 5 Problem 3: Siemens & Halske T52D • Successor of T52a/b/c: Irregular wheel stepping • Possible key settings: 2 73 = 10 24 • Best published method: > 5 messages in depth George Lasry May 2016 6 Problem 4: Hagelin CX-52 • Successor of C38/M209: Irregular wheel stepping • Possible key settings: 2 439 = 10 132 • Best published method: Known-plaintext George Lasry May 2016 7 Problem 5: Fialka M-125 (Russia) • Possible key settings: 2 250 = 10 75 • Best published method: None! George -

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -
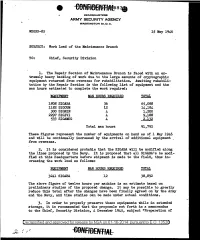
Work Load of the Maintenance Branch
HEADQUARTERS ARMY SECURITY AGENCY WASHINGTON 25, D. C. WDGSS-85 15 May 1946 SUBJECT: Work Load of the Maintenance Branch TO: Chief, Security Division 1. The Repair Section of Maintenance Branch is .faced with an ex tremely heavy backlog of' work due to the large amounts of' cryptographic equipment returned from overseas for rehabilitation. Awaiting rehabili tation by the Repair Section is the followi~g list of equipment and the man hours estimated to complete the work required.: EQUIPMENT MAN HOURS REQUIRED TOTAL 1808 SIGABA 36 65,088 1182 SIGCUM 12 14,184 300 SIGNIN 4 1,200 2297 SIGIVI 4 9,188 533 SIGAMUG 4, 2,132 Total man hours 91,792 These figures represent the number of equipments on hand as of 1 May 1946 and will be continually increased by the arrival of additional equipment . from overseas. 2. It is considered probable that the SIGABA will be modified along the lines proposed by the Navy. It is proposed that all SIGABA 1s be modi fied at this Headquarters before shipment is made to the field, thus in creasing the work load as follows: EQUIPMENT MAN HOURS REQUIRED 3241 SIGABA 12 The above figure of' twelve hours per machine is an estimate based on preliminary studies of' the proposed change. It may be possible to greatly reduce this total af'ter the changes have been f inaJ.ly agreed on by the .Army and the Navy, and time studies can be made under actual conditions. ,3. In order to properly preserve these equipments while in extended storage, it is recommended that the proposals set .forth in a memorandum to the Chief, Security Division, 4 December 1945, subject "Preparation of Declassified and approved for release by NSA on 01-16-2014 pursuantto E .0. -

SIS and Cipher Machines: 1930 – 1940
SIS and Cipher Machines: 1930 – 1940 John F Dooley Knox College Presented at the 14th Biennial NSA CCH History Symposium, October 2013 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 United States License. 1 Thursday, November 7, 2013 1 The Results of Friedman’s Training • The initial training regimen as it related to cipher machines was cryptanalytic • But this detailed analysis of the different machine types informed the team’s cryptographic imaginations when it came to creating their own machines 2 Thursday, November 7, 2013 2 The Machines • Wheatstone/Plett Machine • M-94 • AT&T machine • M-138 and M-138-A • Hebern cipher machine • M-209 • Kryha • Red • IT&T (Parker Hitt) • Purple • Engima • SIGABA (M-134 and M-134-C) • B-211(and B-21) 3 Thursday, November 7, 2013 3 The Wheatstone/Plett Machine • polyalphabetic cipher disk with gearing mechanism rotates the inner alphabet. • Plett’s improvement is to add a second key and mixed alphabet to the inner ring. • Friedman broke this in 1918 Principles: (a) The inner workings of a mechanical cryptographic device can be worked out using a paper and pencil analog of the device. (b) if there is a cycle in the mechanical device (say for particular cipher alphabets), then that cycle can be discovered by analysis of the paper and pencil analog. 4 Thursday, November 7, 2013 4 The Army M-94 • Traces its roots back to Jefferson and Bazieres • Used by US Army from 1922 to circa 1942 • 25 mixed alphabets. Disk order is the key. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -

George Lasry: Modern Cryptanalysis of Historical Ciphers
Modern Cryptanalysis of Historical Ciphers November 1, 2019 George Lasry Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 2 Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 3 Motivation • Historical cryptanalysis • Undecrypted texts • Public challenges • Fun George Lasry 4 Difficulty - Factors • System design – Diffusion – Confusion – Weaknesses • Key – Key space/length • Ciphertext – Length – Language George Lasry 5 Difficulty Easy Moderate Hard Very hard Intractable? Monoalphabetic Playfair Playfair Playfair Fialka substitution (long ciphertext) (short ciphertext) (very short) Transposition Transposition ADFGVX Double transposition Double transposition (short key) (long key) (long random key) Vigenere Enigma Enigma SIGABA (long ciphertext) (short ciphertext) (known plaintext) Hagelin M-209 Hagelin M-209 (long ciphertext) (short ciphertext) Hagelin M-209 Sturgeon T52 Sturgeon T52 (known plaintext) (regular stepping) (irregular stepping) George Lasry 6 Generic Approaches - 1 Exhaustive Combinatorial Stochastic Search Search Search ● Simple brute force ● Backtracking ● Hill climbing ● Dictionary search ● Meet in the Middle ● Simulated annealing (MITM) ● Hybrid (e.g., nested) ● Match some ● Others (e.g., genetic constraints (e.g., ● Match some algorithms) known plaintext) constraints ● Or optimize a scoring ● Optimize a fitness -

Scamp Iv, Lecture V; History of the Invention And
REF ID:A38396 r I LECTURE V HISTORY OF THE INVENTION AND DEVELOHllENT OF CIPHER DEVICES AND MACHI.NF.$. Three or four years ago I was asked to give a lecture before the Communica- tions-Electronics Division of the Air University, USAF, on the subject of communications security (COMSEC). About that time there was 'hP r "o:s..ui.i.ered into our ears over the radio a slogan concerned wi+~ ~oile traffic safety rules • ..... ThE" o1iugta.n." was: "Don't learn your traffic laws by accident!" I thought the slogan useful. as the title of my talk but l modified it a little: "Don't learn your COMSEC laws by accident•" I began my talk by reading Webster's definition of the word accident. I know, of course, that this group here today is not concerned particularly with COMSEC duties of any sort. But the definition of the word accident will nevertheless be of interest 11l connection with what will be said in a moment or two, so I'll read Webster's definition if you'll bear with me. Webster: "Acc:ulent" - literally, a be:talling. ~ '\ a. An event that takes place without one's foresight or expectation, ) '\;r an undesigned, sudden, and unexpected event. @'pp roved for Release by NSA on 10-10-2013 pursuantto E .0. 1352a REF ID:A38396 b Hence, often, an undesigned and unforeseen occurrence of an afflictive or unfortunate character, a llll.Shap resulting in injury to a person or damage to a thing, a casualty, as to die by an accident Having defined the word, I'll now proceed by relating an interesting, minor, but nevertheless quite important episode of the war in the Pacific Theatre during WWII, and I will introduce the acrount of that episode by saying that: During the W'lr, the President of the United States, Chief of' Sta.ff of the Ar1ff3' 1 the Commander-in-Chief' of the U.S. -

Female Mtis Celebrate Women's History Month
A PUBLICATION OF THE 502nd AIR BASE WING JOINT BASE SAN ANTONIO-LACKLAND, TEXAS • Vol. 72 No. 13 • April 3, 2015 Female MTIs celebrate Women's History Month Photo by Benjamin Faske In honor of Women’s History Month, an all-female fl ight of military training instructors marched down the bomb run during the Basic Military Training graduation, March 27. All of the leadership positions for the entire parade were fi lled by female military training instructors. INSIDE | Commentary 2 News 3 Community Briefs 10 Sports 16 ONLINE | http://www.jbsa.af.mil PAGE 2 commentary TALESPINNER April 3, 2015 Joint Base San Antonio- Lackland Make a list, check it twice: Editorial Staff BRIG. GEN. BOB LABRUTTA 502ND AIR BASE WING/JBSA Ensure your day counts! COMMANDER TODD G. WHITE 502ND AIR BASE WING/JBSA By Lt. Col. David Woodley backs, and things will not always go our have given up. PUBLIC AFFAIRS DIRECTOR 71st OSS commander, Vance Air Force Base, Okla. way. It will happen more than we want. Why? Most set a goal of something like How do you overcome these obstacles? losing 50 pounds. Great goal, but it will OSCAR BAllADARES ach day is a gift, and we need to I use the 24 hour rule. not happen overnight. So most people JBSA-LacKLAND PUBLIC AFFAIRS CHIEF ensure we make every day count After a setback give yourself 24 hours will focus on losing that 50 pounds, and to the fullest. But with everything to get mad, reflect and accept. in four weeks, when they only lose eight SENIOR AIRMAN LYNSIE NICHOLS E EDITOR else in life, many people do not know Get mad that it happened. -

Enigma Sim Manual
ENIGMA SIM MANUAL About the Enigma Sim The program is an exact simulation of the 3-rotor Wehrmacht & Luftwaffe, the 3-rotor Kriegsmarine M3, and the famous 4-rotor Kriegsmarine M4 model of the German Enigma cipher machine, as they were used during World War II from 1939 until 1945. You can select between the three models, choose different rotors or 'Walzen', preset the rotor wiring positions or 'Ringstellung' and switch letters by using plugs or 'Stecker'. The internal wiring of all rotors is identical to those used by the Wehrmacht, Luftwaffe and Kriegsmarine. This simulator is therefore fully compatible with the real Enigma-machine and you can decipher original messages and encipher your own messages. This manual explains how to use the Enigma simulator, describes the message procedures as used by the German Armed Forces, a complete technical description and a brief history of the Enigma. For more information, please visit Cipher Machines & Cryptology http://users.telenet.be/d.rijmenants Copyright Information THE ENIGMA SIMULATOR SOFTWARE IS FREEWARE AND CAN BE USED AND DISTRIBUTED UNDER THE FOLLOWING RESTRICTIONS: IT IS STRICTLY FORBIDDEN TO USE THIS SOFTWARE OR COPIES OR PARTS OF IT FOR COMMERCIAL PURPOSES, OR TO SELL, LEASE OR MAKE PROFIT FROM THIS PROGRAM BY ANY MEANS. THIS SOFTWARE MAY ONLY BE USED IF YOU AGREE TO THESE CONDITIONS. Picture Gallery Copyrights: © Tom Perera, Enigma Museum - http://w1tp.com/mcpu.htm © KMi The Open University DISCLAIMER OF WARRANTIES THIS SOFTWARE AND THE ACCOMPANYING FILES ARE SUPPLIED "AS IS" AND WITHOUT WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, WITH RESPECT TO THIS PRODUCT, ITS QUALITY, PERFORMANCE, MERCHANTABILITY, OR FITNESS FOR ANY PARTICULAR PURPOSE. -

Part I History and Machines of Cryptography
Part I History and machines of cryptography CHAPTER 14: MACHINES and HISTORY of CRYPTOGRAPHY MACHINES and HISTORY of CRYPTOGRAPHY IV054 1. History and machines of cryptography 2/78 PROLOGUE PROLOGUE IV054 1. History and machines of cryptography 3/78 WHAT to VALUE MORE As information becomes an increasingly valuable commodity, the encryption is the only way to protect our privacy and guarantee the success of the e-business. Some groups, for example businessmen and civil libertarians, require strong cryptography. The forces of law and order are pressing governments to restrict the use of cryptography. What to value more? Personal freedom? or the order and law? IV054 1. History and machines of cryptography 4/78 WHO are CODEBREAKERS The vision of codebreakers has changed through the history, depending on the tools used for encryption and cryptanalysis. Before computer era views; Codebreakers or cryptanalysts are linguistic alchemists, a mystical tribe attempting to conjure sensible words out of meaningless symbols. Current view: Codebreakers and cryptanalyst's are artists that can superbly use modern mathematics, informatics and computing super-technology. Three views of the history First World War was the war of chemists (deadly gases). Second World War was the war of physicists (atomic bombs) Third World War would be the war of informaticians (cryptographers and cryptanalysts). IV054 1. History and machines of cryptography 5/78 PERIODS of the HISTORY of CRYPTOGRAPHY Prehistory - before nontrivial machines period: till about 1930 - no electrical