Email Delivery Terminology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MTA STS Improving Email Security.Pdf
Improving Email Security with the MTA-STS Standard By Brian Godiksen An Email Best Practices Whitepaper CONTENTS Executive Overview 03 Why Does Email Need Encryption in Transit? 04 The Problem with “Opportunistic Encryption” 07 The Anatomy of a Man-in-the-Middle Attack 08 The Next Major Step with Email Encryption: MTA-STS 10 What Steps Should Senders Take to Adopt MTA-STS? 11 About SocketLabs 12 Brian Godiksen Brian has been helping organizations optimize email deliverability since joining SocketLabs in 2011. He currently manages a team of deliverability analysts that consult with customers on best infrastructure practices, including email authentication implementation, bounce processing, IP address warm-up, and email marketing list management. Brian leads the fight against spam and email abuse at SocketLabs by managing compliance across the platform. He is an active participant in key industry groups such as M3AAWG and the Email Experience Council. You can read more of Brian’s content here on the SocketLabs website. ©2019 SocketLabs 2 Executive The Edward Snowden leaks of 2013 opened many peoples’ eyes to the fact that mass surveillance was possible by Overview intercepting and spying on email transmissions. Today, compromised systems, database thefts, and technology breaches remain common fixtures in news feeds around the world. As a natural response, the technology industry is rabidly focused on improving the security and encryption of communications across all platforms. Since those early days of enlightenment, industry experts have discussed and attempted a variety of new strategies to combat “pervasive monitoring” of email channels. While pervasive monitoring assaults can take many forms, the most prominent forms of interference were man-in-the-middle (MitM) attacks. -

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

Delivering Results to the Inbox Sailthru’S 2020 Playbook on Deliverability, Why It’S Imperative and How It Drives Business Results Introduction to Deliverability
Delivering Results to the Inbox Sailthru’s 2020 Playbook on Deliverability, Why It’s Imperative and How It Drives Business Results Introduction to Deliverability Every day, people receive more than 293 billion Deliverability is the unsung hero of email marketing, emails, a staggering number that only represents ultimately ensuring a company’s emails reach their the tip of the iceberg. Why? The actual number intended recipients. It’s determined by a host of of emails sent is closer to 5.9 quadrillion, with the factors, including the engagement of your subscribers overwhelming majority blocked outright or delivered and the quality of your lists. All together, these factors to the spam folder. result in your sender reputation score, which is used to determine how the ISPs treat your email stream. Something many people don’t realize is that to the Deliverability is also a background player, so far in the major Internet Service Providers (ISPs) — Gmail, shadows that many people don’t think about it, until Yahoo!, Hotmail, Comcast and AOL — “spam” there’s a major issue. doesn’t refer to marketing messages people may find annoying, but rather malicious email filled with That’s why Sailthru’s deliverability team created this scams and viruses. In order to protect their networks guide. Read on to learn more about how deliverability and their customers, the ISPs cast a wide net. If a works on the back-end and how it impacts revenue, message is deemed to be spam by the ISP’s filters, it’s your sender reputation and how to maintain a good dead on arrival, never to see the light of the inbox, as one, and best practices for list management, email protecting users’ inboxes is the top priority of any ISP. -

Spam, Spammers, and Spam Control a White Paper by Ferris Research March 2009
Spam, Spammers, and Spam Control A White Paper by Ferris Research March 2009. Report #810 Ferris Research, Inc. One San Antonio Place San Francisco, Calif. 94133, USA Phone: +1 (650) 452-6215 Fax: +1 (408) 228-8067 www.ferris.com Table of Contents Spam, Spammers, and Spam Control................................................3 Defining Spam.................................................................................3 Spammer Tactics .............................................................................3 Sending Mechanisms.................................................................4 Spammer Tricks.........................................................................4 Techniques for Identifying Spam ....................................................5 Connection Analysis..................................................................5 Behavioral Analysis...................................................................6 Content Scanning.......................................................................6 Controlling Spam: How and Where ................................................7 The Key Role of Reputation Services .......................................7 Conclusion: An Arms Race.............................................................8 Trend Micro Interview........................................................................9 Ferris Analyzer Information Service. Report #810. March 2009. © 2009 Ferris Research, Inc. All rights reserved. This document may be copied or freely reproduced provided you -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
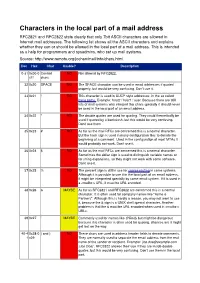
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

Idns: Internationalized Domain Names Did You Know?
I N T E R N E T C O R P O R AT I O N F O R A SS I G N E D N A M E S A N D N U M B E R S IDNs: Internationalized Domain Names Did you know? · Internationalized Domain Names (IDNs) are domain names with characters other than a, b…, z; 0, 1,…, 9; and “-“. · IDNs on the second and third levels exist in some generic top-level domains (gTLDs) and in some country code top-level domains (ccTLDs). TLD registries determine the choice of characters available under these TLDs. · Some languages, like Arabic, are written from right to left. IDNs at the second level are not very useful for the communities that use these languages because users would need to change both the type direction and script in the middle of entering a domain name. · IDN TLDs will be made available through two separate processes, initially through the New gTLD Program and the IDN ccTLD Fast Track Process. · 60 percent of Internet users are non-English speakers, while the dominant language used on the Internet is English (see Global Reach at www.glreach.com). One of the most significant innovations in the Internet since its incep- tion is the introduction of Internationalized Domain Names (IDNs) in the Internet’s address space. You may be familiar with some of the larger top- level domains: dot-com, dot-cn, and dot-org are just three examples. IDN top-level domain names will offer many new opportunities and benefits for Internet users around the world by allowing them to establish and use domains in their native languages and scripts. -

How to Add an Email Address to Your Safe Senders' List
How to Add an Email Address to your Safe Senders' List An increasing number of e-mail clients (Outlook, AOL, Hotmail, etc.) are including spam blockers that can affect delivery and display of some e-mail messages. This means that sometimes those desired e-mail communications might not reach you, or they might be displayed without images. To ensure that you continue receiving your e-mail or your subscriptions, and that they display properly, we recommend adding the email address or domain to your list of safe senders. Here are some instructions to help you do that: Instructions regarding email clients Apple Mail • Add the email address to your address book. • In Training mode, emails will arrive in the INBOX highlighted in brown. In Automatic mode, junk emails will arrive in the Junk box. To add an email that arrived in the JUNK folder, highlight the email message. • Choose Message > Mark > As Not Junk Mail AOL For AOL version 9.0: You can ensure that valued e-mail is delivered to your Inbox by adding the sending address to your "People I Know" list. • Open your latest issue of Brill’s E-Newsletter. • Click the Add Address button (over on the right) to add that sender to your "People IKnow" list. Alternatively, you can simply send an e-mail to [email protected]. Even if the e-mail you send doesn't get through (for whatever reason), the act of sending it does the job of putting the address into your "People I Know" list--and that's what counts. -

Going Live Tutorial Contents
Going Live Tutorial Contents Going Live with Your Online Business 1 Let’s Get Started 2 Domain names, IP addresses and DNS 2 Some advanced terminology 3 Going Live Step by Step 5 1. Getting a domain name 5 2. Setting up your domain & its email settings 5 2a. Adding your domain name to the system 5 2b. Email settings for your domain 7 3. Setting up email 8 3a. Creating mailboxes 8 3b. Creating aliases 8 4. Pointing your domain to us 9 5. Setting up your email client 10 For Advanced Users - using an external DNS service 11 Going Live with Your Online Business When your site is looking hot and you’re ready to rock, you’ll want to take your site out of trial mode and make it live. Taking a site live means a few things: You’re ready to pay for your site. You’re ready to buy a domain name (www.mybusiness.com) and allow people to access your site by typing that address into their web browser. OR you’ve got a domain name that currently goes to your old site, and you want to switch it over to your brand-spanking-new online business. Who is this for? This guide is for anyone who’s ready to take their site live and show it off to the world! Some sections can be skipped by those with more advanced knowledge - these sections will be marked accordingly. Business Catalyst • Going Live Tutorial 1 Let’s Get Started Domain names, IP addresses and DNS If you already know what a domain name is, what an IP address is and how DNS works, you can skip this section. -

Email Authentication Faqs V3
Email Authentication GUIDE Frequently Asked QUES T ION S T OGETHER STRONGER EMAIL AUTHENTICATION Marketers that use email for communication and transactional purposes should adopt and use identification and authentication protocols.” This document will explain what authentication is – includ- ing some recommendations on what you should do as an email marketer to implement these guidelines within your organization. * This Guide should not be considered as legal advice. It is being provided for informational purposes only. Please review your email program with your legal counsel to ensure that your program is meeting appropriate legal requirements. THIS COMPLIANCE GUIDE COVERS: Basics of Email Authentication Technologies Basic FAQs on the DMA’s Email Authentication Guidelines Implementation: Complementary Types of Email Authentication Systems Beyond Authentication: Email Reputation Email Authentication Resources for Marketers 1. What Do the DMA’s Email Authentication Guidelines Require? The DMA’s guidelines require marketers to choose and implement authentication technolo- gies in their email systems. It is up to your company to decide what kind of authentication protocol to use, though all are recommended based on current-day trends. The DMA does not require nor endorse the use of any specific protocol, as there are several interoperable, inexpensive, and easy to implement solutions available today. 2. Why does the DMA Require Members to Authenticate Their Email Systems? The DMA requires its members to authenticate their email systems primarily because mailbox providers (aka ISPs, MSPs or receivers) are increasingly requiring authentication. This strongly aligns with a growing trend in the email deliverability industry that’s leaning more towards domain-based reputation (as opposed to IP-based reputation a couple of years ago). -
Best Php Webmail Software
Best php webmail software Get the answer to "What are the best self-hosted webmail clients? in your config/ file) if you need messages to appear instantly. Free and open source webmail software for the masses, written in PHP. Install it on your web servers for personal or commercial use, redistribute, integrate with other software, or alter the source code (provided that. These clients can work under many types of platforms such as PHP, ASP Here, we have compiled a collection of seven webmail. SquirrelMail is one of the best webmail clients written purely in PHP. It supports basic email protocols such as SMTP, IMAP, and others. Webmail's software's are scripts which run on your servers and give you browser based mail client interface like Gmail, Yahoo etc. There are. For this roundup we have compiled a list of Best Webmail Clients for both T-dah is a free PHP webmail application which is built from the. Hastymail2 is a full featured IMAP/SMTP client written in PHP. Our goal is to create a fast, secure, compliant web mail client that has great usability. Hastymail2 is much more lightweight than most popular web based mail applications but still. RainLoop Webmail - Simple, modern & fast web-based email client. Also known as “Horde IMP”, Horde Mail is a free and open source web-mail client written in PHP. Its development started in , so it's a. Check out these 10 amazing webmail clients worth considering and see how In today's article, we're going to highlight some of the best webmail clients It's free to use and can be installed on any server that supports PHP. -

WHITE PAPER Email Deliverability Review
WHITE PAPER Email DELIVeraBility REView dmawe are the White Paper Email Deliverability Review Published by Deliverability Hub of the Email Marketing Council Sponsored by 1 COPYRIGHT: THE DIRECT MARKETING ASSOCIATION (UK) LTD 2012 WHITE PAPER Email DELIVeraBility REView Contents About this document ...............................................................................................................................3 About the authors ...................................................................................................................................4 Sponsor’s perspective .............................................................................................................................5 Executive summary .................................................................................................................................6 1. Major factors that impact on deliverability ..............................................................................................7 1.1 Sender reputation .............................................................................................................................7 1.2 Spam filtering ...................................................................................................................................7 1.3 Blacklist operators ............................................................................................................................8 1.4 Smart Inboxes ..................................................................................................................................9