Linux Journal | February 2010 | Issue
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ultumix GNU/Linux 0.0.1.7 32 Bit!
Welcome to Ultumix GNU/Linux 0.0.1.7 32 Bit! What is Ultumix GNU/Linux 0.0.1.7? Ultumix GNU/Linux 0.0.1.7 is a full replacement for Microsoft©s Windows and Macintosh©s Mac OS for any Intel based PC. Of course we recommend you check the system requirements first to make sure your computer meets our standards. The 64 bit version of Ultumix GNU/Linux 0.0.1.7 works faster than the 32 bit version on a 64 bit PC however the 32 bit version has support for Frets On Fire and a few other 32 bit applications that won©t run on 64 bit. We have worked hard to make sure that you can justify using 64 bit without sacrificing too much compatibility. I would say that Ultumix GNU/Linux 0.0.1.7 64 bit is compatible with 99.9% of all the GNU/Linux applications out there that will work with Ultumix GNU/Linux 0.0.1.7 32 bit. Ultumix GNU/Linux 0.0.1.7 is based on Ubuntu 8.04 but includes KDE 3.5 as the default interface and has the Mac4Lin Gnome interface for Mac users. What is Different Than Windows and Mac? You see with Microsoft©s Windows OS you have to defragment your computer, use an anti-virus, and run chkdsk or a check disk manually or automatically once every 3 months in order to maintain a normal Microsoft Windows environment. With Macintosh©s Mac OS you don©t have to worry about fragmentation but you do have to worry about some viruses and you still should do a check disk on your system every once in a while or whatever is equivalent to that in Microsoft©s Windows OS. -

Asus Eee PC for Dummies
Index journal, 101 • Symbols and Numerics • KCalc, 100 > (greater than), redirecting output, 311 KNotes, 105 >> (greater thans), appending to a fi le, 311 Kontact, 100–101 | (vertical bar), directing output to KSnapshot, 102–103 another command, 311–312 PIM (Personal Information Manager), 2G Surf, 14 100–101 4G, 14–15 PIM icon, 99 4G Surf, 14–15 pop-up notes, 101, 105 701SD, 15 Screen Capture icon, 99 900 series, 15–18 to-do list, 101 901 and Beyond icon, 6 Accessories icon, 92, 99 1000 series, 18–19 account name, personalizing, 149 Acrobat Reader, 184. See also PDF readers Acronis True Image, 284 • A • Ad-Aware Free, 231 Adblock Plus, 60 AbiWord, 219–220 add-ons accessories, hardware. See also Firefox, 59–60 personalization Thunderbird, 95–96 Bluetooth, 254–255 Add/Remove Software, 163. See also carrying case, 249–251 installing; uninstalling case graphics, 255–256 Add/Remove Software icon, 147, 163 GPS (Global Positioning System), 259–261 address books, Thunderbird, 96. See also keyboards, 252–253 contact lists mice, 251–252 administrative privileges, 309 modems, 256–257 Advanced Mode, 295–301. See also monitors, 257–259 Easy Mode projectors, 257–259 Advanced Packaging Tool (APT), 204–205 skins (themes), 255–256 advertisements, blocking, 60 USB powered work light, 254 adware, 231 accessories, software. See also AIM, 65 personalization COPYRIGHTEDAll About MATERIAL Eee, 343 accessing, 99 Amarok music player/organizer, 139–140 Calculator, 100 Amazon, 22 Calculator icon, 99 Andreesen, Marc, 58 calendar, 101 Andrew K’s XP Games, 228 capturing -

Introduction to Fmxlinux Delphi's Firemonkey For
Introduction to FmxLinux Delphi’s FireMonkey for Linux Solution Jim McKeeth Embarcadero Technologies [email protected] Chief Developer Advocate & Engineer For quality purposes, all lines except the presenter are muted IT’S OK TO ASK QUESTIONS! Use the Q&A Panel on the Right This webinar is being recorded for future playback. Recordings will be available on Embarcadero’s YouTube channel Your Presenter: Jim McKeeth Embarcadero Technologies [email protected] | @JimMcKeeth Chief Developer Advocate & Engineer Agenda • Overview • Installation • Supported platforms • PAServer • SDK & Packages • Usage • UI Elements • Samples • Database Access FireDAC • Migrating from Windows VCL • midaconverter.com • 3rd Party Support • Broadway Web Why FMX on Linux? • Education - Save money on Windows licenses • Kiosk or Point of Sale - Single purpose computers with locked down user interfaces • Security - Linux offers more security options • IoT & Industrial Automation - Add user interfaces for integrated systems • Federal Government - Many govt systems require Linux support • Choice - Now you can, so might as well! Delphi for Linux History • 1999 Kylix: aka Delphi for Linux, introduced • It was a port of the IDE to Linux • Linux x86 32-bit compiler • Used the Trolltech QT widget library • 2002 Kylix 3 was the last update to Kylix • 2017 Delphi 10.2 “Tokyo” introduced Delphi for x86 64-bit Linux • IDE runs on Windows, cross compiles to Linux via the PAServer • Designed for server side development - no desktop widget GUI library • 2017 Eugene -

Linux: Come E Perchх
ÄÒÙÜ Ô ©2007 mcz 12 luglio 2008 ½º I 1. Indice II ½º Á ¾º ¿º ÈÖÞÓÒ ½ º È ÄÒÙÜ ¿ º ÔÔÖÓÓÒÑÒØÓ º ÖÒÞ ×Ó×ØÒÞÐ ÏÒÓÛ× ¾½ º ÄÒÙÜ ÕÙÐ ×ØÖÙÞÓÒ ¾ º ÄÒÙÜ ÀÖÛÖ ×ÙÔÔ ÓÖØØÓ ¾ º È Ð ÖÒÞ ØÖ ÖÓ ÓØ Ù×Ö ¿½ ½¼º ÄÒÙÜ × Ò×ØÐÐ ¿¿ ½½º ÓÑ × Ò×ØÐÐÒÓ ÔÖÓÖÑÑ ¿ ½¾º ÒÓÒ ØÖÓÚÓ ÒÐ ×ØÓ ÐÐ ×ØÖÙÞÓÒ ¿ ½¿º Ó׳ ÙÒÓ ¿ ½º ÓÑ × Ð ××ØÑ ½º ÓÑ Ð ½º Ð× Ñ ½º Ð Ñ ØÐ ¿ ½º ÐÓ ½º ÓÑ × Ò×ØÐÐ Ð ×ØÑÔÒØ ¾¼º ÓÑ ÐØØÖ¸ Ø×Ø ÐÖ III Indice ¾½º ÓÑ ÚÖ Ð ØÐÚ×ÓÒ ¿ 21.1. Televisioneanalogica . 63 21.2. Televisione digitale (terrestre o satellitare) . ....... 64 ¾¾º ÐÑØ ¾¿º Ä 23.1. Fotoritocco ............................. 67 23.2. Grafica3D.............................. 67 23.3. Disegnovettoriale-CAD . 69 23.4.Filtricoloreecalibrazionecolori . .. 69 ¾º ×ÖÚ Ð ½ 24.1.Vari.................................. 72 24.2. Navigazionedirectoriesefiles . 73 24.3. CopiaCD .............................. 74 24.4. Editaretesto............................. 74 24.5.RPM ................................. 75 ¾º ×ÑÔ Ô ´ËÐе 25.1.Montareundiscoounapenna . 77 25.2. Trovareunfilenelsistema . 79 25.3.Vedereilcontenutodiunfile . 79 25.4.Alias ................................. 80 ¾º × ÚÓÐ×× ÔÖÓÖÑÑÖ ½ ¾º ÖÓÛ×Ö¸ ÑÐ ººº ¿ ¾º ÖÛÐРгÒØÚÖÙ× Ð ÑØØÑÓ ¾º ÄÒÙÜ ½ ¿¼º ÓÑ ØÖÓÚÖ ÙØÓ ÖÖÑÒØ ¿ ¿½º Ð Ø×ØÙÐ Ô Ö Ð ×ØÓÔ ÄÒÙÜ ¿¾º ´ÃµÍÙÒØÙ¸ ÙÒ ×ØÖÙÞÓÒ ÑÓÐØÓ ÑØ ¿¿º ËÙÜ ÙÒ³ÓØØÑ ×ØÖÙÞÓÒ ÄÒÙÜ ½¼½ ¿º Á Ó Ò ÄÒÙÜ ½¼ ¿º ÃÓÒÕÙÖÓÖ¸ ÕÙ×ØÓ ½¼ ¿º ÃÓÒÕÙÖÓÖ¸ Ñ ØÒØÓ Ô Ö ½½¿ 36.1.Unaprimaocchiata . .114 36.2.ImenudiKonqueror . .115 36.3.Configurazione . .116 IV Indice 36.4.Alcuniesempidiviste . 116 36.5.Iservizidimenu(ServiceMenu) . 119 ¿º ÃÓÒÕÙÖÓÖ Ø ½¾¿ ¿º à ÙÒ ÖÖÒØ ½¾ ¿º à ÙÒ ÐÙ×ÓÒ ½¿½ ¼º ÓÒÖÓÒØÓ Ò×ØÐÐÞÓÒ ÏÒÓÛ×È ÃÍÙÒØÙ º½¼ ½¿¿ 40.1. -

Praise for the Official Ubuntu Book
Praise for The Official Ubuntu Book “The Official Ubuntu Book is a great way to get you started with Ubuntu, giving you enough information to be productive without overloading you.” —John Stevenson, DZone Book Reviewer “OUB is one of the best books I’ve seen for beginners.” —Bill Blinn, TechByter Worldwide “This book is the perfect companion for users new to Linux and Ubuntu. It covers the basics in a concise and well-organized manner. General use is covered separately from troubleshooting and error-handling, making the book well-suited both for the beginner as well as the user that needs extended help.” —Thomas Petrucha, Austria Ubuntu User Group “I have recommended this book to several users who I instruct regularly on the use of Ubuntu. All of them have been satisfied with their purchase and have even been able to use it to help them in their journey along the way.” —Chris Crisafulli, Ubuntu LoCo Council, Florida Local Community Team “This text demystifies a very powerful Linux operating system . in just a few weeks of having it, I’ve used it as a quick reference a half dozen times, which saved me the time I would have spent scouring the Ubuntu forums online.” —Darren Frey, Member, Houston Local User Group This page intentionally left blank The Official Ubuntu Book Sixth Edition This page intentionally left blank The Official Ubuntu Book Sixth Edition Benjamin Mako Hill Matthew Helmke Amber Graner Corey Burger With Jonathan Jesse, Kyle Rankin, and Jono Bacon Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris • Madrid Capetown • Sydney • Tokyo • Singapore • Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. -
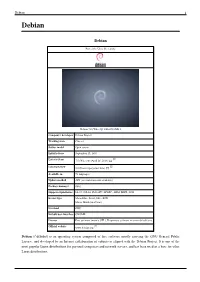
Debian 1 Debian
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -

LNCS 3532, Pp
Activity Based Metadata for Semantic Desktop Search Paul Alexandru Chirita, Rita Gavriloaie, Stefania Ghita, Wolfgang Nejdl, and Raluca Paiu L3S Research Center / University of Hanover, Deutscher Pavillon, Expo Plaza 1, 30539 Hanover, Germany {chirita, gavriloaie, ghita, nejdl, paiu}@l3s.de Abstract. With increasing storage capacities on current PCs, searching the World Wide Web has ironically become more efficient than searching one’s own per- sonal computer. The recently introduced desktop search engines are a first step towards coping with this problem, but not yet a satisfying solution. The reason for that is that desktop search is actually quite different from its web counter- part. Documents on the desktop are not linked to each other in a way compara- ble to the web, which means that result ranking is poor or even inexistent, be- cause algorithms like PageRank cannot be used for desktop search. On the other hand, desktop search could potentially profit from a lot of implicit and explicit semantic information available in emails, folder hierarchies, browser cache con- texts and others. This paper investigates how to extract and store these activity based context information explicitly as RDF metadata and how to use them, as well as additional background information and ontologies, to enhance desktop search. 1 Introduction The capacity of our hard-disk drives has increased tremendously over the past decade, and so has the number of files we usually store on our computer. It is no wonder that sometimes we cannot find a document any more, even when we know we saved it somewhere. Ironically, in quite a few of these cases nowadays, the document we are looking for can be found faster on the World Wide Web than on our personal com- puter. -

Master Thesis Innovation Dynamics in Open Source Software
Master thesis Innovation dynamics in open source software Author: Name: Remco Bloemen Student number: 0109150 Email: [email protected] Telephone: +316 11 88 66 71 Supervisors and advisors: Name: prof. dr. Stefan Kuhlmann Email: [email protected] Telephone: +31 53 489 3353 Office: Ravelijn RA 4410 (STEPS) Name: dr. Chintan Amrit Email: [email protected] Telephone: +31 53 489 4064 Office: Ravelijn RA 3410 (IEBIS) Name: dr. Gonzalo Ord´o~nez{Matamoros Email: [email protected] Telephone: +31 53 489 3348 Office: Ravelijn RA 4333 (STEPS) 1 Abstract Open source software development is a major driver of software innovation, yet it has thus far received little attention from innovation research. One of the reasons is that conventional methods such as survey based studies or patent co-citation analysis do not work in the open source communities. In this thesis it will be shown that open source development is very accessible to study, due to its open nature, but it requires special tools. In particular, this thesis introduces the method of dependency graph analysis to study open source software devel- opment on the grandest scale. A proof of concept application of this method is done and has delivered many significant and interesting results. Contents 1 Open source software 6 1.1 The open source licenses . 8 1.2 Commercial involvement in open source . 9 1.3 Opens source development . 10 1.4 The intellectual property debates . 12 1.4.1 The software patent debate . 13 1.4.2 The open source blind spot . 15 1.5 Litterature search on network analysis in software development . -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

How-To Build Meteohub on Sheevaplug (The Easy Way)
How-To Build Meteohub on SheevaPlug (the easy way) The SheevaPlug is a low power, small form factor device that can be seen as the successor of the famous NSLU2. Meteohub has now been experimentally ported to the SheevaPlug. Please be aware that this port is rather alpha, but it seems to work. At the moment Meteohub on SheevaPlug has these limitations: ● no WebCam support: This is also not planned for the future ● no WLAN support: Might be added via USB WLAN sticks in the future (low priority) ● no Labjack support: unclear if this can be added by a home-brew kernel module, low priority Meteohub on SheevaPlug makes use of a SD card where operating system, Meteohub application and data are stored. Capacity is 4GB. It should be a SLC based card. As not all SD cards are working with the plug, you might have some experiments in front of you. SLC-based SD card that is proven to be working ● Transcend SDHC Class 6 150x: TS4GSDHC150 Weather stations are connected to the Meteohub by USB connector. This one USB port can be extended with an USB hub. It looks like it can be a passive USB hub, as the Meteohub provides the 500mA on USB and this should be enough to drive a few weather station USB connections and/or RS232-USB converter. Meteohub on SheevaPlug consumes about 5 watts , which is really effective. Meteohub's performance looks fine. It can do about 900 records per second during recomputation (NSLU2 is about 200, x86 Geode platforms are up to 2000). -

Instructions for the Preparation of a Camera-Ready Paper in MS Word
Review Semantic web; towards Ontology based Web Application Editor(s): Name Surname, University, Country Solicited review(s): Name Surname, University, Country Open review(s): Name Surname, University, Country Zeeshan Ahmed*, Saman Majeed Department of Bioinformatics, Biocenter, University of Wuerzburg, Am Hubland 97074, Wuerzburg Germany Abstract. In this review we address the importance of field i.e. Semantic Web; a mechanism of presenting information over the web in a format so that human being as well as machines can understand the semantic of context. Describing the techno- logical contributions of Semantic Web in detail, we present its main innovation i.e. Ontology, and development supporting technologies i.e. XML (eXtensible Mark-up Language), RDF (Resource Description Framework) and OWL (Web Ontology Language), offering different ways of more explicitly structuring and richly annotating Web pages. Furthermore, in this review paper, we discuss how ontology is contributing to semantic web development with the presentation of some Semantic Web application and conclude with some existing limitations need to be overcome. Keywords: Web, Ontology, Semantic Web 1. Introduction easy to go for scattered extensive information by looking into bookmarked web pages but quite diffi- Targeting the challenge of implementing a web cult to extract a piece of needed information. Al- based system capable of performing semantic based though some search engines and screen scrapers are search to extract desired information from attached invented, search -

ALT Linux Master 2.2 Руководство Системного Администратора
ALT Linux Master 2.2 Руководство системного администратора А. Боковой, И. Вергейчик, О. Власенко, М. Забалуев, Ю. Зотов, С. Иевлев, Д. Левин, И. Муратов, А. Новодворский, А. Орлов, А. Турбин ALT Linux Master 2.2: Руководство систем- ного администратора А. Боковой, И. Вергейчик, О. Власенко, М. Забалуев, Ю. Зотов, С. Иевлев, Д. Левин, И. Муратов, А. Новодворский, А. Орлов, А. Турбин Большую работу по редактированию книги осуществили: А. Астафьев А. Добровольский М. Шигорин Настоящая книга составлена из документов, распространяющихсяна условиях GNU Free Documentation License, версия 1.1. Каждый имеет право воспроизводить, распространять и/или вносить изменения в настоящий Документв соответствии с условиями этой лицензий. Данный Документ не содержит Неизменяемых разделов; Данный Документ не содержит текста, помещаемого на первой или последней страницах обложки. Часть I. Оборудование 2 Руководство системного администратора Глава 1. Общая информация Основная информация Linux поддерживает практически все современное оборудование для архитектуры x86, за исключением специально ориентированного на ОС Windows (например, так называемые winmodem и winprinter), а так- же продукцию тех производителей, которые по тем или иным причи- нам не желают давать спецификации на устройства для написания драйверов. Информация, предоставленная в этом руководстве, не претендует на полноту описания, поэтому, если вы не найдёте здесь ответа на интересующий вас вопрос, прежде чем писать в список рассылки ALT Linux1, рекомендуется посмотреть следующую документацию: 1. документация к ядру (пакет kernel-doc2); 2. FAQ и HOWTO по Linux можно найти в как в Интернете, так и в дистрибутиве; 3. поиск в Интернете по спискам конференций; 4. исходные коды это для тех, кто желает в них разобраться. С точки зрения системного администратора, задачей которого явля- ется настройка оборудования и проверка его работоспособности для Linux, устройства в первую очередь определяются своим типом, про- изводителем, затем способом подключения.