Risk Fluctuation Characteristics of Internet Finance: Combining Industry Characteristics with Ecological Value
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Crowdfunding in Asia
Crowdfunding in Asia May 2018 Introducing the first free directory of crowdfunding platforms across Asia. The data is based on the AlliedCrowds Capital Finder, a database of over 7,000 alternative finance capital providers across emerging markets. Our data has been used by organizations like FSD Asia, UNDP, World Green Economy Organization, GIZ, World Bank, and others in order to provide unique, actionable insights into the world of emerging market alternative finance. This is the latest of our regular reports on alternative finance in emerging markets; you can find all previous reports here. Crowdfunding rose in prominence in the post-financial crisis years (starting in 2012), and for good reason: a global credit crunch limited the amount of funding available to entrepreneurs and small businesses. Since then, crowdfunding has grown rapidly around the world. Crowdfunding is especially consequential in countries where SMEs find it difficult to raise capital to start or grow their businesses. This is the case in many Asian countries; according to the SME Finance Forum, there is a $2.3 trillion MSME credit gap in East Asia and the Pacific. Crowdfunding can help to fill this gap by offering individuals and small businesses an alternative source of capital. This can come in the form of donation-based as well as lending-based (peer-to-peer or peer-to-business) crowdfunding. In order to help entrepreneurs and small business owners to find the crowdfunding platform that’s right for them, we are releasing the first publicly available list of all crowdfunding platforms across Asia. The report is split into two key sections: the first one is an overview of crowdfunding platforms, and how active they are across the largest markets on the continent. -

HW&Co. Landscape Industry Reader Template
TECHNOLOGY, MEDIA, & TELECOM QUARTERLY SOFTWARE SECTOR REVIEW │ 3Q 2016 www.harriswilliams.com Investment banking services are provided by Harris Williams LLC, a registered broker-dealer and member of FINRA and SIPC, and Harris Williams & Co. Ltd, which is authorised and regulated by the Financial Conduct Authority. Harris Williams & Co. is a trade name under which Harris Williams LLC and Harris Williams & Co. Ltd conduct business. TECHNOLOGY, MEDIA, & TELECOM QUARTERLY SOFTWARE SECTOR REVIEW │ 3Q 2016 HARRIS WILLIAMS & CO. OVERVIEW HARRIS WILLIAMS & CO. (HW&CO.) GLOBAL ADVISORY PLATFORM CONTENTS . DEAL SPOTLIGHT . M&A TRANSACTIONS – 2Q 2016 KEY FACTS . SOFTWARE M&A ACTIVITY . 25 year history with over 120 . SOFTWARE SECTOR OVERVIEWS closed transactions in the . SOFTWARE PRIVATE PLACEMENTS last 24 months OVERVIEW . SOFTWARE PUBLIC COMPARABLES . Approximately 250 OVERVIEW professionals across seven . TECHNOLOGY IPO OVERVIEW offices in the U.S. and . DEBT MARKET OVERVIEW Europe . APPENDIX: PUBLIC COMPARABLES DETAIL . Strategic relationships in India and China HW&Co. Office TMT CONTACTS Network Office UNITED STATES . 10 industry groups Jeff Bistrong Managing Director HW&CO. TECHNOLOGY, MEDIA & TELECOM (TMT) GROUP FOCUS AREAS [email protected] Sam Hendler SOFTWARE / SAAS INTERNET & DIGITAL MEDIA Managing Director [email protected] . Enterprise Software . IT and Tech-enabled . AdTech and Marketing . Digital Media and Content Services Solutions Mike Wilkins . Data and Analytics . eCommerce Managing Director . Infrastructure and . Data Center and . Consumer Internet . Mobile [email protected] Managed Services Security Software EUROPE Thierry Monjauze TMT VERTICAL FOCUS AREAS Managing Director [email protected] . Education . Fintech . Manufacturing . Public Sector and Non-Profit . Energy, Power, and . Healthcare IT . Professional Services . Supply Chain, Transportation, TO SUBSCRIBE PLEASE EMAIL: Infrastructure and Logistics *[email protected] SELECT RECENT HW&CO. -

Starburst Enterprise on Google Cloud
SOLUTION BRIEF Starburst Enterprise on Google Cloud The Starburst Enterprise Difference As organizations scale up, Starburst Enterprise on Google Cloud drives Available on the Google Cloud Marketplace, the better business outcomes, consistency, and reliability, delighting your data Starburst Enterprise platform is a fully supported, engineers and scientists. Teams look to Starburst Enterprise on Google Cloud production-tested, enterprise-grade distribution for expertise & constant fine-tuning that results in overall lower costs & faster of the open source Trino MPP SQL query engine. time-to-insights: Starburst integrates Google’s scalable cloud storage and computing services with a more Performance: stable, secure, efficient, and cost-effective way Includes the latest optimizations; Starburst Cached Views available for to query all your enterprise data, wherever it frequently accessed data; stable code that minimizes failed queries. resides. Leading organizations across multiple industries Connectivity rely on Starburst Enterprise and Google. 40+ supported enterprise connectors; high performance connectors for Oracle, Teradata, Snowflake, IBM DB2, Delta Lake, and many more. Analytics Anywhere Designed for the separation of storage and Security compute, Trino is ideal for querying data residing in multiple systems, from cloud data lakes to Role-based access control (via Apache Ranger); Kerberos, OKTA, LDAP legacy data warehouses. Deployed via Google integration; data encryption & masking; query auditing to see who is doing what. Kubernetes Engine (GKE), Starburst Enterprise on Google Cloud enables the user to run analytic Management queries across Google Cloud data sources and on-prem systems such as Teradata, Oracle, Enhanced tools for configuration, auto scaling, and Starburst Insights and others via Trino clusters. Within a single monitoring dashboards; easy deployment on Google platforms. -

Understanding the Value of Arts & Culture | the AHRC Cultural Value
Understanding the value of arts & culture The AHRC Cultural Value Project Geoffrey Crossick & Patrycja Kaszynska 2 Understanding the value of arts & culture The AHRC Cultural Value Project Geoffrey Crossick & Patrycja Kaszynska THE AHRC CULTURAL VALUE PROJECT CONTENTS Foreword 3 4. The engaged citizen: civic agency 58 & civic engagement Executive summary 6 Preconditions for political engagement 59 Civic space and civic engagement: three case studies 61 Part 1 Introduction Creative challenge: cultural industries, digging 63 and climate change 1. Rethinking the terms of the cultural 12 Culture, conflict and post-conflict: 66 value debate a double-edged sword? The Cultural Value Project 12 Culture and art: a brief intellectual history 14 5. Communities, Regeneration and Space 71 Cultural policy and the many lives of cultural value 16 Place, identity and public art 71 Beyond dichotomies: the view from 19 Urban regeneration 74 Cultural Value Project awards Creative places, creative quarters 77 Prioritising experience and methodological diversity 21 Community arts 81 Coda: arts, culture and rural communities 83 2. Cross-cutting themes 25 Modes of cultural engagement 25 6. Economy: impact, innovation and ecology 86 Arts and culture in an unequal society 29 The economic benefits of what? 87 Digital transformations 34 Ways of counting 89 Wellbeing and capabilities 37 Agglomeration and attractiveness 91 The innovation economy 92 Part 2 Components of Cultural Value Ecologies of culture 95 3. The reflective individual 42 7. Health, ageing and wellbeing 100 Cultural engagement and the self 43 Therapeutic, clinical and environmental 101 Case study: arts, culture and the criminal 47 interventions justice system Community-based arts and health 104 Cultural engagement and the other 49 Longer-term health benefits and subjective 106 Case study: professional and informal carers 51 wellbeing Culture and international influence 54 Ageing and dementia 108 Two cultures? 110 8. -

Redeye-Gaming-Guide-2020.Pdf
REDEYE GAMING GUIDE 2020 GAMING GUIDE 2020 Senior REDEYE Redeye is the next generation equity research and investment banking company, specialized in life science and technology. We are the leading providers of corporate broking and corporate finance in these sectors. Our clients are innovative growth companies in the nordics and we use a unique rating model built on a value based investment philosophy. Redeye was founded 1999 in Stockholm and is regulated by the swedish financial authority (finansinspektionen). THE GAMING TEAM Johan Ekström Tomas Otterbeck Kristoffer Lindström Jonas Amnesten Head of Digital Senior Analyst Senior Analyst Analyst Entertainment Johan has a MSc in finance Tomas Otterbeck gained a Kristoffer Lindström has both Jonas Amnesten is an equity from Stockholm School of Master’s degree in Business a BSc and an MSc in Finance. analyst within Redeye’s tech- Economic and has studied and Economics at Stockholm He has previously worked as a nology team, with focus on e-commerce and marketing University. He also studied financial advisor, stockbroker the online gambling industry. at MBA Haas School of Busi- Computing and Systems and equity analyst at Swed- He holds a Master’s degree ness, University of California, Science at the KTH Royal bank. Kristoffer started to in Finance from Stockholm Berkeley. Johan has worked Institute of Technology. work for Redeye in early 2014, University, School of Business. as analyst and portfolio Tomas was previously respon- and today works as an equity He has more than 6 years’ manager at Swedbank Robur, sible for Redeye’s website for analyst covering companies experience from the online equity PM at Alfa Bank and six years, during which time in the tech sector with a focus gambling industry, working Gazprombank in Moscow he developed its blog and on the Gaming and Gambling in both Sweden and Malta as and as hedge fund PM at community and was editor industry. -

Next-Gen Technology Transformation in Financial Services
April 2020 Next-gen Technology transformation in Financial Services Introduction Financial Services technology is currently in the midst of a profound transformation, as CIOs and their teams prepare to embrace the next major phase of digital transformation. The challenge they face is significant: in a competitive environment of rising cost pressures, where rapid action and response is imperative, financial institutions must modernize their technology function to support expanded digitization of both the front and back ends of their businesses. Furthermore, the current COVID-19 situation is putting immense pressure on technology capabilities (e.g., remote working, new cyber-security threats) and requires CIOs to anticipate and prepare for the “next normal” (e.g., accelerated shift to digital channels). Most major financial institutions are well aware of the imperative for action and have embarked on the necessary transformation. However, it is early days—based on our experience, most are only at the beginning of their journey. And in addition to the pressures mentioned above, many are facing challenges in terms of funding, complexity, and talent availability. This collection of articles—gathered from our recent publishing on the theme of financial services technology—is intended to serve as a roadmap for executives tasked with ramping up technology innovation, increasing tech productivity, and modernizing their platforms. The articles are organized into three major themes: 1. Reimagine the role of technology to be a business and innovation partner 2. Reinvent technology delivery to drive a step change in productivity and speed 3. Future-proof the foundation by building flexible and secure platforms The pace of change in financial services technology—as with technology more broadly—leaves very little time for leaders to respond. -

Miniclip Free Games to Download
Miniclip free games to download Downloadable Games. Play 3 Foot Ninja 3 Foot Ninja Download · Play 3FootNinja 2 3FootNinja 2 Download · Play Slacking Slacking Download · Play Alien. Play Free Online Games, fun games, puzzle games, action games, sports you can try the games for free on Miniclip and then download them to your iPhone. 8 Ball Pool - Miniclip, free and safe download. 8 Ball Pool - Miniclip latest version: Free and addictive Multiplayer Pool Game. 8 Ball Pool - Miniclip is one of. Download 8 Ball Pool - Miniclip for Windows now from Softonic: % safe Free pool game with realistic physics A Full Version Sport game for Windows. Top Download Free Games by , Free Online Games, Adventure Games, Shooting Games, Action Games, Arcade Games, Sports Games, Racing. Find Miniclip software downloads at CNET , the most games are extremely popular because they are fun, free, high quality. Miniclip Roll on Miniclip War on Angry Gran Toss Free Run, Free Kick Expert. Free Board, 3G Free Kick, Free Kicker, A Game About Kingdoms CCG. All Games from Miniclip. Games from Miniclip. Sorted by date | Sorted by total downloads | Sorted by last week downloads Miniclip Alien Attack Updated: 07/29/ Miniclip FREE GAMES DOWNLOAD - PC Games Free Download. How to Download Miniclip Games. You can download Miniclip games, free and legitimately. Downloading "Miniclip games" is simple to do on a computer or on. This video is showing how to Download Miniclip Games Link: If you want to use the. Free download. Vote: 1 2 3 4 5 As a single player "practice" game, 8 Ball Pool stands up quite well. -

Chinese Corporate Acquisitions in Sweden: a Survey Jerker Hellström, Oscar Almén, Johan Englund
Chinese corporate acquisitions in Sweden: A survey Jerker Hellström, Oscar Almén, Johan Englund Main conclusions • This survey has resulted in the first comprehensive and openly accessible compilation of Chinese corporate acquisitions in Sweden. • The audit has identified 51 companies in Sweden in which Chinese (including Hong Kong) companies have acquired a majority ownership. In addition, the survey has identified another 14 minority acquisitions. • Zhejiang Geely’s acquisition of a minority stake in Swedish truck-maker AB Volvo was among the largest Chinese acquisitions completed in Europe and North America in 2018. • Through these acquisitions, Chinese investors have taken control of at least some one hundred subsidiaries. • Most of the identified acquisitions were made since 2014. The highest annual amount of acquisitions was recorded in 2017. • The majority of the acquired companies belong to the following five sectors: industrial products and machinery, health and biotechnology, information and communications technology (ICT), electronics, and the automotive industry. • For nearly half of the acquired companies, there is a correlation between their operations and the technology sectors highlighted in the “Made in China 2025” plan for China's national industrial development. The sectors included in the plan are of particular importance to the Chinese state. • This survey includes several companies that have not been identified as Chinese acquisitions in previous compilations of Chinese investments. • More than 1,000 companies have reported to Sweden’s Companies Registration Office that their beneficial owner is a citizen of either China or Hong Kong. For the majority of these companies, however, the Chinese ownership is not a result of an acquisition. -

Are3na Crabbé Et Al
ARe3NA Crabbé et al. (2014) AAA for Data and Services (D1.1.2 & D1.2.2): Analysing Standards &Technologies for AAA ISA Action 1.17: A Reusable INSPIRE Reference Platform (ARE3NA) Authentication, Authorization & Accounting for Data and Services in EU Public Administrations D1.1.2 & D1.2.2– Analysing standards and technologies for AAA Ann Crabbé Danny Vandenbroucke Andreas Matheus Dirk Frigne Frank Maes Reijer Copier 0 ARe3NA Crabbé et al. (2014) AAA for Data and Services (D1.1.2 & D1.2.2): Analysing Standards &Technologies for AAA This publication is a Deliverable of Action 1.17 of the Interoperability Solutions for European Public Admin- istrations (ISA) Programme of the European Union, A Reusable INSPIRE Reference Platform (ARE3NA), managed by the Joint Research Centre, the European Commission’s in-house science service. Disclaimer The scientific output expressed does not imply a policy position of the European Commission. Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use which might be made of this publication. Copyright notice © European Union, 2014. Reuse is authorised, provided the source is acknowledged. The reuse policy of the European Commission is implemented by the Decision on the reuse of Commission documents of 12 December 2011. Bibliographic Information: Ann Crabbé, Danny Vandenbroucke, Andreas Matheus, Dirk Frigne, Frank Maes and Reijer Copier Authenti- cation, Authorization and Accounting for Data and Services in EU Public Administrations: D1.1.2 & D1.2.2 – Analysing standards and technologies for AAA. European Commission; 2014. JRC92555 1 ARe3NA Crabbé et al. (2014) AAA for Data and Services (D1.1.2 & D1.2.2): Analysing Standards &Technologies for AAA Contents 1. -
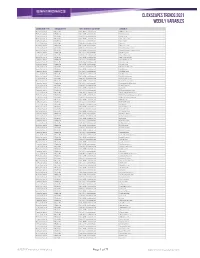
Clickscapes Trends 2021 Weekly Variables
ClickScapes Trends 2021 Weekly VariableS Connection Type Variable Type Tier 1 Interest Category Variable Home Internet Website Arts & Entertainment 1075koolfm.com Home Internet Website Arts & Entertainment 8tracks.com Home Internet Website Arts & Entertainment 9gag.com Home Internet Website Arts & Entertainment abs-cbn.com Home Internet Website Arts & Entertainment aetv.com Home Internet Website Arts & Entertainment ago.ca Home Internet Website Arts & Entertainment allmusic.com Home Internet Website Arts & Entertainment amazonvideo.com Home Internet Website Arts & Entertainment amphitheatrecogeco.com Home Internet Website Arts & Entertainment ancestry.ca Home Internet Website Arts & Entertainment ancestry.com Home Internet Website Arts & Entertainment applemusic.com Home Internet Website Arts & Entertainment archambault.ca Home Internet Website Arts & Entertainment archive.org Home Internet Website Arts & Entertainment artnet.com Home Internet Website Arts & Entertainment atomtickets.com Home Internet Website Arts & Entertainment audible.ca Home Internet Website Arts & Entertainment audible.com Home Internet Website Arts & Entertainment audiobooks.com Home Internet Website Arts & Entertainment audioboom.com Home Internet Website Arts & Entertainment bandcamp.com Home Internet Website Arts & Entertainment bandsintown.com Home Internet Website Arts & Entertainment barnesandnoble.com Home Internet Website Arts & Entertainment bellmedia.ca Home Internet Website Arts & Entertainment bgr.com Home Internet Website Arts & Entertainment bibliocommons.com -

Crowdlending in Asia: Landscape and Investor Characteristics
Crowdlending in Asia: Landscape and Investor Characteristics November 2020 2 Table of Contents Overview 3 Methodology Overview 4 Methodology Statement 4 Crowdlending in Asia 5 Text Analytics and Insights 7 Crowdlending Investor Characteristics 15 Survey Analysis and Insights 16 Crowdlending in Asia: Landscape and Investor Characteristics | Findings and Insights | Findings and insights 3 Overview Multiple issues arise with the emergence of crowdlending; these pertain to regulation, risk management and investors’ behaviour. Compared to the non-investment crowdfunding model, crowdlending is the dominant model in the world. As of 2019, crowdlending accounted for more than 95% of the funds raised worldwide, with Asian countries – particularly China – in the lead. In early 2020, China had the largest volume of money-raising transactions from crowdfunding totalling more than 200 billion USD. However, given the industry’s potential growth in Asian countries, multiple issues with crowdfunding practices need to be resolved. Media coverage on crowdlending is increasingly widespread, as seen from how it has become a buzzword within the last few years. Media attention on crowdlending can help us understand media awareness, media framing, and public understanding of the topic. Further, there is a lack of information on distinct characteristics and decision making of crowdfunding investors in the field of investor behaviour. We analysed the news coverage on crowdlending in Asia spanning a ten-year period from 2009 to 2019. We also surveyed crowdlending investors to understand their behaviours when interacting with crowdlending platforms. Our analyses provide insights into the challenges and opportunities of the crowdlending industry in Asia. They also reveal crowdlending investors’ behaviour. -

CIAM Platforms LEADERSHIP COMPASS
KuppingerCole Report LEADERSHIP COMPASS by John Tolbert December 2018 CIAM Platforms This report provides an overview of the market for Consumer Identity and AcCess Management and provides you with a Compass to help you to find the Consumer Identity and ACCess Management produCt that best meets your needs. We examine the market segment, vendor product and service functionality, relative market share, and innovative approaChes to providing CIAM solutions. by John Tolbert [email protected] December 2018 Leadership Compass CIAM Platforms KuppingerCole Leadership Compass CIAM Platforms By KuppingerCole Report No.: 79059 Content 1 Introduction .................................................................................................................................... 6 1.1 Market Segment ...................................................................................................................... 7 1.2 Delivery models ....................................................................................................................... 9 1.3 Required Capabilities .............................................................................................................. 9 2 Leadership .................................................................................................................................... 12 3 Correlated View ............................................................................................................................ 20 3.1 The Market/Product Matrix .................................................................................................