Master of Public Management Part-Time Courses Big-Time Career Impact
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Changing Lives: Engaging People, Places and Systems to Improve Health Outcomes, 2014
Changing Lives Engaging People, Places and Systems to Improve Health Outcomes 2014 Highmark Foundation Giving Report www.highmarkfoundation.org The image on the cover of this report is meant to represent positive change and improvement, and speaks directly to the positive impact the Foundation has on the people and communities it serves. 1 Changing Lives: Engaging People, Places and Systems to Improve Health Outcomes Mission The Highmark Foundation is a private, charitable organization of Highmark Inc. that supports initiatives and programs aimed at improving community health. The Foundation’s mission is to improve the health, well-being and quality of life for individuals who reside in the communities served by Highmark Inc. The Foundation strives to support evidence-based programs that impact multiple counties and work collaboratively to leverage additional funding to achieve replicable models. For more information, visit www.highmarkfoundation.org. Contents Board Members and Officers 3 Introduction to the Highmark Foundation 4 Highmark Foundation Grants 8 Highmark Foundation in the News 18 2014 Highmark Foundation Giving Report 1 The Highmark Foundation was established in 2000 to improve The initiatives funded by the Foundation fall within four the health and well-being of people living in the diverse categories: chronic disease, family health, service delivery communities served by Highmark Inc. We do this by awarding systems and healthy communities. These are the areas where high-impact grants to charitable organizations, hospitals and we have seen the greatest needs and remain our primary schools that develop programs to advance community health. areas of focus. The Foundation’s greatest successes are strong partnerships As we look ahead to 2015 and beyond, the Foundation with regional, national and global organizations with similar remains committed to improving the health and well-being missions, working to raise awareness of community health of communities throughout Pennsylvania and West Virginia. -

Student Handbook 2020-2021
Student Handbook 2020-2021 Master of Science in Public Policy and Management Two Year Track Three Semester Track Data Analytics Track Global Track 1 Contents 1 INTRODUCTION .................................................................................................................................. 4 2 Mission statement ................................................................................................................................... 4 3 CURRICULUM ..................................................................................................................................... 4 3.1 MSPPM Requirements .............................................................................................................. 5 3.2 MSPPM Two-Year Track Requirements .................................................................................. 5 3.3 MSPPM Three-Semester Track Requirements ......................................................................... 6 3.4 MSPPM-Data Analytics Track Requirements .......................................................................... 7 3.5 MS-Global Track Requirements ............................................................................................... 9 3.6 Information Technology Core Requirement ........................................................................... 10 3.7 Advanced Coursework ............................................................................................................ 12 3.7.1 Advanced Policy Topics (12 units required) ...................................................................... -

2002 Opinions
ERIE COUNTY LEGAL JOURNAL (Published by the Committee on Publications of the Erie County Legal Journal and the Erie County Bar Association) Reports of Cases Decided in the Several Courts of Erie County for the Year 2002 LXXXV ERIE, PA JUDGES of the Courts of Erie County during the period covered by this volume of reports COURTS OF COMMON PLEAS HONORABLE WILLIAM R. CUNNINGHAM -------- President Judge HONORABLE GEORGE LEVIN ---------------------------- Senior Judge HONORABLE ROGER M. FISCHER ----------------------- Senior Judge HONORABLE FRED P. ANTHONY --------------------------------- Judge HONORABLE SHAD A. CONNELLY ------------------------------- Judge HONORABLE JOHN A. BOZZA ------------------------------------ Judge HONORABLE STEPHANIE DOMITROVICH --------------------- Judge HONORABLE ERNEST J. DISANTIS, JR. ------------------------- Judge HONORABLE MICHAEL E. DUNLAVEY -------------------------- Judge HONORABLE ELIZABETH K. KELLY ----------------------------- Judge HONORABLE JOHN J. TRUCILLA --------------------------------- Judge Volume 85 TABLE OF CASES -A- Ager, et al. v. Steris Corporation ------------------------------------------------ 54 Alessi, et al. v. Millcreek Township Zoning Hearing Bd. and Sheetz, et al. 77 Altadonna; Commonwealth v. --------------------------------------------------- 90 American Manufacturers Mutual Insurance Co.; Odom v. ----------------- 232 Azzarello; Washam v. ------------------------------------------------------------ 181 -B- Beaton, et. al.; Brown v. ------------------------------------------------------------ -

Chief Data Officer Certificate Program
CHIEF DATA OFFICER CERTIFICATE PROGRAM The success of a modern enterprise is increasingly dependent on its ability to maximize value from data and manage large, diverse, and rapidly changing data. Most executives admit that their organizations mismanage their information assets, leading to missed business opportunities and undue expense. To establish a data-driven culture change in an organization, management needs to engage with stakeholders across the enterprise to secure buy-in and ongoing support in treating data as an asset — not data as a byproduct. To cope with these challenges, many organizations are appointing data governance executives, or Chief Data Officers (CDO), whose responsibilities span the recognition of opportunities afforded by new data sources to ensuring compliance with emerging regulations around security, privacy, and bias. The CMU Heinz College Chief Data Officer Certificate Program provides current or future CDOs a thorough understanding of critical data management related responsibilities and the foundations for developing a robust enterprise data governance program. The 13-module CDataO certificate program will cover key areas – data engineering, data science, decision making, emerging technology, change management, CDO operations, communication/influencing/ leadership skills - to help data executives build important data analytical and decision-making capabilities to better support the strategic mission of their organizations. To meet the needs of these busy professionals, the six-month program will be delivered as a hybrid model, blending the benefits of focused in-person sessions at our CMU campus in Pittsburgh, PA with synchronous distance learning. Participants can expect to develop a tight-knit cohort of their peers. Distance teaching allows participants the flexibility to engage at their own pace to develop their skills to become an effective data executive. -
Conflict Kitchen Reopens After Threats Uber Gets Sigma Phi Pittsburgh Comes to License Brian Trimboli Campus News Editor
Bahcall explains distribution Women’s soccer dominates Walk the Moon performs in of dark matter • A4 in NCAA • A12 Wiegand Gymnasium • B5 SCITECH SPORTS PILLBOX thetartan.org @thetartan November 17, 2014 Volume 109, Issue 12 Carnegie Mellon’s student newspaper since 1906 Alpha Conflict Kitchen reopens after threats Uber gets Sigma Phi Pittsburgh comes to license BRIAN TRIMBOLI campus News Editor CHELSEA DICKSON College students around Staffwriter Pittsburgh were disappoint- ed early last summer when Given the many time an investigation by the commitments and respon- Pennsylvania Public Utility sibilities the average Carn- Commission (PUC) led to egie Mellon student juggles cease-and-desist orders for daily, it could be hard to both Uber Technologies Inc. understand why one would and Lyft Inc. On Thursday, want to find yet another however, the PUC voted 4–1 reason not to sleep. Yet for to grant an experimental li- some undergraduate men cense to Uber, allowing the at Carnegie Mellon, the op- company to operate across portunity to create a new Pennsylvania. Before, Uber community of friends and and Lyft were both operat- leaders was too exciting to ing under temporary au- turn down. thority from the PUC. Alpha Sigma Phi and Phi Uber and Lyft were Delta Theta are the new- founded in San Francisco est arrivals on Carnegie in 2009 and 2012, respec- Mellon’s ever-developing tively. Both companies use fraternity scene. Alpha Sig- an app — available on iOS ma Phi is still in the early and Android — to give “colony” stage of forma- rides to users from drivers tion, while Phi Delta Theta at a cheaper rate than most was officially designated a existing taxicab services. -

Pennsylvania's Largest Employers (At Least 1,000 Employees)
Pennsylvania's Largest Employers (At Least 1,000 Employees) 1st Quarter, 2018 Combined Government Ownerships Center for Workforce Information & Analysis (877) 4WF-DATA • www.workstats.dli.pa.gov • [email protected] September 2018 Rank Employer Rank Employer 1 Federal Government 51 ACME Markets Inc 2 State Government 52 Aerotek Inc 3 Wal-Mart Associates Inc 53 Geisinger Medical Center 4 Trustees of the University of PA 54 Reading Hospital 5 City of Philadelphia 55 Dolgencorp LLC 6 Pennsylvania State University 56 Carnegie Mellon University 7 Giant Food Stores LLC 57 Abington Memorial Hospital 8 School District of Philadelphia 58 FedEx Ground Package System Inc 9 UPMC Presbyterian Shadyside 59 Highmark Inc 10 United Parcel Service Inc 60 Kohl's Department Stores Inc 11 PNC Bank NA 61 Rite Aid of Pennsylvania Inc 12 University of Pittsburgh 62 Marmaxx Operating Corporation 13 Lowe's Home Centers LLC 63 The Hershey Company 14 Weis Markets Inc 64 Wells Fargo NA 15 The Children's Hospital of Philadelphia 65 Temple University Hospital Inc 16 Comcast Cablevision Corp (PA) 66 York Hospital 17 Home Depot USA Inc 67 SmithKline Beecham Corporation 18 PA State System of Higher Education 68 Starbucks Corporation 19 Giant Eagle Inc 69 Boscov's Department Store LLC 20 Amazon.com DEDC LLC 70 School District of Pittsburgh 21 The Vanguard Group Inc 71 UPMC Pinnacle Hospitals 22 Target Corporation 72 Geisinger Clinic 23 Merck Sharp & Dohme Corporation 73 Dick's Sporting Goods Inc 24 Western Penn Allegheny Health 74 Hershey Entertainment & Resorts Co 25 -
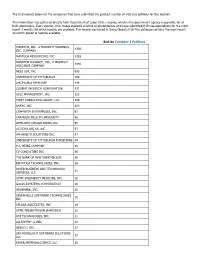
The H1B Records Below List the Companies That Have Submitted the Greatest Number of H1B Visa Petitions for This Location
The H1B records below list the companies that have submitted the greatest number of H1B visa petitions for this location. This information was gathered directly from Department of Labor (DOL) records, which is the government agency responsible for all H1B submissions. Every quarter, DOL makes available a listing of all companies who have submitted H1B visa applications for the most recent 3 months for which records are available. The records contained in Going Global's H1B Plus database contains the most recent 12-month period of records available. Sort by Company | Petitions MASTECH, INC., A MASTECH HOLDINGS, 4339 INC. COMPANY MASTECH RESOURCING, INC. 1393 MASTECH ALLIANCE, INC., A MASTECH 1040 HOLDINGS COMPANY NESS USA, INC. 693 UNIVERSITY OF PITTSBURGH 169 UHCP D/B/A UPMC MEP 144 COGENT INFOTECH CORPORATION 131 SDLC MANAGEMENT, INC. 123 FIRST CONSULTING GROUP, LLC 104 ANSYS, INC. 100 COMPUTER ENTERPRISES, INC. 97 CARNEGIE MELLON UNIVERSITY 96 INTELLECT DESIGN ARENA INC. 95 ACCION LABS US, INC. 63 HM HEALTH SOLUTIONS INC. 57 UNIVERSITY OF PITTSBURGH PHYSICIANS 44 H.J. HEINZ COMPANY 40 CV CONSULTING INC 36 THE BANK OF NEW YORK MELLON 36 INFOYUGA TECHNOLOGIES, INC. 36 BAYER BUSINESS AND TECHNOLOGY 31 SERVICES, LLC UPMC EMERGENCY MEDICINE, INC. 28 GALAX-ESYSTEMS CORPORATION 26 HIGHMARK, INC. 25 SEVEN HILLS SOFTWARE TECHNOLOGIES 25 INC VELAGA ASSOCIATES, INC 24 UPMC PRESBYTERIAN SHADYSIDE 22 DVI TECHNOLOGES, INC. 21 ALLEGHENY CLINIC 20 GENCO I. INC. 17 SRI MOONLIGHT SOFTWARE SOLUTIONS 17 LLC BAYER MATERIALSCIENCE, LLC 16 BAYER HEALTHCARE PHARMACEUTICALS, 16 INC. VISVERO, INC. 16 CYBYTE, INC. 15 BOMBARDIER TRANSPORTATION 15 (HOLDINGS) USA, INC. -

Management Consulting Syllabus 98
MANAGEMENT CONSULTING 94808, 94408 FALL 2020 Heinz College, Carnegie Mellon University Monday, 6:40 - 9:30 PM EST, Section A, 12 Units Dr. Chris W. Brussalis Jordan R. Pallitto Office: 412.722.1111, ext. 111 Office: 412.722.1111, ext. 115 Cell: 412.720.4669 Cell: 724.493.3517 [email protected] [email protected] [email protected] [email protected] Description This is an applications course exploring the profession of management consulting and the art and science of providing management counsel to organizations in the public and private sectors. The course is designed to provide a framework for collaborating with organizations to solve problems and to execute projects efficiently and effectively. Students will explore and utilize practical tools that will enable them to solve problems and execute projects as external or internal consultants or as individual contributors or leaders within organizations. The course introduces frameworks as well as quantitative and qualitative methods that are typically used in management consulting. Course Objectives 1. View problems from the perspective of practicing experts in the field. 2. Utilize quantitative and qualitative methods and interpersonal skills to collaboratively solve problems and execute solutions. 3. Expose students to the classical literature of the profession. 4. Prepare solutions through case studies utilizing technical expertise and experience. 5. Apply course theories and principles to provide consulting services to actual clients. Learning Outcomes 1. Define management consulting and understand why and how consultants are utilized. 2. Apply a consulting process framework to an actual client engagement. 3. Understand the value of stakeholder engagement and how to apply it. -

Downloads of Information Outside the Patterns of Normal Behavior by Those Employees
Insider Theft of Intellectual Property for Business Advantage: A Preliminary Model* 1 Insider Theft of Intellectual Property for Business Advantage: A Preliminary Model* Andrew P. Moore [email protected], Dawn M. Cappelli [email protected], Thomas C. Caron1 [email protected], Eric Shaw2 [email protected], Randall F. Trzeciak [email protected] CERT®3 Program, Software Engineering Institute and CyLab at Carnegie Mellon University 4555 Fifth Avenue Pittsburgh, PA 15213 Abstract. A study conducted by the CERT Program at Carnegie Mellon University’s Software Engineering Institute analyzed hundreds of insider cyber crimes across U.S. critical infrastructure sectors. Follow-up work involved detailed group modeling and analysis of 35 cases of insider theft of intellectual property. In the context of this paper, insider theft of intellectual property for business advantage includes incidents in which the insider’s primary goal is stealing confidential or proprietary information from the organization with the intent to use it to take to a new job, to get a new job, or to start a business. It does not include cases of in which insiders sell an organization’s information. This paper describes general observations about, and a preliminary system dynamics model of, this class of insider crime based on our empirical data. This work generates empirically-based hypotheses for validation and a basis for identifying mititgative measures in future work. 1 Introduction Since 2002, the CERT Program at Carnegie Mellon University’s Software Engineering Institute has been gathering and analyzing actual malicious insider incidents, including IT sabotage, fraud, theft of confidential or proprietary information, espionage, and potential threats to the critical infrastructure of the United * This paper appears in the proceedings of the 1st International Workshop on Managing Insider Security Threats (MIST 2009), Purdue University, West Lafayette, 15-19 June 2009. -

History and Organization Table of Contents
History and Organization Table of Contents History and Organization Carnegie Mellon University History Carnegie Mellon Colleges, Branch Campuses, and Institute Carnegie Mellon University in Qatar Carnegie Mellon Silicon Valley Software Engineering Institute Research Centers and Institutes Accreditations by College and Department Carnegie Mellon University History Introduction The story of Carnegie Mellon University is unique and remarkable. After its founding in 1900 as the Carnegie Technical Schools, serving workers and young men and women of the Pittsburgh area, it became the degree-granting Carnegie Institute of Technology in 1912. “Carnegie Tech,” as it was known, merged with the Mellon Institute to become Carnegie Mellon University in 1967. Carnegie Mellon has since soared to national and international leadership in higher education—and it continues to be known for solving real-world problems, interdisciplinary collaboration, and innovation. The story of the university’s famous founder—Andrew Carnegie—is also remarkable. A self-described “working-boy” with an “intense longing” for books, Andrew Carnegie emigrated from Scotland with his family in 1848 and settled in Pittsburgh, Pennsylvania. He became a self-educated entrepreneur, whose Carnegie Steel Company grew to be the world’s largest producer of steel by the end of the nineteenth century. On November 15, 1900, Andrew Carnegie formally announced: “For many years I have nursed the pleasing thought that I might be the fortunate giver of a Technical Institute to our City, fashioned upon the best models, for I know of no institution which Pittsburgh, as an industrial centre, so much needs.” He concluded with the words “My heart is in the work,” which would become the university’s official motto. -

Download Our 2020 Corporate Profile
HIGHMARK HEALTH 2020 CORPORATE PROFILE 1 Living Health: Together for a Purpose 2020 Corporate Profile HIGHMARK HEALTH 2020 CORPORATE PROFILE 2 Our vision is a world Highmark Health is committed to reinventing the health experience so that everything and everyone works together for the health of those we serve. Boldly challenging unsustainable health care models of the past, we are where everyone building a new model, Living Health, to simplify the customer experience, free up clinicians to focus on care, embraces health. and leverage innovative technology and partnerships to deliver truly individualized health planning. We believe that creating a remarkable health experience will drive better health outcomes and lower total cost of care. Like our work, our financial priorities also serve our social purpose of building stronger communities of Our mission is to healthier people. In 2020, that included more than $750 million invested to support customers, providers, and create a remarkable communities during the pandemic, and another $760 million in capital investments. health experience, A DIVERSE PORTFOLIO OF LEADING HEALTH COMPANIES freeing people to Highmark Health’s diverse portfolio of aliates and subsidiaries meets a broad spectrum of health needs for be their best. consumers, business customers, and government entities. Highmark Inc. and its Blue-branded aliates HM Health Solutions combines technology and (Highmark Health Plans) proudly cover the leading industry knowledge to deliver business insurance needs of millions of individuals, families, solutions to health plan payers so they can run their and seniors, while also oering a variety of health- organizations eciently in a competitive and ever- related products and services. -

2019 Highmark Health Annual Report: Corporate Profile
HIGHMARK HEALTH 2019 CORPORATE PROFILE 1 Embracing Health in Remarkable Ways GLORIA, AHN PATIENT ▶ 2019 Corporate Profile HIGHMARK HEALTH 2019 CORPORATE PROFILE 2 Our vision is a world Highmark Health is committed to reinventing the health experience so that everything and everyone works together seamlessly for the health of those we serve. Boldly challenging unsustainable health care models of where everyone the past, we are simplifying the customer experience, freeing up clinicians to focus on care, and leveraging embraces health. innovative technology and partnerships to deliver truly individualized health planning. We believe that creating a remarkable health experience is also the path to better health outcomes and lower total cost of care. Like our work, our organizational giving — totaling $206.5 million in 2019 — centers on our larger social purpose of Our mission is to building stronger communities of healthier people. create a remarkable A DIVERSE PORTFOLIO OF LEADING HEALTH CARE COMPANIES health experience, Highmark Health’s strong and diverse portfolio of businesses meets a broad spectrum of health needs for freeing people to consumers, business customers, and government entities. be their best. Highmark Inc. and its Blue-branded affiliates (Health HM Home & Community Services specializes Plan) proudly cover the insurance needs of millions of in population health management solutions that individuals, families and seniors, while also offering a benefit payers, providers, and customers. variety of health-related products and services. HM Insurance Group works to protect businesses Allegheny Health Network (AHN) has more and their employees from the financial risks than 250 clinical facilities, including hospitals associated with catastrophic health care costs.