Character Input/Output for Multics J
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Backspace
spumante e rosato* (choose 2) per la tavola glera NV lunetta prosecco, veneto straw, baked apple, peach 11 43 farm greens :: giardiniera, red onion, pecorino romano lambrusco NV medici ermete, emilia romagna black currant, violet, graphite 10 39 lamb & pork meatballs :: stewed tomato, bread crumb, asiago, mint NV l’onesta, emilia romagna fresh strawberry, violet, orange zest 11 43 baked ricotta :: lemon, poached tomato, olive oil * lambrusco whipped lardo bruschetta :: herbs, citrus segment * aglianico 2015 feudi di san gregorio ‘ros‘aura’, irpinia, campania fresh strawberry, rose petal 12 47 shishito peppers :: melon, basil roasted corn :: ricotta, pesto bianco bombino bianco 2016 poderi dal nespoli “pagadebit”, romagna gooseberry, apple, hawthorn blossom 11 43 antipasti (choose 3) pinot grigio 2015 ronchi di pietro, friuli hazelnut, white peach, limestone 48 sweet potato :: cippolini onion, mushroom, rosemary friulano 2014 villa chiopris, friuli grave straw, white flowers, almond 10 39 braised greens :: golden raisins, pecan, red pepper falanghina 2014 terredora, campagna lemon, quince, pear 13 51 :: tomato, basil, balsamic house-made mozzarella chardonnay 2014 tenute del cabreo ‘la pietra’, chianti classico peach preserves, salted popcorn, vanilla 85 roasted beets :: celery, lemon zest, pepperoncini moscato 2015 oddera cascina di fiori, asti tangerine, peach, sage 12 47 the backspace marinated olives :: lemon, rosemary, oregano green beans :: pancetta, garlic, lemon family-style menu rosso $20 per guest pizze (choose 2) pergola rosso -

Programmer Guide: Advanced Data Formatting (ADF)
Advanced Data Formatting (ADF) 72E-69680-07 PROGRAMMER GUIDE ADVANCED DATA FORMATTING PROGRAMMER GUIDE 72E-69680-07 Revision A June 2019 ii Advanced Data Formatting Programmer Guide No part of this publication may be reproduced or used in any form, or by any electrical or mechanical means, without permission in writing from Zebra. This includes electronic or mechanical means, such as photocopying, recording, or information storage and retrieval systems. The material in this manual is subject to change without notice. The software is provided strictly on an “as is” basis. All software, including firmware, furnished to the user is on a licensed basis. Zebra grants to the user a non-transferable and non-exclusive license to use each software or firmware program delivered hereunder (licensed program). Except as noted below, such license may not be assigned, sublicensed, or otherwise transferred by the user without prior written consent of Zebra. No right to copy a licensed program in whole or in part is granted, except as permitted under copyright law. The user shall not modify, merge, or incorporate any form or portion of a licensed program with other program material, create a derivative work from a licensed program, or use a licensed program in a network without written permission from Zebra. The user agrees to maintain Zebra’s copyright notice on the licensed programs delivered hereunder, and to include the same on any authorized copies it makes, in whole or in part. The user agrees not to decompile, disassemble, decode, or reverse engineer any licensed program delivered to the user or any portion thereof. -

KEYBOARD SHORTCUTS (Windows)
KEYBOARD SHORTCUTS (Windows) Note: For Mac users, please substitute the Command key for the Ctrl key. This substitution with work for the majority of commands _______________________________________________________________________ General Commands Navigation Windows key + D Desktop to foreground Context menu Right click Alt + underlined letter Menu drop down, Action selection Alt + Tab Toggle between open applications Alt, F + X or Alt + F4 Exit application Alt, Spacebar + X Maximize window Alt, Spacebar + N Minimize window Ctrl + W Closes window F2 Renames a selected file or folder Open Programs To open programs from START menu: Create a program shortcut and drop it into START menu To open programs/files on Desktop: Select first letter, and then press Enter to open Dialog Boxes Enter Selects highlighted button Tab Selects next button Arrow keys Selects next (>) or previous button (<) Shift + Tab Selects previous button _______________________________________________________________________ Microsoft Word Formatting Ctrl + P Print Ctrl + S Save Ctrl + Z Undo Ctrl + Y Redo CTRL+B Make text bold CTRL+I Italicize CTRL+U Underline Ctrl + C Copy Ctrl + V Paste Ctrl + X Copy + delete Shift + F3 Change case of letters Ctrl+Shift+> Increase font size Ctrl+Shift+< Decrease font size Highlight Text Shift + Arrow Keys Selects one letter at a time Shift + Ctrl + Arrow keys Selects one word at a time Shift + End or Home Selects lines of text Change or resize the font CTRL+SHIFT+ > Increase the font size 1 KEYBOARD SHORTCUTS (Windows) CTRL+SHIFT+ < -

How to Enter Foreign Language Characters on Computers
How to Enter Foreign Language Characters on Computers Introduction Current word processors and operating systems provide a large number of methods for writing special characters such as accented letters used in foreign languages. Unfortunately, it is not always obvious just how to enter such characters. Moreover, even when one knows a method of typing an accented letter, there may be a much simpler method for doing the same thing. This note may help you find the most convenient method for typing such characters. The choice of method will largely depend on how frequently you have to type in foreign languages. 1 The “ALT Key” Method This is the most common method of entering special characters. It always works, regardless of what pro- gram you are using. On both PCs and Macs, you can write foreign characters in any application by combining the ALT key (the key next to the space bar) with some alphabetic characters (on the Mac) or numbers (on PCs), pro- vided you type numbers on the numeric keypad, rather than using the numbers at the top of the keyboard. To do that, of course, also requires your NumLock Key to be turned on, which it normally will be. For example, On the Mac, ALT + n generates “ñ”. On the PC, ALT + (number pad) 164 or ALT + (number pad) 0241 generate “ñ”. A list of three- and four-digit PC codes for some common foreign languages appears at the end of this note. 2 The “Insert Symbol” Method Most menus in word processors and other applications offer access to a window displaying all the printable characters in a particular character set. -

Chapter 1 -Using the Command-Line Interface
CHAPTER 1 Using the Command-Line Interface The command-line interface (CLI) is a line-oriented user interface that provides commands for configuring, managing, and monitoring the Cisco wireless LAN controller. This chapter contains the following topics: • CLI Command Keyboard Shortcuts, page 1-2 • Using the Interactive Help Feature, page 1-3 Cisco Wireless LAN Controller Command Reference OL-19843-02 1-1 Chapter 1 Using the Command-Line Interface CLI Command Keyboard Shortcuts CLI Command Keyboard Shortcuts Table 1-1 lists CLI keyboard shortcuts to help you enter and edit command lines on the controller. Table 1-1 CLI Command Keyboard Shortcuts Action Description Keyboard Shortcut Change The word at the cursor to lowercase. Esc I The word at the cursor to uppercase. Esc u Delete A character to the left of the cursor. Ctrl-h, Delete, or Backspace All characters from the cursor to the beginning of Ctrl-u the line. All characters from the cursor to the end of the line. Ctrl-k All characters from the cursor to the end of the Esc d word. The word to the left of the cursor. Ctrw-w or Esc Backspace Display MORE Exit from MORE output. q, Q, or Ctrl-C output Next additional screen. The default is one screen. Spacebar To display more than one screen, enter a number before pressing the Spacebar key. Next line. The default is one line. To display more Enter than one line, enter the number before pressing the Enter key. Enter an Enter or Return key character. Ctrl-m Expand the command or abbreviation. -

International Language Environments Guide
International Language Environments Guide Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 806–6642–10 May, 2002 Copyright 2002 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, Java, XView, ToolTalk, Solstice AdminTools, SunVideo and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. SunOS, Solaris, X11, SPARC, UNIX, PostScript, OpenWindows, AnswerBook, SunExpress, SPARCprinter, JumpStart, Xlib The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. -

The ASCII Character Set
The ASCII Character Set The American Standard Code for Information Interchange or ASCII assigns values between 0 and 255 for upper and lower case letters, numeric digits, punctuation marks and other symbols. ASCII characters can be split into the following sections: ❑ 0 – 31 Control codes ❑ 32 – 127 Standard, implementation-independent characters ❑ 128 – 255 Special symbols, international character sets – generally, non-standard characters. Control Codes : ASCII Characters 0 - 31 The following table lists and describes the first 32 ASCII characters, often referred to as control codes. The columns show the decimal and hexadecimal ASCII values for each code along with their abbreviated and full names. Descriptions are given to those most in use today. Decimal Octal Hexadecimal Code Description 000 000 00 NUL Null 001 001 01 SOH Start Of Heading 002 002 02 STX Start of TeXt 003 003 03 ETX End of TeXt 004 004 04 EOT End Of Transmission 005 005 05 ENQ ENQuiry 006 006 06 ACK ACKnowledge Table continued on following page Appendix F Decimal Octal Hexadecimal Code Description 007 007 07 BEL BELl. Caused teletype machines to ring a bell. Causes a beep in many common terminals and terminal emulation programs. 008 010 08 BS BackSpace. Moves the cursor move backwards (left) one space. 009 011 09 HT Horizontal Tab. Moves the cursor right to the next tab stop. The spacing of tab stops is dependent on the output device, but is often either 8 or 10 characters wide. 010 012 0A LF Line Feed. Moves the cursor to a new line. On Unix systems, moves to a new line AND all the way to the left. -

Lessons 18-20: Z, :, CAPS LOCK, ?, Backspace, TAB Z: the “Z” Is Keyed with Your Left Pinkie Finger, Moving from the “A” Key Down to the “Z” Key
Lessons 18-20: z, :, CAPS LOCK, ?, Backspace, TAB z: The “z” is keyed with your left pinkie finger, moving from the “a” key down to the “z” key. : (colon) The “:” is keyed with your right pinkie finger. You need to shift (left shift) the semicolon to key the colon. Space twice after a colon used as punctuation. CAPS LOCK: Press the CAPS LOCK with your left pinkie finger, moving from the “a” key to the CAPS LOCK without lifting your hand off home row. The CAPS LOCK is a “toggle” key (on/off). CAPS LOCK is used to key a word or series of words in all caps. It is not intended to be used to capitalize an individual letter. ? (question mark): The question mark is keyed with the right pinkie finger, moving from the semicolon down to the “?” key. You need to shift (left shift) to key the question mark. Backspace Key: Reach up to the backspace key with your right pinkie finger (keep your index finger anchored to home row). The backspace key deletes the letter to the left of the cursor. TAB Key: Use your left pinkie finger to press the TAB key (keep your index finger anchored to home row). When you press the tab key, the cursor will move .5” to the right. The tab is used most often to indent paragraphs. aa az az aza aza zip zip zap zap zoo zoo zest zest zone zone maze maze size size aa az az aza aza zip zip zap zap zoo zoo zest zest zone zone maze maze size size raze raze daze daze hazy hazy zipper zipper dozen dozen buzz buzz hazel hazel raze raze daze daze hazy hazy zipper zipper dozen dozen buzz buzz hazel hazel zoology zoology quizzes quizzes zigzag zigzag hazardous hazardous dizzy dizzy zoology zoology quizzes quizzes zigzag zigzag hazardous hazardous dizzy dizzy buzzard buzzard dazzle dazzle equalize equalize kazoo kazoo zero zero zinc zinc buzzard buzzard dazzle dazzle equalize equalize kazoo kazoo zero zero zinc zinc (See next page for additional practice.) The Utah Jazz dazzled their fans on their home court in Salt Lake City, Utah. -
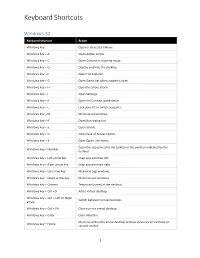
Keyboard Shortcuts
Keyboard Shortcuts Windows 10 Keyboard shortcut Action Windows key Open or close Start Menu. Windows key + A Open Action center. Windows key + C Open Cortana in listening mode. Windows key + D Display and hide the desktop. Windows key + E Open File Explorer. Windows key + G Open Game bar when a game is open. Windows key + H Open the Share charm. Windows key + I Open Settings. Windows key + K Open the Connect quick action. Windows key + L Lock your PC or switch accounts. Windows key + M Minimize all windows. Windows key + R Open Run dialog box. Windows key + S Open Search. Windows key + U Open Ease of Access Center. Windows key + X Open Quick Link menu. Open the app pinned to the taskbar in the position indicated by the Windows key + Number number. Windows key + Left arrow key Snap app windows left. Windows key + Right arrow key Snap app windows right. Windows key + Up arrow key Maximize app windows. Windows key + Down arrow key Minimize app windows. Windows key + Comma Temporarily peek at the desktop. Windows key + Ctrl +D Add a virtual desktop. Windows key + Ctrl + Left or Right Switch between virtual desktops. arrow Windows key + Ctrl + F4 Close current virtual desktop. Windows key + Enter Open Narrator. Minimize all but the active desktop window (restores all windows on Windows key + Home second stroke). 1 Keyboard Shortcuts Keyboard shortcut Action Windows key + PrtScn Capture a screenshot and save in Screenshots folder. Windows key + Shift + Up arrow Stretch the desktop window to the top and bottom of the screen. Windows key + Tab Open Task view. -

The Affirmative Driverless PC/5250 Keyboard Has Been Optimized For
The Affirmative 122-Key Driverless PC/5250 keyboard has been optimized for IBM Client Access 5250 and should be compatible with other 5250 emulation software packages which include a keyboard mapping utility. The PC/5250 keyboard uses the Microsoft standard 101/102-key keyboard driver and does not require any additional keyboard drivers. Figure 1 shows the layout of this keyboard with the keycap nomenclature. F13 F14 F15 F16 F17 F18 F19 F20 F21 F22 F23 F24 F1 F2 F3 F4 F5 F6 F7 F8 F9 F10 F11 F12 Figure 1. 122-Key Driverless PC/5250 Keyboard Layout PC functions are in black. 5250 unique functions are in blue SysRq | ! @ # $ % ^ ¬ & * ( ) _ + Dup NumLk Esc ~ PgUp End Insert ScrLk / * Attn ¢ ` 1 2 3 4 5 6 7 8 9 0 - = RollDn Zoom Jump Cl Print Pause { } 7 89 - TAB QWE R TYUI OP Delete PgDn Scrn Clear [ ] Enter RollUp Home PgUp Field - SysRq Break Rule : " ¦ 456 Print Help Caps Lock A S D FGHJK L Field+ ; ' \ + Field Exit ? , . ? 2 Recrd Play ShiftZ X C V B N M Shift 1 3 , . / Home End . PgDn Enter Win Win Ctrl Alt Alt Ctrl 0 . Field Start Apps Reset Enter Ins Del Exit Quit To use the Driverless PC/5250 keyboard, the user must ensure that the 5250 functions are mapped properly by the emulation software program being used. Most of the key mappings are standard (between emulation packages) and will require no changes to the system’s configuration and set-up. However, some changes will probably be required using the emulation software’s keyboard mapping utility to enable a few specific functions. -

Title Keyboard : All Special Keys : Enter, Del, Shift, Backspace ,Tab … Contributors Dhanya.P Std II Reviewers Submission Approval Date Date Ref No
Title Keyboard : All special keys : Enter, Del, Shift, Backspace ,Tab ¼ Contributors Dhanya.P Std II Reviewers Submission Approval Date Date Ref No: This topic describes the special keys on the keyboard of a computer Brief Description and their functionalities . Goal To familiarize the special keys on the keyboard of a computer. Pre-requisites Familiarity with computer. Learning Concepts that special keys on a keyboard has special functionalities. Outcome One Period Duration http://www.ckls.org/~crippel/computerlab/tutorials/keyboard/ References http://computer.howstuffworks.com/ Page Nos: 2,3,4,5,6 Detailed Description Page No: 7 Lesson Plan Page No: 7 Worksheet Page No: 8 Evaluation Page No: 8 Other Notes Detailed Description A computer keyboard is a peripheral , partially modeled after the typewriter keyboard. Keyboards are designed for the input of text and characters. Special Keys Function Keys Cursor Control Keys Esc Key Control Key Shift Key Enter Key Tab Key Insert Key Delete Key ScrollLock Key NumLock Key CapsLock Key Pasue/Break Key PrtScr Key Function Keys F1 through F12 are the function keys. They have special purposes. The following are mainly the purpose of the function keys. But it may vary according to the software currently running. # F1 - Help # F2 - Renames selected file # F3 - Opens the file search box # F4 - Opens the address bar in Windows Explorer # F5 - Refreshes the screen in Windows Explorer # F6 - Navigates between different sections of a Windows Explorer window # F8 - Opens the start-up menu when booting Windows # F11 - Opens full screen mode in Explorer Function Keys F1 through F12 are the function keys. -

Print › Keyboarding Finger Placement Quiz | Quizlet
Keyboarding Finger Placement Quiz Study online at quizlet.com/_1gegh0 1. ASDF: Home row keys for the left hand are: 44. Right Ring: O, L, period 2. F and R: The left index finger strikes which keys? 45. Right Ring: Which hand and finger strikes the "L" key? 3. Flat on the floor: Where should your feet be placed? 46. Right Ring: Which hand and finger strikes the "O" key? 4. JKL;: Home keys for the right hand are: 47. Right Ring: Which hand and finger strikes the period (.) key? 5. Keys on the right side of the keyboard: The Left Shift Key is 48. Thumbs: Which hand and finger strikes the space bar? used to capitalize which keys? 6. Left Middle: Which hand and finger strikes the "E" key? 7. Left Middle: Which hand and finger strikes the "C" key? 8. Left Middle: Which hand and finger strikes the "D" key? 9. Left Middle: D, E, C 10. Left Pinky: A, Q, Z, Tab, and Shift 11. Left Pinky: Which hand and finger strikes the "Q" key? 12. Left Pinky: Which hand and finger strikes the TAB key? 13. Left Pinky: Which hand and finger strikes the "A" key? 14. Left Pinky: Which hand and finger strikes the "Z" key? 15. Left Pointer: What hand and finger strikes the "T" key? 16. Left Pointer: Which hand and finger strikes the "B" key? 17. Left Pointer: R, T, F, G, V, B 18. Left Pointer: Which hand and finger strike the "F" key? 19. Left Pointer: Which hand and finger strikes the "G" key? 20.