Microsoft Security Update for January 2020 Fixes 49 Security Vulnerabilities
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

3700Document22374461
Copyright (c) 2018, Oracle. All rights reserved. RES QA / Test – Microsoft Patch Security Report (Doc ID 2237446.1) To Bottom Modified: 16-Apr-2018 Type: REFERENCE In this Document Purpose Scope Details Windows Security Updates Miscellaneous Information Internet Explorer 7 Known Issues Internet Explorer 8 Known Issues Internet Explorer 9 Known Issues Internet Explorer 10 Known Issues Internet Explorer 11 Known Issues Adobe Known Issues Non-Security, High Priority Updates Microsoft Security Essentials References APPLIES TO: Oracle Hospitality RES 3700 - Version 4.9.0 and later Information in this document applies to any platform. PURPOSE The Security Report contains a listing of select Microsoft patches that are directly related to the RES and E7 applications and have been tested against the RES and E7 applications to validate there are no issues or identify any updates that should NOT be installed. The list is not inclusive of ALL Microsoft patches. This report is updated monthly for patches released monthly and YTD cumulative. SCOPE This document is intended for support employees and users of the RES E7 products. DETAILS WARNING: On Workstation 2015 – POSReady 2009, the Microsoft “Optional Hardware” Update, “MosChip Semiconductor Technology Ltd – Bus Controllers and Ports – PCI Multi-IO Controller” is incompatible with the RES IDN Driver, and will cause IDN Printing to fail. Even if this update is uninstalled, IDN printing could be effected adversely. DO NOT INSTALL THIS Optional MICROSOFT UPDATE. If this was already done, reload the Ghost image for the 2015 posted on MOS, and reload all other applicable Microsoft Updates. As of August of 2016 the RES Microsoft security bulletin has been split off from the combined RES/e7 bulletin. -

Configuration Sheets
PRIMERGY RX600 S4 Configuration Sheets About this manual A Configuration Sheets of Hardware Use this form to record the hardware configuration and various settings of your server. B Configuration Sheets of BIOS Setup Utility Parameters Use this form to record the settings of the BIOS Setup Utility. C Configuration Sheets of Remote Management Controller's Web Interface Use this form to record the settings of the Remote Management Controller Web interface. D Design Sheet of the RAID Configuration Use this form to record the definitions of the disk groups (or the physical packs) and the logical drives in the RAID configuration (array configuration). E Design Sheet Use this form to record the software settings. F Accident Sheet Use this form to record any failures that occur in your server. 1 Product Names The following expressions and abbreviations are used to describe the product names used in this manual. Product names Expressions and abbreviations PRIMERGY RX600 S4 This server or the server Windows Server 2003 R2, Windows Microsoft® Windows Server® 2003 R2, Standard Edition Standard Edition 2003 Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Enterprise Edition Enterprise Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise Edition Enterprise Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard Edition Standard Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Standard x64 Edition Standard x64 Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2 , Enterprise x64 Edition Enterprise x64 Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard x64 Edition Standard x64 Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise x64 Edition Enterprise x64 Edition Microsoft® Windows Server® 2003 Service Pack SP ■Trademarks Microsoft, Windows, MS, Windows Server are registered trademarks of the Microsoft Corporation in the USA and other countries. -

Linux Networking 101
The Gorilla ® Guide to… Linux Networking 101 Inside this Guide: • Discover how Linux continues its march toward world domination • Learn basic Linux administration tips • See how easy it can be to build your entire network on a Linux foundation • Find out how Cumulus Linux is your ticket to networking freedom David M. Davis ActualTech Media Helping You Navigate The Technology Jungle! In Partnership With www.actualtechmedia.com The Gorilla Guide To… Linux Networking 101 Author David M. Davis, ActualTech Media Editors Hilary Kirchner, Dream Write Creative, LLC Christina Guthrie, Guthrie Writing & Editorial, LLC Madison Emery, Cumulus Networks Layout and Design Scott D. Lowe, ActualTech Media Copyright © 2017 by ActualTech Media. All rights reserved. No portion of this book may be reproduced or used in any manner without the express written permission of the publisher except for the use of brief quotations. The information provided within this eBook is for general informational purposes only. While we try to keep the information up- to-date and correct, there are no representations or warranties, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the information, products, services, or related graphics contained in this book for any purpose. Any use of this information is at your own risk. ActualTech Media Okatie Village Ste 103-157 Bluffton, SC 29909 www.actualtechmedia.com Entering the Jungle Introduction: Six Reasons You Need to Learn Linux ....................................................... 7 1. Linux is the future ........................................................................ 9 2. Linux is on everything .................................................................. 9 3. Linux is adaptable ....................................................................... 10 4. Linux has a strong community and ecosystem ........................... 10 5. -
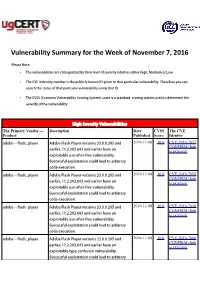
Vulnerability Summary for the Week of November 7, 2016
Vulnerability Summary for the Week of November 7, 2016 Please Note: • The vulnerabilities are cattegorized by their level of severity which is either High, Medium or Low. • The !" indentity number is the #ublicly $nown %& given to that #articular vulnerability. Therefore you can search the status of that #articular vulnerability using that %&. • The !'S (Common !ulnerability 'coring System) score is a standard scoring system used to determine the severity of the vulnerability. High Severity Vulnerabilities The Primary Vendor --- Description Date CVSS The CVE Product Published Score Identity adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7857 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7858 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7859 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7860 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable type confusion vulnerability. -

Windows Internals, Sixth Edition, Part 2
spine = 1.2” Part 2 About the Authors Mark Russinovich is a Technical Fellow in ® the Windows Azure™ group at Microsoft. Windows Internals He is coauthor of Windows Sysinternals SIXTH EDITION Administrator’s Reference, co-creator of the Sysinternals tools available from Microsoft Windows ® The definitive guide—fully updated for Windows 7 TechNet, and coauthor of the Windows Internals and Windows Server 2008 R2 book series. Delve inside Windows architecture and internals—and see how core David A. Solomon is coauthor of the Windows Internals book series and has taught components work behind the scenes. Led by a team of internationally his Windows internals class to thousands of renowned internals experts, this classic guide has been fully updated Windows developers and IT professionals worldwide, SIXTH for Windows 7 and Windows Server® 2008 R2—and now presents its including Microsoft staff. He is a regular speaker 6EDITION coverage in two volumes. at Microsoft conferences, including TechNet As always, you get critical, insider perspectives on how Windows and PDC. operates. And through hands-on experiments, you’ll experience its Alex Ionescu is a chief software architect and internal behavior firsthand—knowledge you can apply to improve consultant expert in low-level system software, application design, debugging, system performance, and support. kernel development, security training, and Internals reverse engineering. He teaches Windows internals courses with David Solomon, and is ® In Part 2, you will: active in the security research community. -

Exploration of Windows Vista Advanced Forensic Topics – Day 1
Windows Vista and NTFS File System Internals Exploration of Windows Vista Advanced Forensic Topics – Day 1 LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Windows Client Forensics (Windows Vista Advanced Topics) Transactional NTFS and Registry Explained LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved New Features Important Changes of Interest LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Self-Healing File System • Vista includes a “self-healing” function which can correct certain errors in the system • Vista maintains a list of hashes of known files and checks the hashes periodically • On non-system files Vista will validate the file metadata • Files whose hashes do not match or metadata is not valid will be replaced the next time the system is rebooted LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Self-Healing File System • Equivalent to Chkdsk and defrag processes constantly running in the background • This has the potential to decrease the usefulness of the free space and slack space on the disk as well as limit the ability to recover deleted files LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Self-Healing File System • Healed files can be identified by an examination of the event -

Microsoft Patches Were Evaluated up to and Including CVE-2019-1303
Honeywell Security Group 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2019-1303. Patches not listed below are not applicable to a Pro-Watch system. 2019 – Microsoft® Patches Tested with Pro-Watch .NET Quality Rollup for .NET Framework CVE-2019-1371 Internet Explorer Memory Corruption Vulnerability CVE-2019-1368 Windows Secure Boot Security Feature Bypass Vulnerability CVE-2019-1367 Scripting Engine Memory Corruption Vulnerability CVE-2019-1366 Chakra Scripting Engine Memory Corruption Vulnerability CVE-2019-1365 Microsoft IIS Server Elevation of Privilege Vulnerability CVE-2019-1359 Jet Database Engine Remote Code Execution Vulnerability CVE-2019-1358 Jet Database Engine Remote Code Execution Vulnerability CVE-2019-1357 Browser Spoofing Vulnerability Microsoft Edge based on Edge HTML Information Disclosure CVE-2019-1356 Vulnerability CVE-2019-1347 Windows Denial of Service Vulnerability CVE-2019-1346 Windows Denial of Service Vulnerability CVE-2019-1345 Windows Kernel Information Disclosure Vulnerability CVE-2019-1344 Windows Code Integrity Module Information Disclosure Vulnerability CVE-2019-1343 Windows -
![[MS-WMLOG]: Windows Media Log Data Structure](https://docslib.b-cdn.net/cover/5100/ms-wmlog-windows-media-log-data-structure-3185100.webp)
[MS-WMLOG]: Windows Media Log Data Structure
[MS-WMLOG]: Windows Media Log Data Structure Intellectual Property Rights Notice for Open Specifications Documentation . Technical Documentation. Microsoft publishes Open Specifications documentation (“this documentation”) for protocols, file formats, data portability, computer languages, and standards support. Additionally, overview documents cover inter-protocol relationships and interactions. Copyrights. This documentation is covered by Microsoft copyrights. Regardless of any other terms that are contained in the terms of use for the Microsoft website that hosts this documentation, you can make copies of it in order to develop implementations of the technologies that are described in this documentation and can distribute portions of it in your implementations that use these technologies or in your documentation as necessary to properly document the implementation. You can also distribute in your implementation, with or without modification, any schemas, IDLs, or code samples that are included in the documentation. This permission also applies to any documents that are referenced in the Open Specifications documentation. No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation. Patents. Microsoft has patents that might cover your implementations of the technologies described in the Open Specifications documentation. Neither this notice nor Microsoft's delivery of this documentation grants any licenses under those patents or any other Microsoft patents. However, a given Open Specifications document might be covered by the Microsoft Open Specifications Promise or the Microsoft Community Promise. If you would prefer a written license, or if the technologies described in this documentation are not covered by the Open Specifications Promise or Community Promise, as applicable, patent licenses are available by contacting [email protected]. -

3700Document22374461
Copyright (c) 2018, Oracle. All rights reserved. RES QA / Test – Microsoft Patch Security Report (Doc ID 2237446.1) To Bottom Modified: 26-Feb-2018 Type: REFERENCE In this Document Purpose Scope Details Windows Security Updates Miscellaneous Information Internet Explorer 7 Known Issues Internet Explorer 8 Known Issues Internet Explorer 9 Known Issues Internet Explorer 10 Known Issues Internet Explorer 11 Known Issues Adobe Known Issues Non-Security, High Priority Updates Microsoft Security Essentials References APPLIES TO: Oracle Hospitality RES 3700 - Version 4.9.0 and later Information in this document applies to any platform. PURPOSE The Security Report contains a listing of select Microsoft patches that are directly related to the RES and E7 applications and have been tested against the RES and E7 applications to validate there are no issues or identify any updates that should NOT be installed. The list is not inclusive of ALL Microsoft patches. This report is updated monthly for patches released monthly and YTD cumulative. SCOPE This document is intended for support employees and users of the RES E7 products. DETAILS WARNING: On Workstation 2015 – POSReady 2009, the Microsoft “Optional Hardware” Update, “MosChip Semiconductor Technology Ltd – Bus Controllers and Ports – PCI Multi-IO Controller” is incompatible with the RES IDN Driver, and will cause IDN Printing to fail. Even if this update is uninstalled, IDN printing could be effected adversely. DO NOT INSTALL THIS Optional MICROSOFT UPDATE. If this was already done, reload the Ghost image for the 2015 posted on MOS, and reload all other applicable Microsoft Updates. As of August of 2016 the RES Microsoft security bulletin has been split off from the combined RES/e7 bulletin. -

Advisory Microsoft February 2020 Patch Tuesday
Advisory Microsoft February 2020 Patch Tuesday aeCERT One of Telecommunications Regulatory Authority (TRA) Initiatives P O Box 116688, Dubai, United Arab Emirates (UAE) www.aecert.ae | www.tra.gov.ae Version: 1.0 Ref: ADV-19-011 Document Date: 16/02/2020 Document Details Disclaimer Whilst every effort has been made to ensure the accuracy of the information contained within this report, aeCERT and the TRA bear no liability or responsibility for any recommendations issued or inadvertent damages that could be caused by the recipient of this information. Accessing third-party links in this advisory will direct you to an external website. Please note that aeCERT bears no responsibility for third-party website traffic. aeCERT will have no liability to the entities for the content or use of the content available through the hyperlinks that are referenced. Contents Contents 1 Summary 2 Details 2 Recommendations 9 References 9 1 | P a g e Summary aeCERT has received the latest Microsoft security updates that aim to patch recent vulnerabilities discovered in their system. The release has impact on some Microsoft products. In order to protect windows from security risks, users should install latest update as soon as possible. Details In addition to the Internet Explorer zero-day vulnerability discovered in the middle of January, Microsoft discovered other three vulnerabilities that were disclosed to the public but not exploited yet: • CVE-2020-0683 - Windows installer elevation of privilege vulnerability. • CVE-2020-0686 - Windows installer elevation of privilege vulnerability. • CVE-2020-0706 - Microsoft browser information disclosure vulnerability. Further details about the security update can be found on Microsoft’s website here. -

Windows Server 2003 SP1 Performance ~10 Gflops ~10 Gflops ~10 Gflops
Longhorn Server Overview 张大磊 开发技术经理 微软(中国)有限公司 http://www.cnblogs.com/msdpe http://msdpe.spaces.live.com Server Perspective in Past 15 Years 1991 1998 2005 System Cray Y-MP C916 Sun HPC10000 Small Form Factor PCs Architecture 16 x Vector 24 x 333MHz Ultra- 4 x 2.2GHz Athlon64 4GB, Bus SPARCII, 24GB, SBus 4GB, GigE OS UNICOS Solaris 2.5.1 Windows Server 2003 SP1 Performance ~10 GFlops ~10 GFlops ~10 GFlops Price $40,000,000 $1,000,000 (40x drop) < $4,000 (250x drop) Customers Government Labs Large Enterprises Every Engineer & Scientist Applications Classified, Climate, Manufacturing, Energy, Bioinformatics, Materials Physics Research Finance, Telecom Sciences, Digital Media Everyman Mystery Hear of Wow, it’s ours! Quiz: What’s your demands? “Make high-end computing easier and more productive to use. Emphasis should be 应用 placed on time to solution, the major metric of value to high- 强大 end computing users… A common software environment for scientific computation encompassing desktop to high- end systems will enhance productivity gains by promoting 管理 服务 ease of use and manageability 便捷 稳定 of systems.” High-End Computing Revitalization Task Force, (Office of Science and Technology Policy, Executive Office of the President) App Platform Management .NET Framework 3.0 WS-Management IIS 7 Monitoring The Fundamentals Server Roles Transactions Recovery Core Storage Networking Integrated Hypervisor 应用服务器 .NET Framework 3.0 新的托管代码编程模型 包括WCF、WPF、WF、Card Space. IIS 7.0 模块化设计 为寄宿内容提供扩展性架构 新的管理程序和API Windows激活服务(WAS) 可管理应用程序池的配置和工作进程(之前用WWW服务管理) • 可为HTTP站点和非HTTP站点使用同样的配置和处理模型 -

Windows Server 2003 R2 Overview and Reviewer Guide
Windows Server 2003 R2 Reviewer's Guide Microsoft Windows Server 2003 R2 Overview Guide Microsoft Corporation Published: December 2005 Abstract Microsoft® Windows Server™ 2003 R2 makes it easier and more cost-effective to extend connectivity and control to identities, locations, data and applications throughout and beyond an organization. Windows Server 2003 R2 is an update release of the award-winning Windows Server 2003 operating system. Built on Windows Server 2003 with Service Pack 1 (SP1), Windows Server 2003 R2 takes advantage of the stability and security enhancements of a proven code base while extending connectivity and control into new areas. Windows Server 2003 R2 offers all of the benefits of Windows Server 2003 with SP1 while greatly improving identity and access management, branch server management, storage configuration and management, and application development inside and outside your organization’s boundaries. Windows Server 2003 R2 is easy to integrate into an existing Windows Server 2003 environment since it shares the same application compatibility, manageability, and serviceability as existing servers with Windows Server 2003 with SP1. Windows Server 2003 R2 Reviewer's Guide The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT.