Advisory Microsoft Patch Tuesday – May 2020
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Microsoft Security Update for January 2020 Fixes 49 Security Vulnerabilities
Microsoft Security Update for January 2020 Fixes 49 Security Vulnerabilities Overview Microsoft released the January security update on Tuesday, fixing 49 security issues ranging from simple spoofing attacks to remote code execution, discovered in products like .NET Framework, Apps, ASP.NET, Common Log File System Driver, Microsoft Dynamics, Microsoft Graphics Component, Microsoft Office, Microsoft Scripting Engine, Microsoft Windows, Microsoft Windows Search Component, Windows Hyper-V, Windows Media, Windows RDP, Windows Subsystem for Linux, and Windows Update Stack. Of the vulnerabilities fixed by Microsoft's this monthly update, a total of eight critical vulnerabilities exist in the .NET Framework, ASP.NET, Microsoft Scripting Engine, and Windows RDP. In addition, there are 41 important vulnerabilities. Critical Vulnerabilities The following are eight critical vulnerabilities covered in this update. @NSFOUS 2020 http://www.nsfocus.com Windows RDP CVE-2020-0609、CVE-2020-0610 These two remote code execution vulnerabilities in the Windows Remote Desktop Gateway (RD Gateway) could be exploited by unauthenticated attackers. If the two vulnerabilities are exploited successfully, arbitrary code may be executed on the target system, allowing the attacker to install the program, view, change or delete data, or create a new account with full user rights. To exploit this vulnerability, an attacker needs to send a specially crafted request to the RD gateway of the target system via RDP. This update addresses these issues by correcting the way the RD gateway handles connection requests. For more details about the vulnerabilities and download updates, please refer to Microsoft's official security advisories: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0609 https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0610 CVE-2020-0611 This is a remote code execution vulnerability in Windows Remote Desktop clients. -

Internet Explorer 9 Features
m National Institute of Information Technologies NIIT White Paper On “What is New in Internet Explorer 9” Submitted by: Md. Yusuf Hasan Student ID: S093022200027 Year: 1st Quarter: 2nd Program: M.M.S Date - 08 June 2010 Dhaka - Bangladesh Internet Explorer History Abstract: In the early 90s—the dawn of history as far as the World Wide Web is concerned—relatively few users were communicating across this Internet Explorer 9 (abbreviated as IE9) is the upcoming global network. They used an assortment of shareware and other version of the Internet Explorer web browser from software for Microsoft Windows operating system. In 1995, Microsoft Microsoft. It is currently in development, but developer hosted an Internet Strategy Day and announced its commitment to adding Internet capabilities to all its products. In fulfillment of that previews have been released. announcement, Microsoft Internet Explorer arrived as both a graphical Web browser and the name for a set of technologies. IE9 will have complete or nearly complete support for all 1995: Internet Explorer 1.0: In July 1995, Microsoft released the CSS 3 selectors, border-radius CSS 3 property, faster Windows 95 operating system, which included built-in support for JavaScript and embedded ICC v2 or v4 color profiles dial-up networking and TCP/IP (Transmission Control support via Windows Color System. IE9 will feature Protocol/Internet Protocol), key technologies for connecting to the hardware accelerated graphics rendering using Direct2D, Internet. In response to the growing public interest in the Internet, Microsoft created an add-on to the operating system called Internet hardware accelerated text rendering using Direct Write, Explorer 1.0. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

Introduction to Windows Runtime (Winrt)
Introduction to Windows Runtime (WinRT) Raffaele Rialdi @raffaeler [email protected] http://www.iamraf.net Tailored User Experience full screen different resolutions Immersive Multiple live tiles form factors Engaging secure, and Alive trustable Inspiring Confidence Metro Connected Multitasking use live data Touch-first fast and fluid small devices Current problems • No marketplace: how can you trust an application? • Admin privilege is required to install most Apps • Interoperability is difficult (PInvoke / COM) –Memory and Performance costs are high –Accessing OS API can be tough • Mixing native and managed language is hard • "C" APIs lifecycle is error-prone (CreateFile … CloseHandle) • I/Os are blocking (network, storage, …) • No standards for App to App communication • Search, Tweets, Facebook posts, … Windows Runtime Architecture Metro apps Desktop apps Win MFC XAML DirectX HTML WPF SL HTML form DX Language Projections .NET / Js / C++ .NET / Js / C++ Filtered access BCL / libraries to WinRT Windows Runtime APIs and Services UI Controls Storage Media Win32 Win32 Windows Metadata XAML Pickers Network … Runtime Broker Windows Runtime Core Windows Kernel Services What is the Windows Runtime? • It's the evolution of the Component Object Model (COM) • The infrastructure reuse old concepts like apartments, IUnknown and addref/release • IDispatch is gone, IInspectable is the new base interface • New support for Events (no connection points) and static types • Totally different Type System (no Variants, no BSTRs, …) • WinRT use ECMA-335 -

3700Document22374461
Copyright (c) 2018, Oracle. All rights reserved. RES QA / Test – Microsoft Patch Security Report (Doc ID 2237446.1) To Bottom Modified: 16-Apr-2018 Type: REFERENCE In this Document Purpose Scope Details Windows Security Updates Miscellaneous Information Internet Explorer 7 Known Issues Internet Explorer 8 Known Issues Internet Explorer 9 Known Issues Internet Explorer 10 Known Issues Internet Explorer 11 Known Issues Adobe Known Issues Non-Security, High Priority Updates Microsoft Security Essentials References APPLIES TO: Oracle Hospitality RES 3700 - Version 4.9.0 and later Information in this document applies to any platform. PURPOSE The Security Report contains a listing of select Microsoft patches that are directly related to the RES and E7 applications and have been tested against the RES and E7 applications to validate there are no issues or identify any updates that should NOT be installed. The list is not inclusive of ALL Microsoft patches. This report is updated monthly for patches released monthly and YTD cumulative. SCOPE This document is intended for support employees and users of the RES E7 products. DETAILS WARNING: On Workstation 2015 – POSReady 2009, the Microsoft “Optional Hardware” Update, “MosChip Semiconductor Technology Ltd – Bus Controllers and Ports – PCI Multi-IO Controller” is incompatible with the RES IDN Driver, and will cause IDN Printing to fail. Even if this update is uninstalled, IDN printing could be effected adversely. DO NOT INSTALL THIS Optional MICROSOFT UPDATE. If this was already done, reload the Ghost image for the 2015 posted on MOS, and reload all other applicable Microsoft Updates. As of August of 2016 the RES Microsoft security bulletin has been split off from the combined RES/e7 bulletin. -

Your Chakra Is Not Aligned Hunting Bugs in the Microsoft Edge Script Engine About Me
Your Chakra Is Not Aligned Hunting bugs in the Microsoft Edge Script Engine About Me ● Natalie Silvanovich AKA natashenka ● Project Zero member ● Previously did mobile security on Android and BlackBerry ● ECMAScript enthusiast What are Edge and Chakra ● Edge: Windows 10 browser ● Chakra: Edge’s open-source ECMAScript core ○ Regularly updated ○ Accepts external contributions What is ECMAScript ● ECMAScript == Javascript (mostly) ● Javascript engines implement the ECMAScript standard ● ES7 released in June Why newness matters ● Standards don’t specify implementation ● Design decisions are untested ○ Security and performance advantages (and disadvantages) ● Developers and hackers learn from new bugs ● Attacks mature over time ● High contention space Goals ● Find bugs in Chakra ● Understand and improve weak areas ● Find deep, unusual bugs* Approach ● Code review ○ Finds quality bugs ○ Bugs live longer* ○ Easier to fix an entire class of bugs RTFS ● Reading the standard is important ○ Mozilla docs (MDN) is a great start ● Many features are used infrequently but cause bugs ● Features are deeply intertwined Array.species “But what if I subclass an array and slice it, and I want the thing I get back to be a regular Array and not the subclass?” class MyArray extends Array { static get [Symbol.species]() { return Array;} } ● Easily implemented by inserting a call to script into *every single* Array native call Array Conversion ● Arrays can be complicated but most Arrays are simple ○ Most implementations have simple arrays with more complex fallbacks IntegerArray Add a float FloatArray Add a non-numeric value Configure a value (e.g read-only) ES5Array VarArray Array Conversion ● Integer, Float and ES5 arrays are subclasses of Var Array superclass ● vtable swapping (for real) Array Conversion IntSegment IntArray length vtable size length left head next .. -

Configuration Sheets
PRIMERGY RX600 S4 Configuration Sheets About this manual A Configuration Sheets of Hardware Use this form to record the hardware configuration and various settings of your server. B Configuration Sheets of BIOS Setup Utility Parameters Use this form to record the settings of the BIOS Setup Utility. C Configuration Sheets of Remote Management Controller's Web Interface Use this form to record the settings of the Remote Management Controller Web interface. D Design Sheet of the RAID Configuration Use this form to record the definitions of the disk groups (or the physical packs) and the logical drives in the RAID configuration (array configuration). E Design Sheet Use this form to record the software settings. F Accident Sheet Use this form to record any failures that occur in your server. 1 Product Names The following expressions and abbreviations are used to describe the product names used in this manual. Product names Expressions and abbreviations PRIMERGY RX600 S4 This server or the server Windows Server 2003 R2, Windows Microsoft® Windows Server® 2003 R2, Standard Edition Standard Edition 2003 Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Enterprise Edition Enterprise Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise Edition Enterprise Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard Edition Standard Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Standard x64 Edition Standard x64 Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2 , Enterprise x64 Edition Enterprise x64 Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard x64 Edition Standard x64 Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise x64 Edition Enterprise x64 Edition Microsoft® Windows Server® 2003 Service Pack SP ■Trademarks Microsoft, Windows, MS, Windows Server are registered trademarks of the Microsoft Corporation in the USA and other countries. -

Linux Networking 101
The Gorilla ® Guide to… Linux Networking 101 Inside this Guide: • Discover how Linux continues its march toward world domination • Learn basic Linux administration tips • See how easy it can be to build your entire network on a Linux foundation • Find out how Cumulus Linux is your ticket to networking freedom David M. Davis ActualTech Media Helping You Navigate The Technology Jungle! In Partnership With www.actualtechmedia.com The Gorilla Guide To… Linux Networking 101 Author David M. Davis, ActualTech Media Editors Hilary Kirchner, Dream Write Creative, LLC Christina Guthrie, Guthrie Writing & Editorial, LLC Madison Emery, Cumulus Networks Layout and Design Scott D. Lowe, ActualTech Media Copyright © 2017 by ActualTech Media. All rights reserved. No portion of this book may be reproduced or used in any manner without the express written permission of the publisher except for the use of brief quotations. The information provided within this eBook is for general informational purposes only. While we try to keep the information up- to-date and correct, there are no representations or warranties, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the information, products, services, or related graphics contained in this book for any purpose. Any use of this information is at your own risk. ActualTech Media Okatie Village Ste 103-157 Bluffton, SC 29909 www.actualtechmedia.com Entering the Jungle Introduction: Six Reasons You Need to Learn Linux ....................................................... 7 1. Linux is the future ........................................................................ 9 2. Linux is on everything .................................................................. 9 3. Linux is adaptable ....................................................................... 10 4. Linux has a strong community and ecosystem ........................... 10 5. -

Time-Travel Debugging for Javascript/Node.Js
Time-Travel Debugging for JavaScript/Node.js Earl T. Barr Mark Marron Ed Maurer University College London, UK Microsoft Research, USA Microsoft, USA [email protected] [email protected] [email protected] Dan Moseley Gaurav Seth Microsoft, USA Microsoft, USA [email protected] [email protected] ABSTRACT Time-traveling in the execution history of a program during de- bugging enables a developer to precisely track and understand the sequence of statements and program values leading to an error. To provide this functionality to real world developers, we embarked on a two year journey to create a production quality time-traveling de- bugger in Microsoft’s open-source ChakraCore JavaScript engine and the popular Node.js application framework. CCS Concepts •Software and its engineering ! Software testing and debug- Figure 1: Visual Studio Code with extra time-travel functional- ging; ity (Step-Back button in top action bar) at a breakpoint. Keywords • Options for both using time-travel during local debugging Time-Travel Debugging, JavaScript, Node.js and for recording a trace in production for postmortem de- bugging or other analysis (Section 2.1). 1. INTRODUCTION • Reverse-Step Local and Dynamic operations (Section 2.2) Modern integrated development environments (IDEs) provide a that allow the developer to step-back in time to the previously range of tools for setting breakpoints, examining program state, and executed statement in the current function or to step-back in manually logging execution. These features enable developers to time to the previously executed statement in any frame in- quickly track down localized bugs, provided all of the relevant val- cluding exception throws or callee returns. -

NET Technology Guide for Business Applications // 1
.NET Technology Guide for Business Applications Professional Cesar de la Torre David Carmona Visit us today at microsoftpressstore.com • Hundreds of titles available – Books, eBooks, and online resources from industry experts • Free U.S. shipping • eBooks in multiple formats – Read on your computer, tablet, mobile device, or e-reader • Print & eBook Best Value Packs • eBook Deal of the Week – Save up to 60% on featured titles • Newsletter and special offers – Be the first to hear about new releases, specials, and more • Register your book – Get additional benefits Hear about it first. Get the latest news from Microsoft Press sent to your inbox. • New and upcoming books • Special offers • Free eBooks • How-to articles Sign up today at MicrosoftPressStore.com/Newsletters Wait, there’s more... Find more great content and resources in the Microsoft Press Guided Tours app. The Microsoft Press Guided Tours app provides insightful tours by Microsoft Press authors of new and evolving Microsoft technologies. • Share text, code, illustrations, videos, and links with peers and friends • Create and manage highlights and notes • View resources and download code samples • Tag resources as favorites or to read later • Watch explanatory videos • Copy complete code listings and scripts Download from Windows Store Free ebooks From technical overviews to drilldowns on special topics, get free ebooks from Microsoft Press at: www.microsoftvirtualacademy.com/ebooks Download your free ebooks in PDF, EPUB, and/or Mobi for Kindle formats. Look for other great resources at Microsoft Virtual Academy, where you can learn new skills and help advance your career with free Microsoft training delivered by experts. -

College Catalog
401 Medical Park Drive Concord, NC 28025 704-403-1555 • Fax: 704-403-2077 Email: [email protected] www.cabarruscollege.edu 2016–2017 CATALOG CONTENTS Greetings from the President .................................................................................................................. 3 Academic Calendars .................................................................................................................................. 4 Accreditation .............................................................................................................................................. 8 Right to Know ........................................................................................................................................... 9 Right to Revise ........................................................................................................................................... 9 History ......................................................................................................................................................... 9 Vision ........................................................................................................................................................ 10 Mission & Goals ...................................................................................................................................... 10 Core Values ............................................................................................................................................. -
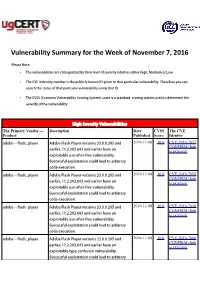
Vulnerability Summary for the Week of November 7, 2016
Vulnerability Summary for the Week of November 7, 2016 Please Note: • The vulnerabilities are cattegorized by their level of severity which is either High, Medium or Low. • The !" indentity number is the #ublicly $nown %& given to that #articular vulnerability. Therefore you can search the status of that #articular vulnerability using that %&. • The !'S (Common !ulnerability 'coring System) score is a standard scoring system used to determine the severity of the vulnerability. High Severity Vulnerabilities The Primary Vendor --- Description Date CVSS The CVE Product Published Score Identity adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7857 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7858 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7859 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7860 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable type confusion vulnerability.