Setting up Virtual Desktops in Horizon Console
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Accelerometer Sensor Emulation!!!! by Columbia University NYC Thesis Raghavan Santhanam Benchmark
Enabling the Virtual Phones to remotely sense the Real Phones in real-time ~ A Sensor Emulation initiative for virtualized Android-x86 ~ Raghavan Santhanam Submitted in partial fulfillment of the requirements for the degree of Master of Science in Computer Science in the School of Engineering and Applied Science 2014 © 2014 Raghavan Santhanam All Rights Reserved ABSTRACT Enabling the Virtual Phones to remotely sense the Real Phones in real-time ~ A Sensor Emulation initiative for virtualized Android-x86 ~ Smartphones nowadays have the ground-breaking features that were only a figment of one’s imagination. For the ever-demanding cellphone users, the exhaustive list of features that a smartphone supports just keeps getting more exhaustive with time. These features aid one’s personal and professional uses as well. Extrapolating into the future the features of a present-day smartphone, the lives of us humans using smartphones are going to be unimaginably agile. With the above said emphasis on the current and future potential of a smartphone, the ability to virtualize smartphones with all their real-world features into a virtual platform, is a boon for those who want to rigorously experiment and customize the virtualized smartphone hardware without spending an extra penny. Once virtualizable independently on a larger scale, the idea of virtualized smartphones with all the virtualized pieces of hardware takes an interesting turn with the sensors being virtualized in a way that’s closer to the real-world behavior. When accessible remotely with the real-time responsiveness, the above mentioned real-world behavior will be a real dealmaker in many real-world systems, namely, the life-saving systems like the ones that instantaneously get alerts about harmful magnetic radiations in the deep mining areas, etc. -

Microsoft Security Update for January 2020 Fixes 49 Security Vulnerabilities
Microsoft Security Update for January 2020 Fixes 49 Security Vulnerabilities Overview Microsoft released the January security update on Tuesday, fixing 49 security issues ranging from simple spoofing attacks to remote code execution, discovered in products like .NET Framework, Apps, ASP.NET, Common Log File System Driver, Microsoft Dynamics, Microsoft Graphics Component, Microsoft Office, Microsoft Scripting Engine, Microsoft Windows, Microsoft Windows Search Component, Windows Hyper-V, Windows Media, Windows RDP, Windows Subsystem for Linux, and Windows Update Stack. Of the vulnerabilities fixed by Microsoft's this monthly update, a total of eight critical vulnerabilities exist in the .NET Framework, ASP.NET, Microsoft Scripting Engine, and Windows RDP. In addition, there are 41 important vulnerabilities. Critical Vulnerabilities The following are eight critical vulnerabilities covered in this update. @NSFOUS 2020 http://www.nsfocus.com Windows RDP CVE-2020-0609、CVE-2020-0610 These two remote code execution vulnerabilities in the Windows Remote Desktop Gateway (RD Gateway) could be exploited by unauthenticated attackers. If the two vulnerabilities are exploited successfully, arbitrary code may be executed on the target system, allowing the attacker to install the program, view, change or delete data, or create a new account with full user rights. To exploit this vulnerability, an attacker needs to send a specially crafted request to the RD gateway of the target system via RDP. This update addresses these issues by correcting the way the RD gateway handles connection requests. For more details about the vulnerabilities and download updates, please refer to Microsoft's official security advisories: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0609 https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0610 CVE-2020-0611 This is a remote code execution vulnerability in Windows Remote Desktop clients. -

Vmware Horizon 7 Datasheet
DATASHEET VMWARE HORIZON 7 AT A GLANCE End-User Computing Today VMware Horizon® 7 delivers virtualized or Today, end users are leveraging new types of devices for work—accessing hosted desktops and applications through a Windows and Linux applications alongside iOS or Android applications—and single platform to end users. These desktop are more mobile than ever. and application services—including Remote Desktop Services (RDS) hosted apps, In this new mobile cloud world, managing and delivering services to end users packaged apps with VMware ThinApp®, with traditional PC-centric tools have become increasingly di cult. Data loss software-as-a-service (SaaS) apps, and and image drift are real security and compliance concerns. And organizations even virtualized apps from Citrix—can all are struggling to contain costs. Horizon 7 provides IT with a new streamlined be accessed from one digital workspace approach to deliver, protect, and manage Windows and Linux desktops and across devices, locations, media, and applications while containing costs and ensuring that end users can work connections without compromising quality anytime, anywhere, on any device. and user experience. Leveraging complete workspace environment Horizon 7: Delivering Desktops and Applications as a Service management and optimized for the software– defi ned data center, Horizon 7 helps IT control, Horizon 7 enables IT to centrally manage images to streamline management, manage, and protect all of the Windows reduce costs, and maintain compliance. With Horizon 7, virtualized or hosted resources end users want, at the speed they desktops and applications can be delivered through a single platform to end expect, with the e ciency business demands. -

Virtualization with Limited Hardware Support
Virtualization with Limited Hardware Support by Bi Wu Department of Computer Science Duke University Date: Approved: Landon Cox, Supervisor Jeffrey Chase Alvin Lebeck Harvey Tuch Dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Department of Computer Science in the Graduate School of Duke University 2013 Abstract Virtualization with Limited Hardware Support by Bi Wu Department of Computer Science Duke University Date: Approved: Landon Cox, Supervisor Jeffrey Chase Alvin Lebeck Harvey Tuch An abstract of a dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Department of Computer Science in the Graduate School of Duke University 2013 Copyright c 2013 by Bi Wu All rights reserved except the rights granted by the Creative Commons Attribution-Noncommercial Licence Abstract Over the past 15 years, virtualization has become a standard way to migrate old software to new hardware, isolate untrusted code, and encapsulate application state. However, many of the techniques for implementing common virtualization functional- ity, such as transparent isolation and full-system record and replay, rely on hardware features provided by the x86 architecture. As the mainstream computing landscape diversifies to include less feature-rich mobile and embedded systems, it is critical to rethink how to efficiently provide core virtualization functionality with limited hardware support. As a result, this dissertation explores the feasibility of providing common virtu- alization functionality with limited hardware support. We propose three approaches to virtualization using limited hardware support. First, we describe a way to transparently virtualize a CPU using hardware break- points and on-demand control-flow analysis. -

Vmware Product Guide
VMWARE PRODUCT GUIDE J U L Y 2017 Table of Contents 1 TERMS APPLICABLE TO ALL PRODUCTS 4 - 10 2 DATA CENTER AND CLOUD INFRASTRUCTURE 11 - 23 2.1 VMware vSphere 11 - 13 2.2 VMware vSphere Essentials Plus with vSphere Storage Appliance 13 2.3 VMware vCloud Director 13 2.4 VMware vSphere Storage Appliance 14 2.5 VMware NSX Platform 14 - 15 2.6 VMware vSAN 15 - 20 2.7 VMware vSphere Data Protection Advanced 20- 21 2.8 VMware vCenter Support Assistant 21 2.9 VMware Software Manager 21 2.10 VMware Continuent 21 - 22 2.11 VMware Photon Platform 22 - 23 3 INFRASTRUCTURE AND OPERATIONS MANAGEMENT 24 - 30 3.1 VMware vCenter Server 24 3.2 VMware vRealize Suite 24 - 25 3.3 VMware vRealize Operations Insight 25 3.4 VMware Site Recovery Manager 25 - 26 3.5 VMware vRealize Automation 26 - 27 3.6 VMware vCloud Connector Core 27 3.7 VMware vRealize Log Insight 27 - 28 3.8 VMware vRealize Operations Management Pack for EPIC 28 - 29 3.9 VMware vRealize Code Stream 29 3.10 VMware Health Analyzer Collector 29 3.11 VMware vRealize Operations Management Pack for MEDITECH 29 3.12 VMware vRealize Network Insight 29 - 30 4 SECURITY PRODUCTS 31 4.1 VMware vCloud Networking and Security 31 5 VMWARE SUITES 32 - 39 5.1 VMware vCloud Suite 32 - 33 5.2 VMware vSphere with Operations Management 33 - 35 5.3 VMware vRealize Operations 35 - 37 5.4 VMware vCloud NFV 37 5.5 VMware Cloud Foundation 38 - 39 1 5.6 Server SAN Suite 39 6 DESKTOP AND END USER COMPUTING 40 - 56 6.1 VMware Horizon View Enterprise Add-on 40 6.2 VMware Horizon Client for IOS 40 - 41 6.3 VMware Horizon -

A Full GPU Virtualization Solution with Mediated Pass-Through
A Full GPU Virtualization Solution with Mediated Pass-Through Kun Tian, Yaozu Dong, David Cowperthwaite Intel Corporation Abstract shows the spectrum of GPU virtualization solutions Graphics Processing Unit (GPU) virtualization is an (with hardware acceleration increasing from left to enabling technology in emerging virtualization right). Device emulation [7] has great complexity and scenarios. Unfortunately, existing GPU virtualization extremely low performance, so it does not meet today’s approaches are still suboptimal in performance and full needs. API forwarding [3][9][22][31] employs a feature support. frontend driver, to forward the high level API calls inside a VM, to the host for acceleration. However, API This paper introduces gVirt, a product level GPU forwarding faces the challenge of supporting full virtualization implementation with: 1) full GPU features, due to the complexity of intrusive virtualization running native graphics driver in guest, modification in the guest graphics software stack, and and 2) mediated pass-through that achieves both good incompatibility between the guest and host graphics performance and scalability, and also secure isolation software stacks. Direct pass-through [5][37] dedicates among guests. gVirt presents a virtual full-fledged GPU the GPU to a single VM, providing full features and the to each VM. VMs can directly access best performance, but at the cost of device sharing performance-critical resources, without intervention capability among VMs. Mediated pass-through [19], from the hypervisor in most cases, while privileged passes through performance-critical resources, while operations from guest are trap-and-emulated at minimal mediating privileged operations on the device, with cost. Experiments demonstrate that gVirt can achieve good performance, full features, and sharing capability. -

3700Document22374461
Copyright (c) 2018, Oracle. All rights reserved. RES QA / Test – Microsoft Patch Security Report (Doc ID 2237446.1) To Bottom Modified: 16-Apr-2018 Type: REFERENCE In this Document Purpose Scope Details Windows Security Updates Miscellaneous Information Internet Explorer 7 Known Issues Internet Explorer 8 Known Issues Internet Explorer 9 Known Issues Internet Explorer 10 Known Issues Internet Explorer 11 Known Issues Adobe Known Issues Non-Security, High Priority Updates Microsoft Security Essentials References APPLIES TO: Oracle Hospitality RES 3700 - Version 4.9.0 and later Information in this document applies to any platform. PURPOSE The Security Report contains a listing of select Microsoft patches that are directly related to the RES and E7 applications and have been tested against the RES and E7 applications to validate there are no issues or identify any updates that should NOT be installed. The list is not inclusive of ALL Microsoft patches. This report is updated monthly for patches released monthly and YTD cumulative. SCOPE This document is intended for support employees and users of the RES E7 products. DETAILS WARNING: On Workstation 2015 – POSReady 2009, the Microsoft “Optional Hardware” Update, “MosChip Semiconductor Technology Ltd – Bus Controllers and Ports – PCI Multi-IO Controller” is incompatible with the RES IDN Driver, and will cause IDN Printing to fail. Even if this update is uninstalled, IDN printing could be effected adversely. DO NOT INSTALL THIS Optional MICROSOFT UPDATE. If this was already done, reload the Ghost image for the 2015 posted on MOS, and reload all other applicable Microsoft Updates. As of August of 2016 the RES Microsoft security bulletin has been split off from the combined RES/e7 bulletin. -

Configuration Sheets
PRIMERGY RX600 S4 Configuration Sheets About this manual A Configuration Sheets of Hardware Use this form to record the hardware configuration and various settings of your server. B Configuration Sheets of BIOS Setup Utility Parameters Use this form to record the settings of the BIOS Setup Utility. C Configuration Sheets of Remote Management Controller's Web Interface Use this form to record the settings of the Remote Management Controller Web interface. D Design Sheet of the RAID Configuration Use this form to record the definitions of the disk groups (or the physical packs) and the logical drives in the RAID configuration (array configuration). E Design Sheet Use this form to record the software settings. F Accident Sheet Use this form to record any failures that occur in your server. 1 Product Names The following expressions and abbreviations are used to describe the product names used in this manual. Product names Expressions and abbreviations PRIMERGY RX600 S4 This server or the server Windows Server 2003 R2, Windows Microsoft® Windows Server® 2003 R2, Standard Edition Standard Edition 2003 Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Enterprise Edition Enterprise Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise Edition Enterprise Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard Edition Standard Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Standard x64 Edition Standard x64 Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2 , Enterprise x64 Edition Enterprise x64 Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard x64 Edition Standard x64 Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise x64 Edition Enterprise x64 Edition Microsoft® Windows Server® 2003 Service Pack SP ■Trademarks Microsoft, Windows, MS, Windows Server are registered trademarks of the Microsoft Corporation in the USA and other countries. -

KVM/ARM: Experiences Building the Linux ARM Hypervisor
KVM/ARM: Experiences Building the Linux ARM Hypervisor Christoffer Dall and Jason Nieh fcdall, [email protected] Department of Computer Science, Columbia University Technical Report CUCS-010-13 April 2013 Abstract ization. To address this problem, ARM has introduced hardware virtualization extensions in the newest ARM As ARM CPUs become increasingly common in mo- CPU architectures. ARM has benefited from the hind- bile devices and servers, there is a growing demand sight of x86 in its design. For example, nested page for providing the benefits of virtualization for ARM- tables, not part of the original x86 virtualization hard- based devices. We present our experiences building the ware, are standard in ARM. However, there are impor- Linux ARM hypervisor, KVM/ARM, the first full sys- tant differences between ARM and x86 virtualization ex- tem ARM virtualization solution that can run unmodified tensions such that x86 hypervisor designs may not be guest operating systems on ARM multicore hardware. directly amenable to ARM. These differences may also KVM/ARM introduces split-mode virtualization, allow- impact hypervisor performance, especially for multicore ing a hypervisor to split its execution across CPU modes systems, but have not been evaluated with real hardware. to take advantage of CPU mode-specific features. This allows KVM/ARM to leverage Linux kernel services and We describe our experiences building KVM/ARM, functionality to simplify hypervisor development and the ARM hypervisor in the mainline Linux kernel. maintainability while utilizing recent ARM hardware KVM/ARM is the first hypervisor to leverage ARM virtualization extensions to run application workloads in hardware virtualization support to run unmodified guest guest operating systems with comparable performance operating systems (OSes) on ARM multicore hardware. -

Linux Networking 101
The Gorilla ® Guide to… Linux Networking 101 Inside this Guide: • Discover how Linux continues its march toward world domination • Learn basic Linux administration tips • See how easy it can be to build your entire network on a Linux foundation • Find out how Cumulus Linux is your ticket to networking freedom David M. Davis ActualTech Media Helping You Navigate The Technology Jungle! In Partnership With www.actualtechmedia.com The Gorilla Guide To… Linux Networking 101 Author David M. Davis, ActualTech Media Editors Hilary Kirchner, Dream Write Creative, LLC Christina Guthrie, Guthrie Writing & Editorial, LLC Madison Emery, Cumulus Networks Layout and Design Scott D. Lowe, ActualTech Media Copyright © 2017 by ActualTech Media. All rights reserved. No portion of this book may be reproduced or used in any manner without the express written permission of the publisher except for the use of brief quotations. The information provided within this eBook is for general informational purposes only. While we try to keep the information up- to-date and correct, there are no representations or warranties, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the information, products, services, or related graphics contained in this book for any purpose. Any use of this information is at your own risk. ActualTech Media Okatie Village Ste 103-157 Bluffton, SC 29909 www.actualtechmedia.com Entering the Jungle Introduction: Six Reasons You Need to Learn Linux ....................................................... 7 1. Linux is the future ........................................................................ 9 2. Linux is on everything .................................................................. 9 3. Linux is adaptable ....................................................................... 10 4. Linux has a strong community and ecosystem ........................... 10 5. -

Virtual GPU Software User Guide Is Organized As Follows: ‣ This Chapter Introduces the Capabilities and Features of NVIDIA Vgpu Software
Virtual GPU Software User Guide DU-06920-001 _v13.0 Revision 02 | August 2021 Table of Contents Chapter 1. Introduction to NVIDIA vGPU Software..............................................................1 1.1. How NVIDIA vGPU Software Is Used....................................................................................... 1 1.1.2. GPU Pass-Through.............................................................................................................1 1.1.3. Bare-Metal Deployment.....................................................................................................1 1.2. Primary Display Adapter Requirements for NVIDIA vGPU Software Deployments................2 1.3. NVIDIA vGPU Software Features............................................................................................. 3 1.3.1. GPU Instance Support on NVIDIA vGPU Software............................................................3 1.3.2. API Support on NVIDIA vGPU............................................................................................ 5 1.3.3. NVIDIA CUDA Toolkit and OpenCL Support on NVIDIA vGPU Software...........................5 1.3.4. Additional vWS Features....................................................................................................8 1.3.5. NVIDIA GPU Cloud (NGC) Containers Support on NVIDIA vGPU Software...................... 9 1.3.6. NVIDIA GPU Operator Support.......................................................................................... 9 1.4. How this Guide Is Organized..................................................................................................10 -
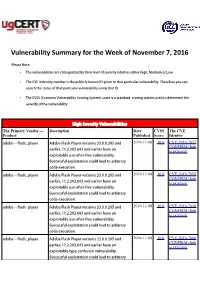
Vulnerability Summary for the Week of November 7, 2016
Vulnerability Summary for the Week of November 7, 2016 Please Note: • The vulnerabilities are cattegorized by their level of severity which is either High, Medium or Low. • The !" indentity number is the #ublicly $nown %& given to that #articular vulnerability. Therefore you can search the status of that #articular vulnerability using that %&. • The !'S (Common !ulnerability 'coring System) score is a standard scoring system used to determine the severity of the vulnerability. High Severity Vulnerabilities The Primary Vendor --- Description Date CVSS The CVE Product Published Score Identity adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7857 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7858 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7859 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7860 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable type confusion vulnerability.