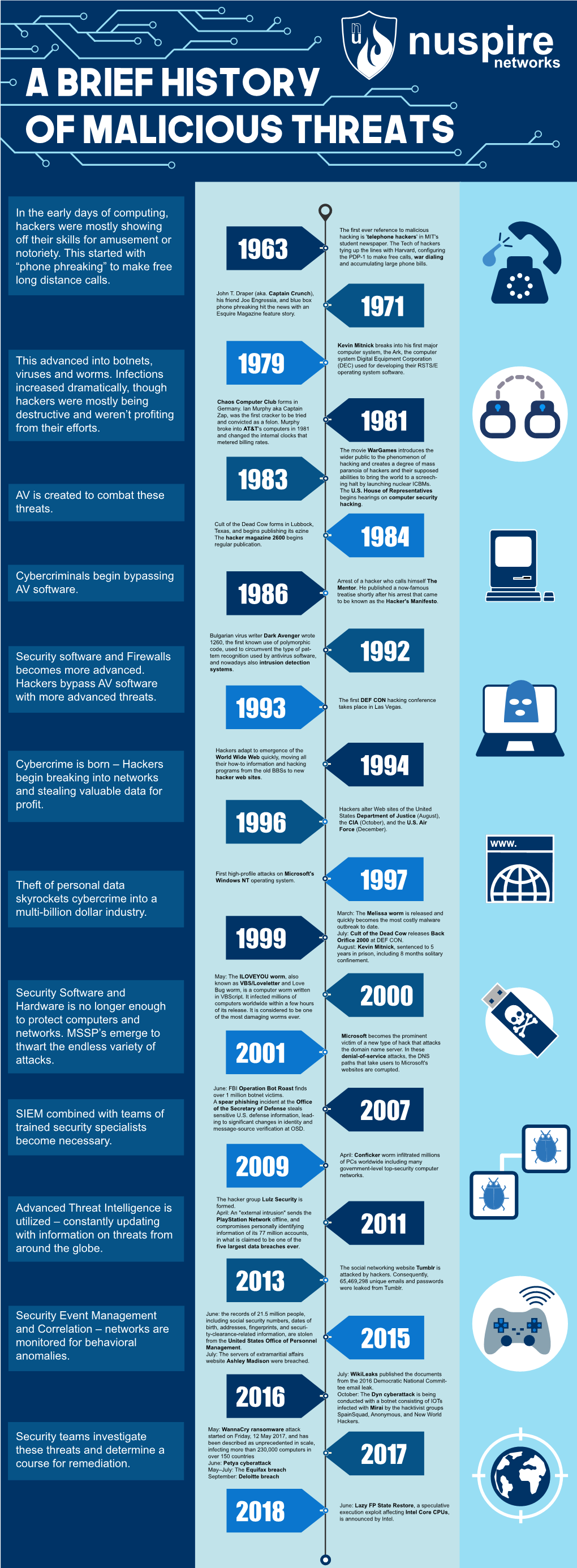
In the Early Days of Computing, Hackers Were Mostly Showing Off
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PC Magazine Fighting Spyware Viruses And
01_577697 ffirs.qxd 12/7/04 11:49 PM Page i PC Magazine® Fighting Spyware, Viruses, and Malware Ed Tittel TEAM LinG - Live, Informative, Non-cost and Genuine ! 01_577697 ffirs.qxd 12/7/04 11:49 PM Page ii PC Magazine® Fighting Spyware, Viruses, and Malware Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256-5774 www.wiley.com Copyright © 2005 by Wiley Publishing Published simultaneously in Canada ISBN: 0-7645-7769-7 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1B/RW/RS/QU/IN No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, e-mail: [email protected]. Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. -

Why We Should Consider the Plurality of Hacker and Maker Cultures 2017
Repositorium für die Medienwissenschaft Sebastian Kubitschko; Annika Richterich; Karin Wenz „There Simply Is No Unified Hacker Movement.“ Why We Should Consider the Plurality of Hacker and Maker Cultures 2017 https://doi.org/10.25969/mediarep/1115 Veröffentlichungsversion / published version Zeitschriftenartikel / journal article Empfohlene Zitierung / Suggested Citation: Kubitschko, Sebastian; Richterich, Annika; Wenz, Karin: „There Simply Is No Unified Hacker Movement.“ Why We Should Consider the Plurality of Hacker and Maker Cultures. In: Digital Culture & Society, Jg. 3 (2017), Nr. 1, S. 185– 195. DOI: https://doi.org/10.25969/mediarep/1115. Erstmalig hier erschienen / Initial publication here: https://doi.org/10.14361/dcs-2017-0112 Nutzungsbedingungen: Terms of use: Dieser Text wird unter einer Creative Commons - This document is made available under a creative commons - Namensnennung - Nicht kommerziell - Keine Bearbeitungen 4.0 Attribution - Non Commercial - No Derivatives 4.0 License. For Lizenz zur Verfügung gestellt. Nähere Auskünfte zu dieser Lizenz more information see: finden Sie hier: https://creativecommons.org/licenses/by-nc-nd/4.0 https://creativecommons.org/licenses/by-nc-nd/4.0 “There Simply Is No Unified Hacker Movement.” Why We Should Consider the Plurality of Hacker and Maker Cultures Sebastian Kubitschko in Conversation with Annika Richterich and Karin Wenz Sebastian Kubitschko is a postdoctoral researcher at the Centre for Media, Communication and Information Research (ZeMKI) at the University of Bremen in Germany. His main research fields are political communication, social movements and civil society organisations. In order to address the relevance of new forms of techno-political civic engagement, he has conducted qualitative, empirical research on one of the world’s oldest and largest hacker organisations, the Chaos Computer Club (CCC). -

Paradise Lost , Book III, Line 18
_Paradise Lost_, book III, line 18 %%%%%%%%%%%%%%%%%%%%%%%% ++++++++++Hacker's Encyclopedia++++++++ ===========by Logik Bomb (FOA)======== <http://www.xmission.com/~ryder/hack.html> ---------------(1997- Revised Second Edition)-------- ##################V2.5################## %%%%%%%%%%%%%%%%%%%%%%%% "[W]atch where you go once you have entered here, and to whom you turn! Do not be misled by that wide and easy passage!" And my Guide [said] to him: "That is not your concern; it is his fate to enter every door. This has been willed where what is willed must be, and is not yours to question. Say no more." -Dante Alighieri _The Inferno_, 1321 Translated by John Ciardi Acknowledgments ---------------------------- Dedicated to all those who disseminate information, forbidden or otherwise. Also, I should note that a few of these entries are taken from "A Complete List of Hacker Slang and Other Things," Version 1C, by Casual, Bloodwing and Crusader; this doc started out as an unofficial update. However, I've updated, altered, expanded, re-written and otherwise torn apart the original document, so I'd be surprised if you could find any vestiges of the original file left. I think the list is very informative; it came out in 1990, though, which makes it somewhat outdated. I also got a lot of information from the works listed in my bibliography, (it's at the end, after all the quotes) as well as many miscellaneous back issues of such e-zines as _Cheap Truth _, _40Hex_, the _LOD/H Technical Journals_ and _Phrack Magazine_; and print magazines such as _Internet Underground_, _Macworld_, _Mondo 2000_, _Newsweek_, _2600: The Hacker Quarterly_, _U.S. News & World Report_, _Time_, and _Wired_; in addition to various people I've consulted. -

Dictionary of Health Information Technology and Security
DICTIONARY OF HEALTH INFORMATION TECHNOLOGY AND SECURITY Dr. David Edward Marcinko, MBA , CFP© Certifi ed Medical Planner© Editor-in-Chief Hope Rachel Hetico, RN, MSHA, CPHQ Certifi ed Medical Planner© Managing Editor NEW YORK 33021009_FM1.indd021009_FM1.indd i 003/17/20073/17/2007 116:48:506:48:50 Copyright © 2007 Springer Publishing Company, LLC All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmit- ted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior permission of Springer Publishing Company, LLC. Springer Publishing Company, LLC 11 West 42nd Street New York, NY 10036 www.springerpub.com Acquisitions Editor: Sheri W. Sussman Production Editor: Carol Cain Cover design: Mimi Flow Composition: Apex Publishing, LLC 07 08 09 10/ 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data Dictionary of health information technology and security / David Edward Marcinko, editor-in-chief, Hope Rachel Hetico, managing editor. p. ; cm. Includes bibliographical references. ISBN-13: 978-0-8261-4995-4 (alk. paper) ISBN-10: 0-8261-4995-2 (alk. paper) 1. Medical informatics—Dictionaries. 2. Medicine—Information technology—Dictionaries. 3. Medical informatics—Security measures— Dictionaries. I. Marcinko, David E. (David Edward) II. Hetico, Hope R. [DNLM: 1. Informatics—Dictionary—English. 2. Medical Informatics— Dictionary—English. 3. Computer Communication Networks—Dictionary— English. 4. Computer Security—Dictionary—English. W 13 D557165 2007] R858.D53 2007 610.3—dc22 2007005879 Printed in the United States of America by RR Donnelley. 33021009_FM1.indd021009_FM1.indd iiii 003/17/20073/17/2007 116:48:516:48:51 Th e Dictionary of Health Information Technology and Security is dedicated to Edward Anthony Marcinko Sr., and Edward Anthony Marcinko Jr., of Fell’s Point, Maryland. -

Cybersecurity Forum Für Datensicherheit, Datenschutz Und Datenethik 23
3. JAHRESTAGUNG CYBERSECURITY FORUM FÜR DATENSICHERHEIT, DATENSCHUTZ UND DATENETHIK 23. APRIL 2020, FRANKFURT AM MAIN #cyberffm Premium-Partner: Veranstaltungspartner: 3. JAHRESTAGUNG CYBERSECURITY DEUTSCHLAND — DIGITAL — SICHER — BSI Die Schadsoftware »Emotet« hat uns in den letzten Wochen und Monaten erneut schmerzhaft vor Augen geführt, welche Auswirkungen es haben kann, wenn man die Vorteile der Digitalisierung genießt, ohne die dafür unabdingbar notwendige Infor- mationssicherheit zu gewährleisten. Stadtverwaltungen, Behörden, Krankenhäuser und Universitäten wurden lahmgelegt, Unternehmen mussten zeitweise den Betrieb einstellen. Die Folgen sind für jeden von uns spürbar: Arbeitsplätze sind in Gefahr, Waren und Dienstleistungen können nicht mehr angeboten und verkauft werden, Krankenhäuser müssen die Patientenannahme ablehnen. Stadtverwaltungen sind nicht mehr arbeitsfähig und schließen ihre Bürgerbüros. Bürgerinnen und Bürger konnten keine Ausweise und Führerscheine beantragen, keine Autos anmelden und keine Sperrmüllabfuhr bestellen. Sogar Hochzeiten mussten verschoben werden. Und wie würde die Lage wohl erst aussehen, wenn wir tatsächlich in einer voll digitalisierten Welt lebten? Das BSI beschäftigt sich damit, in welchen Anwendungsfeldern der Digitalisierung Risiken entstehen könnten und wie wir diese Risiken kalkulierbar und beherrschbar machen können. Unsere Stärke ist es, Themen der Informationssicherheit gebündelt fachlich zu analysieren und aus der gemeinsamen Analyse heraus konkrete Angebote für unterschiedliche Zielgruppen -

Flexible Infections: Computer Viruses, Human Bodies, Nation-States, Evolutionary Capitalism
Science,Helmreich Technology, / Flexible Infections& Human Values Flexible Infections: Computer Viruses, Human Bodies, Nation-States, Evolutionary Capitalism Stefan Helmreich New York University This article analyzes computer security rhetoric, particularly in the United States, argu- ing that dominant cultural understandings of immunology, sexuality, legality, citizen- ship, and capitalism powerfully shape the way computer viruses are construed and com- bated. Drawing on popular and technical handbooks, articles, and Web sites, as well as on e-mail interviews with security professionals, the author explores how discussions of computer viruses lean on analogies from immunology and in the process often encode popular anxieties about AIDS. Computer security rhetoric about compromised networks also uses language reminiscent of that used to describe the “bodies” of nation-states under military threat from without and within. Such language portrays viruses using images of foreignness, illegality, and otherness. The security response to viruses advo- cates the virtues of the flexible and adaptive response—a rhetoric that depends on evolu- tionary language but also on the ideological idiom of advanced capitalism. As networked computing becomes increasingly essential to the operations of corporations, banks, government, the military, and academia, worries about computer security and about computer viruses are intensifying among the people who manage and use these networks. The end of the 1990s saw the emergence of a small industry dedicated to antivirus protection software, and one can now find on the World Wide Web a great deal of information about how viruses work, how they can be combated, and how computer users might keep up with ever-changing inventories and taxonomies of the latest viruses. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

Ethical Hacking
Ethical Hacking Alana Maurushat University of Ottawa Press ETHICAL HACKING ETHICAL HACKING Alana Maurushat University of Ottawa Press 2019 The University of Ottawa Press (UOP) is proud to be the oldest of the francophone university presses in Canada and the only bilingual university publisher in North America. Since 1936, UOP has been “enriching intellectual and cultural discourse” by producing peer-reviewed and award-winning books in the humanities and social sciences, in French or in English. Library and Archives Canada Cataloguing in Publication Title: Ethical hacking / Alana Maurushat. Names: Maurushat, Alana, author. Description: Includes bibliographical references. Identifiers: Canadiana (print) 20190087447 | Canadiana (ebook) 2019008748X | ISBN 9780776627915 (softcover) | ISBN 9780776627922 (PDF) | ISBN 9780776627939 (EPUB) | ISBN 9780776627946 (Kindle) Subjects: LCSH: Hacking—Moral and ethical aspects—Case studies. | LCGFT: Case studies. Classification: LCC HV6773 .M38 2019 | DDC 364.16/8—dc23 Legal Deposit: First Quarter 2019 Library and Archives Canada © Alana Maurushat, 2019, under Creative Commons License Attribution— NonCommercial-ShareAlike 4.0 International (CC BY-NC-SA 4.0) https://creativecommons.org/licenses/by-nc-sa/4.0/ Printed and bound in Canada by Gauvin Press Copy editing Robbie McCaw Proofreading Robert Ferguson Typesetting CS Cover design Édiscript enr. and Elizabeth Schwaiger Cover image Fragmented Memory by Phillip David Stearns, n.d., Personal Data, Software, Jacquard Woven Cotton. Image © Phillip David Stearns, reproduced with kind permission from the artist. The University of Ottawa Press gratefully acknowledges the support extended to its publishing list by Canadian Heritage through the Canada Book Fund, by the Canada Council for the Arts, by the Ontario Arts Council, by the Federation for the Humanities and Social Sciences through the Awards to Scholarly Publications Program, and by the University of Ottawa. -

IBM X-Force Threat Insight Quarterly 2 X-Force Threat Insight Quarterly IBM Security Solutions
IBM Security Solutions May 2011 IBM X-Force Threat Insight Quarterly 2 X-Force Threat Insight Quarterly IBM Security Solutions Contents About the report 2 About the Report The IBM X-Force® Threat Insight Quarterly is designed to highlight some of the most significant threats and challenges 3 Evolution: From Nuisance to Weapon facing security professionals today. This report is a product of IBM Managed Security Services and the IBM X-Force 8 Prolific and Impacting Issues of Q1 2011 research and development team. Each issue focuses on specific challenges and provides a recap of the most significant recent 16 References online threats. IBM Managed Security Services are designed to help an organization improve its information security, by outsourcing security operations or supplementing your existing security teams. The IBM protection on-demand platform helps deliver Managed Security Services and the expertise, knowledge and infrastructure an organization needs to secure its information assets from Internet attacks. The X-Force team provides the foundation for a preemptive approach to Internet security. The X-Force team is one of the best-known commercial security research groups in the world. This group of security experts researches and evaluates vulnerabilities and security issues, develops assessment and countermeasure technology for IBM security products, and educates the public about emerging Internet threats. We welcome your feedback. Questions or comments regarding the content of this report should be addressed to [email protected]. 3 X-Force Threat Insight Quarterly IBM Security Solutions Evolution: From Nuisance to Weapon One of the more notable examples here is Brain3, a boot sector infector which originated in Pakistan and released in 1986, was Creeper, Wabbit, Animal, Elk Cloner, Brain, Vienna, Lehigh, one of the first examples of malware that infected PC’s running Stoned, Jerusalem. -

Introduction
Introduction Toward a Radical Criminology of Hackers In the expansive Rio Hotel and Casino in Las Vegas, I stood in line for around an hour and a half to pay for my badge for admittance into DEF CON 21, one of the largest hacker conventions in the world. The wad of cash in my hand felt heavier than it should have as I approached the badge vendor. DEF CON is an extravagant affair and attendees pay for it (though, from my own readings, the conference administrators work to keep the costs reduced). The line slowly trickled down the ramp into the hotel con- vention area where the badge booths were arranged. As I laid eyes on the convention, my jaw dropped. It was packed. Attendees were already mov- ing hurriedly throughout the place, engaged in energetic conversations. Black t- shirts— a kind of hacker uniform— were everywhere. Las Vegas- and gambling- themed décor lined the walls and floors. Already, I could see a line forming at the DEF CON merchandise booth. Miles, a hacker I had gotten to know throughout my research, mentioned that if I wanted some of the “swag” or “loot” (the conference merchandise), I should go ahead and get in line, a potential three- to four-hour wait. Seemingly, everyone wanted to purchase merchandise to provide some evidence they were in attendance. Wait too long and the loot runs out. After winding through the serpentine line of conference attendees wait- ing for admittance, I approached the badge vendors and (dearly) departed with almost $200. Stepping into the convention area, I felt that loss in the pit of my stomach. -

Hacktivism Cyberspace Has Become the New Medium for Political Voices
White Paper Hacktivism Cyberspace has become the new medium for political voices By François Paget, McAfee Labs™ Table of Contents The Anonymous Movement 4 Origins 4 Defining the movement 6 WikiLeaks meets Anonymous 7 Fifteen Months of Activity 10 Arab Spring 10 HBGary 11 The Sony ordeal 11 Lulz security and denouncements 12 Groups surrounding LulzSec 13 Green rights 14 Other operations 15 AntiSec, doxing, and copwatching 16 Police responses 17 Anonymous in the streets 18 Manipulation and pluralism 20 Operation Megaupload 21 Communications 21 Social networks and websites 21 IRC 22 Anonymity 23 DDoS Tools 24 Cyberdissidents 25 Telecomix 26 Other achievements 27 Patriots and Cyberwarriors 28 Backlash against Anonymous 29 TeaMp0isoN 30 Other achievements 30 Conclusion 32 2 Hacktivism What is hacktivism? It combines politics, the Internet, and other elements. Let’s start with the political. Activism, a political movement emphasising direct action, is the inspiration for hacktivism. Think of Greenpeace activists who go to sea to disrupt whaling campaigns. Think of the many demonstrators who protested against human rights violations in China by trying to put out the Olympic flame during its world tour in 2008. Think of the thousands of activists who responded to the Adbusters call in July 2011 to peacefully occupy a New York City park as part of Occupy Wall Street. Adding the online activity of hacking (with both good and bad connotations) to political activism gives us hacktivism. One source claims this term was first used in an article on the filmmaker Shu Lea Cheang; the article was written by Jason Sack and published in InfoNation in 1995. -
![Reversing Malware [Based on Material from the Textbook]](https://docslib.b-cdn.net/cover/8924/reversing-malware-based-on-material-from-the-textbook-1438924.webp)
Reversing Malware [Based on Material from the Textbook]
SoftWindows 11/23/05 Reversing Malware [based on material from the textbook] Reverse Engineering (Reversing Malware) © SERG What is Malware? • Malware (malicious software) is any program that works against the interest of the system’s user or owner. • Question: Is a program that spies on the web browsing habits of the employees of a company considered malware? • What if the CEO authorized the installation of the spying program? Reverse Engineering (Reversing Malware) © SERG Reversing Malware • Revering is the strongest weapon we have against the creators of malware. • Antivirus researchers engage in reversing in order to: – analyze the latest malware, – determine how dangerous the malware is, – learn the weaknesses of malware so that effective antivirus programs can be developed. Reverse Engineering (Reversing Malware) © SERG Distributed Objects 1 SoftWindows 11/23/05 Uses of Malware • Why do people develop and deploy malware? – Financial gain – Psychological urges and childish desires to “beat the system”. – Access private data – … Reverse Engineering (Reversing Malware) © SERG Typical Purposes of Malware • Backdoor access: – Attacker gains unlimited access to the machine. • Denial-of-service (DoS) attacks: – Infect a huge number of machines to try simultaneously to connect to a target server in hope of overwhelming it and making it crash. • Vandalism: – E.g., defacing a web site. • Resource Theft: – E.g., stealing other user’s computing and network resources, such as using your neighbors’ Wireless Network. • Information Theft: – E.g., stealing other user’s credit card numbers. Reverse Engineering (Reversing Malware) © SERG Types of Malware • Viruses • Worms • Trojan Horses • Backdoors • Mobile code • Adware • Sticky software Reverse Engineering (Reversing Malware) © SERG Distributed Objects 2 SoftWindows 11/23/05 Viruses • Viruses are self-replicating programs that usually have a malicious intent.