WO 2015/077865 Al 4 June 2015 (04.06.2015) W P O P C T
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Albuquerque Citizen, 06-26-1908 Hughes & Mccreight
University of New Mexico UNM Digital Repository Albuquerque Citizen, 1891-1906 New Mexico Historical Newspapers 6-26-1908 Albuquerque Citizen, 06-26-1908 Hughes & McCreight Follow this and additional works at: https://digitalrepository.unm.edu/abq_citizen_news Recommended Citation Hughes & McCreight. "Albuquerque Citizen, 06-26-1908." (1908). https://digitalrepository.unm.edu/abq_citizen_news/2799 This Newspaper is brought to you for free and open access by the New Mexico Historical Newspapers at UNM Digital Repository. It has been accepted for inclusion in Albuquerque Citizen, 1891-1906 by an authorized administrator of UNM Digital Repository. For more information, please contact [email protected]. TRAIN ARRIVALS WEATHER FORECAST . No. i 5 P- - No 4 5. 50 p. m ..; - No. 7 Jo. Si p. m. ? '' PeuTtr, Cfllj.. J111 26. -T- oa! local No. 8 6.40 p. m. shiwerj. Sittirdii inerilli fair. f - No. p m. Albuouemje Citizen 9114$ WE GET THE NEWS FIRST VOLUME 23. ALBUUUEHQDE. NEW MEXICO. FRIDAY, JUNE 2G. 1908. NUMBER 152 ENTHUSIASTIC RECTI MYSTERY HAS NARROW AN INSAN E NOTABLE MEN ASSEMBLE DEATH OF YOUTH ESCAPE FROM HANGS HIMSELF GREETS DELEbK ANDREWS TO HONOR GRDVER CLEVELAND AT INKWELL FLAMES INJAIL Citizens of Albuquerque Joi Extend- Body of Health Seeker From Fire Starting In tFurniture Native Brooded Over Murder President Roosevelt and Governors of ing Thanks of the Commuiucy for His St. Louis Found In Brush Store Spreads to Restaur of Child Because He Several States Attend Funeral Ser- Northwest of the ant. Meat Market Thought Himself to Ability to Secure Irrigation Congress Statesman-- City. and Hall. Blame for Death. vices at Princeton for Dead Appropriation and Additional Fund Simple Ritual of Presbyterian for New Federal Building Crowds HIS COMPANION BOY Wild CANDLE USED ROPeITt Church Constitutes Extent of Serv- Meet Delegate at the Train. -

Keek Named Official Video App of Find Your Grind and Learn to Ride at Sundance Film Festival
KEEK NAMED OFFICIAL VIDEO APP OF FIND YOUR GRIND AND LEARN TO RIDE AT SUNDANCE FILM FESTIVAL Mobile Video Social Network Provides Once in a Lifetime Opportunity for Snowboard Enthusiasts to Learn to Ride with Pro Snowboarder Luke “Dingo” Trembath and More at Sundance Film Festival NEW YORK, NY (January 5, 2015)— Keek, Inc. (TSXV: KEK; OTCQX: KEEKF) announced today that it has been named the official social video app of Find Your Grind and Learn to Ride at Sundance Film Festival taking place on January 23‐24th, 2015. Keek will be documenting the entire event, providing behind‐the‐ scenes content in addition to sponsoring the Learn to Ride Sundance Contest where one lucky winner and a guest will win a 4‐day VIP trip to Park City Utah for the Sundance Film Festival. Key influencers and celebrities will be “keeking” their experiences on and off the slopes. The Learn To Ride series is a true “bucket list” VIP event, allowing celebrities and media to pair up with professional snowboard athletes to “learn to ride” with the best! This premiere event at Sundance has been voted “most coveted” by Vanity Fair for four years and counting. Past celebrity attendees have included: Lil’ Jon, Krysten Ritter, Kellan Lutz, Adrian Grenier and Alessandra. This year, for the first time ever, talented young adults and children battling chronic illnesses will hit the slopes in their newly gifted Oakley gear, receiving private lessons from pro snowboard athletes. The Keek Learn to Ride Sundance Contest was designed to attract Winter‐lovers and snowboard enthusiasts, alike. -

Prettylittleliars: How Hashtags Drive the Social TV Phenomenon
Salve Regina University Digital Commons @ Salve Regina Pell Scholars and Senior Theses Salve's Dissertations and Theses Summer 6-2013 #PrettyLittleLiars: How Hashtags Drive The Social TV Phenomenon Melanie Brozek Salve Regina University, [email protected] Follow this and additional works at: https://digitalcommons.salve.edu/pell_theses Part of the American Popular Culture Commons, Film and Media Studies Commons, and the Television Commons Brozek, Melanie, "#PrettyLittleLiars: How Hashtags Drive The Social TV Phenomenon" (2013). Pell Scholars and Senior Theses. 93. https://digitalcommons.salve.edu/pell_theses/93 This Article is brought to you for free and open access by the Salve's Dissertations and Theses at Digital Commons @ Salve Regina. It has been accepted for inclusion in Pell Scholars and Senior Theses by an authorized administrator of Digital Commons @ Salve Regina. For more information, please contact [email protected]. #PrettyLittleLiars: How Hashtags Drive The Social TV Phenomenon By Melanie Brozek Prepared for Dr. Esch English Department Salve Regina University May 10, 2013 Brozek 2 #PrettyLittleLiars: How Hashtags Drive The Social TV Phenomenon ABSTRACT: Twitter is used by many TV shows to promote discussion and encourage viewer loyalty. Most successfully, ABC Family uses Twitter to promote the teen drama Pretty Little Liars through the use of hashtags and celebrity interactions. This study analyzes Pretty Little Liars’ use of hashtags created by the network and by actors from the show. It examines how the Pretty Little Liars’ official accounts engage fans about their opinions on the show and encourage further discussion. Fans use the network- generated hashtags within their tweets to react to particular scenes and to hopefully be noticed by managers of official show accounts. -

Russell Hubright
September 2019 Forest Management Chief Russell Hubright Every work day a relatively small segment of the South Carolina Forestry Commission’s workforce ventures onto private property at the request of the owners. These natural resource professionals, known as Project Foresters in our agency, are in the woods performing field work that will enable them to develop forest management plans that are Success Story: Discovery Trail Signs at HSF Page 9 tailored to the landowners’ objectives. Depending on the complexity of the plan, producing the finished product may take as little as a few hours or as much as a week. So, why does the Forestry Commission (https://sref.info/resources/publications/ Hugo’s 30th Anniversary employ foresters who spend such a incremental-economic-impact-of-a- Pages 12 significant part of their time writing south-carolina-forestry-commission- forest management plans? As with forester) showed that for every $1 all services that our agency provides, spent on the salary and expenses of a the answer is that these plans result in Project Forester each year, more than significant public benefit. Another way $24 of additional economic activity is of putting it is that the investment that generated. South Carolina taxpayers are making And we all know that the economic through funding this work has a positive impact of forestry in South Carolina cost-benefit ratio. In fact, a 2016 study is significant - $21 billion annually, conducted by Scott Phillips and Dr. #1 cash crop, #1 export from the port Employee Spotlight: Allison Doherty Tom Straka of Clemson University of Charleston and #2 manufacturing Page 21 September 2019 1 Faifield/Newberry/Union Project Forester Chase Folk meets with a Newberry county landowner about his forest management objectives. -

Obtaining and Using Evidence from Social Networking Sites
U.S. Department of Justice Criminal Division Washington, D.C. 20530 CRM-200900732F MAR 3 2010 Mr. James Tucker Mr. Shane Witnov Electronic Frontier Foundation 454 Shotwell Street San Francisco, CA 94110 Dear Messrs Tucker and Witnov: This is an interim response to your request dated October 6, 2009 for access to records concerning "use of social networking websites (including, but not limited to Facebook, MySpace, Twitter, Flickr and other online social media) for investigative (criminal or otherwise) or data gathering purposes created since January 2003, including, but not limited to: 1) documents that contain information on the use of "fake identities" to "trick" users "into accepting a [government] official as friend" or otherwise provide information to he government as described in the Boston Globe article quoted above; 2) guides, manuals, policy statements, memoranda, presentations, or other materials explaining how government agents should collect information on social networking websites: 3) guides, manuals, policy statements, memoranda, presentations, or other materials, detailing how or when government agents may collect information through social networking websites; 4) guides, manuals, policy statements, memoranda, presentations and other materials detailing what procedures government agents must follow to collect information through social- networking websites; 5) guides, manuals, policy statements, memorandum, presentations, agreements (both formal and informal) with social-networking companies, or other materials relating to privileged user access by the Criminal Division to the social networking websites; 6) guides, manuals, memoranda, presentations or other materials for using any visualization programs, data analysis programs or tools used to analyze data gathered from social networks; 7) contracts, requests for proposals, or purchase orders for any visualization programs, data analysis programs or tools used to analyze data gathered from social networks. -

Systematic Scoping Review on Social Media Monitoring Methods and Interventions Relating to Vaccine Hesitancy
TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy www.ecdc.europa.eu ECDC TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy This report was commissioned by the European Centre for Disease Prevention and Control (ECDC) and coordinated by Kate Olsson with the support of Judit Takács. The scoping review was performed by researchers from the Vaccine Confidence Project, at the London School of Hygiene & Tropical Medicine (contract number ECD8894). Authors: Emilie Karafillakis, Clarissa Simas, Sam Martin, Sara Dada, Heidi Larson. Acknowledgements ECDC would like to acknowledge contributions to the project from the expert reviewers: Dan Arthus, University College London; Maged N Kamel Boulos, University of the Highlands and Islands, Sandra Alexiu, GP Association Bucharest and Franklin Apfel and Sabrina Cecconi, World Health Communication Associates. ECDC would also like to acknowledge ECDC colleagues who reviewed and contributed to the document: John Kinsman, Andrea Würz and Marybelle Stryk. Suggested citation: European Centre for Disease Prevention and Control. Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy. Stockholm: ECDC; 2020. Stockholm, February 2020 ISBN 978-92-9498-452-4 doi: 10.2900/260624 Catalogue number TQ-04-20-076-EN-N © European Centre for Disease Prevention and Control, 2020 Reproduction is authorised, provided the -

The Public Square Project
THE PUBLIC SQUARE PROJECT The case for building public digital infrastructure to support our community and our democracy With majority support from Australians on curbing Facebook’s influence and role on our civic spaces, it is time to create an alternative social network that serves the public interest Research report Jordan Guiao Peter Lewis CONTENTS 2 // SUMMARY 3 // INTRODUCTION 5 // REIMAGINING THE PUBLIC SQUARE 10 // A NEW PUBLIC DIGITAL INFRASTRUCTURE 12 // CONSIDERATIONS IN BUILDING PUBLIC DIGITAL INFRASTRUCTURE 17 // TOWARDS THE FUTURE 19 // CONCLUSION 20 // APPENDIX — ALTERNATE SOCIAL NETWORKS OVER TIME The public square is a place where citizens come together, exchange ideas and mediate differences. It has its origins in the physical town square, where a community can gather in a central and open public space. As towns grew and technology progressed, the public square has become an anchor of democracy, with civic features like public broadcasting creating a space between the commercial, the personal and the government that helps anchor communities in shared understanding. 1 | SUMMARY In recent times, online platforms like Facebook In re-imagining a new public square, this paper have usurped core aspects of what we expect from proposes an incremental evolution of the Australian a public square. However, Facebook’s surveillance public broadcaster, centred around principles business model and engagement-at-all-costs developed by John Reith, the creator of public algorithm is designed to promote commercial rather broadcasting, of an independent, but publicly-funded than civic objectives, creating a more divided and entity with a remit to ‘inform, educate and entertain’ distorted public discourse. -

Juniper Secure Analytics Application Configuration Guide
Juniper Secure Analytics Application Configuration Guide Release 7.3.1 Modified: 2018-07-31 Copyright © 2018, Juniper Networks, Inc. Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Juniper Networks, the Juniper Networks logo, Juniper, and Junos are registered trademarks of Juniper Networks, Inc. and/or its affiliates in the United States and other countries. All other trademarks may be property of their respective owners. Juniper Networks assumes no responsibility for any inaccuracies in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice. Juniper Secure Analytics Application Configuration Guide 7.3.1 Copyright © 2018 Juniper Networks, Inc. All rights reserved. The information in this document is current as of the date on the title page. YEAR 2000 NOTICE Juniper Networks hardware and software products are Year 2000 compliant. Junos OS has no known time-related limitations through the year 2038. However, the NTP application is known to have some difficulty in the year 2036. END USER LICENSE AGREEMENT The Juniper Networks product that is the subject of this technical documentation consists of (or is intended for use with) Juniper Networks software. Use of such software is subject to the terms and conditions of the End User License Agreement (“EULA”) posted at https://www.juniper.net/support/eula/. By downloading, installing or using such software, you agree to the terms and conditions of that EULA. ii Copyright © 2018, Juniper Networks, Inc. Table of Contents About the Documentation . vii Documentation and Release Notes . vii Documentation Conventions . -

Unmasking the Teen Cyberbully: a First Amendment-Compliant Approach to Protecting Child Victims of Anonymous, School-Related Internet Harassment Benjamin A
The University of Akron IdeaExchange@UAkron Akron Law Review Akron Law Journals November 2017 Unmasking the Teen Cyberbully: A First Amendment-Compliant Approach to Protecting Child Victims of Anonymous, School-Related Internet Harassment Benjamin A. Holden Please take a moment to share how this work helps you through this survey. Your feedback will be important as we plan further development of our repository. Follow this and additional works at: http://ideaexchange.uakron.edu/akronlawreview Part of the Constitutional Law Commons, First Amendment Commons, and the Internet Law Commons Recommended Citation Holden, Benjamin A. (2017) "Unmasking the Teen Cyberbully: A First Amendment-Compliant Approach to Protecting Child Victims of Anonymous, School-Related Internet Harassment," Akron Law Review: Vol. 51 : Iss. 1 , Article 1. Available at: http://ideaexchange.uakron.edu/akronlawreview/vol51/iss1/1 This Article is brought to you for free and open access by Akron Law Journals at IdeaExchange@UAkron, the institutional repository of The nivU ersity of Akron in Akron, Ohio, USA. It has been accepted for inclusion in Akron Law Review by an authorized administrator of IdeaExchange@UAkron. For more information, please contact [email protected], [email protected]. Holden: Unmasking the Teen Cyberbully UNMASKING THE TEEN CYBERBULLY: A FIRST AMENDMENT-COMPLIANT APPROACH TO PROTECTING CHILD VICTIMS OF ANONYMOUS, SCHOOL-RELATED INTERNET HARASSMENT By: Benjamin A. Holden* I. Introduction and Overview ............................................ 2 II. Minors and The First Amendment ................................. 9 A. The First Amendment and Minors Generally ....... 10 B. The First Amendment and The Student Speech Cases ..................................................................... 10 C. The First Amendment and The Child Protection Cases ..................................................................... 12 1. -

ED230696.Pdf
DOCUMENT RESUME ED 230.696 CE 036 054 TITLE Expandplq Employment Opportunitkes for Disadvantaged Youth. Fifth Annual Report to the President and the Congress. Report No. 9. INSTITUTION. National Commission for Employment Policy (DOL), WashinVon, D.C. *PUB DATE Dec 79 .NOTE 247p. AVAILABLE FROM5uperintendent of Documents, U.S. Government Printing Office, Washington, DC 20402. PUB TYPE .Information Analyses (070) -- Reports Descriptive (141) E RS PRICE MF01/PC10 Plus Postage. ESCRIPTORS Adolescents; Adults; *Disadvantaged Youth; Economically Disadvantaged; Educationally Disadvantaged; *Education Work Relationship; *Employment Problems; Employment Programs; *Equal Opportunities (Jobs); Federal Government; Federal Programs; Females; *Government Role; Guidelines; High Schools; Minority Groups; Program Development; School Business Relationship; Unemployment; Young Adults; Youth; *Youth Employment ABSTRACT In its fifth annual report for 1979, the National Commission for Employment Policy recomeended that the nation make a new commitment to improving the employment prospects of disadvantaged youth. In preparing its findings and recommendations op youth unemployment, the commission received information froM the Youth Task Force; academic consultants; public and private agencies; public hearings held in Detroit, Memphis, Philadelphia, and Los Angeles; and the Vice President's Task Force on Youth Employment. The principal findings and recommendations of the commi5sion are the following:. (1) while most young people are able to make the transition -
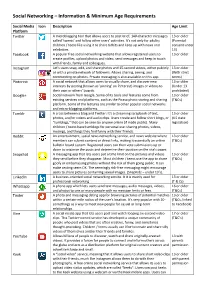
Social Networking – Information & Minimum Age Requirements
Social Networking – Information & Minimum Age Requirements Social Media Icon Description Age Limit Platform Twitter A microblogging tool that allows users to post brief, 140-character messages 13 or older called ‘tweets’ and follow other users' activities. It's not only for adults; (Parental children / teens like using it to share tidbits and keep up with news and consent under celebrities. 13) Facebook A popular free social networking website that allows registered users to 13 or older create profiles, upload photos and video, send messages and keep in touch with friends, family and colleagues. Instagram Let’s users snap, edit, and share photos and 15-second videos, either publicly 13 or older or with a private network of followers. Allows sharing, seeing, and (With strict commenting on photos. Private messaging is also available on this app. terms) Pinterest A social network that allows users to visually share, and discover new 13 or older interests by posting (known as 'pinning' on Pinterest) images or videos to (Under 13 their own or others' boards. prohibited) Google+ Social network from Google. Some of its tools and features come from 13 or older existing services and platforms, such as the Picasa photo storing and sharing (T&Cs) platform. Some of the features are similar to other popular social networks and micro-blogging platforms. Tumblr A cross between a blog and Twitter: It's a streaming scrapbook of text, 13 or older photos, and/or videos and audio clips. Users create and follow short blogs, or (US state "tumblogs," that can be seen by anyone online (if made public).