Summary of Major Us Export
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cuban Missile Crisis JCC: USSR
asdf PMUNC 2015 Cuban Missile Crisis JCC: USSR Chair: Jacob Sackett-Sanders JCC PMUNC 2015 Contents Chair Letter…………………………………………………………………...3 Introduction……………….………………………………………………….4 Topics of Concern………………………...………………….………………6 The Space Race…...……………………………....………………….....6 The Third World...…………………………………………......………7 The Eastern Bloc………………………………………………………9 The Chinese Communists…………………………………………….10 De-Stalinization and Domestic Reform………………………………11 Committee Members….……………………………………………………..13 2 JCC PMUNC 2015 Chair’s Letter Dear Delegates, It is my great pleasure to give you an early welcome to PMUNC 2015. My name is Jacob, and I’ll be your chair, helping to guide you as you take on the role of the Soviet political elites circa 1961. Originally from Wilmington, Delaware, at Princeton I study Slavic Languages and Literature. The Eastern Bloc, as well as Yugoslavia, have long been interests of mine. Our history classes and national consciousness often paints them as communist enemies, but in their own ways, they too helped to shape the modern world that we know today. While ultimately failed states, they had successes throughout their history, contributing their own shares to world science and culture, and that’s something I’ve always tried to appreciate. Things are rarely as black and white as the paper and ink of our textbooks. During the conference, you will take on the role of members of the fictional Soviet Advisory Committee on Centralization and Global Communism, a new semi-secret body intended to advise the Politburo and other major state organs. You will be given unmatched power but also faced with a variety of unique challenges, such as unrest in the satellite states, an economy over-reliant on heavy industry, and a geopolitical sphere of influence being challenged by both the USA and an emerging Communist China. -

Worlds Apart: Bosnian Lessons for Global Security
Worlds Apart Swanee Hunt Worlds Apart Bosnian Lessons for GLoBaL security Duke university Press Durham anD LonDon 2011 © 2011 Duke University Press All rights reserved Printed in the United States of America on acid- free paper ♾ Designed by C. H. Westmoreland Typeset in Charis by Tseng Information Systems, Inc. Library of Congress Cataloging- in- Publication Data appear on the last printed page of this book. To my partners c harLes ansBacher: “Of course you can.” and VaLerie GiLLen: “Of course we can.” and Mirsad JaceVic: “Of course you must.” Contents Author’s Note xi Map of Yugoslavia xii Prologue xiii Acknowledgments xix Context xxi Part i: War Section 1: Officialdom 3 1. insiDe: “Esteemed Mr. Carrington” 3 2. outsiDe: A Convenient Euphemism 4 3. insiDe: Angels and Animals 8 4. outsiDe: Carter and Conscience 10 5. insiDe: “If I Left, Everyone Would Flee” 12 6. outsiDe: None of Our Business 15 7. insiDe: Silajdžić 17 8. outsiDe: Unintended Consequences 18 9. insiDe: The Bread Factory 19 10. outsiDe: Elegant Tables 21 Section 2: Victims or Agents? 24 11. insiDe: The Unspeakable 24 12. outsiDe: The Politics of Rape 26 13. insiDe: An Unlikely Soldier 28 14. outsiDe: Happy Fourth of July 30 15. insiDe: Women on the Side 33 16. outsiDe: Contact Sport 35 Section 3: Deadly Stereotypes 37 17. insiDe: An Artificial War 37 18. outsiDe: Clashes 38 19. insiDe: Crossing the Fault Line 39 20. outsiDe: “The Truth about Goražde” 41 21. insiDe: Loyal 43 22. outsiDe: Pentagon Sympathies 46 23. insiDe: Family Friends 48 24. outsiDe: Extremists 50 Section 4: Fissures and Connections 55 25. -

230 Soviet Defense Policy
#230 SOVIET DEFENSE POLICY: A CONFERENCE REPORT Copyright March 1989 by the Wilson Center The Kennan Institute for Advanced Russian Studies The Woodrow Wilson International Center for Scholars The Kennan Institute for Advanced Russian Studies is a division of the Woodrow Wilson International Center for Scholars. Through its program of fellowships, meetings, and publications, the Institute encourages a wide range of scholarship on Russia and the Soviet Union. The Kennan Institute is supported by contributions from foundations, corporations, individuals, and the United States Government. Kennan Institute Occasional Papers Kennan Institute Occasional Papers are available to all those interested in Russian and Soviet Studies. Occasional Papers are submitted by Kennan Institute scholars and visiting speakers, particularly those who wish to receive timely feedback on their work. Copies of Occasional Papers and a list of papers currently available can be obtained, free of charge, by contacting: Occasional Papers Kennan Institute for Advanced Russian Studies 370 L'Enfant Promenade, SW, Suite 704 Washington, D.C. 20024-2518 (202) 287-3000 The Kennan Institute is a nonpartisan institution committed to the exploration of a broad range of scholarship. It does not necessarily endorse the ideas presented in its Occasional Papers. SOVIET DEFENSE POLICY: A CONFERENCE REPORT ACKNOWLEDGEMENTS On September 21-23, 1987, the Kennan Institute for Advanced Russian Studies and the International Security Studies program of the Woodrow Wilson International Center for Scholars cosponsored a conference on the Dynamics of Soviet Defense Policy. The following report summarizes the proceedings of that conference. This report examines the evolution and context of Soviet defense policy, surveys Soviet military doctrine--including views on theater war in Europe and world war, and on the use of military power in the Third World--and concludes with a discussion of the USSR's nuclear and conventional arms control policies. -

Generate PDF of This Page Notify About This Page
Institute of National Remembrance https://ipn.gov.pl/en/news/4038,Martial-Law-in-Poland-at-the-behest-of-the-Kremlin.html 2021-09-30, 10:53 06.04.2020 Martial Law in Poland at the behest of the Kremlin One of the meetings, crucial for the development of the events of 1981, took place just outside the eastern Polish border. On 3 April in Brest on the Bug River, Stanisław Kania and Wojciech Jaruzelski met with Soviet leaders to discuss the situation. "We are all very concerned about further developments in Poland," said Leonid Brezhnev in early April. The Kremlin dignitaries made it clear to the Polish Party leaders that they expected them to act quickly and decisively against the opposition and "Solidarity". The Kremlin is not glad The spring of 1981 was a period of turbulence for the Polish communists. From 16 March, Poland held military exercises of the Warsaw Pact forces, codenamed "Soyuz 81", and the threat of strikes triggered by "Solidarity" in the wake of the Bydgoszcz provocation had not yet subsided. On 30 March 1981, the authorities concluded a compromise with the "Solidarity" leadership. The trade union dismissed the idea of general strike, and in return was authorised i.a. to legalise the founding committees of rural “Solidarity” and given promises - never kept – that the state would investigate the events that took place on 19 March in Bydgoszcz and draft a law on trade unions. The leadership of the Communist Party of the Soviet Union was not satisfied with such an agreement. The "Polish" topic was raised on 2 April 1981 during the meeting of the Politburo of the Soviet Communist Party. -
Assessment Actions
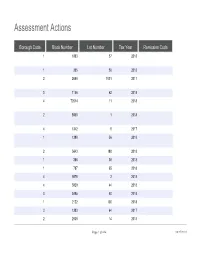
Assessment Actions Borough Code Block Number Lot Number Tax Year Remission Code 1 1883 57 2018 1 385 56 2018 2 2690 1001 2017 3 1156 62 2018 4 72614 11 2018 2 5560 1 2018 4 1342 9 2017 1 1390 56 2018 2 5643 188 2018 1 386 36 2018 1 787 65 2018 4 9578 3 2018 4 3829 44 2018 3 3495 40 2018 1 2122 100 2018 3 1383 64 2017 2 2938 14 2018 Page 1 of 604 09/27/2021 Assessment Actions Owner Name Property Address Granted Reduction Amount Tax Class Code THE TRUSTEES OF 540 WEST 112 STREET 105850 2 COLUM 226-8 EAST 2ND STREET 228 EAST 2 STREET 240500 2 PROSPECT TRIANGLE 890 PROSPECT AVENUE 76750 4 COM CRESPA, LLC 597 PROSPECT PLACE 23500 2 CELLCO PARTNERSHIP 6935500 4 d/ CIMINELLO PROPERTY 775 BRUSH AVENUE 329300 4 AS 4305 65 REALTY LLC 43-05 65 STREET 118900 2 PHOENIX MADISON 962 MADISON AVENUE 584850 4 AVENU CELILY C. SWETT 277 FORDHAM PLACE 3132 1 300 EAST 4TH STREET H 300 EAST 4 STREET 316200 2 242 WEST 38TH STREET 242 WEST 38 STREET 483950 4 124-469 LIBERTY LLC 124-04 LIBERTY AVENUE 70850 4 JOHN GAUDINO 79-27 MYRTLE AVENUE 35100 4 PITKIN BLUE LLC 1575 PITKIN AVENUE 49200 4 GVS PROPERTIES LLC 559 WEST 164 STREET 233748 2 EP78 LLC 1231 LINCOLN PLACE 24500 2 CROTONA PARK 1432 CROTONA PARK EAS 68500 2 Page 2 of 604 09/27/2021 Assessment Actions 1 1231 59 2018 3 7435 38 2018 3 1034 39 2018 3 7947 17 2018 4 370 1 2018 4 397 7 2017 1 389 22 2018 4 3239 1001 2018 3 140 1103 2018 3 1412 50 2017 1 1543 1001 2018 4 659 79 2018 1 822 1301 2018 1 2091 22 2018 3 7949 223 2018 1 471 25 2018 3 1429 17 2018 Page 3 of 604 09/27/2021 Assessment Actions DEVELOPM 268 WEST 84TH STREET 268 WEST 84 STREET 85350 2 BANK OF AMERICA 1415 AVENUE Z 291950 4 4710 REALTY CORP. -

Choosing Butterfly Swords by Jeffrey D
Choosing Butterfly Swords By Jeffrey D. Modell, Esq. and Aaron Cantrell September 6, 2013 Many Chinese martial arts use “Butterfly Swords,” but they are the jewel of the Wing Chun system. Practitioners who reach their level of study are expected to practice intensely, thoughtfully and achieve an understanding that recursively improves their empty hand abilities. Butterfly Swords are a variety of Chinese saber with only one edge sharpened, a blade wider than that of the typical two- edged long sword and a specialized guard. The single edge and wide blade categorize them firmly as “Dao” (“Do” in Cantonese), a term that commonly means knife. Below are a few different words you may want to take note of for the purposes of this article: Hudiedao – Butterfly Swords or Butterfly Knives Baat Jaam Do (& variations on spelling) – Wing Chun Butterfly Swords/Knives (Eight Slash/Cut Swords/Knives) Butterfly swords and especially Baat Jaam Do (“BJD”) are not a one size fits all item. Each style and lineage emphasizes different techniques. The swords must be designed to accommodate and facilitate those movements. Some schools require a weapon based on tradition regardless of whether or not it is appropriate for today’s usage. Individuals develop personal preferences, and each set of swords would ideally be fitted to the specific person’s body. There are a lot of low quality swords on the market. They are not, and do not behave, like the true weapons they seek to imitate. To gain proficiency and understanding of Wing Chun movements, you need BJD that have the weight and feel of the weapons your techniques are designed for. -

Trafficking in Transnistria: the Role of Russia
Trafficking in Transnistria: The Role of Russia by Kent Harrel SIS Honors Capstone Supervised by Professors Linda Lubrano and Elizabeth Anderson Submitted to the School of International Service American University In partial fulfillment of the requirements for graduation with General University Honors Bachelor of Arts Degree May 2009 Abstract After declaring de facto independence from the Republic of Moldova in 1992, the breakaway region of Transnistria became increasingly isolated, and has emerged as a hotspot for weapons and human trafficking. Working from a Realist paradigm, this project assesses the extent to which the Russian government and military abet trafficking in Transnistria, and the way in which Russia uses trafficking as a means to adversely affect Moldova’s designs of broader integration within European spheres. This project proves necessary because the existing scholarship on the topic of Transnistrian trafficking failed to focus on the role of the Russian government and military, and in turn did not account for the ways in which trafficking hinders Moldova’s national interests. The research project utilizes sources such as trafficking policy centers, first-hand accounts, trade agreements, non-governmental organizations, and government documents. A review of the literature employs the use of secondary sources such as scholarly and newspaper articles. In short, this project develops a more comprehensive understanding of Russia’s role in Moldovan affairs and attempts to add a significant work to the existing literature. -

Operating and Capital Improvement Budget July 1, 2018 - Jurte 30, 2019 Fiscal Year 2019
Operating and Capital Improvement Budget July 1, 2018 - Jurte 30, 2019 Fiscal Year 2019 PortAuthority.o rg This page intentionally left blank Board of Directors Officers Jeffrey W. Letwin, Esq., Chairperson of the Board of Directors Jennifer M. Liptak, Vice Chairperson of the Board of Directors Senator Jim Brewster, Secretary of the Board of Directors Directors Representative Dom Costa Robert J. Kania, Jr. Ann Ogoreuc D. Raja John L. Tague, Jr. Stephanie Turman Robert Vescio Michelle Zmijanac 2 | P a g e Chief Executive Officer Katharine Eagan Kelleman Officers and Assistant General Managers Barry Adams, Chief Human Resources Officer Michael Cetra, Chief Legal Officer Jeffrey Devlin, Chief Information Officer David Huffaker, Chief Development Officer William Miller, Chief Operations Officer James Ritchie, Chief Communications Officer Peter Schenk, Chief Financial Officer Heinz 57 Center 345 Sixth Avenue Floor 3 Pittsburgh, PA 15222-2327 (412) 566-5500 www.portauthority.org 3 | P a g e FY 2019 Operating and Capital Table of Contents Improvement Budget Board of Directors ......................................................................................................................................... 2 Officers and Assistant General Managers ..................................................................................................... 3 Regional and Port Authority Profile .............................................................................................................. 6 Allegheny County ..................................................................................................................................... -

Spooneye.Pdf
• • SPOONEYE! First dpcumented as "Thirt y-Fours" in a 1571 British list of injunctions, the modern form of the game developed aboard pirate ships sailing in rhe Caribbean in the late 17th centuty. The game's most nOlOrious enthusiast was none other than the rllthless pirate Spooneye, who had a spoon in the place of a lost hand due to a fo ndness for soups, :iIld who, owing to ext reme myopia in one eye (the right, it is believed), would often cover the bad eye with his spoon-hand in order to focus. During the infamous double mutiny fad of the 1690s, (itself immortalized in the gaIlle, as weI! as numernus ballads,) Spooneye learned of Thirty Fours from the crew fo rmerly belonging to his mortal enemy, the nefarious Danish privateer Weirdbeard. Legend has it that the most powerful card in the game, the Nine, or 'Spooneye', originated when Spooneye was engaged in a �ame with his ship's new cook (name unknown). Fnlstrated at his own poor performance, Spoon eye played a Nine-his favorite card, due to the rcsemulance-and then grabbed one of the cook's cards and placed it on his side of the table. Justifiably angty, the cook argued that rhis was not part of the rules: in rhe origi nal Thirty-fours, Nines grant no special privilege. Spooneye, in response, leaped out of his chair and gouged out the unfortunate cook's left eye with his mighty spoon-hand. Most accounts suggesr thar the cook was keelhauled after the game; some (possibly apoctyphal) accounts suggest that it was this cook who later became the despised buccaneer Disheye. -

Annual Report for the As a Result of the National Financial Environment, Throughout 2009, US Congress Calendar Year 2009, Pursuant to Section 43 of the Banking Law
O R K Y S T W A E T E N 2009 B T A ANNUAL N N E K M REPORT I N T G R D E P A WWW.BANKING.STATE.NY.US 1-877-BANK NYS One State Street Plaza New York, NY 10004 (212) 709-3500 80 South Swan Street Albany, NY 12210 (518) 473-6160 333 East Washington Street Syracuse, NY 13202 (315) 428-4049 September 15, 2010 To the Honorable David A. Paterson and Members of the Legislature: I hereby submit the New York State Banking Department Annual Report for the As a result of the national financial environment, throughout 2009, US Congress calendar year 2009, pursuant to Section 43 of the Banking Law. debated financial regulatory reform legislation. While the regulatory debate developed on the national stage, the Banking Department forged ahead with In 2009, the New York State Banking Department regulated more than 2,700 developing and implementing new state legislation and regulations to address financial entities providing services in New York State, including both depository the immediate crisis and avoid a similar crisis in the future. and non-depository institutions. The total assets of the depository institutions supervised exceeded $2.2 trillion. State Regulation: During 2009, what began as a subprime mortgage crisis led to a global downturn As one of the first states to identify the mortgage crisis, New York was fast in economic activity, leading to decreased employment, decreased borrowing to act on developing solutions. Building on efforts from 2008, in December and spending, and a general contraction in the financial industry as a whole. -

Ilias Bulaid
Ilias Bulaid Ilias Bulaid (born May 1, 1995 in Den Bosch, Netherlands) is a featherweight Ilias Bulaid Moroccan-Dutch kickboxer. Ilias was the 2016 65 kg K-1 World Tournament Runner-Up and is the current Enfusion 67 kg World Champion.[1] Born 1 May 1995 Den Bosch, As of 1 November 2018, he is ranked the #9 featherweight in the world by Netherlands [2] Combat Press. Other The Blade names Titles Nationality Dutch Moroccan 2016 K-1 World GP 2016 -65kg World Tournament Runner-Up[3] 2014 Enfusion World Champion 67 kg[4] (Three defenses; Current) Height 178 cm (5 ft 10 in) Weight 65.0 kg (143.3 lb; Professional kickboxing record 10.24 st) Division Featherweight Style Kickboxing Stance Orthodox Fighting Amsterdam, out of Netherlands Team El Otmani Gym Professional Kickboxing Record Date Result Opponent Event Location Method Round Time KO (Straight 2019- Wei Win Wu Linfeng China Right to the 3 1:11 06-29 Ninghui Body) 2018- Youssef El Decision Win Enfusion Live 70 Belgium 3 3:00 09-15 Haji (Unanimous) 2018- Hassan Wu Linfeng -67KG Loss China Decision (Split) 3 3:00 03-03 Toy Tournament Final Wu Linfeng -67KG 2018- Decision Win Xie Lei Tournament Semi China 3 3:00 03-03 (Unanimous) Finals Kunlun Fight 67 - 2017- 66kg World Sanya, Decision Win 3 3:00 11-12 Petchtanong Championship, China (Unanimous) Banchamek Quarter Finals Despite winning fight, had to withdraw from tournament due to injury. Kunlun Fight 65 - 2017- Jordan Kunlun Fight 16 Qingdao, KO (Left Body Win 1 2:25 08-27 Kranio Man Tournament China Hook) 67 kg- Final 16 KO (Spinning 2017- Manaowan Hoofddorp, Win Fight League 6 Back Kick to The 1 1:30 05-13 Netherlands Sitsongpeenong Body) 2017- Zakaria Eindhoven, Win Enfusion Live 46 Decision 5 3:00 02-18 Zouggary[5] Netherlands Defends the Enfusion -67 kg Championship. -

Types of Chinese Swords There Are Generally Five Types of Swords in Chinese History, They Are Jian, Zhanmadao, Liuyedao, Wodao and Yanmaodao
Types of Chinese Swords There are generally five types of swords in Chinese history, they are Jian, Zhanmadao, Liuyedao, Wodao and Yanmaodao. The jian is a double-edged straight sword used during the last 2,500 years in China. The first Chinese sources that mention the jian date to the 7th century BC during the Spring and Autumn Period;one of the earliest specimens being the Sword of Goujian. Historical one-handed versions have blades varying from 45 to 80 cm (17.7 to 31.5 inches) in length. The weight of an average sword of 70- centimeter (28-inch) blade-length would be in a range of approximately 700 to 900 grams (1.5 to 2 pounds). There are also larger two-handed versions used for training by many styles of Chinese martial arts. The zhanmadao is a saber with a single long broad blade, and a long handle suitable for two-handed use. Dating to 1072, it was used as an anti-cavalry weapon. This is mentioned in the "Wu Jing Zong Yao Song Military Manual" from 1072. Surviving examples include a sword that might resemble a nagamaki in construction; it had a wrapped handle 37 cm long making it easy to grip with two hands. The blade was 114 centimetres long and very straight with a slight curve in the last half. The liuye dao, or "willow leaf saber", is a type of Dao that was commonly used as a military sidearm for both cavalry and infantry during the Ming and Qing dynasties. This weapon features a moderate curve along the length of the blade.