Perfidy in Non-International Armed Conflicts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

“Dangerous Vagabonds”: Resistance to Slave
“DANGEROUS VAGABONDS”: RESISTANCE TO SLAVE EMANCIPATION AND THE COLONY OF SENEGAL by Robin Aspasia Hardy A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in History MONTANA STATE UNIVERSITY Bozeman, Montana April 2016 ©COPYRIGHT by Robin Aspasia Hardy 2016 All Rights Reserved ii DEDICATION PAGE For my dear parents. iii TABLE OF CONTENTS 1. INTRODUCTION .................................................................................................... 1 Historiography and Methodology .............................................................................. 4 Sources ..................................................................................................................... 18 Chapter Overview .................................................................................................... 20 2. SENEGAL ON THE FRINGE OF EMPIRE.......................................................... 23 Senegal, Early French Presence, and Slavery ......................................................... 24 The Role of Slavery in the French Conquest of Senegal’s Interior ......................... 39 Conclusion ............................................................................................................... 51 3. RACE, RESISTANCE, AND PUISSANCE ........................................................... 54 Sex, Trade and Race in Senegal ............................................................................... 55 Slave Emancipation and the Perpetuation of a Mixed-Race -

The Relationship Between International Humanitarian Law and the International Criminal Tribunals Hortensia D
Volume 88 Number 861 March 2006 The relationship between international humanitarian law and the international criminal tribunals Hortensia D. T. Gutierrez Posse Hortensia D. T. Gutierrez Posse is Professor of Public International Law, University of Buenos Aires Abstract International humanitarian law is the branch of customary and treaty-based international positive law whose purposes are to limit the methods and means of warfare and to protect the victims of armed conflicts. Grave breaches of its rules constitute war crimes for which individuals may be held directly accountable and which it is up to sovereign states to prosecute. However, should a state not wish to, or not be in a position to, prosecute, the crimes can be tried by international criminal tribunals instituted by treaty or by binding decision of the United Nations Security Council. This brief description of the current legal and political situation reflects the state of the law at the dawn of the twenty-first century. It does not, however, describe the work of a single day or the fruit of a single endeavour. Quite the contrary, it is the outcome of the international community’s growing awareness, in the face of the horrors of war and the indescribable suffering inflicted on humanity throughout the ages, that there must be limits to violence and that those limits must be established by the law and those responsible punished so as to discourage future perpetrators from exceeding them. Short historical overview International humanitarian law has played a decisive role in this development, as both the laws and customs of war and the rules for the protection of victims fall 65 H. -

The Starvation Myth: the U.S. Blockade of Japan in World War Ii Christopher Clary
DOUGlAS L. BENDELL AWARD THE STARVATION MYTH: THE U.S. BLOCKADE OF JAPAN IN WORLD WAR II CHRISTOPHER CLARY At 8:16 a.m., on August 6, 1945, the world changed. Fifty-seconds earlier, the Enola Gay had dropped an atomic bomb, "Little Boy", from 31,600 feet above Hiroshima, Japan. The world was ushered into the nuclear age. After seeing the "initial burst and 'ball of fire,'" co-pilot Robert Lewis questioned aloud, "My God, what have we done?" 1 Lewis, nearly six miles above the devastation, was responding to the pyrotechnic display. He could only imagine the very real damage the bomb had caused. While disagreements exist concerning the exact figures, it is undeniable that the bomb and its radioactive effects killed at least 70,000 people 2 Though he was one of the first to see its effects, Lewis was not the first to question the decision to use the atomic bomb nor would he be the last. The decision still sits at the center of one of the most debated historical (as well as historiographic) questions. The focus on this episode is justified. This singular event divides the Twentieth Century in numerous ways, but perhaps most relevantly it ends a hot and bloody war, and marks the beginning of a colder conflict. And since we examine the event in the year 2000, we must try to avoid the biases of the post-Cold War era. This paper tries to focus on two different realities: the first is what actually, really happened, the true state of affairs, then secondly the perceptions of that actuality. -

Taming the Trolls: the Need for an International Legal Framework to Regulate State Use of Disinformation on Social Media
Taming the Trolls: The Need for an International Legal Framework to Regulate State Use of Disinformation on Social Media * ASHLEY C. NICOLAS INTRODUCTION Consider a hypothetical scenario in which hundreds of agents of the Russian GRU arrive in the United States months prior to a presidential election.1 The Russian agents spend the weeks leading up to the election going door to door in vulnerable communities, spreading false stories intended to manipulate the population into electing a candidate with policies favorable to Russian positions. The agents set up television stations, use radio broadcasts, and usurp the resources of local newspapers to expand their reach and propagate falsehoods. The presence of GRU agents on U.S. soil is an incursion into territorial integrity⎯a clear invasion of sovereignty.2 At every step, Russia would be required to expend tremendous resources, overcome traditional media barriers, and risk exposure, making this hypothetical grossly unrealistic. Compare the hypothetical with the actual actions of the Russians during the 2016 U.S. presidential election. Sitting behind computers in St. Petersburg, without ever setting foot in the United States, Russian agents were able to manipulate the U.S. population in the most sacred of domestic affairs⎯an election. Russian “trolls” targeted vulnerable populations through social media, reaching millions of users at a minimal cost and without reliance on established media institutions.3 Without using * Georgetown Law, J.D. expected 2019; United States Military Academy, B.S. 2009; Loyola Marymount University M.Ed. 2016. © 2018, Ashley C. Nicolas. The author is a former U.S. Army Intelligence Officer. -

Applying Traditional Military Principles to Cyber Warfare
2012 4th International Conference on Cyber Confl ict Permission to make digital or hard copies of this publication for internal use within NATO and for personal or educational use when for non-profi t or non-commercial C. Czosseck, R. Ottis, K. Ziolkowski (Eds.) purposes is granted providing that copies bear this notice and a full citation on the 2012 © NATO CCD COE Publications, Tallinn first page. Any other reproduction or transmission requires prior written permission by NATO CCD COE. Applying Traditional Military Principles to Cyber Warfare Samuel Liles Marcus Rogers Cyber Integration and Information Computer and Information Operations Department Technology Department National Defense University iCollege Purdue University Washington, DC West Lafayette, IN [email protected] [email protected] J. Eric Dietz Dean Larson Purdue Homeland Security Institute Larson Performance Engineering Purdue University Munster, IN West Lafayette, IN [email protected] [email protected] Abstract: Utilizing a variety of resources, the conventions of land warfare will be analyzed for their cyber impact by using the principles designated by the United States Army. The analysis will discuss in detail the factors impacting security of the network enterprise for command and control, the information conduits found in the technological enterprise, and the effects upon the adversary and combatant commander. Keywords: cyber warfare, military principles, combatant controls, mechanisms, strategy 1. INTRODUCTION Adams informs us that rapid changes due to technology have increasingly effected the affairs of the military. This effect whether economic, political, or otherwise has sometimes been extreme. Technology has also made substantial impacts on the prosecution of war. Adams also informs us that information technology is one of the primary change agents in the military of today and likely of the future [1]. -

Combatant Status and Computer Network Attack
Combatant Status and Computer Network Attack * SEAN WATTS Introduction .......................................................................................... 392 I. State Capacity for Computer Network Attacks ......................... 397 A. Anatomy of a Computer Network Attack ....................... 399 1. CNA Intelligence Operations ............................... 399 2. CNA Acquisition and Weapon Design ................. 401 3. CNA Execution .................................................... 403 B. State Computer Network Attack Capabilites and Staffing ............................................................................ 405 C. United States’ Government Organization for Computer Network Attack .............................................. 407 II. The Geneva Tradition and Combatant Immunity ...................... 411 A. The “Current” Legal Framework..................................... 412 1. Civilian Status ...................................................... 414 2. Combatant Status .................................................. 415 3. Legal Implications of Status ................................. 420 B. Existing Legal Assessments and Scholarship.................. 424 C. Implications for Existing Computer Network Attack Organization .................................................................... 427 III. Departing from the Geneva Combatant Status Regime ............ 430 A. Interpretive Considerations ............................................. 431 * Assistant Professor, Creighton University Law School; Professor, -

JP 3-13.4, Military Deception
Joint Publication 3-13.4 Military Deception 26 January 2012 EXECUTIVE SUMMARY COMMANDER’S OVERVIEW • Provides an Overview of Military Deception (MILDEC) and the Goals, Objectives, Functions, and Principles • Describes the Relationship between MILDEC and Information Operations • Explains MILDEC Planning Methodology and Planning Steps • Discusses Execution of MILDEC Operations Military Deception and Its Goals, Objectives, Functions, and Principles Military deception Specific guidance from the joint force commander (JFC) or (MILDEC) is actions higher authority during planning will determine the military executed to deliberately deception (MILDEC) role in a joint operation. MILDEC mislead adversary is intended to deter hostile actions, increase the success military, paramilitary, or of friendly defensive actions, or to improve the success violent extremist of any potential friendly offensive action. Use of organization decision MILDEC during any phase of an operation should help to makers, thereby causing mislead adversaries as to the strength, readiness, locations, the adversary to take and intended missions of friendly forces. In combat specific actions (or situations, the focus is on driving the adversary to inactions) that will culmination and achieving the objectives defined by the contribute to the JFC. In noncombat situations, the JFC seeks to dominate accomplishment of the the situation with decisive operations designed to establish friendly mission. conditions for an early, favorable conclusion. MILDEC and Information Care should be taken to protect the quality of information Quality available for friendly decisions and public dissemination. This will help ensure the JFC has accurate information by not allowing staffs to unknowingly perceive the joint task force’s MILDEC efforts as accurate information. -
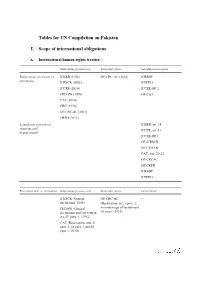
Tables for UN Compilation on Pakistan I. Scope of International
Tables for UN Compilation on Pakistan I. Scope of international obligations1 A. International human rights treaties2 Status during previous cycle Action after review Not ratified/not accepted Ratification, accession or ICERD (1966) OP -CRC-AC (2016) ICRMW succession ICESCR (2008) ICPPED ICCPR (2010) ICCPR-OP 2 CEDAW (1996) OP-CAT CAT (2010) CRC (1990) OP-CRC-SC (2011) CRPD (2011) Complaints procedures, – – ICERD, art. 14 inquiries and ICCPR, art. 41 urgent action3 ICCPR-OP 1 OP-ICESCR OP-CEDAW CAT, arts. 20-22 OP-CRC-IC OP-CRPD ICRMW ICPPED Reservations and / or declarations Status during previous cycle Action after review Current Status ICESCR (General OP -CRC-AC – declaration, 2008) (Declaration, art. 3 para. 2, CEDAW (General minimum age of recruitment declaration and reservation 16 years, (2016) art. 29, para. 1, 1996) CAT (Reservation, arts. 8 para. 2, 28 para. 1 and 30 para. 1. 2010) ICCPR (General reservation, 2008) B. Other main relevant international instruments Status during previous cycle Action after review Not ratified Ratification, accession or Convention on the – Rome Statute of the succession Prevention and Punishment International Criminal Court of the Crime of Genocide Geneva Conventions of 12 Palermo Protocol5 August 19494 Additional Protocols I, II and III to the 1949 Geneva Conventions6 ILO fundamental – Conventions on refugees conventions7 and stateless persons8 – – Convention against Discrimination in Education – – ILO Conventions Nos. 169 and 1899 II. Cooperation with human rights mechanisms and bodies A. Cooperation -

Noncombatant Immunity and War-Profiteering
In Oxford Handbook of Ethics of War / Published 2017 / doi:10.1093/oxfordhb/9780199943418.001.0001 Noncombatant Immunity and War-Profiteering Saba Bazargan Department of Philosophy UC San Diego Abstract The principle of noncombatant immunity prohibits warring parties from intentionally targeting noncombatants. I explicate the moral version of this view and its criticisms by reductive individualists; they argue that certain civilians on the unjust side are morally liable to be lethally targeted to forestall substantial contributions to that war. I then argue that reductivists are mistaken in thinking that causally contributing to an unjust war is a necessary condition for moral liability. Certain noncontributing civilians—notably, war-profiteers— can be morally liable to be lethally targeted. Thus, the principle of noncombatant immunity is mistaken as a moral (though not necessarily as a legal) doctrine, not just because some civilians contribute substantially, but because some unjustly enriched civilians culpably fail to discharge their restitutionary duties to those whose victimization made the unjust enrichment possible. Consequently, the moral criterion for lethal liability in war is even broader than reductive individualists have argued. 1 In Oxford Handbook of Ethics of War / Published 2017 / doi:10.1093/oxfordhb/9780199943418.001.0001 1. Background 1.1. Noncombatant Immunity and the Combatant’s Privilege in International Law In Article 155 of what came to be known as the ‘Lieber Code’, written in 1866, Francis Lieber wrote ‘[a]ll enemies in regular war are divided into two general classes—that is to say, into combatants and noncombatants’. As a legal matter, this distinction does not map perfectly onto the distinction between members and nonmembers of an armed force. -

The End Game Is on in Afghanistan
CIDOB • Barcelona Centre for International for Affairs Centre CIDOB • Barcelona E-ISSN 2014-0843 D.L.: B-8438-2012 opiniónASIA THE END GAME IS ON IN 198 AFGHANISTAN JUNE 2013 Gabriel Reyes & Emma Hooper, Associated Fellows, CIDOB he opening of the Taliban office in Qatar was hailed by many optimis- tic observers – including a number of American officials - as a turning point in the process of finding a negotiated solution to the conflict in TAfghanistan. As much as it deserves credit as yet another attempt to kick start once again a long-needed dialogue, like many other past developments in Afghanistan which have appeared optimistic but which then were short-lived, the event should be taken with a great deal of caution. None the less, one should not lose faith in the possibility of a negotiated end to the conflict, for the moment at least. For many, especially the international community, the week of 17 June 2013 was meant to represent the beginning of the long awaited squaring of the circle of a successful transition to a new Afghanistan in the right track towards stability ahead of 2014. With the official transfer of all security responsibilities to the Afghan National Security Forces across the country officially announced on 18 June 2013 and the planned signing of the Bilateral Security Agreement between the US and the Afghan Government later in the week, by mid week, things were looking good. But, hours later, what could have been the unexpected (for some) icing on the cake of a momentous week – the opening of a Taliban office in Doha as a privileged hub for talks - plunged Afghanistan once again into an- other political crisis. -

Fm 6-27 Mctp 11-10C the Commander's Handbook on the Law of Land Warfare
FM 6-27 MCTP 11-10C THE COMMANDER'S HANDBOOK ON THE LAW OF LAND WARFARE AUGUST 2019 DISTRIBUTION RESTRICTION: Approved for public release; distribution is unlimited. This publication supersedes FM 27-10/MCTP 11-10C, dated 18 July 1956. HEADQUARTERS, DEPARTMENT OF THE ARMY HEADQUARTERS, UNITED STATES MARINE CORPS Foreword The lessons of protracted conflict confirm that adherence to the law of armed conflict (LOAC) by the land forces, both in intern ational and non-international armed conflict, must serve as the standard that we train to and apply across the entire range of military operations. Adhering to LOAC enhances the legitimacy of our operations and supports the moral framework of our armed forces. We have learned th at we deviate from these norms to our detriment and risk undercutting both domesti c and international support for our operations. LOAC has been and remains a vital guide for all military operations conducted by the U.S. Governm ent. This fi eld manual provides a general description of the law of land warfare for Soldiers and Marines, delineated as statements of doctrine and practice, to gui de the land forces in conducting di sci plined military operations in accordance with the rule of law. The Department of Defense Law of War Manual (June 20 15, updated December 2016) is the authoritative statement on the law of war for the Department of Defense. In the event of a conflict or discrepancy regarding the legal standards addressed in this publication and th e DOD Law of War Manual, the latter takes precedence. -

The History of Florida's State Flag the History of Florida's State Flag Robert M
Nova Law Review Volume 18, Issue 2 1994 Article 11 The History of Florida’s State Flag Robert M. Jarvis∗ ∗ Copyright c 1994 by the authors. Nova Law Review is produced by The Berkeley Electronic Press (bepress). https://nsuworks.nova.edu/nlr Jarvis: The History of Florida's State Flag The History of Florida's State Flag Robert M. Jarvis* TABLE OF CONTENTS I. INTRODUCTION ........ .................. 1037 II. EUROPEAN DISCOVERY AND CONQUEST ........... 1038 III. AMERICAN ACQUISITION AND STATEHOOD ......... 1045 IV. THE CIVIL WAR .......................... 1051 V. RECONSTRUCTION AND THE END OF THE NINETEENTH CENTURY ..................... 1056 VI. THE TWENTIETH CENTURY ................... 1059 VII. CONCLUSION ............................ 1063 I. INTRODUCTION The Florida Constitution requires the state to have an official flag, and places responsibility for its design on the State Legislature.' Prior to 1900, a number of different flags served as the state's banner. Since 1900, however, the flag has consisted of a white field,2 a red saltire,3 and the * Professor of Law, Nova University. B.A., Northwestern University; J.D., University of Pennsylvania; LL.M., New York University. 1. "The design of the great seal and flag of the state shall be prescribed by law." FLA. CONST. art. If, § 4. Although the constitution mentions only a seal and a flag, the Florida Legislature has designated many other state symbols, including: a state flower (the orange blossom - adopted in 1909); bird (mockingbird - 1927); song ("Old Folks Home" - 1935); tree (sabal palm - 1.953); beverage (orange juice - 1967); shell (horse conch - 1969); gem (moonstone - 1970); marine mammal (manatee - 1975); saltwater mammal (dolphin - 1975); freshwater fish (largemouth bass - 1975); saltwater fish (Atlantic sailfish - 1975); stone (agatized coral - 1979); reptile (alligator - 1987); animal (panther - 1982); soil (Mayakka Fine Sand - 1989); and wildflower (coreopsis - 1991).