How Do Developers Use Wake Locks in Android Applications? a Large-Scale Empirical Study
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Top 10 Open Source Music Players Scores of Music Players Are Available in the Open Source World, and Each One Has Something That Is Unique
For U & Me Overview The Top 10 Open Source Music Players Scores of music players are available in the open source world, and each one has something that is unique. Here are the top 10 music players for you to check out. verybody likes to use a music player that is hassle- Amarok free and easy to operate, besides having plenty of Amarok is a part of the KDE project and is the default music Efeatures to enhance the music experience. The open player in Kubuntu. Mark Kretschmann started this project. source community has developed many music players. This The Amarok experience can be enhanced with custom scripts article lists the features of the ten best open source music or by using scripts contributed by other developers. players, which will help you to select the player most Its first release was on June 23, 2003. Amarok has been suited to your musical tastes. The article also helps those developed in C++ using Qt (the toolkit for cross-platform who wish to explore the features and capabilities of open application development). Its tagline, ‘Rediscover your source music players. Music’, is indeed true, considering its long list of features. 98 | FEBRUARY 2014 | OPEN SOURCE FOR YoU | www.LinuxForU.com Overview For U & Me Table 1: Features at a glance iPod sync Track info Smart/ Name/ Fade/ gapless and USB Radio and Remotely Last.fm Playback and lyrics dynamic Feature playback device podcasts controlled integration resume lookup playlist support Amarok Crossfade Both Yes Both Yes Both Yes Yes (Xine), Gapless (Gstreamer) aTunes Fade only -

Beets Documentation Release 1.5.1
beets Documentation Release 1.5.1 Adrian Sampson Oct 01, 2021 Contents 1 Contents 3 1.1 Guides..................................................3 1.2 Reference................................................. 14 1.3 Plugins.................................................. 44 1.4 FAQ.................................................... 120 1.5 Contributing............................................... 125 1.6 For Developers.............................................. 130 1.7 Changelog................................................ 145 Index 213 i ii beets Documentation, Release 1.5.1 Welcome to the documentation for beets, the media library management system for obsessive music geeks. If you’re new to beets, begin with the Getting Started guide. That guide walks you through installing beets, setting it up how you like it, and starting to build your music library. Then you can get a more detailed look at beets’ features in the Command-Line Interface and Configuration references. You might also be interested in exploring the plugins. If you still need help, your can drop by the #beets IRC channel on Libera.Chat, drop by the discussion board, send email to the mailing list, or file a bug in the issue tracker. Please let us know where you think this documentation can be improved. Contents 1 beets Documentation, Release 1.5.1 2 Contents CHAPTER 1 Contents 1.1 Guides This section contains a couple of walkthroughs that will help you get familiar with beets. If you’re new to beets, you’ll want to begin with the Getting Started guide. 1.1.1 Getting Started Welcome to beets! This guide will help you begin using it to make your music collection better. Installing You will need Python. Beets works on Python 3.6 or later. • macOS 11 (Big Sur) includes Python 3.8 out of the box. -

Music Machinery
30/10/2015 Music APIs | Music Machinery Music Machinery Music APIs Here’s a categorized list of all the Music APIs. Notice one that is missing or miscategorized? Let me know. (http://musicmachinery.files.wordpress.com/2013/10/music-api-logos.png) Music Metadata ArtistLink (http://developer.artistlink.com/) Decibel (http://decibel.net/) Discogs (https://www.discogs.com/developers/) FreeDB (http://www.freedb.org/) http://musicmachinery.com/music-apis/ 1/7 30/10/2015 Music APIs | Music Machinery Gracenote (https://developer.gracenote.com/web-api) Last.fm (http://www.last.fm/api) MusicBrainz (http://musicbrainz.org/doc/Development/XML_Web_Service/Version_2) MusicStory (http://developers.music-story.com/) Nokia (http://api.ent.nokia.com/) OneMusicAPI (http://www.onemusicapi.com/) OpenAura (http://developer.openaura.com/) Rockol (https://rockol.3scale.net/) Rovi (http://developer.rovicorp.com/) Clipped to Inbox Spotify (http://developer.spotify.com) The Echo NMesut s(ihc tAtpP:I/s/developer.echonest.com) Discovery / Playlisting 8tracks (http://8tracks.com/developers) Bandcamp (http://bandcamp.com/developer) The Hype machine (http://hypem.com/) Last.fm (http://last.fm/) Playlists.net (http://playlists.net/api/documentation) plug.dj (http://blog.plug.dj/api-documentation/) Rovi (http://developer.rovicorp.com/) Setlist.fm (http://api.setlist.fm/docs/index.html) Shuffler.fm (http://developers.shuffler.fm/) Spotify (http://developer.spotify.com) StereoMood (http://www.stereomood.com/api/documentation/) Tastekid (http://www.tastekid.com/page/api) -

Unpacking Thank You for Buying the MSI® X299 TOMAHAWK/ X299 TOMAHAWK AC Motherboard
Unpacking Thank you for buying the MSI® X299 TOMAHAWK/ X299 TOMAHAWK AC motherboard. Check to make sure your motherboard box contains the following items. If something is missing, contact your dealer as soon as possible. Drivers & Utilities Disc Motherboard User Guide Motherboard I/O Shield SLI HB Bridge M x1 SATA Cable x2 Case Badge SATA Cable Labels Antenna x2 (Optional) * These pictures are for reference only and may vary without notice. ** The packing contents may vary according to the country you purchased. Unpacking 1 Safety Information y The components included in this package are prone to damage from electrostatic discharge (ESD). Please adhere to the following instructions to ensure successful computer assembly. y Ensure that all components are securely connected. Loose connections may cause the computer to not recognize a component or fail to start. y Hold the motherboard by the edges to avoid touching sensitive components. y It is recommended to wear an electrostatic discharge (ESD) wrist strap when handling the motherboard to prevent electrostatic damage. If an ESD wrist strap is not available, discharge yourself of static electricity by touching another metal object before handling the motherboard. y Store the motherboard in an electrostatic shielding container or on an anti-static pad whenever the motherboard is not installed. y Before turning on the computer, ensure that there are no loose screws or metal components on the motherboard or anywhere within the computer case. y Do not boot the computer before installation is completed. This could cause permanent damage to the components as well as injury to the user. -

Owncloud User Manual Release 5.0
ownCloud User Manual Release 5.0 The ownCloud developers October 08, 2013 CONTENTS 1 User Documentation 1 1.1 Webinterface...............................................1 1.2 Files & Synchronization.........................................1 1.3 Contacts & Calendar...........................................2 1.4 Bookmarks................................................2 1.5 Mediaplayer...............................................2 1.6 Backup..................................................2 1.7 Indices and tables............................................2 2 The ownCloud Web Interface3 2.1 Overview.................................................3 3 Files & Synchronization 5 3.1 Accessing your Files (WebDav).....................................5 3.2 Version Control.............................................. 12 3.3 Deleted Files............................................... 13 3.4 Desktop Synchronisation......................................... 13 3.5 Files Encryption............................................. 13 4 Contacts & Calendar 15 4.1 Using the Contacts App......................................... 15 4.2 Using the Calendar App......................................... 20 4.3 iOS - Synchronize iPhone/iPad..................................... 22 4.4 Synchronizing with OS X........................................ 24 4.5 Thunderbird - Synchronize Address Book................................ 24 4.6 Synchronizing with KDE SC....................................... 26 4.7 Troubleshooting............................................ -

MUSIC and WEARABLE TECHNOLOGY Major Qualifying Project
MUSIC AND WEARABLE TECHNOLOGY Major Qualifying Project Advisor: William R Michalson Written By: Matthew Barreiro Erin Ferguson Liam Perry A Major Qualifying Project WORCESTER POLYTECHNIC INSTITUTE Submitted to the Faculty of Worcester Polytechnic Institute In partial fulfillment of the requirements for the Degree in Bachelor of Science in Electrical and Computer Engineering August 2016- March 2017 1 Table of Contents 1.Introduction ............................................................................................................................................... 4 2.Background ................................................................................................................................................ 5 2.1Music and Psychology .......................................................................................................................... 5 2.2 Physiological Relationships .............................................................................................................. 5 2.3 Music and Physiology ...................................................................................................................... 11 2.4 Prior Art ....................................................................................................................................... 12 2.5 Market Research ......................................................................................................................... 13 2.6 Technical Research ..................................................................................................................... -
Performance, Security, and Safety Requirements Testing for Smart Systems Through Systematic Software Analysis
Performance, Security, and Safety Requirements Testing for Smart Systems Through Systematic Software Analysis by Ke Hong A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Science and Engineering) in the University of Michigan 2019 Doctoral Committee: Professor Z. Morley Mao, Chair Assistant Professor Qi Alfred Chen, University of California Irvine Professor Scott Mahlke Assistant Professor Florian Schaub Ke Hong [email protected] ORCID iD: 0000-0002-8830-373X c Ke Hong 2019 To Xiaqing and my parents. ii ACKNOWLEDGEMENTS The past five years would be much harder without the guidance from my advisor Pro- fessor Zhuoqing Morley Mao, the assistance from my collaborators and colleagues and the support from my family and friends. Foremost, I would like to express my deepest gratitude to my advisor, Professor Zhuo- qing Morley Mao for her continuous kind support and patient guidance on my research. Her constant support was a definite factor in bringing this dissertation to its completion. I still remember she tried different ways to teach me in details how to define meaningful research problems, effectively communicate my ideas in research discussions and conduct impactful research in my early PhD years. Whenever I got lost or stuck in my research, she would always try her best to gear me to the right track and point me to the right direction. Her candid and insightful feedback has been helping me overcome my weaknesses in the research. With her constant guidance and support over these years, I have grown to be a researcher that can independently conduct research. -

Top 5 Best Itunes Alternatives for Playing Music on Mac Posted by Nick Orin on June 28, 2017 01:34:12 PM
Top 5 Best iTunes Alternatives for Playing Music on Mac Posted by Nick Orin on June 28, 2017 01:34:12 PM. iTunes is the largest music store in the world since February 2010, you can find almost any music you want. In addition, it is also a great music player. However, it has a big disadvantage that it is a very complex bloated software. It may take up lots of the memory on the computer whenever you start it, causing your computer runs slow or freezes. As a result, some people don't like to open iTunes to listen to music only. In this article, I will review the top 5 best iTunes alternatives for playing music on Mac, you can follow me to find the one you like most. Top 1. Ecoute - Simple Music Player with Clean Interface It is known as a simple music player for Mac with clean and elegant interface. With it, you can access iTunes library without starting iTunes on your computer and the iTunes library can be detected automatically and sorted by artist, album etc. Besides, it integrates Twitter, Facebook and Last.fm, you can share your music to others quickly. Finally, it enhances your playing experience with the features for playing music such as 'play next', 'shuffle by albums' etc. Pros: 1. It is a lightweight program, takes very little space; 2. Create indexes for music files quickly; 3. User friendly interface. Cons: 1. Doesn't show long track names; 2. Doesn't work for embedded covers; 3. Only supports 15 days free trial. -

Owncloud 3, Il Cloud Sotto Il Tuo Controllo
OwnCloud 3, il cloud sotto il tuo controllo E’ stato rilasciato pochi giorni fa OwnCloud 3, la nuova versione di un’applicazione web che trovo fondamentale per poter tornare ad avere il pieno controllo delle proprie applicazioni e dei propri dati. Se avete fretta e siete curiosi: potete andare direttamente a provare la demo online. Perché OwnCloud è importante Già qualche tempo fa parlavo di come sia auspicabile che l’utente torni a controllare ciò che è suo, senza dover cedere il proprio “io digitale” agli sconosciuti (leggi Google o Facebook). La recente chiusura di Megaupload (legittima, a mio parere) con conseguente (illegittima, a mio parere) perdita di tutti i dati di chi pagava il servizio, rendono evidente quanto questa esigenza sia importante ed urgente. Su questo fronte OwnCloud ha imboccato la strada giusta. Mette insieme le applicazioni essenziali per chiunque, con un’attenzione particolare per l’usabilità e la gradevolezza estetica, aspetti troppo spesso sottovalutati nel mondo dei nerd opensource. Cosa offre OwnCloud è un’applicazione web che mette insieme: • Un gestore di file. • Un lettore musicale. • Una galleria di foto • Un lettore PDF • Un editor di testi • Un calendario. • Una rubrica. Ogni file può essere tenuto privato, condiviso tra un gruppo di utenti o reso pubblico. Alcune sue funzioni, sfruttando protocolli standard, possono essere utilizzate anche da applicazioni esterne: • Si può accedere ai file dal proprio gestore risorse. • Si può accedere alle canzoni dal proprio lettore musicale. • Si può accedere alla rubrica dal proprio programma di posta • Si può sincronizzare il calendario con i gestori di promemoria. Inoltre OwnCloud è modulare: chiunque ne abbia le capacità, può aggiungerci altre applicazioni per aggiungere nuove funzioni. -
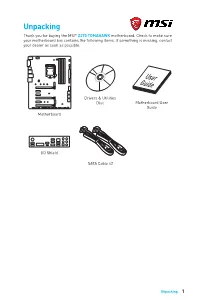
Z270-Tomahawk-User-Guide.Pdf
Unpacking Thank you for buying the MSI® Z270 TOMAHAWK motherboard. Check to make sure your motherboard box contains the following items. If something is missing, contact your dealer as soon as possible. Drivers & Utilities Disc Motherboard User Guide Motherboard I/O Shield SATA Cable x2 Unpacking 1 Safety Information y The components included in this package are prone to damage from electrostatic discharge (ESD). Please adhere to the following instructions to ensure successful computer assembly. y Ensure that all components are securely connected. Loose connections may cause the computer to not recognize a component or fail to start. y Hold the motherboard by the edges to avoid touching sensitive components. y It is recommended to wear an electrostatic discharge (ESD) wrist strap when handling the motherboard to prevent electrostatic damage. If an ESD wrist strap is not available, discharge yourself of static electricity by touching another metal object before handling the motherboard. y Store the motherboard in an electrostatic shielding container or on an anti-static pad whenever the motherboard is not installed. y Before turning on the computer, ensure that there are no loose screws or metal components on the motherboard or anywhere within the computer case. y Do not boot the computer before installation is completed. This could cause permanent damage to the components as well as injury to the user. y If you need help during any installation step, please consult a certified computer technician. y Always turn off the power supply and unplug the power cord from the power outlet before installing or removing any computer component. -

Apple Music Exclusive We Speak to the People Behind the Biggest Digital Launch of the Year 2
thereport ISSUE 368 | 10 JUNE 2015 Apple Music exclusive we speak to the people behind the biggest digital launch of the year 2 ISSUE 368 COVER FEATURE 10.06.15 THE NEW AGE OF RADIO? The first thing Taking the lid to understand is that this is much more interesting than just “Apple off Apple Music versus Spotify” or “streaming versus sales”. This is about Apple and Spotify versus radio. A concerted effort by the two key players in the digital music space – and others, too – to secure a shift in media consumption from the kind of mainstream listeners for whom music discovery has generally meant turning a dial. There are certainly differences in approach. Apple Music’s main curveball at this week’s WWDC reveal was Beats 1, a round-the-clock live radio station staffed by Zane Lowe, Ebro Darden, Julie Adenuga (pictured on next page), with other DJs yet to be confirmed. It’s a worldwide, all-genres station where, in the words of Apple’s announcement, “listeners around the globe will hear the same great programming at the same time”. This Apple was rumoured for years to be transitioning into streaming. Last May it paid $3bn to is something music:)ally hears will not be buy Beats, including the just-launched Beats Music, and then… nothing. Speculation went supported by on-demand access to shows after they air. into overdrive about what it would do, if it would kill Spotify and then talk of delayed From that announcement: “Apple has launches suggested Apple was having a nightmare of the soul. -
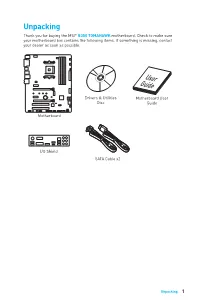
5571013-5438-User-Manual.Pdf
Unpacking Thank you for buying the MSI® B350 TOMAHAWK motherboard. Check to make sure your motherboard box contains the following items. If something is missing, contact your dealer as soon as possible. Drivers & Utilities Motherboard User Disc Guide Motherboard I/O Shield SATA Cable x2 Unpacking 1 Safety Information y The components included in this package are prone to damage from electrostatic discharge (ESD). Please adhere to the following instructions to ensure successful computer assembly. y Ensure that all components are securely connected. Loose connections may cause the computer to not recognize a component or fail to start. y Hold the motherboard by the edges to avoid touching sensitive components. y It is recommended to wear an electrostatic discharge (ESD) wrist strap when handling the motherboard to prevent electrostatic damage. If an ESD wrist strap is not available, discharge yourself of static electricity by touching another metal object before handling the motherboard. y Store the motherboard in an electrostatic shielding container or on an anti-static pad whenever the motherboard is not installed. y Before turning on the computer, ensure that there are no loose screws or metal components on the motherboard or anywhere within the computer case. y Do not boot the computer before installation is completed. This could cause permanent damage to the components as well as injury to the user. y If you need help during any installation step, please consult a certified computer technician. y Always turn off the power supply and unplug the power cord from the power outlet before installing or removing any computer component.