Model Learning and Model Checking of SSH Implementations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CEH: Certified Ethical Hacker Course Content
CEH: Certified Ethical Hacker Course ID #: 1275-100-ZZ-W Hours: 35 Course Content Course Description: The Certified Ethical Hacker (CEH) program is the core of the most desired information security training system any information security professional will ever want to be in. The CEH, is the first part of a 3 part EC-Council Information Security Track which helps you master hacking technologies. You will become a hacker, but an ethical one! As the security mindset in any organization must not be limited to the silos of a certain vendor, technologies or pieces of equipment. This course was designed to provide you with the tools and techniques used by hackers and information security professionals alike to break into an organization. As we put it, “To beat a hacker, you need to think like a hacker”. This course will immerse you into the Hacker Mindset so that you will be able to defend against future attacks. It puts you in the driver’s seat of a hands-on environment with a systematic ethical hacking process. Here, you will be exposed to an entirely different way of achieving optimal information security posture in their organization; by hacking it! You will scan, test, hack and secure your own systems. You will be thought the Five Phases of Ethical Hacking and thought how you can approach your target and succeed at breaking in every time! The ve phases include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks. The tools and techniques in each of these five phases are provided in detail in an encyclopedic approach to help you identify when an attack has been used against your own targets. -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

ECE 435 – Network Engineering Lecture 4
ECE 435 { Network Engineering Lecture 4 Vince Weaver http://web.eece.maine.edu/~vweaver [email protected] 13 September 2018 Announcements • HW#1 was due. • HW#2 will be posted. Write a mini webserver. • Cybersecurity club Linux Security Lab on Saturday 1 WWW wrapup 2 What if Server Overloaded? • Slashdot effect (modern: HackerNews?) • caching/proxy { squid • Content Delivery Network { akami • Server farms 3 Security • SSL { Secure Socket Layer • Replaced by TLS (Transport Layer Security) • Port 443 for https • Public key encryption. 4 Setting Up a Web-server • Apache • Easy to do, more difficult to secure 5 Web Seach • Web-bots index the web. robots.txt file • Altavista, Hotbot, Excite, Inktomi, etc. • Curated search like Yahoo (people organize links rather than automatically search) • Google (1996 some machine in Stanford, 1997-1998) • MSN search 1999, rebranded Microsoft Bing 2009 6 Remote Connections 7 telnet/rlogin/rsh/ssh • telnet { login to remote system (tcp port 23) everything (including passwords) sent in plain text • rsh/rlogin { remote shell, remote login. (tcp port 514) Didn't even need password, could configure to let you run commands on remote machine. Security based if you had same username on both machines, assumption was getting root on a UNIX machine and connected to Ethernet was expensive/difficult 8 SSH secure shell • tcp port 22 • can login, run commands, tunnel tcp/ip, tunnel X11, file transfer (scp, sftp) • Large number of RFCs • Version 1: 1995, originally freeware but became private • Version 2: 2005, openBSD based on last free version • For security reasons there's a push to drop Version 1 • uses public-key cryptography • transport layer: arranges initial key exchange, server 9 authentication, key re-exchange • user authentication layer: can have password, or can set up keys to allow passwordless, DSA or RSA key pairs • connection layer: set up channels • lots of encryption types supported, old ones being obsoleted as found wanting • Various ssh servers/clients. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -
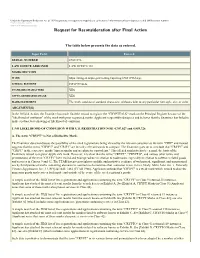
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -

Authenticated Encryption in SSH
Authenticated Encryption in SSH Kenny Paterson Information Security Group @kennyog; www.isg.rhul.ac.uk/~kp Overview (both lectures) • Secure channels and their properties • AEAD (revision) • AEAD ≠ secure channel – the [APW09] attack on SSH • The state of AEAD in SSH today • A new attack on CBC-mode in OpenSSH • Security analysis of other SSH and OpenSSH modes – CTR, ChaChaPoly, gEtM, AES-GCM. 2 Secure channels and their properties Why do we need secure channels? • Secure communications is the most common real- world application of cryptography today. • Secure communications systems are extremely widely-deployed in practice: • SSL/TLS, DTLS, IPsec, SSH, OpenVPN,… • WEP/WPA/WPA2 • GSM/UMTS/4g/LTE • Cryptocat, OTR, SilentCircle • OpenPGP, iMessage, Telegram, Signal, and a thousand other messaging apps • QUIC, MinimalT, TCPcrypt 4 Security properties • Confidentiality – privacy for data • Integrity – detection of data modification • Authenticity – assurance concerning the source of data 5 Some less obvious security properties • Anti-replay • Detection that messages have been repeated. • Detection of deletion • Detection that messages have been deleted by the adversary or dropped by the network. • Detection of re-0rdering • Ensuring that the relative order of messages in each direction on the secure channel is preserved. • Possibly re-ordering the event of violation. • Prevention of traffic-analysis. • Using traffic padding and length-hiding techniques. 6 Possible functionality requirements • Speedy • Low-memory • On-line/parallelisable crypto-operations • Performance is heavily hardware-dependent. • May have different algorithms for different platforms. • IPR-friendly • This issue has slowed down adoption of many otherwise good algorithms, e.g. OCB. • Easy to implement • Without introducing any side-channels. -

Fbi Fbi Flash
TLP: GREEN FBI FLASH FBI FBI Liaison Alert System #M-000045-TT The following information was obtained through FBI investigation and is provided in conjunction with the FBI’s statutory requirement to conduct victim notification as outlined in 42 USC § 10607. In furtherance of public-private partnerships, the FBI routinely advises private industry of various cyber threat indicators observed during the course of our investigations. This data is provided in order to help cyber security professionals and systems administrators to guard against the persistent malicious actions of cyber criminals. This product is released at TLP: GREEN. The information in this product is useful for the awareness of all participating organizations as well as with peers within the broader community or sector. Recipients may share this information with peers and partner organizations within their sector or community, but not via publicly accessible channels. SUMMARY The FBI is providing the following information with HIGH confidence: A group of cyber actors utilizing infrastructure located in Iran have been conducting computer network exploitation activity against public and private U.S. organizations, including Cleared Defense Contractors (CDCs), academic institutions, and energy sector companies. The actors typically utilize common computer intrusion techniques such as the use of TOR, open source reconnaissance, exploitation via SQL injection and web shells, and open source tools for further network penetration and persistence. Internet-facing infrastructures, such as web servers, are typical targets for this group. Once the actors penetrate a victim network, the actors exfiltrate network design information and legitimate user credentials for the victim network. Often times, the actors are able to harvest administrative user credentials and use the credentials to move laterally through a network. -

Wind River® Vxworks® 7 Third Party License Notices
Wind River® VxWorks® 7 Third Party License Notices This document contains third party intellectual property (IP) notices for the BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY Wind River® VxWorks® 7 distribution. Certain licenses and license notices THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, may appear in other parts of the product distribution in accordance with the OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN license requirements. ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Trademarks All company, product and service names used in this software are for ACPICA identification purposes only. Version: 20170303 Component(s): Runtime Wind River and VxWorks are registered trademarks of Wind River Systems. Description: Provides code to implement ACPI specification in VxWorks. UNIX is a registered trademark of The Open Group. IBM and Bluemix are registered trademarks of the IBM Corporation. NOTICES: All other third-party trademarks are the property of their respective owners. 1. Copyright Notice Some or all of this work - Copyright (c) 1999 - 2016, Intel Corp. All rights reserved. Third Party Notices 2. License 2.1. This is your license from Intel Corp. under its intellectual property rights. You may have additional license terms from the party that provided you this software, covering your right to use that party's intellectual property rights. 64-Bit Dynamic Linker Version: 2.2. Intel grants, free of charge, to any person ("Licensee") obtaining a copy Component(s): Runtime of the source code appearing in this file ("Covered Code") an irrevocable, Description: The dynamic linker is used to load shared libraries. -
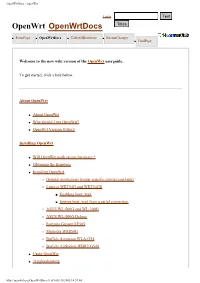
Openwrtdocs - Openwrt
OpenWrtDocs - OpenWrt Login OpenWrt OpenWrtDocs ● FrontPage ● OpenWrtDocs ● TableOfHardware ● RecentChanges ● FindPage Welcome to the new wiki version of the OpenWrt userguide. To get started, click a link below. About OpenWrt ● About OpenWrt ● Why should I run OpenWrt? ● OpenWrt Version History Installing OpenWrt ● Will OpenWrt work on my hardware ? ● Obtaining the firmware ● Installing OpenWrt ❍ General instructions (router specific instructions later) ❍ Linksys WRT54G and WRT54GS ■ Enabling boot_wait ■ Setting boot_wait from a serial connection ❍ ASUS WL-500G and WL-300G ❍ ASUS WL-500G Deluxe ❍ Siemens Gigaset SE505 ❍ Motorola WR850G ❍ Buffalo Airstation WLA-G54 ❍ Buffalo AirStation WBR2-G54S ● Using OpenWrt ● Troubleshooting http://openwrt.org/OpenWrtDocs (1 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt Using OpenWrt ● Using OpenWrt for the first time ● Firstboot / jffs2 ● Editing Files ● ipkg ● Configuration OpenWrt Configuration ● NVRAM ● Network configuration ❍ Sample network configurations ❍ The ethernet switch ■ Normal Behavior ■ Using Robocfg ● Wireless configuration ❍ Basic settings ❍ WEP encryption ❍ WPA encryption ❍ Wireless Distribution System (WDS) / Repeater / Bridge ❍ OpenWrt as client / wireless bridge ● Software configuration ❍ System ■ dnsmasq ■ nas ■ wl ■ TimeZone and NTP ■ Crontab ■ PPPoE Internet Connection ■ Access to syslog ❍ Applications ■ httpd ■ socks-Proxy http://openwrt.org/OpenWrtDocs (2 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt ■ uPnP ■ CUPS - Printing system with spooling ● Hardware ❍ LED OpenWrt -

Analysis and Processing of Cryptographic Protocols
Analysis and Processing of Cryptographic Protocols Submitted in partial fulfilment of the requirements of the degree of Bachelor of Science (Honours) of Rhodes University Bradley Cowie Grahamstown, South Africa November 2009 Abstract The field of Information Security and the sub-field of Cryptographic Protocols are both vast and continually evolving fields. The use of cryptographic protocols as a means to provide security to web servers and services at the transport layer, by providing both en- cryption and authentication to data transfer, has become increasingly popular. However, it is noted that it is rather difficult to perform legitimate analysis, intrusion detection and debugging on data that has passed through a cryptographic protocol as it is encrypted. The aim of this thesis is to design a framework, named Project Bellerophon, that is capa- ble of decrypting traffic that has been encrypted by an arbitrary cryptographic protocol. Once the plain-text has been retrieved further analysis may take place. To aid in this an in depth investigation of the TLS protocol was undertaken. This pro- duced a detailed document considering the message structures and the related fields con- tained within these messages which are involved in the TLS handshake process. Detailed examples explaining the processes that are involved in obtaining and generating the var- ious cryptographic components were explored. A systems design was proposed, considering the role of each of the components required in order to produce an accurate decryption of traffic encrypted by a cryptographic protocol. Investigations into the accuracy and the efficiency of Project Bellerophon to decrypt specific test data were conducted. -

Download CVS 1.11.1P1-3 From: Ftp://Ftp.Software.Ibm.Com/Aix/Freesoftware/Aixtoolbox/RPMS/Ppc/Cvs/ Cvs-1.11.1P1-3.Aix4.3.Ppc.Rpm
2003 CERT Advisories CERT Division [DISTRIBUTION STATEMENT A] Approved for public release and unlimited distribution. http://www.sei.cmu.edu REV-03.18.2016.0 Copyright 2017 Carnegie Mellon University. All Rights Reserved. This material is based upon work funded and supported by the Department of Defense under Contract No. FA8702-15-D-0002 with Carnegie Mellon University for the operation of the Software Engineering Institute, a federally funded research and development center. The view, opinions, and/or findings contained in this material are those of the author(s) and should not be con- strued as an official Government position, policy, or decision, unless designated by other documentation. References herein to any specific commercial product, process, or service by trade name, trade mark, manu- facturer, or otherwise, does not necessarily constitute or imply its endorsement, recommendation, or favoring by Carnegie Mellon University or its Software Engineering Institute. This report was prepared for the SEI Administrative Agent AFLCMC/AZS 5 Eglin Street Hanscom AFB, MA 01731-2100 NO WARRANTY. THIS CARNEGIE MELLON UNIVERSITY AND SOFTWARE ENGINEERING INSTITUTE MATERIAL IS FURNISHED ON AN "AS-IS" BASIS. CARNEGIE MELLON UNIVERSITY MAKES NO WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, AS TO ANY MATTER INCLUDING, BUT NOT LIMITED TO, WARRANTY OF FITNESS FOR PURPOSE OR MERCHANTABILITY, EXCLUSIVITY, OR RESULTS OBTAINED FROM USE OF THE MATERIAL. CARNEGIE MELLON UNIVERSITY DOES NOT MAKE ANY WARRANTY OF ANY KIND WITH RESPECT TO FREEDOM FROM PATENT, TRADEMARK, OR COPYRIGHT INFRINGEMENT. [DISTRIBUTION STATEMENT A] This material has been approved for public release and unlimited distribu- tion. Please see Copyright notice for non-US Government use and distribution.