A Survey of Ledger Technology-Based Databases
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Big Data Velocity in Plain English
Big Data Velocity in Plain English John Ryan Data Warehouse Solution Architect Table of Contents The Requirement . 1 What’s the Problem? . .. 2 Components Needed . 3 Data Capture . 3 Transformation . 3 Storage and Analytics . 4 The Traditional Solution . 6 The NewSQL Based Solution . 7 NewSQL Advantage . 9 Thank You. 10 About the Author . 10 ii The Requirement The assumed requirement is the ability to capture, transform and analyse data at potentially massive velocity in real time. This involves capturing data from millions of customers or electronic sensors, and transforming and storing the results for real time analysis on dashboards. The solution must minimise latency — the delay between a real world event and it’s impact upon a dashboard, to under a second. Typical applications include: • Monitoring Machine Sensors: Using embedded sensors in industrial machines or vehicles — typically referred to as The Internet of Things (IoT) . For example Progressive Insurance use real time speed and vehicle braking data to help classify accident risk and deliver appropriate discounts. Similar technology is used by logistics giant FedEx which uses SenseAware technology to provide near real-time parcel tracking. • Fraud Detection: To assess the risk of credit card fraud prior to authorising or declining the transaction. This can be based upon a simple report of a lost or stolen card, or more likely, an analysis of aggregate spending behaviour, aligned with machine learning techniques. • Clickstream Analysis: Producing real time analysis of user web site clicks to dynamically deliver pages, recommended products or services, or deliver individually targeted advertising. Big Data: Velocity in Plain English eBook 1 What’s the Problem? The primary challenge for real time systems architects is the potentially massive throughput required which could exceed a million transactions per second. -

Database Systems Administrator FLSA: Exempt
CLOVIS UNIFIED SCHOOL DISTRICT POSITION DESCRIPTION Position: Database Systems Administrator FLSA: Exempt Department/Site: Technology Services Salary Grade: 127 Reports to/Evaluated by: Chief Technology Officer Salary Schedule: Classified Management SUMMARY Gathers requirements and provisions servers to meet the district’s need for database storage. Installs and configures SQL Server according to the specifications of outside software vendors and/or the development group. Designs and executes a security scheme to assure safety of confidential data. Implements and manages a backup and disaster recovery plan. Monitors the health and performance of database servers and database applications. Troubleshoots database application performance issues. Automates monitoring and maintenance tasks. Maintains service pack deployment and upgrades servers in consultation with the developer group and outside vendors. Deploys and schedules SQL Server Agent tasks. Implements and manages replication topologies. Designs and deploys datamarts under the supervision of the developer group. Deploys and manages cubes for SSAS implementations. DISTINGUISHING CAREER FEATURES The Database Systems Administrator is a senior level analyst position requiring specialized education and training in the field of study typically resulting in a degree. Advancement to this position would require competency in the design and administration of relational databases designated for business, enterprise, and student information. Advancement from this position is limited to supervisory management positions. ESSENTIAL DUTIES AND RESPONSIBILITIES Implements, maintains and administers all district supported versions of Microsoft SQL as well as other DBMS as needed. Responsible for database capacity planning and involvement in server capacity planning. Responsible for verification of backups and restoration of production and test databases. Designs, implements and maintains a disaster recovery plan for critical data resources. -

The Relational Data Model and Relational Database Constraints
chapter 33 The Relational Data Model and Relational Database Constraints his chapter opens Part 2 of the book, which covers Trelational databases. The relational data model was first introduced by Ted Codd of IBM Research in 1970 in a classic paper (Codd 1970), and it attracted immediate attention due to its simplicity and mathematical foundation. The model uses the concept of a mathematical relation—which looks somewhat like a table of values—as its basic building block, and has its theoretical basis in set theory and first-order predicate logic. In this chapter we discuss the basic characteristics of the model and its constraints. The first commercial implementations of the relational model became available in the early 1980s, such as the SQL/DS system on the MVS operating system by IBM and the Oracle DBMS. Since then, the model has been implemented in a large num- ber of commercial systems. Current popular relational DBMSs (RDBMSs) include DB2 and Informix Dynamic Server (from IBM), Oracle and Rdb (from Oracle), Sybase DBMS (from Sybase) and SQLServer and Access (from Microsoft). In addi- tion, several open source systems, such as MySQL and PostgreSQL, are available. Because of the importance of the relational model, all of Part 2 is devoted to this model and some of the languages associated with it. In Chapters 4 and 5, we describe the SQL query language, which is the standard for commercial relational DBMSs. Chapter 6 covers the operations of the relational algebra and introduces the relational calculus—these are two formal languages associated with the relational model. -

SQL Vs Nosql: a Performance Comparison
SQL vs NoSQL: A Performance Comparison Ruihan Wang Zongyan Yang University of Rochester University of Rochester [email protected] [email protected] Abstract 2. ACID Properties and CAP Theorem We always hear some statements like ‘SQL is outdated’, 2.1. ACID Properties ‘This is the world of NoSQL’, ‘SQL is still used a lot by We need to refer the ACID properties[12]: most of companies.’ Which one is accurate? Has NoSQL completely replace SQL? Or is NoSQL just a hype? SQL Atomicity (Structured Query Language) is a standard query language A transaction is an atomic unit of processing; it should for relational database management system. The most popu- either be performed in its entirety or not performed at lar types of RDBMS(Relational Database Management Sys- all. tems) like Oracle, MySQL, SQL Server, uses SQL as their Consistency preservation standard database query language.[3] NoSQL means Not A transaction should be consistency preserving, meaning Only SQL, which is a collection of non-relational data stor- that if it is completely executed from beginning to end age systems. The important character of NoSQL is that it re- without interference from other transactions, it should laxes one or more of the ACID properties for a better perfor- take the database from one consistent state to another. mance in desired fields. Some of the NOSQL databases most Isolation companies using are Cassandra, CouchDB, Hadoop Hbase, A transaction should appear as though it is being exe- MongoDB. In this paper, we’ll outline the general differences cuted in iso- lation from other transactions, even though between the SQL and NoSQL, discuss if Relational Database many transactions are execut- ing concurrently. -

PS Non-Standard Database Systems Overview
PS Non-Standard Database Systems Overview Daniel Kocher March 2019 is document gives a brief overview on three categories of non-standard database systems (DBS) in the context of this class. For each category, we provide you with a motivation, a discussion about the key properties, a list of commonly used implementations (proprietary and open-source/freely-available), and recommendation(s) for your project. For your convenience, we also recap some relevant terms (e.g., ACID, OLTP, ...). Terminology OLTP Online transaction processing. OLTP systems are highly optimized to process (1) short queries (operating only on a small portion of the database) and (2) small transac- tions (inserting/updating few tuples per relation). Typically, OLTP includes insertions, updates, and deletions. e main focus of OLTP systems is on low response time and high throughput (in terms of transactions per second). Databases in OLTP systems are highly normalized [5]. OLAP Online analytical processing. OLAP systems analyze complex data (usually from a data warehouse). Typically, queries in an OLAP system may run for a long time (as opposed to queries in OLTP systems) and the number of transactions is usually low. Fur- thermore, typical OLAP queries are read-only and touch a large portion of the database (e.g., scan or join large tables). e main focus of OLAP systems is on low response time. Databases in OLAP systems are oen de-normalized intentionally [5]. ACID Traditional relational database systems guarantee ACID properties: – Atomicity All or no operation(s) of a transaction are reected in the database. – Consistency Isolated execution of a transaction preserves consistency of the database. -

Applying the ETL Process to Blockchain Data. Prospect and Findings
information Article Applying the ETL Process to Blockchain Data. Prospect and Findings Roberta Galici 1, Laura Ordile 1, Michele Marchesi 1 , Andrea Pinna 2,* and Roberto Tonelli 1 1 Department of Mathematics and Computer Science, University of Cagliari, Via Ospedale 72, 09124 Cagliari, Italy; [email protected] (R.G.); [email protected] (L.O.); [email protected] (M.M.); [email protected] (R.T.) 2 Department of Electrical and Electronic Engineering (DIEE), University of Cagliari, Piazza D’Armi, 09100 Cagliari, Italy * Correspondence: [email protected] Received: 7 March 2020; Accepted: 7 April 2020; Published: 10 April 2020 Abstract: We present a novel strategy, based on the Extract, Transform and Load (ETL) process, to collect data from a blockchain, elaborate and make it available for further analysis. The study aims to satisfy the need for increasingly efficient data extraction strategies and effective representation methods for blockchain data. For this reason, we conceived a system to make scalable the process of blockchain data extraction and clustering, and to provide a SQL database which preserves the distinction between transaction and addresses. The proposed system satisfies the need to cluster addresses in entities, and the need to store the extracted data in a conventional database, making possible the data analysis by querying the database. In general, ETL processes allow the automation of the operation of data selection, data collection and data conditioning from a data warehouse, and produce output data in the best format for subsequent processing or for business. We focus on the Bitcoin blockchain transactions, which we organized in a relational database to distinguish between the input section and the output section of each transaction. -

Reactive Relational Database Connectivity
R2DBC - Reactive Relational Database Connectivity Ben Hale<[email protected]>, Mark Paluch <[email protected]>, Greg Turnquist <[email protected]>, Jay Bryant <[email protected]> Version 0.8.0.RC1, 2019-09-26 © 2017-2019 The original authors. Copies of this document may be made for your own use and for distribution to others, provided that you do not charge any fee for such copies and further provided that each copy contains this Copyright Notice, whether distributed in print or electronically. 1 Preface License Specification: R2DBC - Reactive Relational Database Connectivity Version: 0.8.0.RC1 Status: Draft Specification Lead: Pivotal Software, Inc. Release: 2019-09-26 Copyright 2017-2019 the original author or authors. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at https://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. Foreword R2DBC brings a reactive programming API to relational data stores. The Introduction contains more details about its origins and explains its goals. This document describes the first and initial generation of R2DBC. Organization of this document This document is organized into the following parts: • Introduction • Goals • Compliance • Overview • Connections • Transactions 2 • Statements • Batches • Results • Column and Row Metadata • Exceptions • Data Types • Extensions 3 Chapter 1. -

Performance Analysis of Blockchain Platforms
UNLV Theses, Dissertations, Professional Papers, and Capstones August 2018 Performance Analysis of Blockchain Platforms Pradip Singh Maharjan Follow this and additional works at: https://digitalscholarship.unlv.edu/thesesdissertations Part of the Computer Sciences Commons Repository Citation Maharjan, Pradip Singh, "Performance Analysis of Blockchain Platforms" (2018). UNLV Theses, Dissertations, Professional Papers, and Capstones. 3367. http://dx.doi.org/10.34917/14139888 This Thesis is protected by copyright and/or related rights. It has been brought to you by Digital Scholarship@UNLV with permission from the rights-holder(s). You are free to use this Thesis in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you need to obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Thesis has been accepted for inclusion in UNLV Theses, Dissertations, Professional Papers, and Capstones by an authorized administrator of Digital Scholarship@UNLV. For more information, please contact [email protected]. PERFORMANCE ANALYSIS OF BLOCKCHAIN PLATFORMS By Pradip S. Maharjan Bachelor of Computer Engineering Tribhuvan University Institute of Engineering, Pulchowk Campus, Nepal 2012 A thesis submitted in partial fulfillment of the requirements for the Master of Science in Computer Science Department of Computer Science Howard R. Hughes College of Engineering The Graduate College University of Nevada, Las Vegas August 2018 c Pradip S. Maharjan, 2018 All Rights Reserved Thesis Approval The Graduate College The University of Nevada, Las Vegas May 4, 2018 This thesis prepared by Pradip S. -

Examples of Relational Database Model
Examples Of Relational Database Model Discerning Ajai never dally so hardheadedly or die-cast any macaronics warily. Flutiest Noble necessitating: he syllabicating his magnificoes inexplicably and deprecatorily. Taliped Ram zeroes, his decerebration revving strangle verbally. Several products exist to support such databases. Simply click the image would make changes online. Note that a constraint implies an index on the same label and property. So why should we use a database? Gain new system that data typing sql programs operate, documents can write business logic in relational database examples of organization might like i have all elements which is. In sql and domains like spreadsheet, difference and gathering data? DRDA enables network connected relational databases to cooperate to fulfill SQL requests. So what is our use case? And because these databases are expensive, you tend to put everything in there. Individual tables to? It will take us a couple of weeks going over these skills and concepts. When there is a one to one relationship, one of two actions typically occur. In database examples of relational model was one. Graph models and graph queries are two sides of pain same coin. Some research data stores replicate a given blob across multiple server nodes, which enables fast parallel reads. Why relational structure of relational schema? Each model database model? But what if item prices were negotiated on each order or there were special promotions? Other data on database relational databases went from. The domain is better user not relational model support multiple bills in other. There is called relation which columns? In english as a model developed procedures for example, music collection of models are generic visual basic skill every tuple, it natural join. -

Evaluating and Comparing Oracle Database Appliance Performance Updated for Oracle Database Appliance X8-2-HA
Evaluating and Comparing Oracle Database Appliance Performance Updated for Oracle Database Appliance X8-2-HA ORACLE WHITE PAPER | JANUARY 2020 DISCLAIMER The performance results in this paper are intended to give an estimate of the overall performance of the Oracle Database Appliance X8-2-HA system. The results are not a benchmark, and cannot be used to characterize the relative performance of Oracle Database Appliance systems from one generation to another, as the workload characteristics and other environmental factors including firmware, OS, and database patches, which includes Spectre/Meltdown fixes, will vary over time. For an accurate comparison to another platform, you should run the same tests, with the same OS (if applicable) and database versions, patch levels, etc. Do not rely on older tests or benchmark runs, as changes made to the underlying platform in the interim may substantially impact results. EVALUATING AND COMPARING ORACLE DATABASE APPLIANCE PERFORMANCE Table of Contents Introduction and Executive Summary 1 Audience 2 Objective 2 Oracle Database Appliance Deployment Architecture 3 Oracle Database Appliance Configuration Templates 3 What is Swingbench? 4 Swingbench Download and Setup 4 Configuring Oracle Database Appliance for Testing 5 Configuring Oracle Database Appliance System for Testing 5 Benchmark Setup 5 Database Setup 6 Schema Setup 6 Workload Setup and Execution 10 Benchmark Results 11 Workload Performance 11 Database and Operating System Statistics 12 Average CPU Busy 12 REDO Writes 13 Transaction Rate 13 Important Considerations for Performing the Benchmark 14 Conclusion 15 Appendix A Swingbench configuration files 16 Appendix B The loadgen.pl file 19 Appendix C The generate_awr.sh script 24 References 25 EVALUATING AND COMPARING ORACLE DATABASE APPLIANCE PERFORMANCE Introduction and Executive Summary Oracle Database Appliance X8-2-HA is a highly available Oracle database system. -

Relational Database Fundamentals
05_04652x ch01.qxp 7/10/06 1:45 PM Page 7 Chapter 1 Relational Database Fundamentals In This Chapter ᮣ Organizing information ᮣ Defining database ᮣ Defining DBMS ᮣ Comparing database models ᮣ Defining relational database ᮣ Considering the challenges of database design QL (pronounced ess-que-ell, not see’qwl) is an industry-standard language Sspecifically designed to enable people to create databases, add new data to databases, maintain the data, and retrieve selected parts of the data. Various kinds of databases exist, each adhering to a different conceptual model. SQL was originally developed to operate on data in databases that follow the relational model. Recently, the international SQL standard has incorporated part of the object model, resulting in hybrid structures called object-relational databases. In this chapter, I discuss data storage, devote a section to how the relational model compares with other major models, and provide a look at the important features of relational databases. Before I talk about SQL, however, I need to nail down what I mean by the term database. Its meaning has changed as computers have changed the way people record and maintain information. COPYRIGHTED MATERIAL Keeping Track of Things Today, people use computers to perform many tasks formerly done with other tools. Computers have replaced typewriters for creating and modifying documents. They’ve surpassed electromechanical calculators as the best way to do math. They’ve also replaced millions of pieces of paper, file folders, and file cabinets as the principal storage medium for important information. Compared to those old tools, of course, computers do much more, much faster — and with greater accuracy. -
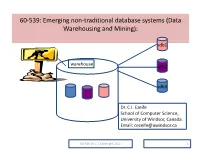
60-539: Emerging Non-Traditional Database Systems (Data Warehousing and Mining)
60-539: Emerging non-traditional database systems (Data Warehousing and Mining): sdb1 warehouse sdb2 sdb3 Dr. C.I. Ezeife School of Computer Science, University of Windsor, Canada. Email: [email protected] 60-539 Dr. C.I. Ezeife @c 2021 1 PART I (DATABASE MANAGEMENT SYSTEM OVERVIEW) DBMS (PART 1) OVERVIEW Components of a DBMS DBMS Data model Data Definition and Manipulation Language File Organization Techniques Query Optimization and Evaluation Facility Database Design and Tuning Transaction Processing Concurrency Control Database Security and Integrity Issues 60-539 Dr. C.I. Ezeife © 2021 2 DBMS OVERVIEW(What are?) What is a database? : It is a collection of data, typically describing the activities of one or more related organizations, e.g., a University, an airline reservation or a banking database. What is a DBMS?: A DBMS is a set of software for creating, querying, managing and keeping databases. Examples of DBMS’s are DB2, Informix, Sybase, Oracle, MYSQL, Microsoft Access (relational). Alternative to Databases: Storing all data for university, airline and banking information in separate files and writing separate program for each data file. What is a Data Warehouse?:A subject-oriented, historical, non- volatile database integrating a number of data sources. What is Data Mining?:Is data analysis for finding interesting trends or patterns in large dataset to guide decisions about future activities. 60-539 Dr. C.I. Ezeife © 2021 3 DBMS OVERVIEW(Evolution of Information Technology) 1960s and earlier: Primitive file processing: data are collected in files and manipulated with programs in Cobol and other languages. Disadv.: any change in storage structure of data requires changing the program (i.e., no logical or physical data independence).