Bluetooth Hacking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Compatibilité Connecteur De Charge De Téléphone Mobile
Sheet1 Compatibilité Connecteur de Charge de Téléphone Mobile Pour vérifier la compatibilité de votre téléphone : - Veuillez chercher votre modèle de téléphone dans la liste ci-dessous. ( Vous pouvez utiliser la fonction Recherche Ctrl+F) - Notez le type du connecteur de votre téléphone. - Assurez vous que le type de connecteur choisi est indiqué dans le descriptif du chargeur. Si votre appareil ne figure pas dans la liste, merci de le signaler : [email protected] Marque Modèle Connecteur Type Acer beTouch E110 microUSB TC4 Acer beTouch E120 microUSB TC4 Acer beTouch E130 microUSB TC4 Acer beTouch E140 microUSB TC4 Acer beTouch E210 microUSB TC4 Acer beTouch E400 microUSB TC4 Acer Inconia Smart microUSB TC4 Acer Liquid Metal microUSB TC4 Acer neoTouch P300 microUSB TC4 Acer neoTouch P400 microUSB TC4 Acer Stream microUSB TC4 Apple Iphone Apple OEM TC1 Apple Iphone 3G Apple OEM TC1 Apple Iphone 3GS Apple OEM TC1 Apple Iphone 4 Apple OEM TC1 Apple Iphone 4S Apple OEM TC1 Apple Iphone 5 Apple Lightning TC9 Blackberry 5790 Mini USB TC5 Blackberry 5820 Mini USB TC5 Blackberry 6210 Mini USB TC5 Blackberry 6220 Mini USB TC5 Blackberry 6230 Mini USB TC5 Blackberry 6280 Mini USB TC5 Blackberry 6510 Mini USB TC5 Blackberry 7210 Mini USB TC5 Blackberry 7230 Mini USB TC5 Blackberry 7250 Mini USB TC5 Blackberry 7280 Mini USB TC5 Blackberry 7290 Mini USB TC5 Blackberry 7510 Mini USB TC5 Blackberry 7520 Mini USB TC5 Blackberry 8800 Mini USB TC5 Blackberry 8820 Mini USB TC5 Blackberry 8830 Mini USB TC5 Blackberry 7100g Mini USB TC5 Blackberry 7100i Mini -

Uso De Sony Ericsson T68/T68i/T610 Con El Concentrador Inalámbrico Logitech
Uso de Sony Ericsson T68/T68i/T610 con el concentrador inalámbrico Logitech © 2003 Logitech, Inc. Uso de Sony Ericsson T68/T68i/T610 con el concentrador inalámbrico Logitech Índice Introducción 3 Compatibilidad de productos 4 Acerca de este manual 5 Conéctese 7 Conexión del Sony Ericsson T68/T68i/T610 7 Comprobación de emparejamiento o conexión del Sony Ericsson T68/T68i/T610 16 Organícese con sincronización 17 Sincronización: qué, cuándo y por qué 17 Comprobación de la configuración de sincronización 20 Sincronización del Sony Ericsson T68/T68i/T610 y el ordenador 21 Comuníquese con amigos y compañeros de trabajo 23 Envío de un mensaje de texto (SMS) 24 Lectura de un mensaje de texto (SMS) 27 Recepción de notificación de llegada de un mensaje de texto (SMS) 28 Copia de seguridad de la libreta de teléfonos del teléfono móvil 29 Comparta sus imágenes 31 Transferencia de imágenes del ordenador al Sony Ericsson T68/T68i/T610 32 Transferencia de imágenes del teléfono Sony Ericsson T610 al ordenador 33 Más información sobre conexión 35 Solicitud de emparejamiento del Sony Ericsson T68/T68i/T610 35 Desconexión y desemparejamiento del Sony Ericsson T68/T68i/T610 37 Resolución de problemas 39 Este manual es una publicación de Logitech. Logitech no asume ninguna responsabilidad por la presencia de posibles errores en el presente manual. La información aquí contenida está sujeta a posibles cambios sin previo aviso. © 2003 Logitech. Reservados todos los derechos. Logitech, el logotipo de Logitech y las demás marcas de Logitech pertenecen a Logitech y pueden estar registradas. Las demás marcas comerciales pertenecen a sus respectivos propietarios. -

Bluetooth Hacking
WhatTheToool Bluetooth Security Workshop July 30th 2005, Liempde, Netherlands Adam Laurie, Marcel Holtmann, Martin Herfurt Who we are ● Adam Laurie – CSO of The Bunker Secure Hosting Ltd. – Co-Maintainer of Apache-SSL – DEFCON Staff/Organiser ● Marcel Holtmann – Maintainer and core developer of the Linux Bluetooth Stack BlueZ ● Martin Herfurt – Security Researcher & Java Programmer – Founder of trifinite.org Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Technology Overview ● Bluetooth SIG – Trade Association – Founded 1998 – Owns & Licenses IP – Individual membership free – Promoter members: Agere, Ericsson, IBM, Intel, Microsoft, Motorola, Nokia and Toshiba – Consumer http://www.bluetooth.com – Technical http://www.bluetooth.org Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Piconet ● Bluetooth devices create a piconet ● One master per piconet ● Up to seven active slaves ● Over 200 passive members are possible ● Master sets the hopping sequence ● Transfer rates of 721 Kbit/sec ● Bluetooth 1.2 and EDR (aka 2.0) ● Adaptive Frequency Hopping ● Faster connection times ● Transfer rates up to 2.1 Mbit/sec Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Scatternet ● Connected piconets create a scatternet ● Master in one and slave in another piconet ● Slave in two different piconets ● Only master in one piconet ● Scatternet support is optional Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Stack Protokoll_Application Application specific security mechanisms Bluetooth host security mechanisms Security mechanisms -

Bluetooth Hacking
Hacking Bluetooth enabled mobile phones and beyond – Full Disclosure Blackhat Security Briefings April 1st 2005, Amsterdam, the Netherlands Adam Laurie, Marcel Holtmann, Martin Herfurt Who we are ● Adam Laurie – CSO of The Bunker Secure Hosting Ltd. – Co-Maintainer of Apache-SSL – DEFCON Staff/Organiser ● Marcel Holtmann – Maintainer and core developer of the Linux Bluetooth Stack BlueZ ● Martin Herfurt – Security Researcher – Founder of trifinite.org Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Technology Overview ● Bluetooth SIG – Trade Association – Founded 1998 – Owns & Licenses IP – Individual membership free – Promoter members: Agere, Ericsson, IBM, Intel, Microsoft, Motorola, Nokia and Toshiba – Consumer http://www.bluetooth.com – Technical http://www.bluetooth.org Adam Laurie, Marcel Holtmann, Martin Herfurt Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Technology ● Data and voice transmission ● ACL data connections ● SCO and eSCO voice channels ● Symmetric and asymmetric connections ● Frequency hopping ● ISM band at 2.4 GHz ● 79 channels ● 1600 hops per second ● Multi-Slot packets Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Piconet ● Bluetooth devices create a piconet ● One master per piconet ● Up to seven active slaves ● Over 200 passive members are possible ● Master sets the hopping sequence ● Transfer rates of 721 Kbit/sec ● Bluetooth 1.2 and EDR (aka 2.0) ● Adaptive Frequency Hopping ● Transfer rates up to 2.1 Mbit/sec Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Scatternet ● Connected piconets create a scatternet ● Master in one and slave in another piconet ● Slave in two different piconets ● Only master in one piconet ● Scatternet support is optional Adam Laurie, Marcel Holtmann, Martin Herfurt Bluetooth Architecture ● Hardware layer ● Radio, Baseband and Link Manager ● Access through Host Controller Interface – Hardware abstraction – Standards for USB and UART ● Host protocol stack ● L2CAP, RFCOMM, BNEP, AVDTP etc. -

Mobile Connection Explorer for Windows Introduction and Features
Mobile Connection Explorer 15 May 2013 for Windows Version 21 Introduction and Features Public version Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic e-mail: [email protected] Contents Contents ...................................................................................................................... 2 History ......................................................................................................................... 3 1. Scope ..................................................................................................................... 3 2. Abbreviations ......................................................................................................... 4 3. Solution .................................................................................................................. 5 4. Specification ........................................................................................................... 5 5. Product description ................................................................................................. 9 5.1 Supported operating systems ....................................................................... 9 5.2 Hardware device connections ....................................................................... 9 5.3 Network connection types ............................................................................. 9 5.4 Customizable graphical skin ...................................................................... -

Einsatz Des Standardtelefons Von Sony Ericsson Mit Dem Kabellosen
Einsatz des Standardtelefons von Sony Ericsson mit dem kabellosen Logitech-Hub © 2005 Logitech, Inc. Einsatz des at mit dem kabellosen Logitech-Hub Inhalt Voraussetzungen 3 Anschließen des Standardtelefons von Sony Ericsson 3 Überprüfen der Verbindung des Geräts 6 Ordnung schaffen durch Synchronisieren! 8 Synchronisieren des Standardtelefons von Sony Ericsson mit dem Computer 8 Überprüfen der Synchronisierungseinstellungen 10 Senden von Bildern 11 Übertragen von Bildern vom Computer auf das Mobiltelefon 11 Übertragen von Bildern vom Mobiltelefon auf den Computer 12 Übertragen von Anrufen auf den Computer 13 Fehleranalyse 14 Herausgeber dieses Handbuchs ist Logitech. Logitech übernimmt keine Haftung für etwaige Fehler in diesem Handbuch. Die hier vorliegenden Informationen können ohne vorherige Benachrichtigung geändert werden. © 2005 Logitech. Alle Rechte vorbehalten. Logitech, das Logitech-Logo und andere Logitech-Marken sind Eigentum von Logitech und ggf. eingetragen. Alle anderen Marken sind Eigentum ihrer jeweiligen Inhaber. DieBluetooth -Wortmarke und -Logos sind Eigentum von Bluetooth SIG, Inc. Jeder Gebrauch dieser Marken durch Logitech unterliegt Lizenzbestimmungen. Alle Marken und Handelsnamen sind Eigentum ihrer jeweiligen Inhaber. Microsoft, MSN, ActiveSync und Windows sind eingetragene Marken bzw. Marken der Microsoft Corporation in den USA und/oder anderen Ländern. Abbildung der Screenshots mit Genehmigung der Microsoft Corporation. Einsatz des at mit dem kabellosen Logitech-Hub Voraussetzungen Bevor Sie das Standardtelefon von Sony Ericsson mit dem kabellosen Hub verwenden können, müssen folgenden Voraussetzungen erfüllt sein: • Sie haben ein funktionstüchtiges, nicht-Symbian Standardtelefon von Sony Ericsson. • Das Logitech-Produkt, die SetPoint™-Software und Easy Synchronization sind installiert. Bei der SetPoint-Installation wird die WIDCOMM® Bluetooth®-Software (der Stack) installiert. Die meisten Versionen des WIDCOMM® Bluetooth®-Stack werden unterstützt. -

Bluetooth Hands Free Car Kit Model No. NLCK-BT01 Installation Guide
Specification: Connection to Microphone Product Bluetooth Car kit 5. Volume control Bluetooth 1.1 specification Bluetooth Compliance Bluetooth headset profiles Adjustable volume by rolling Volume Control button 2.45 GHz ISM band Frequency Band 6. LED signaling 79 channels frequency hopping Bluetooth Hands Free Car Kit TX Output Power Class 2 ( 4dBm ) The LED is used to give an optical feedback to the user. It is Model No. NLCK-BT01 Receiver Sensitivity <-78dBm connected to pin RTS. There are two answering call modes you Operating Range Up to 10 meters can choose as below, basically Security Encrypted link Installation Guide Maximum current 150mA We set it in automatic mode: Input Voltage 12V manual mode: red LED lights up – answering call manually. Installation: automatic mode: green LED lights up – answering call 1. Insert the cigarette lighter plug of Bluetooth Car Kit into the automatically. cigarette lighter socket in the car. 7. Connection to a mobile phone 2. Insert the microphone plug into the microphone socket on The first example describes the process with the Ericsson mobile Bluetooth Hands Free Car kit, and place the microphone phone R520m. For other cell phones with Bluetooth, such as at appropriate position (preferably on the sun visor). Ericsson T68, Ericsson T39, Nokia 6310, are nearly the same Operation: procedure. 1. ON/OFF button To control power on/off by pushing ON/OFF button. 7.1 Switch the car kit on . (Approximately 2 sec) and there 2. Talk button is ring tone means the car kit is turn on, then press Talk button (Approximately 2 sec.) till the red and The Talk button is used for handset handling. -

电子元器件系列(中国.厦门) Email:[email protected]
电子元器件系列(中国.厦门) www.rf-china.com F-Micom co.,Ltd 厦门销售电话:0592-5713956 EMail:[email protected] Tel:0086-592-5713956 Fax:0592-5201617 AB/RCR05G101JS :ALEN BRADLEY resistance AB/RCR05G471JS :ALEN BRADLEY resistance ABB/A94000-230V :ABB A9 40 00 230V ABI/AC4968SI :Lampe 24V 15W E27 sph. depolie ABI/AC5010SI :Lampe 24V 25W dÈpolie ABI/AC6200SI :Lampe 24V 60W E27 sph. depolie ABI/AH3315PP :Lampe pousse plante 75W E27 ABI/AK1363VE :Tube fluorescent vert 18W 590mm ABUS/REF65 :Cadenas laiton 35mm double ancrage ACC/100105 :3 port manifold stainless steel ACC/100111 :Maintenance manifold ACC/438F11510 :Solid state delay ACC/ADPHC4MCK1 :Absorber for compressor ACCEL/106047 :Tubes couleur rouge ACCEL/106050 :Tube couleur vert ACCEL/106053 :Tube couleur bleu ACCEL/107652 :Cordon HQ A/V 3xRCA 3m ACCEL/107655 :Cordon HQ A/V 3xRCA 5m ACCEL/107861 :Cordon HQ peritel M/M 1.5m ACCEL/108093 :Commutateur peritel 3 voies 0.5m ACCEL/109118 :Cordon VHQ 2RCA/2RCA 5m ACCEL/109121 :Cordon VHQ 2xRCA/2xRCA 10m ACCEL/109133 :Cordon VHQ 2xRCA/J3.5st 5m ACCEL/109134 :Cordon VHQ 2xRCA/J3.5st 10m ACCEL/109160 :Cordon VHQ 3xRCA/3xRCA 1.5m ACCEL/109187 :Cordon VHQ S-VHS/S-VHS 5m ACCEL/109192 :Cordon VHQ S-VHS/S-VHS 20m ACCEL/109202 :Cordon VHQ video RCA/RCA 5m ACCEL/111100 :Cordon VHQ vidÈo pÈritel/3xRCA ACCEL/120635 :120635 ACCEL/149951 :Paire enceintes HIFI 90W 3HP 50cm ACCEL/149960 :149960 ACCEL/173457 :Micro UHM68 ACCEL/180026 :Pied micro perche ACCEL/199918 :Haut parleur ACCEL/270576 :270576 ACCEL/337116 :337116 ACCEL/350634 :350634 ACCEL/350662 :350662 ACCEL/399252 -

Themes for Sony Ericsson Phones Developers Guidelines |Sony Ericsson Themes
Developers guidelines June 2010 Themes for Sony Ericsson phones Developers guidelines |Sony Ericsson Themes Preface Purpose of this document This document describes how to implement themes for Sony Ericsson mobile phones. The document is intended for content providers who want guidelines to optimally create themes and the elements required to create an appealing theme. People who can benefit from this document are: • Software developers • Operators and service providers • Content providers It is assumed that the reader is familiar with different graphic and sound formats. These Developers guidelines are published by: This document is published by Sony Ericsson Mobile Communications AB, without any Sony Ericsson Mobile Communications AB, warranty*. Improvements and changes to this text necessitated by typographical errors, SE-221 88 Lund, Sweden inaccuracies of current information or improvements to programs and/or equipment, www.sonyericsson.com/ may be made by Sony Ericsson Mobile Communications AB at any time and without notice. Such changes will, however, be © Sony Ericsson Mobile Communications AB, incorporated into new editions of this document. 2004. All rights reserved. You are hereby granted Printed versions are to be regarded as temporary a license to download and/or print a copy of this reference copies only. document. Any rights not expressly granted herein are *All implied warranties, including without limitation the implied warranties of reserved. merchantability or fitness for a particular purpose, are excluded. In no event shall 40th version (June 2010) Sony Ericsson or its licensors be liable for Publication number: EN/LZT 108 7584 R40A incidental or consequential damages of any nature, including but not limited to lost profits or commercial loss, arising out of the use of the information in this document. -

Protecting Smart Phones by Means of Execution Replication
Technical Report IR-CS-54 (September 2009) Protecting smart phones by means of execution replication Georgios Portokalidis Philip Homburg Vrije Universiteit Amsterdam Vrije Universiteit Amsterdam [email protected] [email protected] Nicholas FitzRoy-Dale NICTA [email protected] Kostas Anagnostakis Herbert Bos Institute for Infocomm Research Vrije Universiteit Amsterdam [email protected] [email protected] Abstract attack detection techniques based on dynamic taint anal- Smartphones have come to resemble PCs in software ysis. complexity, with complexity usually leading to bugs and Categories and Subject Descriptors D.4.6 [Security vulnerabilities. Moreover, as smartphones are increas- and Protection]: Invasive software ingly used for financial transactions and other privacy- sensitive tasks, they are becoming attractive targets for General Terms Security, Mobile phones attackers. Unfortunately, smartphones are quite different Keywords Android, Decoupled security from PCs in terms of resource constraints imposed on the design of protection mechanisms, as battery power 1. Introduction is an extremely scarce resource. As a consequence, se- Smartphones have come to resemble general-purpose curity solutions designed for PCs may not be directly ap- computers: in addition to traditional telephony stacks, plicable to smartphones, as they may reduce battery life- calendars, games and addressbooks, we now use them time significantly. Worse, as no single protection mecha- for browsing the web, reading email, watching online nism offers 100% security, it may be desirable to tighten videos, and many other activities that we used to per- up security further by applying multiple security solu- form on PCs. A plethora of new applications, such as tions at the same time, thus increasing attack coverage navigation and location-sensitive information services, and accuracy. -

Implementasi Nagios Untuk Merancang Sistem Monitoring Client Jaringan Komputer Menggunakan SMS Dan Email
IMPLEMENTASI NAGIOS UNTUK MERANCANG SISTEM MONITORING CLIENT JARINGAN KOMPUTER MENGGUNAKAN SMS DAN EMAIL Disusun Oleh : Endah Mardiyani 104091002867 PROGRAM STUDI TEKNIK INFORMATIKA FAKULTAS SAINS DAN TEKNOLOGI UNIVERSITAS ISLAM NEGERI SYARIF HIDAYATULLAH JAKARTA 2009 IMPLEMENTASI NAGIOS UNTUK MERANCANG SISTEM MONITORING CLIENT JARINGAN KOMPUTER MENGGUNAKAN SMS DAN EMAIL Oleh: Endah Mardiyani 104091002867 Skripsi sebagai salah satu syarat untuk memperoleh gelar Sarjana Komputer Fakultas Sains dan Teknologi Universitas Islam Negeri Syarif Hidayatullah Jakarta PROGRAM STUDI TEKNIK INFORMATIKA FAKULTAS SAINS DAN TEKNOLOGI UNIVERSITAS ISLAM NEGERI SYARIF HIDAYATULLAH JAKARTA 2009 IMPLEMENTASI NAGIOS UNTUK MERANCANG SISTEM MONITORING CLIENT JARINGAN KOMPUTER MENGGUNAKAN SMS DAN EMAIL Skripsi Sebagai Salah Satu Syarat untuk Memperoleh Gelar Sarjana Komputer Pada Fakultas Sains dan Teknologi Universitas Islam Negeri Syarif Hidayatullah Jakarta Oleh : ENDAH MARDIYANI (104091002867) Menyetujui, Pembimbing 1 Pembimbing 2 M. Iwan Wahyudin, ST, MT Hari Satria, M.Si, CCNA Mengetahui, Ketua Program Studi Teknik Informatika Yusuf Durachman, M.Sc, MIT NIP. 150378017 PENGESAHAN UJIAN Skripsi yang berjudul “Implementasi Nagios Untuk Merancang Sistem Monitoring Client Jaringan Komputer Menggunakan SMS Dan Email”. Telah diuji dan dinyatakan lulus dalam sidang munaqosyah Fakultas Sains dan Teknologi UIN Syarif Hidayatullah Jakarta. Skripsi ini telah diterima sebagai salah satu syarat untuk memperoleh gelar sarjana strata satu (S1) pada program studi Teknik -
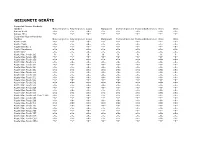
Supported Handset Devices June2010.Xlsx
GEEIGNETE GERÄTE Supported Airness Handsets Handset Mono Ringtones Poly Ringtones Logos Wallpapers Animated pictures Funsounds/Realtones Video Vibra Airness Air99 =N= =Y= =N= =Y= =Y= =N= =N= =Y= Airness HT-1 =N= =Y= =N= =Y= =Y= =Y= =Y= =Y= Supported Alcatel Handsets Handset Mono Ringtones Poly Ringtones Logos Wallpapers Animated pictures Funsounds/Realtones Video Vibra Alcatel C551 =N= =Y= =N= =Y= =Y= =Y= =Y= =N= Alcatel C552 =N= =Y= =N= =Y= =Y= =Y= =Y= =N= Alcatel Elle No. 1 =N= =Y= =N= =Y= =Y= =Y= =Y= =N= Alcatel Mandarina =N= =Y= =N= =Y= =Y= =Y= =Y= =Y= Alcatel OH2 =N= =Y= =N= =Y= =Y= =N= =N= =N= Alcatel One Touch 153 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 155 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 156 =N= =Y= =N= =Y= =Y= =N= =N= =N= Alcatel One Touch 30x =N= =N= =N= =N= =N= =N= =N= =N= Alcatel One Touch 311 =N= =N= =N= =N= =N= =N= =N= =N= Alcatel One Touch 320 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 331 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 332 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 355 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 501 =N= =N= =N= =N= =N= =N= =N= =N= Alcatel One Touch 511 =N= =N= =N= =N= =N= =N= =N= =N= Alcatel One Touch 512 =N= =N= =N= =N= =N= =N= =N= =N= Alcatel One Touch 525 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 526 =N= =Y= =N= =N= =N= =N= =N= =N= Alcatel One Touch 531 =N= =N= =N= =Y= =Y= =N= =N= =N= Alcatel One Touch 535 =N= =Y= =N= =Y= =Y= =Y= =N= =N= Alcatel One Touch 556 / 557 / 565 =N= =Y= =N= =Y= =Y= =Y= =Y= =N= Alcatel One Touch 565 =N=