Elementary Complexity Theory
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Slides 6, HT 2019 Space Complexity
Computational Complexity; slides 6, HT 2019 Space complexity Prof. Paul W. Goldberg (Dept. of Computer Science, University of Oxford) HT 2019 Paul Goldberg Space complexity 1 / 51 Road map I mentioned classes like LOGSPACE (usually calledL), SPACE(f (n)) etc. How do they relate to each other, and time complexity classes? Next: Various inclusions can be proved, some more easy than others; let's begin with \low-hanging fruit"... e.g., I have noted: TIME(f (n)) is a subset of SPACE(f (n)) (easy!) We will see e.g.L is a proper subset of PSPACE, although it's unknown how they relate to various intermediate classes, e.g.P, NP Various interesting problems are complete for PSPACE, EXPTIME, and some of the others. Paul Goldberg Space complexity 2 / 51 Convention: In this section we will be using Turing machines with a designated read only input tape. So, \logarithmic space" becomes meaningful. Space Complexity So far, we have measured the complexity of problems in terms of the time required to solve them. Alternatively, we can measure the space/memory required to compute a solution. Important difference: space can be re-used Paul Goldberg Space complexity 3 / 51 Space Complexity So far, we have measured the complexity of problems in terms of the time required to solve them. Alternatively, we can measure the space/memory required to compute a solution. Important difference: space can be re-used Convention: In this section we will be using Turing machines with a designated read only input tape. So, \logarithmic space" becomes meaningful. Paul Goldberg Space complexity 3 / 51 Definition. -

The Complexity Zoo
The Complexity Zoo Scott Aaronson www.ScottAaronson.com LATEX Translation by Chris Bourke [email protected] 417 classes and counting 1 Contents 1 About This Document 3 2 Introductory Essay 4 2.1 Recommended Further Reading ......................... 4 2.2 Other Theory Compendia ............................ 5 2.3 Errors? ....................................... 5 3 Pronunciation Guide 6 4 Complexity Classes 10 5 Special Zoo Exhibit: Classes of Quantum States and Probability Distribu- tions 110 6 Acknowledgements 116 7 Bibliography 117 2 1 About This Document What is this? Well its a PDF version of the website www.ComplexityZoo.com typeset in LATEX using the complexity package. Well, what’s that? The original Complexity Zoo is a website created by Scott Aaronson which contains a (more or less) comprehensive list of Complexity Classes studied in the area of theoretical computer science known as Computa- tional Complexity. I took on the (mostly painless, thank god for regular expressions) task of translating the Zoo’s HTML code to LATEX for two reasons. First, as a regular Zoo patron, I thought, “what better way to honor such an endeavor than to spruce up the cages a bit and typeset them all in beautiful LATEX.” Second, I thought it would be a perfect project to develop complexity, a LATEX pack- age I’ve created that defines commands to typeset (almost) all of the complexity classes you’ll find here (along with some handy options that allow you to conveniently change the fonts with a single option parameters). To get the package, visit my own home page at http://www.cse.unl.edu/~cbourke/. -

Zero-Knowledge Proof Systems
Extracted from a working draft of Goldreich's FOUNDATIONS OF CRYPTOGRAPHY. See copyright notice. Chapter ZeroKnowledge Pro of Systems In this chapter we discuss zeroknowledge pro of systems Lo osely sp eaking such pro of systems have the remarkable prop erty of b eing convincing and yielding nothing b eyond the validity of the assertion The main result presented is a metho d to generate zero knowledge pro of systems for every language in NP This metho d can b e implemented using any bit commitment scheme which in turn can b e implemented using any pseudorandom generator In addition we discuss more rened asp ects of the concept of zeroknowledge and their aect on the applicabili ty of this concept Organization The basic material is presented in Sections through In particular we start with motivation Section then we dene and exemplify the notions of inter active pro ofs Section and of zeroknowledge Section and nally we present a zeroknowledge pro of systems for every language in NP Section Sections dedicated to advanced topics follow Unless stated dierently each of these advanced sections can b e read indep endently of the others In Section we present some negative results regarding zeroknowledge pro ofs These results demonstrate the optimality of the results in Section and mo tivate the variants presented in Sections and In Section we present a ma jor relaxion of zeroknowledge and prove that it is closed under parallel comp osition which is not the case in general for zeroknowledge In Section we dene and discuss zeroknowledge pro ofs of knowledge In Section we discuss a relaxion of interactive pro ofs termed computationally sound pro ofs or arguments In Section we present two constructions of constantround zeroknowledge systems The rst is an interactive pro of system whereas the second is an argument system Subsection is a prerequisite for the rst construction whereas Sections and constitute a prerequisite for the second Extracted from a working draft of Goldreich's FOUNDATIONS OF CRYPTOGRAPHY. -

A Study of the NEXP Vs. P/Poly Problem and Its Variants by Barıs
A Study of the NEXP vs. P/poly Problem and Its Variants by Barı¸sAydınlıoglu˘ A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Sciences) at the UNIVERSITY OF WISCONSIN–MADISON 2017 Date of final oral examination: August 15, 2017 This dissertation is approved by the following members of the Final Oral Committee: Eric Bach, Professor, Computer Sciences Jin-Yi Cai, Professor, Computer Sciences Shuchi Chawla, Associate Professor, Computer Sciences Loris D’Antoni, Asssistant Professor, Computer Sciences Joseph S. Miller, Professor, Mathematics © Copyright by Barı¸sAydınlıoglu˘ 2017 All Rights Reserved i To Azadeh ii acknowledgments I am grateful to my advisor Eric Bach, for taking me on as his student, for being a constant source of inspiration and guidance, for his patience, time, and for our collaboration in [9]. I have a story to tell about that last one, the paper [9]. It was a late Monday night, 9:46 PM to be exact, when I e-mailed Eric this: Subject: question Eric, I am attaching two lemmas. They seem simple enough. Do they seem plausible to you? Do you see a proof/counterexample? Five minutes past midnight, Eric responded, Subject: one down, one to go. I think the first result is just linear algebra. and proceeded to give a proof from The Book. I was ecstatic, though only for fifteen minutes because then he sent a counterexample refuting the other lemma. But a third lemma, inspired by his counterexample, tied everything together. All within three hours. On a Monday midnight. I only wish that I had asked to work with him sooner. -

Overview of the Massachusetts English Language Assessment-Oral
Overview of the Massachusetts English Language Assessment-Oral (MELA-O) Massachusetts Department of Elementary and Secondary Education June 2010 This document was prepared by the Massachusetts Department of Elementary and Secondary Education Dr. Mitchell D. Chester, Ed.D. Commissioner of Elementary and Secondary Education The Massachusetts Department of Elementary and Secondary Education, an affirmative action employer, is committed to ensuring that all of its programs and facilities are accessible to all members of the public. We do not discriminate on the basis of age, color, disability, national origin, race, religion, sex or sexual orientation. Inquiries regarding the Department’s compliance with Title IX and other civil rights laws may be directed to the Human Resources Director, 75 Pleasant St., Malden, MA 02148-4906 781-338-6105. © 2010 Massachusetts Department of Elementary and Secondary Education Permission is hereby granted to copy any or all parts of this document for non-commercial educational purposes. Please credit the “Massachusetts Department of Elementary and Secondary Education.” This document printed on recycled paper Massachusetts Department of Elementary and Secondary Education 75 Pleasant Street, MA 02148-4906 Phone 781-338-3000 TTY: N.E.T. Relay 800-439-2370 www.doe.mass.edu Commissioner’s Foreword Dear Colleagues: I am pleased to provide you with the Overview of the Massachusetts English Language Assessment-Oral (MELA-O). The purpose of this publication is to provide a description of the MELA-O for educators, parents, and others who have an interest in the assessment of students who are designated as limited English proficient (LEP). The MELA-O is one component of the Massachusetts English Proficiency Assessment (MEPA), the state’s English proficiency assessment. -

Interactions of Computational Complexity Theory and Mathematics
Interactions of Computational Complexity Theory and Mathematics Avi Wigderson October 22, 2017 Abstract [This paper is a (self contained) chapter in a new book on computational complexity theory, called Mathematics and Computation, whose draft is available at https://www.math.ias.edu/avi/book]. We survey some concrete interaction areas between computational complexity theory and different fields of mathematics. We hope to demonstrate here that hardly any area of modern mathematics is untouched by the computational connection (which in some cases is completely natural and in others may seem quite surprising). In my view, the breadth, depth, beauty and novelty of these connections is inspiring, and speaks to a great potential of future interactions (which indeed, are quickly expanding). We aim for variety. We give short, simple descriptions (without proofs or much technical detail) of ideas, motivations, results and connections; this will hopefully entice the reader to dig deeper. Each vignette focuses only on a single topic within a large mathematical filed. We cover the following: • Number Theory: Primality testing • Combinatorial Geometry: Point-line incidences • Operator Theory: The Kadison-Singer problem • Metric Geometry: Distortion of embeddings • Group Theory: Generation and random generation • Statistical Physics: Monte-Carlo Markov chains • Analysis and Probability: Noise stability • Lattice Theory: Short vectors • Invariant Theory: Actions on matrix tuples 1 1 introduction The Theory of Computation (ToC) lays out the mathematical foundations of computer science. I am often asked if ToC is a branch of Mathematics, or of Computer Science. The answer is easy: it is clearly both (and in fact, much more). Ever since Turing's 1936 definition of the Turing machine, we have had a formal mathematical model of computation that enables the rigorous mathematical study of computational tasks, algorithms to solve them, and the resources these require. -

Introduction to the Theory of Computation Computability, Complexity, and the Lambda Calculus Some Notes for CIS262
Introduction to the Theory of Computation Computability, Complexity, And the Lambda Calculus Some Notes for CIS262 Jean Gallier and Jocelyn Quaintance Department of Computer and Information Science University of Pennsylvania Philadelphia, PA 19104, USA e-mail: [email protected] c Jean Gallier Please, do not reproduce without permission of the author April 28, 2020 2 Contents Contents 3 1 RAM Programs, Turing Machines 7 1.1 Partial Functions and RAM Programs . 10 1.2 Definition of a Turing Machine . 15 1.3 Computations of Turing Machines . 17 1.4 Equivalence of RAM programs And Turing Machines . 20 1.5 Listable Languages and Computable Languages . 21 1.6 A Simple Function Not Known to be Computable . 22 1.7 The Primitive Recursive Functions . 25 1.8 Primitive Recursive Predicates . 33 1.9 The Partial Computable Functions . 35 2 Universal RAM Programs and the Halting Problem 41 2.1 Pairing Functions . 41 2.2 Equivalence of Alphabets . 48 2.3 Coding of RAM Programs; The Halting Problem . 50 2.4 Universal RAM Programs . 54 2.5 Indexing of RAM Programs . 59 2.6 Kleene's T -Predicate . 60 2.7 A Non-Computable Function; Busy Beavers . 62 3 Elementary Recursive Function Theory 67 3.1 Acceptable Indexings . 67 3.2 Undecidable Problems . 70 3.3 Reducibility and Rice's Theorem . 73 3.4 Listable (Recursively Enumerable) Sets . 76 3.5 Reducibility and Complete Sets . 82 4 The Lambda-Calculus 87 4.1 Syntax of the Lambda-Calculus . 89 4.2 β-Reduction and β-Conversion; the Church{Rosser Theorem . 94 4.3 Some Useful Combinators . -
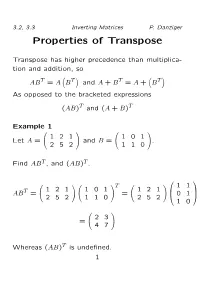
Properties of Transpose
3.2, 3.3 Inverting Matrices P. Danziger Properties of Transpose Transpose has higher precedence than multiplica- tion and addition, so T T T T AB = A B and A + B = A + B As opposed to the bracketed expressions (AB)T and (A + B)T Example 1 1 2 1 1 0 1 Let A = ! and B = !. 2 5 2 1 1 0 Find ABT , and (AB)T . T 1 1 1 2 1 1 0 1 1 2 1 0 1 ABT = ! ! = ! 0 1 2 5 2 1 1 0 2 5 2 B C @ 1 0 A 2 3 = ! 4 7 Whereas (AB)T is undefined. 1 3.2, 3.3 Inverting Matrices P. Danziger Theorem 2 (Properties of Transpose) Given ma- trices A and B so that the operations can be pre- formed 1. (AT )T = A 2. (A + B)T = AT + BT and (A B)T = AT BT − − 3. (kA)T = kAT 4. (AB)T = BT AT 2 3.2, 3.3 Inverting Matrices P. Danziger Matrix Algebra Theorem 3 (Algebraic Properties of Matrix Multiplication) 1. (k + `)A = kA + `A (Distributivity of scalar multiplication I) 2. k(A + B) = kA + kB (Distributivity of scalar multiplication II) 3. A(B + C) = AB + AC (Distributivity of matrix multiplication) 4. A(BC) = (AB)C (Associativity of matrix mul- tiplication) 5. A + B = B + A (Commutativity of matrix ad- dition) 6. (A + B) + C = A + (B + C) (Associativity of matrix addition) 7. k(AB) = A(kB) (Commutativity of Scalar Mul- tiplication) 3 3.2, 3.3 Inverting Matrices P. Danziger The matrix 0 is the identity of matrix addition. -

Lecture 13: Circuit Complexity 1 Binary Addition
CS 810: Introduction to Complexity Theory 3/4/2003 Lecture 13: Circuit Complexity Instructor: Jin-Yi Cai Scribe: David Koop, Martin Hock For the next few lectures, we will deal with circuit complexity. We will concentrate on small depth circuits. These capture parallel computation. Our main goal will be proving circuit lower bounds. These lower bounds show what cannot be computed by small depth circuits. To gain appreciation for these lower bound results, it is essential to first learn about what can be done by these circuits. In next two lectures, we will exhibit the computational power of these circuits. We start with one of the simplest computations: integer addition. 1 Binary Addition Given two binary numbers, a = a1a2 : : : an−1an and b = b1b2 : : : bn−1bn, we can add the two using the elementary school method { adding each column and carrying to the next. In other words, r = a + b, an an−1 : : : a1 a0 + bn bn−1 : : : b1 b0 rn+1 rn rn−1 : : : r1 r0 can be accomplished by first computing r0 = a0 ⊕ b0 (⊕ is exclusive or) and computing a carry bit, c1 = a0 ^ b0. Now, we can compute r1 = a1 ⊕ b1 ⊕ c1 and c2 = (c1 ^ (a1 _ b1)) _ (a1 ^ b1), and in general we have rk = ak ⊕ bk ⊕ ck ck = (ck−1 ^ (ak _ bk)) _ (ak ^ bk) Certainly, the above operation can be done in polynomial time. The main question is, can we do it in parallel faster? The computation expressed above is sequential. Before computing rk, one needs to compute all the previous output bits. -

Computational Complexity
Computational Complexity The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Vadhan, Salil P. 2011. Computational complexity. In Encyclopedia of Cryptography and Security, second edition, ed. Henk C.A. van Tilborg and Sushil Jajodia. New York: Springer. Published Version http://refworks.springer.com/mrw/index.php?id=2703 Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33907951 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Open Access Policy Articles, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#OAP Computational Complexity Salil Vadhan School of Engineering & Applied Sciences Harvard University Synonyms Complexity theory Related concepts and keywords Exponential time; O-notation; One-way function; Polynomial time; Security (Computational, Unconditional); Sub-exponential time; Definition Computational complexity theory is the study of the minimal resources needed to solve computational problems. In particular, it aims to distinguish be- tween those problems that possess efficient algorithms (the \easy" problems) and those that are inherently intractable (the \hard" problems). Thus com- putational complexity provides a foundation for most of modern cryptogra- phy, where the aim is to design cryptosystems that are \easy to use" but \hard to break". (See security (computational, unconditional).) Theory Running Time. The most basic resource studied in computational com- plexity is running time | the number of basic \steps" taken by an algorithm. (Other resources, such as space (i.e., memory usage), are also studied, but they will not be discussed them here.) To make this precise, one needs to fix a model of computation (such as the Turing machine), but here it suffices to informally think of it as the number of \bit operations" when the input is given as a string of 0's and 1's. -

Complexity Theory
Complexity Theory IE 661: Scheduling Theory Fall 2003 Satyaki Ghosh Dastidar Outline z Goals z Computation of Problems { Concepts and Definitions z Complexity { Classes and Problems z Polynomial Time Reductions { Examples and Proofs z Summary University at Buffalo Department of Industrial Engineering 2 Goals of Complexity Theory z To provide a method of quantifying problem difficulty in an absolute sense. z To provide a method comparing the relative difficulty of two different problems. z To be able to rigorously define the meaning of efficient algorithm. (e.g. Time complexity analysis of an algorithm). University at Buffalo Department of Industrial Engineering 3 Computation of Problems Concepts and Definitions Problems and Instances A problem or model is an infinite family of instances whose objective function and constraints have a specific structure. An instance is obtained by specifying values for the various problem parameters. Measurement of Difficulty Instance z Running time (Measure the total number of elementary operations). Problem z Best case (No guarantee about the difficulty of a given instance). z Average case (Specifies a probability distribution on the instances). z Worst case (Addresses these problems and is usually easier to analyze). University at Buffalo Department of Industrial Engineering 5 Time Complexity Θ-notation (asymptotic tight bound) fn( ) : there exist positive constants cc12, , and n 0 such that Θ=(())gn 0≤≤≤cg12 ( n ) f ( n ) cg ( n ) for all n ≥ n 0 O-notation (asymptotic upper bound) fn( ) : there -

Lecture 15: a Brief Look at PCP 1. Overview
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Basic Course on Computational Complexity Lecture 15: A Brief Look at PCP David Mix Barrington and Alexis Maciel August 4, 2000 1. Overview We come now to the strangest of our models of “efficiently provable languages", that of probabilistically checkable proofs. By a theorem of Arora and Safra, if A is any language in NP, Alice can prove to Bob that x A by giving him a proof and having him look at only a constant number of randomly2 chosen bits of it. We won't be able to prove this theorem here. Instead we will show some of its implications for optimization problems and give an overview of one example of a probabilistically checkable proof (though this won't meet the conditions of the Arora-Safra theorem). We begin with a look at optimization problems such as MAX-3SAT, where the • input is a 3CNF boolean formula and the output is the maximum number of clauses that can be satisfied by any one assignment. It is NP-hard to answer this question exactly, and we investigate the difficulty of approximating the correct answer to within some multiplicative factor. We define the notion of a probabilistically checkable proof, and the class • PCP(r(n); q(n)) of languages for which such proofs exist. The parameter r(n) refers to the number of random bits Bob can use, and q(n) refers to the num- ber of bits of the proof he is allowed to see. The PCP theorem says that NP = PCP(log n; 1).