Secure Large Scale Penetration of Electric Vehicles in the Power Grid
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

China at the Crossroads
SPECIAL REPORT China at the Crossroads Energy, Transportation, and the 21st Century James S. Cannon June 1998 INFORM, Inc. 120 Wall Street New York, NY 10005-4001 Tel (212) 361-2400 Fax (212) 361-2412 Site www.informinc.org Gina Goldstein, Editor Emily Robbins, Production Editor © 1998 by INFORM, Inc. All rights reserved. Printed in the United States of America ISSN# 1050-8953 Volume 5, Number 2 Acknowledgments INFORM is grateful to all those who contributed their time, knowledge, and perspectives to the preparation of this report. We also wish to thank ARIA Foundation, The Compton Foundation, The Overbrook Foundation, and The Helen Sperry Lea Foundation, without whose generous support this work would not have been possible. Table of Contents Preface Introduction: A Moment of Choice for China. ........................................................................1 Motor Vehicles in China: Oil and Other Options...................................................................3 Motor Vehicle Manufacturing........................................................................................................3 Oil: Supply and Demand...............................................................................................................5 Alternative Vehicles and Fuels........................................................................................................8 Natural Gas Vehicles.....................................................................................................8 Liquefied Petroleum Gas ..............................................................................................10 -
Meetings Between Representatives of DG Enterprise And
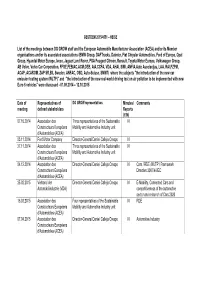
GESTDEM 2015/4551 – HEISE List of the meetings between DG GROW staff and the European Automobile Manufacturer Association (ACEA) and/or its Member organisations and/or its associated associations (BMW Group, DAFTrucks, Daimler, Fiat Chrysler Automobiles, Ford of Europe, Opel Group, Hyundai Motor Europe, Iveco, Jaguar Land Rover, PSA Peugeot Citroën, Renault, Toyota Motor Europe, Volkswagen Group, AB Volvo, Volvo Car Corporation, FFOE,FEBIAC,ACM,OEB, AIA,CCFA, VDA, AHAI, SIMI, ANFIA,Auto Asociacijas, LAA, RAI,PZPM, ACAP, ACAROM, ZAP SR,BIL Sweden, ANFAC, OSD, Auto-Suisse, SMMT) where the subjects "the introduction of the new car emission testing system (WLTP)" and "the introduction of the new real-world driving test on air pollution to be implemented with new Euro 6 vehicles" were discussed - 01.09.2014 – 12.10.2015 Date of Representatives of DG GROW representatives Minutes/ Comments meeting defined stakeholders Reports (Y/N) 07.10.2014 Association des Three representatives of the Sustainable N Constructeurs Européens Mobility and Automotive Industry unit d'Automobiles (ACEA) 03.11.2014 Ford Motor Company Director-General Daniel Calleja Crespo N 27.11.2014 Association des Three representatives of the Sustainable N Constructeurs Européens Mobility and Automotive Industry unit d'Automobiles (ACEA) 04.12.2014 Association des Director-General Daniel Calleja Crespo N Cars / RDE /WLTP / Framework Constructeurs Européens Directive 2007/46/EC d'Automobiles (ACEA) 25.02.2015 Verband der Director-General Daniel Calleja Crespo N E-Mobility, Connected -

Electric Vehicle Demonstration Projects In
ELECTRIC VEHICLE DEMONSTRATION PROJECTS IN THE UNITED STATES Prepared For TEKES The Finnish Funding Agency for Technology and Innovation NWV Market Discovery, Inc. 20781 Evergreen Mills Road · Leesburg, VA 20175, USA Tel 1-703-777-1727 · Cell 1-703-909-0603 · URL: www.nwv.com CONTENTS 1. BACKGROUND & OBJECTIVES ________________________________________ 4 2. INTRODUCTION ____________________________________________________ 6 2.1. POLITICAL CONTEXT _________________________________________________ 6 2.2. ELECTRICAL CAR MANUFACTURERS ___________________________________ 7 2.3. MUNICIPALITIES _____________________________________________________ 7 2.4. INFRASTRUCTURE ___________________________________________________ 7 2.5. TECHNOLOGY & COMPONENT SUPPLIERS______________________________ 9 2.6. RETAIL, SALES & CONSUMER SERVICE _________________________________ 9 2.7. FUNDING ___________________________________________________________ 9 2.8. INTERNATIONAL COLLABORATION ___________________________________ 10 2.9. GLOBAL INITIATIVES ________________________________________________ 10 2.10. SOURCES __________________________________________________________ 12 3. DEMONSTRATION & TEST PROJECTS _________________________________ 13 3.1. THE EV PROJECT ___________________________________________________ 13 3.2. PROJECT PLUG - IN _________________________________________________ 18 3.3. USPS PILOT PROGRAM “CONVERT LLVs TO EVs”_______________________ 23 3.4. PORT OF LOS ANGELES ELECTRIC TRUCK DEMONSTRATION PROJECTS ___ 26 3.5. SDG&E CTP EV DEMONSTRATION -

ELECTRIC VEHICLES: Ready(Ing) for Adoption
ELECTRIC VEHICLES Ready(ing) for Adoption Citi GPS: Global Perspectives & Solutions June 2018 Citi is one of the world’s largest financial institutions, operating in all major established and emerging markets. Across these world markets, our employees conduct an ongoing multi-disciplinary conversation – accessing information, analyzing data, developing insights, and formulating advice. As our premier thought leadership product, Citi GPS is designed to help our readers navigate the global economy’s most demanding challenges and to anticipate future themes and trends in a fast-changing and interconnected world. Citi GPS accesses the best elements of our global conversation and harvests the thought leadership of a wide range of senior professionals across our firm. This is not a research report and does not constitute advice on investments or a solicitations to buy or sell any financial instruments. For more information on Citi GPS, please visit our website at www.citi.com/citigps. Citi GPS: Global Perspectives & Solutions June 2018 Raghav Gupta-Chaudhary is currently the European Autos Analyst. He has been an Analyst for seven years and joined Citi's London office in July 2016 to cover European Auto Parts. Raghav previously worked at Nomura from 2011 to 2016, where he started off on the Food Retail team and later transitioned to cover the Automotive sector. He has an honours degree in Mathematics with Management Studies from UCL and is a qualified chartered accountant. +44-20-7986-2358 | [email protected] Gabriel M Adler is a Senior Associate in the Citi Research European Autos team. He is currently based in the London office and started with Citi in October 2017. -

58 Chevrolet $ Bel-Air Sport Sedan
Fage B-'j Sunday, August 'j, T TORRANCt < * L b !> Automobile* for Sal* 230 Automobiltt for Sal* 200 Automobile* for ial* 200 Automobiles for Sat* 200 Automobiles for sal* 200 Automobiles f*r * ! 100 Alltom*bilM for Sal* 200 AutemebilM f*r sal* 200 *ut*mebile« for Sal* 200 .* : - GLEDHILL HUNT RAMBLER S-L-A-S-H-E-S III PRICES! ES IT AGAIN! BREAKS ALL SALES RECORDS USED CARS NOW THE LARGEST RAMBLER DEALER IN HARBOR AREA TO CONTINUE OUR RECORD SELLING PACE WE OFFER Must Be Sold Regardless of Cost Check These Sensational Buys 1962 RAMBLERS at CLOSEOUT PRICES 59 CHEVROLET $11QR BUY NOW AND SAVE HUNDREDS OF DOLLARS! 2-DOOR...................... 11T ^ ON NEAR NEW EXECUTIVE CARS 4-cylinder, economy stick shift, radio and neater. A real beauty! 3 to choose. i '60CORVAIR $19QI% \ 1962 Rambler Classic 2-Door Custom 4-DOOR..................... latYy Stock No. 14 Stick shift. All white. Radio, h*«t*r. R*al clean and sharp! (4 to choose from) $ '60 CHEVROLET $1C Q C 2144" BEI-AIR 2-DOOR.............. 1979 Equipped with . Radio and heater, automatic transmission, V-8. Local, one owner, 2-tone. R^al n^at! '62 CHEVROLET $ fc Radio * Heater IMPALA SUPER SPORT.......... ^T Automatic Drive 4-.p.ed, all-white with red Interior. Radio, heater. Loaded! Like new, real sharp! * Whitcwalls '60 CHEVROLET Other Extras V-8 STATION WAGON 4-DOOI Iconomy stick shift, radio, heater. Ideal for vacationing family.. '59 CHEVROLET $ CONVERTIBLE............. 1495 1961 RAMBLER 2-DOOR Automatic transmission, V-8, radio and heater. Clean throughout.>ut. Real sharp! Stock No. -

Plug-In Hybrid Electric Vehicle Value Proposition Study
DOCUMENT AVAILABILITY Reports produced after January 1, 1996, are generally available free via the U.S. Department of Energy (DOE) Information Bridge: Web site: http://www.osti.gov/bridge Reports produced before January 1, 1996, may be purchased by members of the public from the following source: National Technical Information Service 5285 Port Royal Road Springfield, VA 22161 Telephone: 703-605-6000 (1-800-553-6847) TDD: 703-487-4639 Fax: 703-605-6900 E-mail: [email protected] Web site: http://www.ntis.gov/support/ordernowabout.htm Reports are available to DOE employees, DOE contractors, Energy Technology Data Exchange (ETDE) representatives, and International Nuclear Information System (INIS) representatives from the following source: Office of Scientific and Technical Information P.O. Box 62 Oak Ridge, TN 37831 Telephone: 865-576-8401 Fax: 865-576-5728 E-mail: [email protected] Web site: http://www.osti.gov/contact.html This report was prepared as an account of work sponsored by an agency of the United States Government. Neither the United States government nor any agency thereof, nor any of their employees, makes any warranty, express or implied, or assumes any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, apparatus, product, or process disclosed, or represents that its use would not infringe privately owned rights. Reference herein to any specific commercial product, process, or service by trade name, trademark, manufacturer, or otherwise, does not necessarily constitute or imply its endorsement, recommendation, or favoring by the United States Government or any agency thereof. The views and opinions of authors expressed herein do not necessarily state or reflect those of the United States Government or any agency thereof. -

Amping up Electric Vehicle Manufacturing in the PNW OPPORTUNITIES for BUSINESS, WORKFORCE, and EDUCATION
Amping Up Electric Vehicle Manufacturing in the PNW OPPORTUNITIES FOR BUSINESS, WORKFORCE, AND EDUCATION Seattle Jobs Initiative 1200 12TH AVENUE SOUTH | SEATTLE, WASHINGTON 1 Contents Contents ........................................................................................................................................................ 2 Tables ............................................................................................................................................................ 3 Figures .......................................................................................................................................................... 3 Abbreviations ................................................................................................................................................ 4 Executive Summary ...................................................................................................................................... 5 The Openings for New Business that Electric Vehicle Production Can Create ............................................ 8 Good News: The Barriers to Entry Are Lower in EV-Related Industries ................................................... 9 Who Could Enter the EV Field? The Supply Chain in More Detail ......................................................... 10 Existing and Potential Businesses in the EV-Related Industries ................................................................ 13 Identifying EV-Related Firms in Oregon and Washington ...................................................................... -

The Automobile Industry Pocket Guide 2014–2015
THE AUTOMOBILE INDUSTRY POCKEt guide 2014–2015 The Automobile Industry Pocket Guide published by ACEA Communications department Please order your personal copy via [email protected] This paper is made in an environmentally-friendly way and according to FSC certification © ACEA_SEPTEMBER 2014 THE AUTOMOBILE INDUSTRY POCKEt guide 2014–2015 Foreword The European Automobile Manufacturers’ Association (ACEA) produces this Pocket Guide annually in order to provide a clear overview of the main characteristics of one of Europe’s key industries. These statistics show an industry that continues to provide employment and mobility for Europe’s citizens, generate tax and trade revenue for governments, and lead the world in terms of innovation. In 2013, around 13.6 million new cars, vans, trucks and buses were registered in the EU. Sales have dropped by over a quarter since the pre-crisis peak in 2007, but things are now gradually improving. With the European economy slowly recovering, ACEA predicts that sales in Europe will recover moderately over the next few years. As one of the cornerstones of Europe’s economy, ACEA is continuing to contribute constructively to discussions with policy makers and other stakeholders in order to consolidate this growth and strengthen the global competitiveness of the automobile sector - thereby fully supporting the EU’s industrial renaissance. ACEA believes that the right policy environment can deliver this – that means a policy environment that is based on three building blocks: driving innovation, fostering -

Manufacturers' Zone Offices
Vehicle Manufacturer – Contact Information MANUFACTURER NAME ADDRESS TELEPHONE # FAX # Acura (See American Honda) American Honda Motor Co., Inc. Acura Mediation Department 1919 Torrance BLVD 800-999-1009 310.533.5537 Honda Torrance, CA 90501 Audi of America, Inc. Customer Care 3499 West Hamlin 800-822-2834 248.754.6504 Rochester Hills, MI 48309 BMW of North America, Inc. P.O. Box 1227 201-307-4000 201.307.9286 MINI USA Westwood, NJ 07675 800-831-1117 201.930.8484 The Braun Corporation 631 W. 11th St. 800-488-0359 574.946.3143 Winamac, IN 46996 Coachmen RV 423 N. Main St. 574.825.5821 574.825.7868 Middlebury, IN 46540 FCA US LLC f/k/a Chrysler Group LLC RoseWaldorf PLLC 501 New Karner Road 800.381.3316 518.869.3334 Albany, New York 12205 Ford Motor Company Consumer Affairs P.O. Box 1270 800.392.3673 866.567.6519 Melbourne, FL 32902 Last updated on 5/19/2015 Page 1 Vehicle Manufacturer – Contact Information MANUFACTURER NAME ADDRESS TELEPHONE # FAX # GENERAL MOTORS LLC Buick Motor Division P.O. Box 33136 800.231.1841 866.480.3633 Detroit, MI 48232-5136 Cadillac Motor Car Division P.O. Box 33169 800.231.1841 866.480.3633 Detroit, MI 48232-5169 Chevrolet Motor Division P.O. Box 33170 800.231.1841 866.480.3633 Detroit, MI 48232-5170 Hummer H2/H3 P.O. Box 33177 800.231.1841 866.480.3633 Detroit, MI 48232-5177 Oldsmobile Division P.O. Box 33171 800.231.1841 866.480.3633 Detroit, MI 48232-5171 Pontiac/GMC Division P.O. -

1994 Pontiac Bonneville
PONTIAC i IS94 EONNEVILLE OWNER'S MANUAL 1994 Owner’s Manual pPontiac Bonneville Table of Contents Introduction HOWto Use This Manual ............ Part I Seats & Restraint Systems ........... 7L Part 2 Features & Controls ............... 41 c Part 3 Comfort Controls & Audio Systems . I I I I Part 4 Your Driving and the Road ......... 137 E Part 5 Problems on the Road ............. 165 Part 6 Service & Appearance Care ........ 193 I Part 7 MaintenanceSchedule ............ 247 E Part 8 Customer Assistance Information . 265 Includes “Reporting Safety Defects” on page 269. Part9 Index ........................... 279 I Service Station Information .. Last Page Printed in USA 10260958 A Second Edition ... Important Notes About thisManual Please keep this manual in your Pontiac, so it will be there if you ever need it when you’re on the road. If YOU sell the vehicle, please leave this manual in it so the new owner can use it. This manual includes the latest information at the time it was printed. We reserve the right to make changes in the product after that time without further notice. Note to Canadian Owners For vehicles first sold in Canada, substitute the name “General Motors of Canada Limited” for Pontiac Division wheneverit appears in this manual. For Canadian Owners Who Prefer a French Language Manual: Aux proprietaires canadiens: Vous pouvez vous procurer un exemplaire de ce guide en franGais chez votre concessionaire ou au DGN Marketing Services Ltd., 1500 Bonhill Rd., Mississauga, Ontario L5T 1C7. Published by Pontiac Division GM and the GM Embiem, Pontiac, the Pontiac Emblem General Motors Corporation and the name Bonneville are registered trademarks of General Motors Corporation. -

Tomorrow Today
ROADS REPORT Tomorrow today The days of dreaming about three-wheeled electric cars, million-mile trucks and robots in wooden shoes are over An affair to remember the car’s front wheels, giving the ZAP enough A Wisconsin man’s 1991 truck zip to go from 0 to 60 mph in just 5.7 sec- has gone through four radia- onds, even faster than a Porsche Boxster. tors, three gas tanks, fi ve trans- The Alias is expected to be in production missions, six water pumps and next year and will cost around $30,000. more than 300 Now sure, three-wheeled tune-ups. But electric cars are great, but what it’s no lemon. All about those rugged individual- that work adds ists who need a vehicle they can BY DAVID up to a very im- The developer of drive over the fallen trees and MATTHEWS pressive fi gure: 1 the TankPitstop landslide debris in their subur- million miles. figured that if ro- ban culs-de-sac? Frank Oresnik bots can milk cows, Not surprisingly, Hummer of Catawba, Wis., they ought to be has the solution. At the Detroit bought his 1991 able to pump gas. Auto Show in January, GM in- Chevrolet Silvera- troduced the Hummer HX, a do in 1996 with two-door Hummer convertible 41,000 miles on that runs on E85 ethanol. the odometer. He began using it for his Of course, the HX is just a con- work as a seafood delivery man, racking cept design, much like last year’s up an average of 85,000 miles a year. -

Owner's Manual
1994 TRACKER 1994 Owner’s Manual Geo Tracker Table of Contents ii : . :: Introduction How to Use This Manual 4 ;..:::;.: Part 1 Seats & RestraintSystems =.= Part 2 Features & Controls Part 3 Comfort Controls & Audio Systems Part 4 Your DrivingandtheRoad = 99 1 Part 5 Problemsthe on Road 131 I Part 6 Service & AppearanceCare 155 I PartSchedule 7 Maintenance 203 Part 8 CustomerAssistance information 233 I Including “Reporting Safety Defects” on page 236. Part 9 Index .................... ............... 243 I Service Station Information PageLast Printed in U.S.A. Part No. 10260663 A Second Edition 1 ... How to Use This Manual Important Notes aboutThis For Canadian Owners Who Prefer a Published by: Manual French Language Manual Chevrolet Motor Division Aux propriktaires canadiens: Vous pouvez Please keep this manual in your Geo, so it General Motors Corporation vous procurer un exemplaire de ce guide will be there if you ever need it when en fransais chez votre concessionaire ou au General Motors, GM and the GM you’re on the road. If you sell the vehicle, DGN Marketing Services Ltd., 1500 emblem, Chevrolet and the Chevrolet please leave this manual in it so the new Bonhill Rd., Mississauga, Ontario L5T emblem, and Geo and the Geo emblem are owner can use it. 1 C7. registered trademarks of General Motors This manual includes the latest information Corporation. at the time it was printed. We reserve the @Copyright 1993 General Motors right to make changes in the product after Corporation, Chevrolet/Geo Division. All that time without further notice. For Rights Reserved. vehicles first sold in Canada, substitute the name “General Motorsof Canada Limited” for Chevrolet Motor Division wherever it appears in this manual.