Chapter 11: Building Secure Software Lars-Helge Netland [email protected] 10.10.2005 INF329: Utvikling Av Sikre Applikasjoner Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using Frankencerts for Automated Adversarial Testing of Certificate
Using Frankencerts for Automated Adversarial Testing of Certificate Validation in SSL/TLS Implementations Chad Brubaker ∗ y Suman Janay Baishakhi Rayz Sarfraz Khurshidy Vitaly Shmatikovy ∗Google yThe University of Texas at Austin zUniversity of California, Davis Abstract—Modern network security rests on the Secure Sock- many open-source implementations of SSL/TLS are available ets Layer (SSL) and Transport Layer Security (TLS) protocols. for developers who need to incorporate SSL/TLS into their Distributed systems, mobile and desktop applications, embedded software: OpenSSL, NSS, GnuTLS, CyaSSL, PolarSSL, Ma- devices, and all of secure Web rely on SSL/TLS for protection trixSSL, cryptlib, and several others. Several Web browsers against network attacks. This protection critically depends on include their own, proprietary implementations. whether SSL/TLS clients correctly validate X.509 certificates presented by servers during the SSL/TLS handshake protocol. In this paper, we focus on server authentication, which We design, implement, and apply the first methodology for is the only protection against man-in-the-middle and other large-scale testing of certificate validation logic in SSL/TLS server impersonation attacks, and thus essential for HTTPS implementations. Our first ingredient is “frankencerts,” synthetic and virtually any other application of SSL/TLS. Server authen- certificates that are randomly mutated from parts of real cer- tication in SSL/TLS depends entirely on a single step in the tificates and thus include unusual combinations of extensions handshake protocol. As part of its “Server Hello” message, and constraints. Our second ingredient is differential testing: if the server presents an X.509 certificate with its public key. -

Anonymity in a Time of Surveillance
LESSONS LEARNED TOO WELL: ANONYMITY IN A TIME OF SURVEILLANCE A. Michael Froomkin* It is no longer reasonable to assume that electronic communications can be kept private from governments or private-sector actors. In theory, encryption can protect the content of such communications, and anonymity can protect the communicator’s identity. But online anonymity—one of the two most important tools that protect online communicative freedom—is under practical and legal attack all over the world. Choke-point regulation, online identification requirements, and data-retention regulations combine to make anonymity very difficult as a practical matter and, in many countries, illegal. Moreover, key internet intermediaries further stifle anonymity by requiring users to disclose their real names. This Article traces the global development of technologies and regulations hostile to online anonymity, beginning with the early days of the Internet. Offering normative and pragmatic arguments for why communicative anonymity is important, this Article argues that anonymity is the bedrock of online freedom, and it must be preserved. U.S. anti-anonymity policies not only enable repressive policies abroad but also place at risk the safety of anonymous communications that Americans may someday need. This Article, in addition to providing suggestions on how to save electronic anonymity, calls for proponents of anti- anonymity policies to provide stronger justifications for such policies and to consider alternatives less likely to destroy individual liberties. In -

RSA BSAFE Crypto-C 5.21 FIPS 140-1 Security Policy2.…
RSA Security, Inc. RSA™ BSAFE® Crypto-C Crypto-C Version 5.2.1 FIPS 140-1 Non-Proprietary Security Policy Level 1 Validation Revision 1.0, May 2001 © Copyright 2001 RSA Security, Inc. This document may be freely reproduced and distributed whole and intact including this Copyright Notice. Table of Contents 1 INTRODUCTION.................................................................................................................. 3 1.1 PURPOSE ............................................................................................................................. 3 1.2 REFERENCES ....................................................................................................................... 3 1.3 DOCUMENT ORGANIZATION ............................................................................................... 3 2 THE RSA BSAFE PRODUCTS............................................................................................ 5 2.1 THE RSA BSAFE CRYPTO-C TOOLKIT MODULE .............................................................. 5 2.2 MODULE INTERFACES ......................................................................................................... 5 2.3 ROLES AND SERVICES ......................................................................................................... 6 2.4 CRYPTOGRAPHIC KEY MANAGEMENT ................................................................................ 7 2.4.1 Protocol Support........................................................................................................ -
![Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019](https://docslib.b-cdn.net/cover/5245/arxiv-1911-09312v2-cs-cr-12-dec-2019-485245.webp)
Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019
Revisiting and Evaluating Software Side-channel Vulnerabilities and Countermeasures in Cryptographic Applications Tianwei Zhang Jun Jiang Yinqian Zhang Nanyang Technological University Two Sigma Investments, LP The Ohio State University [email protected] [email protected] [email protected] Abstract—We systematize software side-channel attacks with three questions: (1) What are the common and distinct a focus on vulnerabilities and countermeasures in the cryp- features of various vulnerabilities? (2) What are common tographic implementations. Particularly, we survey past re- mitigation strategies? (3) What is the status quo of cryp- search literature to categorize vulnerable implementations, tographic applications regarding side-channel vulnerabili- and identify common strategies to eliminate them. We then ties? Past work only surveyed attack techniques and media evaluate popular libraries and applications, quantitatively [20–31], without offering unified summaries for software measuring and comparing the vulnerability severity, re- vulnerabilities and countermeasures that are more useful. sponse time and coverage. Based on these characterizations This paper provides a comprehensive characterization and evaluations, we offer some insights for side-channel of side-channel vulnerabilities and countermeasures, as researchers, cryptographic software developers and users. well as evaluations of cryptographic applications related We hope our study can inspire the side-channel research to side-channel attacks. We present this study in three di- community to discover new vulnerabilities, and more im- rections. (1) Systematization of literature: we characterize portantly, to fortify applications against them. the vulnerabilities from past work with regard to the im- plementations; for each vulnerability, we describe the root cause and the technique required to launch a successful 1. -

Black-Box Security Analysis of State Machine Implementations Joeri De Ruiter
Black-box security analysis of state machine implementations Joeri de Ruiter 18-03-2019 Agenda 1. Why are state machines interesting? 2. How do we know that the state machine is implemented correctly? 3. What can go wrong if the implementation is incorrect? What are state machines? • Almost every protocol includes some kind of state • State machine is a model of the different states and the transitions between them • When receiving a messages, given the current state: • Decide what action to perform • Which message to respond with • Which state to go the next Why are state machines interesting? • State machines play a very important role in security protocols • For example: • Is the user authenticated? • Did we agree on keys? And if so, which keys? • Are we encrypting our traffic? • Every implementation of a protocol has to include the corresponding state machine • Mistakes can lead to serious security issues! State machine example Confirm transaction Verify PIN 0000 Failed Init Failed Verify PIN 1234 OK Verified Confirm transaction OK State machines in specifications • Often specifications do not explicitly contain a state machine • Mainly explained in lots of prose • Focus usually on happy flow • What to do if protocol flow deviates from this? Client Server ClientHello --------> ServerHello Certificate* ServerKeyExchange* CertificateRequest* <-------- ServerHelloDone Certificate* ClientKeyExchange CertificateVerify* [ChangeCipherSpec] Finished --------> [ChangeCipherSpec] <-------- Finished Application Data <-------> Application Data -

1 Term of Reference Reference Number TOR-VNM-2021-21
Term of Reference Reference number TOR-VNM-2021-21 (Please refer to this number in the application) Assignment title International Gender Consultant Purpose to develop a technical paper comparing legal frameworks and setting out good practices for legal recognition of gender identity/protection of the human rights of trans persons in other countries/regions. Location Home-based Contract duration 1 June 2021 – 31 August 2021 (32 working days) Contract supervision UN Women Programme Specialist UN Women Viet Nam Country Office I. Background UN Women Grounded in the vision of equality enshrined in the Charter of the United Nations, the United Nations Entity for Gender Equality and the Empowerment of Women (UN Women) works for the elimination of discrimination against women and girls; the empowerment of women; and the achievement of substantive equality between women and men. The fundamental objective of UN Women is to enhance national capacity and ownership to enable national partners to formulate gender responsive laws, policies and upscale successful strategies to deliver on national and international commitments to gender equality. UN Women Viet Nam Country Office is the chair of the UN Gender Theme Group and has been an active member of the UN Human Rights Thematic Group (HRTG) and Viet Nam UN HIV Thematic Group and acts as a leading agency in related to promoting gender equality in the national HIV response. The result under this LOA will contribute to the achievements of the following outcome and output of UN Women Viet Nam’s Annual Work Plan. - VCO Impact 3 (SP outcome 4): Women and girls live a life free from violence. -

You Really Shouldn't Roll Your Own Crypto: an Empirical Study of Vulnerabilities in Cryptographic Libraries
You Really Shouldn’t Roll Your Own Crypto: An Empirical Study of Vulnerabilities in Cryptographic Libraries Jenny Blessing Michael A. Specter Daniel J. Weitzner MIT MIT MIT Abstract A common aphorism in applied cryptography is that cryp- The security of the Internet rests on a small number of open- tographic code is inherently difficult to secure due to its com- source cryptographic libraries: a vulnerability in any one of plexity; that one should not “roll your own crypto.” In par- them threatens to compromise a significant percentage of web ticular, the maxim that complexity is the enemy of security traffic. Despite this potential for security impact, the character- is a common refrain within the security community. Since istics and causes of vulnerabilities in cryptographic software the phrase was first popularized in 1999 [52], it has been in- are not well understood. In this work, we conduct the first voked in general discussions about software security [32] and comprehensive analysis of cryptographic libraries and the vul- cited repeatedly as part of the encryption debate [26]. Conven- nerabilities affecting them. We collect data from the National tional wisdom holds that the greater the number of features Vulnerability Database, individual project repositories and in a system, the greater the risk that these features and their mailing lists, and other relevant sources for eight widely used interactions with other components contain vulnerabilities. cryptographic libraries. Unfortunately, the security community lacks empirical ev- Among our most interesting findings is that only 27.2% of idence supporting the “complexity is the enemy of security” vulnerabilities in cryptographic libraries are cryptographic argument with respect to cryptographic software. -

Security Issues in the Diffie-Hellman Key Agreement Protocol
Security Issues in the Diffie-Hellman Key Agreement Protocol Jean-Franc¸ois Raymond and Anton Stiglic Zero-Knowledge Systems Inc. jfr, anton ¡ @zeroknowledge.com Abstract Diffie-Hellman key agreement protocol [20] implementations have been plagued by serious security flaws. The attacks can be very subtle and, more often than not, have not been taken into account by protocol designers. In this summary we discuss both theoretical attacks against the Diffie-Hellman key agreement pro- tocol and attacks based on implementation details . It is hoped that computer se- curity practitioners will obtain enough information to build and design secure and efficient versions of this classic key agreement protocol. 1 Introduction In their landmark 1976 paper “New Directions in Cryptography”[20], Diffie and Hell- man present a secure key agreement protocol that can be carried out over public com- munication channels. Their protocol is still widely used to this day. Even though the protocol seems quite simple, it can be vulnerable to certain attacks. As with many cryptographic protocols, the Diffie-Hellman key agreement protocol (DH protocol) has subtle problems that cryptographers have taken many years to discover. This vulnerability is compounded by the fact that programmers often do not have a proper understanding of the security issues. In fact, bad implementations of crypto- graphic protocols are, unfortunately, common [2]. In this work, we attempt to give a comprehensive listing of attacks on the DH proto- col. This listing will, in turn, allow us to motivate protocol design decisions. Note that throughout this presentation emphasis is placed on practice. After reading this paper, one might not have an extremely detailed understanding of previous work and theoret- ical problems, but should have a very good idea about how to securely implement the DH protocol in different settings. -

Master's Thesis
Securing In-Boat CAN Communication over the Internet Using a Cell Phone as Wi-Fi Router with Limited Hardware Master's Thesis in Computer Science and Engineering RICKARD PERSSON ALESANDRO SANCHEZ Chalmers University of Technology Department of Computer Science and Engineering Gothenburg, Sweden 2015 The Author grants to Chalmers University of Technology and University of Gothen- burg the non-exclusive right to publish the Work electronically and in a non-commercial purpose make it accessible on the Internet. The Author warrants that he/she is the author to the Work, and warrants that the Work does not contain text, pictures or other material that violates copyright law. The Author shall, when transferring the rights of the Work to a third party (for example a publisher or a company), acknowledge the third party about this agreement. If the Author has signed a copyright agreement with a third party regarding the Work, the Author warrants hereby that he/she has obtained any necessary permission from this third party to let Chalmers University of Technology and University of Gothenburg store the Work electronically and make it accessible on the Internet. Securing In-Boat CAN Communication over the Internet Securing In-Boat CAN Communication over the Internet Using a Cell Phone as Wi-FI Router with Limited Hardware Rickard, Persson Alesandro, Sanchez ©Rickard Persson, June 2015 ©Alesandro Sanchez, June 2015 Examiner: Tomas Olovsson Chalmers University of Technology Department of Computer Science and Engineering SE-412 96 G¨oteborg Sweden Telephone + 46 (0)31-772 1000 Department of Computer Science and Engineering Gothenburg, Sweden June 2014 Abstract Opening a communication channel to the internal vehicle bus of pleasure boats through the Internet, offers benefits such as remote diagnostics and software update of boat components. -
Policy and Procedures for Contracting Individual Consultants
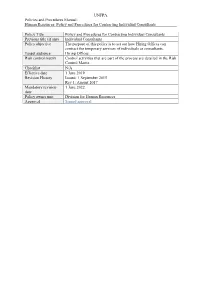
UNFPA Policies and Procedures Manual: Human Resources: Policy and Procedures for Contracting Individual Consultants Policy Title Policy and Procedures for Contracting Individual Consultants Previous title (if any) Individual Consultants Policy objective The purpose of this policy is to set out how Hiring Offices can contract the temporary services of individuals as consultants. Target audience Hiring Offices Risk control matrix Control activities that are part of the process are detailed in the Risk Control Matrix Checklist N/A Effective date 1 June 2019 Revision History Issued: 1 September 2015 Rev 1: August 2017 Mandatory revision 1 June 2022 date Policy owner unit Division for Human Resources Approval Signed approval UNFPA Policies and Procedures Manual: Human Resources: Policy and Procedures for Contracting Individual Consultants POLICY AND PROCEDURES FOR CONTRACTING INDIVIDUAL CONSULTANTS TABLE OF CONTENTS I. PURPOSE ....................................................................................................................... 1 II. POLICY ........................................................................................................................... 1 III. PROCEDURES ............................................................................................................... 2 Initiating request for individual consultant ............................................................................ 2 Verifying availability of funds .............................................................................................. -

RSA BSAFE Crypto-C Micro Edition 4.1.4 Security Policy Level 1
Security Policy 28.01.21 RSA BSAFE® Crypto-C Micro Edition 4.1.4 Security Policy Level 1 This document is a non-proprietary Security Policy for the RSA BSAFE Crypto-C Micro Edition 4.1.4 (Crypto-C ME) cryptographic module from RSA Security LLC (RSA), a Dell Technologies company. This document may be freely reproduced and distributed whole and intact including the Copyright Notice. Contents: Preface ..............................................................................................................2 References ...............................................................................................2 Document Organization .........................................................................2 Terminology .............................................................................................2 1 Crypto-C ME Cryptographic Toolkit ...........................................................3 1.1 Cryptographic Module .......................................................................4 1.2 Crypto-C ME Interfaces ..................................................................17 1.3 Roles, Services and Authentication ..............................................19 1.4 Cryptographic Key Management ...................................................20 1.5 Cryptographic Algorithms ...............................................................24 1.6 Self Tests ..........................................................................................30 2 Secure Operation of Crypto-C ME ..........................................................33 -

MPH UG 990-2417.Book
Contents Introduction--1 Content and Purpose of This Guide . 1 User Management . 2 Security--3 Security Features . 3 Authentication . 7 Encryption . 8 Creating and Installing Digital Certificates . 10 Firewalls. 15 Using the APC Security Wizard--16 Overview . 16 Create a Root Certificate and Server Certificates . 19 Create a Server Certificate and Signing Request . 23 Create an SSH Host Key . 26 Control Console Access and Security--28 Introduction . 28 Telnet and Secure SHell (SSH) . 28 Web Interface Access and Security--31 RADIUS--34 Supported RADIUS Functions and Servers . 34 Configure the Management Card or Device . 34 Configure the RADIUS Server. 36 SECURITY HANDBOOK Devices Network-Enabled Index--40 ® i Introduction Content and Purpose of This Guide This guide documents security features for firmware versions 3.x.x for APC® Network Management Cards and for devices with embedded components of APC Network Management Cards, which enable the devices to function remotely over the network. For any 2.x.x firmware release, see the security-related chapters in the User's Guide for that release. This guide documents the following protocols and features, how to select which ones are appropriate for your situation, and how to set up and use them within an overall security system: • Telnet and Secure SHell (SSH) • Secure Sockets Layer (SSL) •RADIUS • SNMPv1 and SNMPv3 In addition, this guide documents how to use the APC Security Wizard to create the components required for the high security available through SSL and SSH. SECURITY HANDBOOK Devices Network-Enabled ® 1 User Management Types of user accounts A Network Management Card or network-enabled device has three basic levels of access: • An Administrator can use all of the management menus available in the Web interface and control console.