Anonymity in a Time of Surveillance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

“Where the Internet Lives” Data Centers As Cloud Infrastructure
C HAPTER 3 “Where the Internet Lives” Data Centers as Cloud Infrastructure JN OEN IFER H LT AND PATRICK VONDERAU mblazoned with the headline “Transparency,” Google released dozens of Einterior and exterior glossy images of their data centers on the company’s website in 2012. Inviting the public to “come inside” and “see where the In- ternet lives,” Google proudly announced they would reveal “what we’re made of— inside and out” by offering virtual tours through photo galleries of the tech- nology, the people, and the places making up their data centers.1 Google’s tours showed the world a glimpse of these structures with a series of photographs showcasing “the physical Internet,” as the site characterized it. The pictures consisted mainly of slick, artful images of buildings, wires, pipes, servers, and dedicated workers who populate the centers. Apple has also put the infrastructure behind its cloud services on display for the digital audience by featuring a host of infographics, statistics, and polished inside views of the company’s “environmentally responsible” data center fa- cilities on its website.2 Facebook, in turn, features extensive photo and news coverage of its global physical infrastructure on dedicated Facebook pages, while Microsoft presents guided video tours of their server farms for free download on its corporate website.3 Even smaller data centers like those owned by Eu- ropean Internet service provider Bahnhof AB, located in Sweden, are increas- ingly on digital exhibit, with their corporate parents offering various images of server racks, cooling and power technology, or even their meeting rooms, Copyright © ${Date}. -

Anonymity and Encryption in Digital Communications, February 2015
Submission to the UN Special Rapporteur on freedom of expression – anonymity and encryption in digital communications, February 201 1! Introduction Privacy International submits this information for the Special Rapporteur's report on the use of encryption and anonymity in digital communications. Anonymity and the use of encryption in digital communications engage both the right to freedom of expression and right to privacy very closely: anonymity and encryption protects privacy, and ithout effective protection of the right to privacy, the right of individuals to communicate anonymously and ithout fear of their communications being unla fully detected cannot be guaranteed. As noted by the previous mandate holder, !rank #aRue, $the right to privacy is essential for individuals to express themselves freely. Indeed, throughout history, people%s illingness to engage in debate on controversial sub&ects in the public sphere has al ays been linked to possibilities for doing so anonymously.'( Individuals' right to privacy extends to their digital communications.) As much as they offer ne opportunities to freely communicate, the proliferation of digital communications have signi*cantly increased the capacity of states, companies and other non+state actors to interfere ith individual's privacy and free expression. Such interference ranges from mass surveillance of communications by state intelligence agencies, to systematic collection and storage of private information by internet and telecommunication companies, to cybercrime. Anonymity and encryption are essential tools available to individuals to mitigate or avert interferences ith their rights to privacy and free expression. In this ay, they are means of individuals exercising to the fullest degree their rights hen engaging in digital communications. -

RSA BSAFE Crypto-C 5.21 FIPS 140-1 Security Policy2.…
RSA Security, Inc. RSA™ BSAFE® Crypto-C Crypto-C Version 5.2.1 FIPS 140-1 Non-Proprietary Security Policy Level 1 Validation Revision 1.0, May 2001 © Copyright 2001 RSA Security, Inc. This document may be freely reproduced and distributed whole and intact including this Copyright Notice. Table of Contents 1 INTRODUCTION.................................................................................................................. 3 1.1 PURPOSE ............................................................................................................................. 3 1.2 REFERENCES ....................................................................................................................... 3 1.3 DOCUMENT ORGANIZATION ............................................................................................... 3 2 THE RSA BSAFE PRODUCTS............................................................................................ 5 2.1 THE RSA BSAFE CRYPTO-C TOOLKIT MODULE .............................................................. 5 2.2 MODULE INTERFACES ......................................................................................................... 5 2.3 ROLES AND SERVICES ......................................................................................................... 6 2.4 CRYPTOGRAPHIC KEY MANAGEMENT ................................................................................ 7 2.4.1 Protocol Support........................................................................................................ -

No. 16-3588 in the UNITED STATES COURT of APPEALS for THE
Case: 16-3588 Document: 003112605572 Page: 1 Date Filed: 04/26/2017 No. 16-3588 IN THE UNITED STATES COURT OF APPEALS FOR THE THIRD CIRCUIT ______________________ UNITED STATES OF AMERICA, Appellee v. GABRIEL WERDENE, Appellant ______________________ On Appeal from the United States District Court for the Eastern District of Pennsylvania ______________________ BRIEF OF AMICUS CURIAE PRIVACY INTERNATIONAL IN SUPPORT OF APPELLANT AND IN SUPPORT OF REVERSAL OF THE DECISION BELOW ______________________ Of counsel: Caroline Wilson Palow* Lisa A. Mathewson Scarlet Kim* The Law Offices of PRIVACY INTERNATIONAL Lisa A. Mathewson, LLC 62 Britton Street 123 South Broad Street, Suite 810 London EC1M 5UY Philadelphia, PA 19109 Phone: +44 (0) 20 3422 4321 Phone: (215) 399-9592 [email protected] [email protected] Counsel for Amicus Curiae, *Counsel not admitted to Third Circuit Bar Privacy International Case: 16-3588 Document: 003112605572 Page: 2 Date Filed: 04/26/2017 CORPORATE DISCLOSURE STATEMENT Pursuant to Federal Rule of Appellate Procedure 26.1 and Local Appellate Rule 26.1.1, amicus curiae Privacy International certifies that it does not have a parent corporation and that no publicly held corporation owns 10% or more of its stock. i Case: 16-3588 Document: 003112605572 Page: 3 Date Filed: 04/26/2017 TABLE OF CONTENTS TABLE OF AUTHORITIES ................................................................................... iii STATEMENT OF INTEREST ................................................................................. -

Aiding Surveillance an Exploration of How Development and Humanitarian Aid Initiatives Are Enabling Surveillance in Developing Countries
Privacy International Aiding Surveillance An exploration of how development and humanitarian aid initiatives are enabling surveillance in developing countries Gus Hosein and Carly Nyst 01 October 2013 www.privacyinternational.org Aiding Surveillance — Privacy International Contents Executive Summary 04 Section 1 Introduction 05 Section 2 Methodology 15 Section 3 Management Information Systems 17 and electronic transfers Section 4 Digital identity registration and biometrics 28 Section 5 Mobile phones and data 42 Section 6 Border surveillance and security 50 Section 7 Development at the expense of human rights? 56 The case for caution Endnotes 59 03/80 Aiding Surveillance — Privacy International Executive Summary Information technology transfer is increasingly a crucial element of development and humanitarian aid initiatives. Social protection programmes are incorporating digitised Management Information Systems and electronic transfers, registration and electoral systems are deploying biometric technologies, the proliferation of mobile phones is facilitating access to increased amounts of data, and technologies are being transferred to support security and rule of law efforts. Many of these programmes and technologies involve the surveillance of individuals, groups, and entire populations. The collection and use of personal information in these development and aid initiatives is without precedent, and subject to few legal safeguards. In this report we show that as development and humanitarian donors and agencies rush to adopt new technologies that facilitate surveillance, they may be creating and supporting systems that pose serious threats to individuals’ human rights, particularly their right to privacy. 04/80 Section 1 Aiding Surveillance — Privacy International Introduction 1.0 It is hard to imagine a current public policy arena that does not incorporate new technologies in some way, whether in the planning, development, deployment, or evaluation phases. -
![Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019](https://docslib.b-cdn.net/cover/5245/arxiv-1911-09312v2-cs-cr-12-dec-2019-485245.webp)
Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019
Revisiting and Evaluating Software Side-channel Vulnerabilities and Countermeasures in Cryptographic Applications Tianwei Zhang Jun Jiang Yinqian Zhang Nanyang Technological University Two Sigma Investments, LP The Ohio State University [email protected] [email protected] [email protected] Abstract—We systematize software side-channel attacks with three questions: (1) What are the common and distinct a focus on vulnerabilities and countermeasures in the cryp- features of various vulnerabilities? (2) What are common tographic implementations. Particularly, we survey past re- mitigation strategies? (3) What is the status quo of cryp- search literature to categorize vulnerable implementations, tographic applications regarding side-channel vulnerabili- and identify common strategies to eliminate them. We then ties? Past work only surveyed attack techniques and media evaluate popular libraries and applications, quantitatively [20–31], without offering unified summaries for software measuring and comparing the vulnerability severity, re- vulnerabilities and countermeasures that are more useful. sponse time and coverage. Based on these characterizations This paper provides a comprehensive characterization and evaluations, we offer some insights for side-channel of side-channel vulnerabilities and countermeasures, as researchers, cryptographic software developers and users. well as evaluations of cryptographic applications related We hope our study can inspire the side-channel research to side-channel attacks. We present this study in three di- community to discover new vulnerabilities, and more im- rections. (1) Systematization of literature: we characterize portantly, to fortify applications against them. the vulnerabilities from past work with regard to the im- plementations; for each vulnerability, we describe the root cause and the technique required to launch a successful 1. -

Black-Box Security Analysis of State Machine Implementations Joeri De Ruiter
Black-box security analysis of state machine implementations Joeri de Ruiter 18-03-2019 Agenda 1. Why are state machines interesting? 2. How do we know that the state machine is implemented correctly? 3. What can go wrong if the implementation is incorrect? What are state machines? • Almost every protocol includes some kind of state • State machine is a model of the different states and the transitions between them • When receiving a messages, given the current state: • Decide what action to perform • Which message to respond with • Which state to go the next Why are state machines interesting? • State machines play a very important role in security protocols • For example: • Is the user authenticated? • Did we agree on keys? And if so, which keys? • Are we encrypting our traffic? • Every implementation of a protocol has to include the corresponding state machine • Mistakes can lead to serious security issues! State machine example Confirm transaction Verify PIN 0000 Failed Init Failed Verify PIN 1234 OK Verified Confirm transaction OK State machines in specifications • Often specifications do not explicitly contain a state machine • Mainly explained in lots of prose • Focus usually on happy flow • What to do if protocol flow deviates from this? Client Server ClientHello --------> ServerHello Certificate* ServerKeyExchange* CertificateRequest* <-------- ServerHelloDone Certificate* ClientKeyExchange CertificateVerify* [ChangeCipherSpec] Finished --------> [ChangeCipherSpec] <-------- Finished Application Data <-------> Application Data -

Privacy International, Human and Digital Rights Organizations, and International Legal Scholars As Amici Curiae in Support of Respondent
No. 17-2 IN THE Supreme Court of the United States IN THE MdATTER OF A WARRANT TO SEARCH A CERTAIN EMAIL ACCOUNT CONTROLLED AND MAINTAINED BY MICROSOFT CORPORATION UNITED STATES OF AMERICA, Petitioner, —v.— MICROSOFT CORPORATION, Respondent. ON WRIT OF CERTIORARI TO THE UNITED STATES COURT OF APPEALS FOR THE SECOND CIRCUIT BRIEF OF PRIVACY INTERNATIONAL, HUMAN AND DIGITAL RIGHTS ORGANIZATIONS, AND INTERNATIONAL LEGAL SCHOLARS AS AMICI CURIAE IN SUPPORT OF RESPONDENT LAUREN GALLO WHITE BRIAN M. WILLEN RYAN T. O’HOLLAREN Counsel of Record WILSON, SONSINI, GOODRICH BASTIAAN G. SUURMOND & ROSATI, P.C. WILSON, SONSINI, GOODRICH One Market Plaza Spear Tower, & ROSATI, P.C. Suite 3300 1301 Avenue of the Americas, San Francisco, California 94105 40th Floor (415) 947-2000 New York, New York 10019 [email protected] (212) 999-5800 [email protected] [email protected] [email protected] Attorneys for Amici Curiae (Counsel continued on inside cover) CAROLINE WILSON PALOW SCARLET KIM PRIVACY INTERNATIONAL 62 Britton Street London, EC1M 5UY United Kingdom [email protected] [email protected] i QUESTION PRESENTED Whether construing the Stored Communications Act (“SCA”) to authorize the seizure of data stored outside the United States would conflict with foreign data-protection laws, including those of Ireland and the European Union, and whether these conflicts should be avoided by applying established canons of construction, including presumptions against extra- territoriality and in favor of international comity, which direct U.S. courts to construe statutes as applying only domestically and consistently with foreign laws, absent clear Congressional intent. ii TABLE OF CONTENTS PAGE QUESTION PRESENTED .......................... -

1 Term of Reference Reference Number TOR-VNM-2021-21
Term of Reference Reference number TOR-VNM-2021-21 (Please refer to this number in the application) Assignment title International Gender Consultant Purpose to develop a technical paper comparing legal frameworks and setting out good practices for legal recognition of gender identity/protection of the human rights of trans persons in other countries/regions. Location Home-based Contract duration 1 June 2021 – 31 August 2021 (32 working days) Contract supervision UN Women Programme Specialist UN Women Viet Nam Country Office I. Background UN Women Grounded in the vision of equality enshrined in the Charter of the United Nations, the United Nations Entity for Gender Equality and the Empowerment of Women (UN Women) works for the elimination of discrimination against women and girls; the empowerment of women; and the achievement of substantive equality between women and men. The fundamental objective of UN Women is to enhance national capacity and ownership to enable national partners to formulate gender responsive laws, policies and upscale successful strategies to deliver on national and international commitments to gender equality. UN Women Viet Nam Country Office is the chair of the UN Gender Theme Group and has been an active member of the UN Human Rights Thematic Group (HRTG) and Viet Nam UN HIV Thematic Group and acts as a leading agency in related to promoting gender equality in the national HIV response. The result under this LOA will contribute to the achievements of the following outcome and output of UN Women Viet Nam’s Annual Work Plan. - VCO Impact 3 (SP outcome 4): Women and girls live a life free from violence. -

Gender Perspectives on Privacy’
September 2018 Privacy International’s submission on the consultation ‘Gender perspectives on privacy’ In response to the consultation on ‘Gender perspectives on Privacy’ by the UN Special Rapporteur on the right to privacy, Privacy International submit the following observations. The organisation is publishing in October 2018 a report on the topic, which it will share with the Rapporteur as soon as it is released. 1. What gender issues arise in the digital era in the Thematic Action Streams (Privacy and Personality; Security and Surveillance; Big Data and Open Data; Health Data, and the Use of Personal Data by Corporations)? What challenges need to be addressed and what positives can be promoted more widely? As a necessary condition to define boundaries, protect human dignity and enable autonomy, the right to privacy can be particularly important for women and queer persons, influencing most aspect of their lives, preventing them from being victims of discrimination, unwanted exposure, unlawful surveillance, and harassment, among other harms. A gender perspective is also necessary to address power imbalances in the exercise of the right to privacy, making sure that it does not become an excuse from providing proper redress when this right is affected. Within that context, we would like to draw your attention to particular issues and challenges that we believe should be addressed. Previous research on the topic, as well as our on-going research, document a reality in which traditional systems of oppression that are based on gender discrimination can find new manifestations in the information age. Of particular concern to us is the issue of online gender-based violence. -
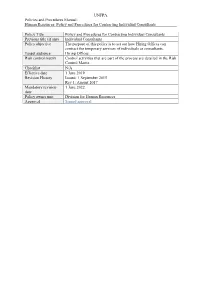
Policy and Procedures for Contracting Individual Consultants
UNFPA Policies and Procedures Manual: Human Resources: Policy and Procedures for Contracting Individual Consultants Policy Title Policy and Procedures for Contracting Individual Consultants Previous title (if any) Individual Consultants Policy objective The purpose of this policy is to set out how Hiring Offices can contract the temporary services of individuals as consultants. Target audience Hiring Offices Risk control matrix Control activities that are part of the process are detailed in the Risk Control Matrix Checklist N/A Effective date 1 June 2019 Revision History Issued: 1 September 2015 Rev 1: August 2017 Mandatory revision 1 June 2022 date Policy owner unit Division for Human Resources Approval Signed approval UNFPA Policies and Procedures Manual: Human Resources: Policy and Procedures for Contracting Individual Consultants POLICY AND PROCEDURES FOR CONTRACTING INDIVIDUAL CONSULTANTS TABLE OF CONTENTS I. PURPOSE ....................................................................................................................... 1 II. POLICY ........................................................................................................................... 1 III. PROCEDURES ............................................................................................................... 2 Initiating request for individual consultant ............................................................................ 2 Verifying availability of funds .............................................................................................. -

Bredband2 I Sk'navien Reason: In-Depth Research Company Sponsored Research Rooted in Fibre, and a Market Contender Not Rated
Equity Research - 06 April 2020 23:52 CET Bredband2 i Sk'navien Reason: In-depth research Company sponsored research Rooted in fibre, and a market contender Not rated Market not yet saturated, but growth likely to slow Estimate changes (%) Strong track record, ’19-’22e sales CAGR of 7% 2020e 2021e 2022e We see a fair value range of SEK 0.95-1.83/share Sales -1.2% -1.5% -1.5% EBIT (rep) -3.7% -9.6% -10.4% Fibre remains the superior internet connection alternative EPS (rep) -3.7% -9.6% -10.4% Our analysis focuses on the fibre landscape and how Bredband2 – a Source: ABG Sundal Collier pure fibre-oriented operator – contends in this market. Based on a Share price (SEK) 06/04/2020 1.3 recently report (27 March 2020) from Post och Telestyrelsen (PTS), fibre accounted for 69% of Sweden’s broadband subscriptions in H1’19 vs. Telecommunication Services, Sweden 67% in H2’18. This has expanded rapidly in recent years (up from 49% in BRE2.ST/BRE2 SS 2015) on the back of significant advantages vs. COAX/xDSL as well as large investments in the area. We argue that this will continue to support MCap (SEKm) 876 further market growth, but at a slower rate as fibre deployment gradually MCap (EURm) 79.7 matures. Net debt (EURm) -16 We see relatively low impact from COVID-19 No. of shares (m) 701 While the number of subscriptions is important for sales growth, Free float (%) 70.0 increasing the ARPU is just as important. Bredband2 has historically Av.