Lattices, Linear Codes, and Invariants, Part II Noam D
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Topological Modes in Dual Lattice Models
Topological Modes in Dual Lattice Models Mark Rakowski 1 Dublin Institute for Advanced Studies, 10 Burlington Road, Dublin 4, Ireland Abstract Lattice gauge theory with gauge group ZP is reconsidered in four dimensions on a simplicial complex K. One finds that the dual theory, formulated on the dual block complex Kˆ , contains topological modes 2 which are in correspondence with the cohomology group H (K,Zˆ P ), in addition to the usual dynamical link variables. This is a general phenomenon in all models with single plaquette based actions; the action of the dual theory becomes twisted with a field representing the above cohomology class. A similar observation is made about the dual version of the three dimensional Ising model. The importance of distinct topological sectors is confirmed numerically in the two di- 1 mensional Ising model where they are parameterized by H (K,Zˆ 2). arXiv:hep-th/9410137v1 19 Oct 1994 PACS numbers: 11.15.Ha, 05.50.+q October 1994 DIAS Preprint 94-32 1Email: [email protected] 1 Introduction The use of duality transformations in statistical systems has a long history, beginning with applications to the two dimensional Ising model [1]. Here one finds that the high and low temperature properties of the theory are related. This transformation has been extended to many other discrete models and is particularly useful when the symmetries involved are abelian; see [2] for an extensive review. All these studies have been confined to hypercubic lattices, or other regular structures, and these have rather limited global topological features. Since lattice models are defined in a way which depends clearly on the connectivity of links or other regions, one expects some sort of topological effects generally. -

The Observability of the Fibonacci and the Lucas Cubes
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Discrete Mathematics 255 (2002) 55–63 www.elsevier.com/locate/disc The observability of the Fibonacci and the Lucas cubes Ernesto DedÃo∗;1, Damiano Torri1, Norma Zagaglia Salvi1 Dipartimento di Matematica, Politecnico di Milano, Piazza Leonardo da Vinci 32, 20133 Milano, Italy Received 5 April 1999; received inrevised form 31 July 2000; accepted 8 January2001 Abstract The Fibonacci cube n is the graph whose vertices are binary strings of length n without two consecutive 1’s and two vertices are adjacent when their Hamming distance is exactly 1. If the binary strings do not contain two consecutive 1’s nora1intheÿrst and in the last position, we obtainthe Lucas cube Ln. We prove that the observability of n and Ln is n, where the observability of a graph G is the minimum number of colors to be assigned to the edges of G so that the coloring is proper and the vertices are distinguished by their color sets. c 2002 Elsevier Science B.V. All rights reserved. MSC: 05C15; 05A15 Keywords: Fibonacci cube; Fibonacci number; Lucas number; Observability 1. Introduction A Fibonacci string of order n is a binary string of length n without two con- secutive ones. Let and ÿ be binary strings; then ÿ denotes the string obtained by concatenating and ÿ. More generally, if S is a set of strings, then Sÿ = {ÿ: ∈ S}. If Cn denotes the set of the Fibonacci strings of order n, then Cn+2 =0Cn+1 +10Cn and |Cn| = Fn, where Fn is the nth Fibonacci number. -

On Hardy's Apology Numbers
ON HARDY’S APOLOGY NUMBERS HENK KOPPELAAR AND PEYMAN NASEHPOUR Abstract. Twelve well known ‘Recreational’ numbers are generalized and classified in three generalized types Hardy, Dudeney, and Wells. A novel proof method to limit the search for the numbers is exemplified for each of the types. Combinatorial operators are defined to ease programming the search. 0. Introduction “Recreational Mathematics” is a broad term that covers many different areas including games, puzzles, magic, art, and more [31]. Some may have the impres- sion that topics discussed in recreational mathematics in general and recreational number theory, in particular, are only for entertainment and may not have an ap- plication in mathematics, engineering, or science. As for the mathematics, even the simplest operation in this paper, i.e. the sum of digits function, has application outside number theory in the domain of combinatorics [13, 26, 27, 28, 34] and in a seemingly unrelated mathematical knowledge domain: topology [21, 23, 15]. Pa- pers about generalizations of the sum of digits function are discussed by Stolarsky [38]. It also is a surprise to see that another topic of this paper, i.e. Armstrong numbers, has applications in “data security” [16]. In number theory, functions are usually non-continuous. This inhibits solving equations, for instance, by application of the contraction mapping principle because the latter is normally for continuous functions. Based on this argument, questions about solving number-theoretic equations ramify to the following: (1) Are there any solutions to an equation? (2) If there are any solutions to an equation, then are finitely many solutions? (3) Can all solutions be found in theory? (4) Can one in practice compute a full list of solutions? arXiv:2008.08187v1 [math.NT] 18 Aug 2020 The main purpose of this paper is to investigate these constructive (or algorith- mic) problems by the fixed points of some special functions of the form f : N N. -

Figurate Numbers
Figurate Numbers by George Jelliss June 2008 with additions November 2008 Visualisation of Numbers The visual representation of the number of elements in a set by an array of small counters or other standard tally marks is still seen in the symbols on dominoes or playing cards, and in Roman numerals. The word "calculus" originally meant a small pebble used to calculate. Bear with me while we begin with a few elementary observations. Any number, n greater than 1, can be represented by a linear arrangement of n counters. The cases of 1 or 0 counters can be regarded as trivial or degenerate linear arrangements. The counters that make up a number m can alternatively be grouped in pairs instead of ones, and we find there are two cases, m = 2.n or 2.n + 1 (where the dot denotes multiplication). Numbers of these two forms are of course known as even and odd respectively. An even number is the sum of two equal numbers, n+n = 2.n. An odd number is the sum of two successive numbers 2.n + 1 = n + (n+1). The even and odd numbers alternate. Figure 1. Representation of numbers by rows of counters, and of even and odd numbers by various, mainly symmetric, formations. The right-angled (L-shaped) formation of the odd numbers is known as a gnomon. These do not of course exhaust the possibilities. 1 2 3 4 5 6 7 8 9 n 2 4 6 8 10 12 14 2.n 1 3 5 7 9 11 13 15 2.n + 1 Triples, Quadruples and Other Forms Generalising the divison into even and odd numbers, the counters making up a number can of course also be grouped in threes or fours or indeed any nonzero number k. -

Fibonacci's Perfect Spiral
Middle School Fibonacci's Perfect Spiral This l esson was created to combine math history, math, critical thinking, and art. Students will l earn about Fibonacci, the code he created, and how the Fibonacci sequence relates to real l ife and the perfect spiral. Students will practice drawing perfect spirals and l earn how patterns are a mathematical concept that surrounds us i n real l ife. This l esson i s designed to take 3 to 4 class periods of 45 minutes each, depending on the students’ focus and depth of detail i n the assignments. Common Core CCSS.MATH.CONTENT.HSF.IF.A.3 Recognize that Standards: sequences are functions, sometimes defined recursively, whose domain i s a subset of the i ntegers. For example, the Fibonacci sequence i s defined recursively by f(0) = f(1) = 1, f(n+1) = f(n) + f(n1) for n ≥ 1. CCSS.MATH.CONTENT.7.EE.B.4 Use variables to represent quantities i n a realworld or mathematical problem, and construct simple equations and inequalities to solve problems by reasoning about the quantities. CCSS.MATH.CONTENT.7.G.A.1 Solve problems involving scale drawings of geometric figures, i ncluding computing actual l engths and areas from a scale drawing and reproducing a scale drawing at a different scale. CCSS.MATH.CONTENT.7.G.A.2 Draw (freehand, with ruler and protractor, and with technology) geometric shapes with given conditions. CCSS.MATH.CONTENT.8.G.A.2 Understand that a twodimensional figure i s congruent to another i f the second can be obtained from the first by a sequence of rotations, reflections, and translations; given two congruent figures, describe a sequence that exhibits the congruence between them. -

The Mathematics of Lattices
The Mathematics of Lattices Daniele Micciancio January 2020 Daniele Micciancio (UCSD) The Mathematics of Lattices Jan 2020 1 / 43 Outline 1 Point Lattices and Lattice Parameters 2 Computational Problems Coding Theory 3 The Dual Lattice 4 Q-ary Lattices and Cryptography Daniele Micciancio (UCSD) The Mathematics of Lattices Jan 2020 2 / 43 Point Lattices and Lattice Parameters 1 Point Lattices and Lattice Parameters 2 Computational Problems Coding Theory 3 The Dual Lattice 4 Q-ary Lattices and Cryptography Daniele Micciancio (UCSD) The Mathematics of Lattices Jan 2020 3 / 43 Key to many algorithmic applications Cryptanalysis (e.g., breaking low-exponent RSA) Coding Theory (e.g., wireless communications) Optimization (e.g., Integer Programming with fixed number of variables) Cryptography (e.g., Cryptographic functions from worst-case complexity assumptions, Fully Homomorphic Encryption) Point Lattices and Lattice Parameters (Point) Lattices Traditional area of mathematics ◦ ◦ ◦ Lagrange Gauss Minkowski Daniele Micciancio (UCSD) The Mathematics of Lattices Jan 2020 4 / 43 Point Lattices and Lattice Parameters (Point) Lattices Traditional area of mathematics ◦ ◦ ◦ Lagrange Gauss Minkowski Key to many algorithmic applications Cryptanalysis (e.g., breaking low-exponent RSA) Coding Theory (e.g., wireless communications) Optimization (e.g., Integer Programming with fixed number of variables) Cryptography (e.g., Cryptographic functions from worst-case complexity assumptions, Fully Homomorphic Encryption) Daniele Micciancio (UCSD) The Mathematics of Lattices Jan 2020 4 / 43 Point Lattices and Lattice Parameters Lattice Cryptography: a Timeline 1982: LLL basis reduction algorithm Traditional use of lattice algorithms as a cryptanalytic tool 1996: Ajtai's connection Relates average-case and worst-case complexity of lattice problems Application to one-way functions and collision resistant hashing 2002: Average-case/worst-case connection for structured lattices. -

Student Task Statements (8.7.B.3)
GRADE 8 MATHEMATICS BY NAME DATE PERIOD Unit 7, Lesson 3: Powers of Powers of 10 Let's look at powers of powers of 10. 3.1: Big Cube What is the volume of a giant cube that measures 10,000 km on each side? 3.2: Taking Powers of Powers of 10 1. a. Complete the table to explore patterns in the exponents when raising a power of 10 to a power. You may skip a single box in the table, but if you do, be prepared to explain why you skipped it. expression expanded single power of 10 b. If you chose to skip one entry in the table, which entry did you skip? Why? 2. Use the patterns you found in the table to rewrite as an equivalent expression with a single exponent, like . GRADE 8 MATHEMATICS BY NAME DATE PERIOD 3. If you took the amount of oil consumed in 2 months in 2013 worldwide, you could make a cube of oil that measures meters on each side. How many cubic meters of oil is this? Do you think this would be enough to fill a pond, a lake, or an ocean? 3.3: How Do the Rules Work? Andre and Elena want to write with a single exponent. • Andre says, “When you multiply powers with the same base, it just means you add the exponents, so .” • Elena says, “ is multiplied by itself 3 times, so .” Do you agree with either of them? Explain your reasoning. Are you ready for more? . How many other whole numbers can you raise to a power and get 4,096? Explain or show your reasoning. -

Electromagnetic Duality for Children
Electromagnetic Duality for Children JM Figueroa-O'Farrill [email protected] Version of 8 October 1998 Contents I The Simplest Example: SO(3) 11 1 Classical Electromagnetic Duality 12 1.1 The Dirac Monopole ....................... 12 1.1.1 And in the beginning there was Maxwell... 12 1.1.2 The Dirac quantisation condition . 14 1.1.3 Dyons and the Zwanziger{Schwinger quantisation con- dition ........................... 16 1.2 The 't Hooft{Polyakov Monopole . 18 1.2.1 The bosonic part of the Georgi{Glashow model . 18 1.2.2 Finite-energy solutions: the 't Hooft{Polyakov Ansatz . 20 1.2.3 The topological origin of the magnetic charge . 24 1.3 BPS-monopoles .......................... 26 1.3.1 Estimating the mass of a monopole: the Bogomol'nyi bound ........................... 27 1.3.2 Saturating the bound: the BPS-monopole . 28 1.4 Duality conjectures ........................ 30 1.4.1 The Montonen{Olive conjecture . 30 1.4.2 The Witten e®ect ..................... 31 1.4.3 SL(2; Z) duality ...................... 33 2 Supersymmetry 39 2.1 The super-Poincar¶ealgebra in four dimensions . 40 2.1.1 Some notational remarks about spinors . 40 2.1.2 The Coleman{Mandula and Haag{ÃLopusza¶nski{Sohnius theorems .......................... 42 2.2 Unitary representations of the supersymmetry algebra . 44 2.2.1 Wigner's method and the little group . 44 2.2.2 Massless representations . 45 2.2.3 Massive representations . 47 No central charges .................... 48 Adding central charges . 49 1 [email protected] draft version of 8/10/1998 2.3 N=2 Supersymmetric Yang-Mills . -
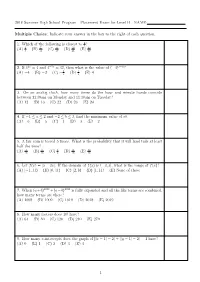
2018 Summer High School Program Placement Exam for Level B NAME
2018 Summer High School Program Placement Exam for Level B NAME: Multiple Choice: Indicate your answer in the box to the right of each question. 1 1. Which of the following is closest to 2 ? 2 7 9 10 23 (A) 3 (B) 13 (C) 19 (D) 21 (E) 48 2. If 42x = 4 and 4−5y = 32, then what is the value of (−4)x−y? 1 1 (A) −4 (B) −2 (C) − 4 (D) 4 (E) 4 3. On an analog clock, how many times do the hour and minute hands coincide between 11:30am on Monday and 11:30am on Tuesday? (A) 12 (B) 13 (C) 22 (D) 23 (E) 24 4. If −1 ≤ a ≤ 2 and −2 ≤ b ≤ 3, find the minimum value of ab. (A) −6 (B) −5 (C) −4 (D) −3 (E) −2 5. A fair coin is tossed 5 times. What is the probability that it will land tails at least half the time? 3 5 1 11 13 (A) 16 (B) 16 (C) 2 (D) 16 (E) 16 6. Let f(x) = j5 − 2xj. If the domain of f(x) is (−3; 3], what is the range of f(x)? (A) [−1; 11) (B) [0; 11) (C) [2; 8) (D) [1; 11) (E) None of these 7. When (a+b)2018 +(a−b)2018 is fully expanded and all the like terms are combined, how many terms are there? (A) 1008 (B) 1009 (C) 1010 (D) 2018 (E) 2019 8. How many factors does 10! have? (A) 64 (B) 80 (C) 120 (D) 240 (E) 270 9. -

The Enumerative Geometry of Rational and Elliptic Tropical Curves and a Riemann-Roch Theorem in Tropical Geometry
The enumerative geometry of rational and elliptic tropical curves and a Riemann-Roch theorem in tropical geometry Michael Kerber Am Fachbereich Mathematik der Technischen Universit¨atKaiserslautern zur Verleihung des akademischen Grades Doktor der Naturwissenschaften (Doctor rerum naturalium, Dr. rer. nat.) vorgelegte Dissertation 1. Gutachter: Prof. Dr. Andreas Gathmann 2. Gutachter: Prof. Dr. Ilia Itenberg Abstract: The work is devoted to the study of tropical curves with emphasis on their enumerative geometry. Major results include a conceptual proof of the fact that the number of rational tropical plane curves interpolating an appropriate number of general points is independent of the choice of points, the computation of intersection products of Psi- classes on the moduli space of rational tropical curves, a computation of the number of tropical elliptic plane curves of given genus and fixed tropical j-invariant as well as a tropical analogue of the Riemann-Roch theorem for algebraic curves. Mathematics Subject Classification (MSC 2000): 14N35 Gromov-Witten invariants, quantum cohomology 51M20 Polyhedra and polytopes; regular figures, division of spaces 14N10 Enumerative problems (combinatorial problems) Keywords: Tropical geometry, tropical curves, enumerative geometry, metric graphs. dedicated to my parents — in love and gratitude Contents Preface iii Tropical geometry . iii Complex enumerative geometry and tropical curves . iv Results . v Chapter Synopsis . vi Publication of the results . vii Financial support . vii Acknowledgements . vii 1 Moduli spaces of rational tropical curves and maps 1 1.1 Tropical fans . 2 1.2 The space of rational curves . 9 1.3 Intersection products of tropical Psi-classes . 16 1.4 Moduli spaces of rational tropical maps . -

Solve the Rubik's Cube Using Proc
Solve the Rubik’s Cube using Proc IML Jeremy Hamm Cancer Surveillance & Outcomes (CSO) Population Oncology BC Cancer Agency Overview Rubik’s Cube basics Translating the cube into linear algebra Steps to solving the cube using proc IML Proc IML examples The Rubik’s Cube 3x3x3 cube invented in 1974 by Hungarian Erno Rubik – Most popular in the 80’s – Still has popularity with speed-cubers 43x1018 permutations of the Rubik’s Cube – Quintillion Interested in discovering moves that lead to permutations of interest – or generalized permutations Generalized permutations can help solve the puzzle The Rubik’s Cube Made up of Edges and corners Pieces can permute – Squares called facets Edges can flip Corners can rotate Rubik’s Cube Basics Each move can be defined as a combination of Basic Movement Generators – each face rotated a quarter turn clockwise Eg. – Movement of front face ¼ turn clockwise is labeled as move F – ¼ turn counter clockwise is F-1 – 2 quarter turns would be F*F or F2 Relation to Linear Algebra The Rubik’s cube can represented by a Vector, numbering each facet 1-48 (excl centres). Permutations occur through matrix algebra where the basic movements are represented by Matrices Ax=b Relation to Linear Algebra Certain facets are connected and will always move together Facets will always move in a predictable fashion – Can be written as: F= (17,19,24,22) (18,21,23,20) (6,25,43,16) (7,28,42,13) (8,30,41,11) Relation to Linear Algebra Therefore, if you can keep track of which numbers are edges and which are corners, you can use a program such as SAS to mathematically determine moves which are useful in solving the puzzle – Moves that only permute or flip a few pieces at a time such that it is easy to predict what will happen Useful Group Theory Notes: – All moves of the Rubik’s cube are cyclical where the order is the number of moves needed to return to the original Eg. -

The Mathematical Beauty of Triangular Numbers
2015 HAWAII UNIVERSITY INTERNATIONAL CONFERENCES S.T.E.A.M. & EDUCATION JUNE 13 - 15, 2015 ALA MOANA HOTEL, HONOLULU, HAWAII S.T.E.A.M & EDUCATION PUBLICATION: ISSN 2333-4916 (CD-ROM) ISSN 2333-4908 (ONLINE) THE MATHEMATICAL BEAUTY OF TRIANGULAR NUMBERS MULATU, LEMMA & ET AL SAVANNAH STATE UNIVERSITY, GEORGIA DEPARTMENT OF MATHEMATICS The Mathematical Beauty Of Triangular Numbers Mulatu Lemma, Jonathan Lambright and Brittany Epps Savannah State University Savannah, GA 31404 USA Hawaii University International Conference Abstract: The triangular numbers are formed by partial sum of the series 1+2+3+4+5+6+7….+n [2]. In other words, triangular numbers are those counting numbers that can be written as Tn = 1+2+3+…+ n. So, T1= 1 T2= 1+2=3 T3= 1+2+3=6 T4= 1+2+3+4=10 T5= 1+2+3+4+5=15 T6= 1+2+3+4+5+6= 21 T7= 1+2+3+4+5+6+7= 28 T8= 1+2+3+4+5+6+7+8= 36 T9=1+2+3+4+5+6+7+8+9=45 T10 =1+2+3+4+5+6+7+8+9+10=55 In this paper we investigate some important properties of triangular numbers. Some important results dealing with the mathematical concept of triangular numbers will be proved. We try our best to give short and readable proofs. Most of the results are supplemented with examples. Key Words: Triangular numbers , Perfect square, Pascal Triangles, and perfect numbers. 1. Introduction : The sequence 1, 3, 6, 10, 15, …, n(n + 1)/2, … shows up in many places of mathematics[1] .