Annual Report 2018 3
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ransom Where?
Ransom where? Holding data hostage with ransomware May 2019 Author With the evolution of digitization and increased interconnectivity, the cyberthreat landscape has transformed from merely a security and privacy concern to a danger much more insidious by nature — ransomware. Ransomware is a type of malware that is designed to encrypt, Imani Barnes Analyst 646.572.3930 destroy or shut down networks in exchange [email protected] for a paid ransom. Through the deployment of ransomware, cybercriminals are no longer just seeking to steal credit card information and other sensitive personally identifiable information (PII). Instead, they have upped their games to manipulate organizations into paying large sums of money in exchange for the safe release of their data and control of their systems. While there are some business sectors in which the presence of this cyberexposure is overt, cybercriminals are broadening their scopes of potential victims to include targets of opportunity1 across a multitude of industries. This paper will provide insight into how ransomware evolved as a cyberextortion instrument, identify notorious strains and explain how companies can protect themselves. 1 WIRED. “Meet LockerGoga, the Ransomware Crippling Industrial Firms” March 25, 2019; https://www.wired.com/story/lockergoga-ransomware-crippling-industrial-firms/. 2 Ransom where? | May 2019 A brief history of ransomware The first signs of ransomware appeared in 1989 in the healthcare industry. An attacker used infected floppy disks to encrypt computer files, claiming that the user was in “breach of a licensing agreement,”2 and demanded $189 for a decryption key. While the attempt to extort was unsuccessful, this attack became commonly known as PC Cyborg and set the archetype in motion for future attacks. -

Crypto Ransomware Analysis and Detection Using
CRYPTO RANSOMWARE ANALYSIS AND DETECTION USING PROCESS MONITOR by ASHWINI BALKRUSHNA KARDILE Presented to the Faculty of the Graduate School of The University of Texas at Arlington in Partial Fulfillment of the Requirements for the Degree of MASTER OF SCIENCE IN COMPUTER SCIENCE THE UNIVERSITY OF TEXAS AT ARLINGTON December 2017 Copyright © by Ashwini Balkrushna Kardile 2017 All Rights Reserved ii Acknowledgements I would like to thank Dr. Ming for his timely guidance and motivation. His insights for this research were valuable. I would also like to thank my committee members Dr. David Levine and Dr. David Kung for taking out time from their schedule and attending my dissertation. I am grateful to John Podolanko; it would not have been possible without his help and support. Thank you, John, for helping me and foster my confidence. I would like to thank my colleagues for supporting me directly or indirectly. Last but not the least; I would like to thank my parents, my family and my friends for encouraging me and supporting me throughout my research. November 16, 2017 iii Abstract CRYPTO RANSOMWARE ANALYSIS AND DETECTION USING PROCESS MONITOR Ashwini Balkrushna Kardile, MS The University of Texas at Arlington, 2017 Supervising Professor: Jiang Ming Ransomware is a faster growing threat that encrypts user’s files and locks the computer and holds the key required to decrypt the files for ransom. Over the past few years, the impact of ransomware has increased exponentially. There have been several reported high profile ransomware attacks, such as CryptoLocker, CryptoWall, WannaCry, Petya and Bad Rabbit which have collectively cost individuals and companies well over a billion dollars according to FBI. -

Analysis of the Teslacrypt Family and How to Protect Against Future
Sophia Wang COMP 116 Final Project Analysis of the TeslaCrypt Family and How to Protect Against Future Ransomware/Cyber Attacks Abstract Ransomware accounts for a large majority of the malicious attacks in the cyber security world, with a company hit with a ransomware attack once every 40 seconds. There was a 300% increase in ransomware attacks from 2015 to 2016 — and it’s only going up from there. One family of Trojan-style ransomware technology that introduced itself in early 2015 is TeslaCrypt. TeslaCrypt affected Windows users from the US, Germany, Spain, Italy, France, and the United Kingdom, targeting mostly gamers. This form of ransomware would encrypt the victim’s files using a highly complicated encryption key and demand $250 to $1,000 for ransom. The creators of TeslaCrypt eventually released the master decryption key in May of 2016, so in the end the victims were able to recover their files and systems. This paper will explore the process by which the TeslaCrypt ransomware infected a system, the steps that were taken to ameliorate this issue, and what steps should be taken to avoid an incident like this in the future. Introduction Ransomware is a special form of malware that can infect a system through either encrypting and denying users access to their files, or restricting access and locking users out of their systems. Once the ransomware has the target’s files and/or system on lock, it demands a ransom be paid, usually through some form of cryptocurrency. In February of 2015, a new family of file-encrypting Trojan-style ransomware technology was introduced — TeslaCrypt. -

Newmind-Ransomware-Ebook.Pdf
Contents What Is Ransomware? ............................................................................................................................. 3 Who Is It Affecting? ................................................................................................................................. 4 Common Forms Of Ransomware .......................................................................................................... 5 Protect Yourself With These Tips: ........................................................................................................ 9 How To Handle An Infection: ................................................................................................................ 11 Your Next Step ........................................................................................................................................ 12 There’s a malware threat online, maybe lurking in your inbox or spam folder, called Ransomware. It’s been around for a while, but recent months have seen it gaining traction, under different names you may have heard, such as Cryptolocker, Cryptowall, and TeslaCrypt. What is Ransomware? One of the ways that Ransomware makes its way to end users is through a well-crafted email with an attachment. The attachment is malicious and when you click to download it, the ransomware encrypts (locks) certain types of files (.docx, .pdf, .jpg, etc) stored on local and mounted network drives, such as a server shared drive at the office. It then displays a message which offers to decrypt -

Best Practices to Protect Against Ransomware, Phishing & Email Fraud
WHITE PAPER Best Practices for Protecting Against Phishing, Ransomware and Email Fraud An Osterman Research White Paper Published April 2018 SPON Osterman Research, Inc. P.O. Box 1058 • Black Diamond • Washington • 98010-1058 • USA +1 206 683 5683 • [email protected] www.ostermanresearch.com • @mosterman Executive Summary • Various types of security threats are increasing in number and severity at a rapid pace, most notably cryptojacking malware that is focused on mining coins for the roughly 1,400 cryptocurrencies currently in use. • Organizations have been victimized by a wide range of threats and exploits, most notably phishing attacks that have penetrated corporate defenses, targeted email attacks launched from compromised accounts, and sensitive or confidential information accidentally leaked through email. • Threats are becoming more sophisticated as well-financed cybercriminal gangs develop improved variants of malware and social engineering attacks. The result is that the perceived effectiveness of current security solutions is not improving – or is actually getting worse – for many organizations. • Decision makers are most concerned about endpoints getting infected with malware through email or web browsing, user credentials being stolen through email-based phishing, and senior executives’ credentials being stolen through email-based spearphishing. • Four of the five leading concerns expressed by decision makers focus on email as the primary threat vector for cybercriminal activity, and nearly one-half of attacks are focused on account takeovers. Many organizations • Most decision makers have little confidence that their security infrastructure can adequately address infections on mobile devices, are not CEO Fraud/BEC, and preventing users personal devices from introducing malware into the corporate network. -

Society's Genome.Indb
Society’s Genome Genetic Diversity’s Role in Digital Preservation By Nathan Thompson with Bob Cone and John Kranz Copyright © 2016 by Spectra Logic Corporation All rights reserved. No part of this book may be reproduced in any form or by any electronic or mechanical means, including storage and retrieval systems—except in the case of brief quotations embodied in critical articles or reviews—without permission in writing from Spectra Logic Corporation. All product names, logos, and brands mentioned in this book are the property of their respective owners. Neither the authors nor publisher claim any right of ownership to such names, logos, and brands. Cover design by Kristen Coats Back cover image: Detail of “Ptolemy World Map,” from Ptolemy’s the Geography, redrawn by Francesco di Antonio del Chierco (15th century). Housed in the British Library, London. Image retrieved from https:// commons.wikimedia.org/wiki/File:PtolemyWorldMap.jpg. Published by Spectra Logic Corporation 6285 Lookout Road Boulder, Colorado 80301-3580 Tel.: 1.800.833.1132 Fax: 1.303.939.8844 www.spectralogic.com ISBN: 978-0-9975644-0-2 Second Printing Printed and bound in the United States of America 10 9 8 7 6 5 4 3 2 1 This book is printed on acid-free paper. “We are survival machines—robot vehicles blindly programmed to preserve the selfish molecules known as genes. This is a truth that still fills me with astonishment.” —Richard Dawkins, The Selfish Gene Chapter 6 Wolves at the Door Just a few years after the 9/11 attacks, the digital world began showing signs of sudden, profound change. -

Jane Hutt: Businesses That Have Received Welsh Government Grants During 2011/12
Jane Hutt: Businesses that have received Welsh Government grants during 2011/12 1 STOP FINANCIAL SERVICES 100 PERCENT EFFECTIVE TRAINING 1MTB1 1ST CHOICE TRANSPORT LTD 2 WOODS 30 MINUTE WORKOUT LTD 3D HAIR AND BEAUTY LTD 4A GREENHOUSE COM LTD 4MAT TRAINING 4WARD DEVELOPMENT LTD 5 STAR AUTOS 5C SERVICES LTD 75 POINT 3 LTD A AND R ELECTRICAL WALES LTD A JEFFERY BUILDING CONTRACTOR A & B AIR SYSTEMS LTD A & N MEDIA FINANCE SERVICES LTD A A ELECTRICAL A A INTERNATIONAL LTD A AND E G JONES A AND E THERAPY A AND G SERVICES A AND P VEHICLE SERVICES A AND S MOTOR REPAIRS A AND T JONES A B CARDINAL PACKAGING LTD A BRADLEY & SONS A CUSHLEY HEATING SERVICES A CUT ABOVE A FOULKES & PARTNERS A GIDDINGS A H PLANT HIRE LTD A HARRIES BUILDING SERVICES LTD A HIER PLUMBING AND HEATING A I SUMNER A J ACCESS PLATFORMS LTD A J RENTALS LIMITED A J WALTERS AVIATION LTD A M EVANS A M GWYNNE A MCLAY AND COMPANY LIMITED A P HUGHES LANDSCAPING A P PATEL A PARRY CONSTRUCTION CO LTD A PLUS TRAINING & BUSINES SERVICES A R ELECTRICAL TRAINING CENTRE A R GIBSON PAINTING AND DEC SERVS A R T RHYMNEY LTD A S DISTRIBUTION SERVICES LTD A THOMAS A W JONES BUILDING CONTRACTORS A W RENEWABLES LTD A WILLIAMS A1 CARE SERVICES A1 CEILINGS A1 SAFE & SECURE A19 SKILLS A40 GARAGE A4E LTD AA & MG WOZENCRAFT AAA TRAINING CO LTD AABSOLUTELY LUSH HAIR STUDIO AB INTERNET LTD ABB LTD ABER GLAZIERS LTD ABERAVON ICC ABERDARE FORD ABERGAVENNY FINE FOODS LTD ABINGDON FLOORING LTD ABLE LIFTING GEAR SWANSEA LTD ABLE OFFICE FURNITURE LTD ABLEWORLD UK LTD ABM CATERING FOR LEISURE LTD ABOUT TRAINING -
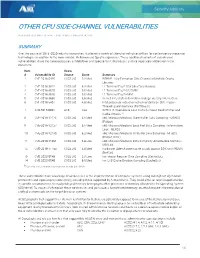
Other Cpu Side-Channel Vulnerabilities
Security Advisory OTHER CPU SIDE-CHANNEL VULNERABILITIES PUBLISHED: DECEMBER 14, 2018 | LAST UPDATE: FEBRUARY 18, 2020 SUMMARY Over the course of 2018 -2020 industry researchers disclosed a variety of side-channel vulnerabilities for contemporary processor technologies in addition to the more notable Meltdown and Spectre exposures. These additional variants of side-channel vulnerabilities share the same exposures as Meltdown and Spectre for A10 products and are separately addressed in this document. Item Score # Vulnerability ID Source Score Summary 1 CVE-2018-0495 CVSS 3.0 5.1 Med ROHNP - Key Extraction Side Channel in Multiple Crypto Libraries 2 CVE-2018-3615 CVSS 3.0 6.3 Med L1 Terminal Fault-SGX (aka Foreshadow) 3 CVE-2018-3620 CVSS 3.0 5.6 Med L1 Terminal Fault-OS/SMM 4 CVE-2018-3646 CVSS 3.0 5.6 Med L1 Terminal Fault-VMM 5 CVE-2018-3665 CVSS 3.0 5.6 Med Kernel: FPU state information leakage via lazy FPU restore 6 CVE-2018-5407 CVSS 3.0 4.8 Med Intel processor side-channel vulnerability on SMT/Hyper- Threading architectures (PortSmash) 7 A10-2019-0001 A10 Low SPOILER: Speculative Load Hazards Boost Rowhammer and Cache Attacks (i) 8 CVE-2018-12126 CVSS 3.0 6.5 Med x86: Microarchitectural Store Buffer Data Sampling - MSBDS (Fallout) 9 CVE-2018-12127 CVSS 3.0 6.5 Med x86: Microarchitectural Load Port Data Sampling - Information Leak - MLPDS 10 CVE-2018-12130 CVSS 3.0 6.2 Med x86: Microarchitectural Fill Buffer Data Sampling - MFBDS (Fallout, RIDL) 11 CVE-2019-11091 CVSS 3.0 3.8 Low x86: Microarchitectural Data Sampling Uncacheable Memory - MDSUM 12 CVE-2019-11184 CVSS 3.0 4.8 Med hardware: Side-channel cache attack against DDIO with RDMA (NetCat) 13 CVE-2020-0548 CVSS 3.0 2.3 Low hw: Vector Register Data Sampling (CacheOut) 14 CVE-2020-0549 CVSS 3.0 6.5 Med hw: L1D Cache Eviction Sampling (CacheOut) (i) Can only affect vThunder deployments on Intel Core CPUs. -

Factor Authentication
THIS COMPUTER HAS BEEN…. WHAT DO I DO NOW? Paul Seldes, FPEM, CEM, FMI ntb group, LLC Director of Operations I DON’T HAVE TO BE HERE RANSOMWARE DEFINED Ransomware is a type of malicious software used by cybercriminals that is designed to extort money from their victims, either by • Encrypting data on the disk or OR • By blocking access to the system CAN IT HAPPEN TO ME? 56% increase in ransomware attacks 2018-2019 (DHS- CISA) $84,000 typical cost of recovery $6 TRILLION cybercrime global costs by 2021 HOW IT WORKS RANSOMWARE IS A GROWTH INDUSTRY Cost of ransomware to the US in 2019 was $7.5 billion Ransomware attacks are also known as BGH 2020: $10 billion ? 2021: $15 billion? 2022: $20 billion? CRYPTOLOCKER – FIRST GLOBAL RANSOMWARE CAMPAIGN 500,000 victims Between $3 and $27 million in payments June 2014 CRYPTOLOCKER – FIRST GLOBAL RANSOMWARE CAMPAIGN There is a $3 million reward for information leading to his arrest (FBI) June 2014 AND SO IT GOES Over 100 variants between 2014 and 2019. WANNACRY – MAY 2017 WORLDWIDE ATTACK In order to spread like a worm, utilized an exploit called ETERNALBLUE, one of the leaked NSA hacking tools released by the Shadow Brokers hacking group in April 2017 The patch for the vulnerability was available for 59 days prior to the attack Hit critical infrastructure in some countries such as Germany and Russia. In the U.K., the health care sector received a hard hit: hospitals had to turn away patients, reroute ambulances, paralyze emergency services, and reschedule surgeries and appointments WANNACRY – MAY 2017 WORLDWIDE ATTACK In order to spread like a worm, utilized an exploit called ETERNALBLUE, one of the leaked NSA hacking tools released by the Shadow Brokers hacking group in April 2017 The patch for the vulnerability was available for 59 days prior to the attack Hit critical infrastructure in some countries such as Germany and Russia. -

Ultra-Clever Attacks
Security Now! Transcript of Episode #663 Page 1 of 22 Transcript of Episode #663 Ultra-Clever Attacks Description: This week we will examine two incredibly clever, new, and bad attacks named eFail and Throwhammer. But first we catch up on the rest of the past week's security and privacy news, including the evolution of UPnProxy, a worrisome flaw discovered in a very popular web development platform, the first anniversary of EternalBlue, the exploitation of those GPON routers, this week's disgusting security headshaker, a summary of the RSA Conference's security practices survey, the appearance of persistent IoT malware, a significant misconception about hard drive failure, an interesting bit of listener feedback, and then a look at two VERY clever new attacks. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-663.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-663-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson is here with all the week's news plus a couple of clever attacks - cleverly named, as well. One's called eFail, and it really is an issue if you use PGP or S/MIME to encrypt your email. The other's called Throwhammer, and I'll let Steve explain how that works. It's all coming up next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 663, recorded Tuesday, May 15th, 2018: Ultra-Clever Attacks. It's time for Security Now!, the show where we cover your security and privacy online with this guy right here, Mr. -

Efail: Breaking S/MIME and Openpgp Email Encryption Using Exfiltration Channels
Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels Damian Poddebniak and Christian Dresen, Münster University of Applied Sciences; Jens Müller, Ruhr University Bochum; Fabian Ising and Sebastian Schinzel, Münster University of Applied Sciences; Simon Friedberger, NXP Semiconductors, Belgium; Juraj Somorovsky and Jörg Schwenk, Ruhr University Bochum https://www.usenix.org/conference/usenixsecurity18/presentation/poddebniak This paper is included in the Proceedings of the 27th USENIX Security Symposium. August 15–17, 2018 • Baltimore, MD, USA ISBN 978-1-939133-04-5 Open access to the Proceedings of the 27th USENIX Security Symposium is sponsored by USENIX. Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels Damian Poddebniak1, Christian Dresen1, Jens Muller¨ 2, Fabian Ising1, Sebastian Schinzel1, Simon Friedberger3, Juraj Somorovsky2, and Jorg¨ Schwenk2 1Munster¨ University of Applied Sciences 2Ruhr University Bochum 3NXP Semiconductors, Belgium Abstract is designed to protect user data in such scenarios. With end-to-end encryption, the email infrastructure becomes OpenPGP and S/MIME are the two prime standards merely a transportation service for opaque email data and for providing end-to-end security for emails. We de- no compromise – aside from the endpoints of sender or scribe novel attacks built upon a technique we call mal- receiver – should affect the security of an end-to-end en- leability gadgets to reveal the plaintext of encrypted crypted email. emails. We use CBC/CFB gadgets to inject malicious plaintext snippets into encrypted emails. These snippets S/MIME and OpenPGP. The two most prominent stan- abuse existing and standard conforming backchannels to dards offering end-to-end encryption for email, S/MIME exfiltrate the full plaintext after decryption. -

PGP Und S/MIME: So Funktioniert Efail | Heise Security
05/12/2019 PGP und S/MIME: So funktioniert Efail | heise Security Anmelden Suchen Menü Anzeige Anzeige Die optimale Warenpräsentation Georg Haag AG WEITERE INFOS News Hintergrund Events Foren Kontakt Security > Hintergrund > PGP und S/MIME: So funktioniert Efail PGP und S/MIME: So funktioniert Efail Dienste Hintergrund 14.05.2018 16:21 Uhr – Jürgen Schmidt Security Consulter Emailcheck Netzwerkcheck Browsercheck Anti-Virus Krypto-Kampagne secIT 2020 Der Trepunkt für Security-Anwender und -Anbieter Hochkarätiges Vortragsprogramm mit Top- Referenten Über 10 Stunden redaktionelle Vorträge Die Angrie auf verschlüsselte E-Mails mit S/MIME und OpenPGP lassen sich eigentlich Über 50 Aussteller ganz einfach erklären. Wenn man sie einmal verstanden hat, weiß man auch, warum das Spannende Workshops & Expert-Talks zum mit dem Fixen nicht ganz so einfach ist. Thema IT-Sicherheit Top-Keynote: "Krypto-Papst" Bruce Schneier Ein Forscherteam rund um Sebastian Schinzel hat erfolgreiche Angrie gegen verschlüsselt verschickte E-Mails demonstriert. Dabei gelangt der Angreifer in den Besitz zumindest eines Jetzt Ticket sichern! Teils des Klartexts der Mails. Betroen sind die beiden am weitesten verbreiteten Standards für E-Mail-Verschlüsselung S/MIME und OpenPGP – und in der ein oder anderen Form nahezu Alerts! alle Alert-Meldungen » alle E-Mail-Programme. Die wichtigste Voraussetzung für einen erfolgreichen Angri ist, dass der Angreifer die verschlüsselte Mail unterwegs abfangen und manipulieren kann. Das düre Firefox, Firefox ESR, Tor Browser in vielen Fällen zutreen, in denen die Ende-zu-Ende-Verschlüsselung von PGP oder S/MIME Splunk-Plattform (Cloud, Light, eigentlich Schutz bieten soll. Enterprise) Das grundsätzliche Problem der E-Mail-Verschlüsselung ist die Tatsache, dass die E-Mails IBM Spectrum Protect Server nicht oder zumindest nicht ausreichend gegen solche Manipulationen gesichert sind.