An Abstraction Oriented Programming System for Literate Programming
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
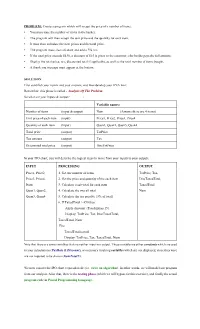
Create a Program Which Will Accept the Price of a Number of Items. • You Must State the Number of Items in the Basket
PROBLEM: Create a program which will accept the price of a number of items. • You must state the number of items in the basket. • The program will then accept the unit price and the quantity for each item. • It must then calculate the item prices and the total price. • The program must also calculate and add a 5% tax. • If the total price exceeds $450, a discount of $15 is given to the customer; else he/she pays the full amount. • Display the total price, tax, discounted total if applicable, as well as the total number of items bought. • A thank you message must appear at the bottom. SOLUTION First establish your inputs and your outputs, and then develop your IPO chart. Remember: this phase is called - Analysis Of The Problem. So what are your inputs & output? : Variable names: Number of items (input & output) Num (Assume there are 4 items) Unit price of each item (input) Price1, Price2, Price3, Price4 Quantity of each item (Input) Quan1, Quan2, Quan3, Quan4 Total price (output) TotPrice Tax amount (output) Tax Discounted total price (output) DiscTotPrice In your IPO chart, you will describe the logical steps to move from your inputs to your outputs. INPUT PROCESSING OUTPUT Price1, Price2, 1. Get the number of items TotPrice, Tax, Price3, Price4, 2. Get the price and quantity of the each item DiscTaxedTotal, Num 3. Calculate a sub-total for each item TaxedTotal Quan1, Quan2, 4. Calculate the overall total Num Quan3, Quan4 5. Calculate the tax payable {5% of total} 6. If TaxedTotal > 450 then Apply discount {Total minus 15} Display: TotPrice, Tax, DiscTaxedTotal, TaxedTotal, Num Else TaxedTotal is paid Display: TotPrice, Tax, TaxedTotal, Num Note that there are some variables that are neither input nor output. -

Knuthweb.Pdf
Literate Programming Donald E. Knuth Computer Science Department, Stanford University, Stanford, CA 94305, USA The author and his associates have been experimenting for the past several years with a program- ming language and documentation system called WEB. This paper presents WEB by example, and discusses why the new system appears to be an improvement over previous ones. I would ordinarily have assigned to student research A. INTRODUCTION assistants; and why? Because it seems to me that at last I’m able to write programs as they should be written. The past ten years have witnessed substantial improve- My programs are not only explained better than ever ments in programming methodology. This advance, before; they also are better programs, because the new carried out under the banner of “structured program- methodology encourages me to do a better job. For ming,” has led to programs that are more reliable and these reasons I am compelled to write this paper, in easier to comprehend; yet the results are not entirely hopes that my experiences will prove to be relevant to satisfactory. My purpose in the present paper is to others. propose another motto that may be appropriate for the I must confess that there may also be a bit of mal- next decade, as we attempt to make further progress ice in my choice of a title. During the 1970s I was in the state of the art. I believe that the time is ripe coerced like everybody else into adopting the ideas of for significantly better documentation of programs, and structured programming, because I couldn’t bear to be that we can best achieve this by considering programs found guilty of writing unstructured programs. -

Programming Pearls: a Literate Program
by jot1 Be~~tley programming with Special Guest Oysters Don Knuth and Doug McIlroy pearls A LITERATE PROGRAM Last month‘s column introduced Don Knuth’s style of frequency; or there might not even be as many as k “Literate Programming” and his WEB system for building words. Let’s be more precise: The most common programs that are works of literature. This column pre- words are to be printed in order of decreasing fre- sents a literate program by Knuth (its origins are sketched quency, with words of equal frequency listed in al- in last month‘s column) and, as befits literature, a review. phabetic order. Printing should stop after k words So without further ado, here is Knuth’s program, have been output, if more than k words are present. retypeset in Communications style. -Jon Bentley 2. The input file is assumed to contain the given Common Words Section text. If it begins with a positive decimal number Introduction.. , . , , . , . , . , , . 1 (preceded by optional blanks), that number will be Strategic considerations . , a the value of k; otherwise we shall assume that Basic input routines . , , . 9 k = 100. Answers will be sent to the output file. Dictionary lookup . , . , . , .17 define default-k = 100 (use this value if k isn’t The frequency counts . .32 otherwise specified) Sortingatrie . ...36 Theendgame................................41 3. Besides solving the given problem, this program is Index . ...42 supposed to be an example of the WEB system, for people who know some Pascal but who have never 1. Introduction. The purpose of this program is to seen WEB before. -

A First Course to Openfoam
Basic Shell Scripting Slides from Wei Feinstein HPC User Services LSU HPC & LON [email protected] September 2018 Outline • Introduction to Linux Shell • Shell Scripting Basics • Variables/Special Characters • Arithmetic Operations • Arrays • Beyond Basic Shell Scripting – Flow Control – Functions • Advanced Text Processing Commands (grep, sed, awk) Basic Shell Scripting 2 Linux System Architecture Basic Shell Scripting 3 Linux Shell What is a Shell ▪ An application running on top of the kernel and provides a command line interface to the system ▪ Process user’s commands, gather input from user and execute programs ▪ Types of shell with varied features o sh o csh o ksh o bash o tcsh Basic Shell Scripting 4 Shell Comparison Software sh csh ksh bash tcsh Programming language y y y y y Shell variables y y y y y Command alias n y y y y Command history n y y y y Filename autocompletion n y* y* y y Command line editing n n y* y y Job control n y y y y *: not by default http://www.cis.rit.edu/class/simg211/unixintro/Shell.html Basic Shell Scripting 5 What can you do with a shell? ▪ Check the current shell ▪ echo $SHELL ▪ List available shells on the system ▪ cat /etc/shells ▪ Change to another shell ▪ csh ▪ Date ▪ date ▪ wget: get online files ▪ wget https://ftp.gnu.org/gnu/gcc/gcc-7.1.0/gcc-7.1.0.tar.gz ▪ Compile and run applications ▪ gcc hello.c –o hello ▪ ./hello ▪ What we need to learn today? o Automation of an entire script of commands! o Use the shell script to run jobs – Write job scripts Basic Shell Scripting 6 Shell Scripting ▪ Script: a program written for a software environment to automate execution of tasks ▪ A series of shell commands put together in a file ▪ When the script is executed, those commands will be executed one line at a time automatically ▪ Shell script is interpreted, not compiled. -

Teaching Foundations of Computation and Deduction Through Literate Functional Programming and Type Theory Formalization
Teaching Foundations of Computation and Deduction Through Literate Functional Programming and Type Theory Formalization Gérard Huet Inria Paris Laboratory, France Abstract We describe experiments in teaching fundamental informatics notions around mathematical struc- tures for formal concepts, and effective algorithms to manipulate them. The major themes of lambda-calculus and type theory served as guides for the effective implementation of functional programming languages and higher-order proof assistants, appropriate for reflecting the theor- etical material into effective tools to represent constructively the concepts and formally certify the proofs of their properties. Progressively, a literate programming and proving style replaced informal mathematics in the presentation of the material as executable course notes. The talk will evoke the various stages of (in)completion of the corresponding set of notes along the years (see [1, 2, 14, 5, 6, 10, 12, 16, 7, 15, 17, 9, 3, 13, 11, 4, 8]), and tell how their elaboration proved to be essential to the discovery of fundamental results. 1998 ACM Subject Classification F.3.1 Specifying and Verifying Programs, F.4.1 Mathematical Logic and G.4 Mathematical Software Keywords and phrases Foundations, Computation, Deduction, Programming, Proofs Digital Object Identifier 10.4230/LIPIcs.FSCD.2016.3 Category Invited Talk References 1 Gérard Huet. Initiation à la logique mathématique. Notes de cours du DEA d’Informatique, Université Paris-Sud, 1977. 2 Gérard Huet. Démonstration automatique en logique de premier ordre et programmation en clauses de horn. Notes de cours du DEA d’Informatique, Université Paris-Sud, 1978. 3 Gérard Huet. Confluent reductions: Abstract properties and applications to term rewriting systems. -

Typeset MMIX Programs with TEX Udo Wermuth Abstract a TEX Macro
TUGboat, Volume 35 (2014), No. 3 297 Typeset MMIX programs with TEX Example: In section 9 the lines \See also sec- tion 10." and \This code is used in section 24." are given. Udo Wermuth No such line appears in section 10 as it only ex- tends the replacement code of section 9. (Note that Abstract section 10 has in its headline the number 9.) In section 24 the reference to section 9 stands for all of ATEX macro package is presented as a literate pro- the eight code lines stated in sections 9 and 10. gram. It can be included in programs written in the If a section is not used in any other section then languages MMIX or MMIXAL without affecting the it is a root and during the extraction of the code a assembler. Such an instrumented file can be pro- file is created that has the name of the root. This file cessed by TEX to get nicely formatted output. Only collects all the code in the sequence of the referenced a new first line and a new last line must be entered. sections from the code part. The collection process And for each end-of-line comment a flag is set to for all root sections is called tangle. A second pro- indicate that the comment is written in TEX. cess is called weave. It outputs the documentation and the code parts as a TEX document. How to read the following program Example: The following program has only one The text that starts in the next chapter is a literate root that is defined in section 4 with the headline program [2, 1] written in a style similar to noweb [7]. -

Bash Guide for Beginners
Bash Guide for Beginners Machtelt Garrels Garrels BVBA <tille wants no spam _at_ garrels dot be> Version 1.11 Last updated 20081227 Edition Bash Guide for Beginners Table of Contents Introduction.........................................................................................................................................................1 1. Why this guide?...................................................................................................................................1 2. Who should read this book?.................................................................................................................1 3. New versions, translations and availability.........................................................................................2 4. Revision History..................................................................................................................................2 5. Contributions.......................................................................................................................................3 6. Feedback..............................................................................................................................................3 7. Copyright information.........................................................................................................................3 8. What do you need?...............................................................................................................................4 9. Conventions used in this -

Lecture 17 the Shell and Shell Scripting Simple Shell Scripts
Lecture 17 The Shell and Shell Scripting In this lecture • The UNIX shell • Simple Shell Scripts • Shell variables • File System commands, IO commands, IO redirection • Command Line Arguments • Evaluating Expr in Shell • Predicates, operators for testing strings, ints and files • If-then-else in Shell • The for, while and do loop in Shell • Writing Shell scripts • Exercises In this course, we need to be familiar with the "UNIX shell". We use it, whether bash, csh, tcsh, zsh, or other variants, to start and stop processes, control the terminal, and to otherwise interact with the system. Many of you have heard of, or made use of "shell scripting", that is the process of providing instructions to shell in a simple, interpreted programming language . To see what shell we are working on, first SSH into unix.andrew.cmu.edu and type echo $SHELL ---- to see the working shell in SSH We will be writing our shell scripts for this particular shell (csh). The shell scripting language does not fit the classic definition of a useful language. It does not have many of the features such as portability, facilities for resource intensive tasks such as recursion or hashing or sorting. It does not have data structures like arrays and hash tables. It does not have facilities for direct access to hardware or good security features. But in many other ways the language of the shell is very powerful -- it has functions, conditionals, loops. It does not support strong data typing -- it is completely untyped (everything is a string). But, the real power of shell program doesn't come from the language itself, but from the diverse library that it can call upon -- any program. -

Constructing Algorithms and Pseudocoding This Document Was Originally Developed by Professor John P
Constructing Algorithms and Pseudocoding This document was originally developed by Professor John P. Russo Purpose: # Describe the method for constructing algorithms. # Describe an informal language for writing PSEUDOCODE. # Provide you with sample algorithms. Constructing Algorithms 1) Understand the problem A common mistake is to start writing an algorithm before the problem to be solved is fully understood. Among other things, understanding the problem involves knowing the answers to the following questions. a) What is the input list, i.e. what information will be required by the algorithm? b) What is the desired output or result? c) What are the initial conditions? 2) Devise a Plan The first step in devising a plan is to solve the problem yourself. Arm yourself with paper and pencil and try to determine precisely what steps are used when you solve the problem "by hand". Force yourself to perform the task slowly and methodically -- think about <<what>> you are doing. Do not use your own memory -- introduce variables when you need to remember information used by the algorithm. Using the information gleaned from solving the problem by hand, devise an explicit step-by-step method of solving the problem. These steps can be written down in an informal outline form -- it is not necessary at this point to use pseudo-code. 3) Refine the Plan and Translate into Pseudo-Code The plan devised in step 2) needs to be translated into pseudo-code. This refinement may be trivial or it may take several "passes". 4) Test the Design Using appropriate test data, test the algorithm by going through it step by step. -

ASCII Delimited Format Plug-In User’S Guide
ASCII Delimited Format Plug-in User’s Guide Version 3.4 ASCII DELIMITED ......................................................................................................... 4 CREATING AN ASCII DELIMITED MESSAGE ....................................................... 4 ASCII DELIMITED EXTERNAL MESSAGE UI........................................................ 6 DEFINING AN ASCII DELIMITED MESSAGE FORMAT...................................... 7 ASCII DELIMITED FORMAT OPTIONS .............................................................................. 7 Delimiter ..................................................................................................................... 8 Message Options......................................................................................................... 9 Treat Entire Input/Output as a Single Message (Message Mode) ...................... 9 Treat Each Record as a Separate Message (Batch Mode) ................................ 10 Single Record Mode ......................................................................................... 10 Header/Trailer Option.............................................................................................. 11 ADDING A NEW FIELD.................................................................................................... 12 SPECIFYING FIELD PROPERTIES...................................................................................... 13 The Required Property..................................................................................... -

STAT579: SAS Programming
Note on homework for SAS date formats I'm getting error messages using the format MMDDYY10D. even though this is listed on websites for SAS date formats. Instead, MMDDYY10 and similar (without the D seems to work for both hyphens and slashes. Also note that a date format such as MMDDYYw. means that the w is replaced by a number indicating the width of the string (e.g., 8 or 10). SAS Programming SAS data sets (Chapter 4 of Cody book) SAS creates data sets internally once they are read in from a Data Step. The data sets can be stored in different locations and accessed later on. The default is to store them in WORK, so if you create a data set using data adress; the logfile will say that it created a SAS dataset called WORK.ADDRESS. You can nagivate to the newly created SAS dataset. In SAS Studio, go to the Libraries Tab on the left (Usually appears toward the bottom until you click on it). Then WORK.ADDRESS should appear. SAS Programming SAS data sets SAS Programming SAS data sets SAS Programming Making datasets permanent You can also make SAS datasets permanent. This is done using the libname statement. E.g. SAS Programming Permanent SAS datasets The new dataset should be available to be accessed directly from other SAS programs without reading in original data. This can save a lot of time for large datasets. If the SAS dataset is called mydata, the SAS dataset will be called mydata.sas7bdat, where the 7 refers to the datastructures used in version 7 (and which hasn't changed up to version 9). -

Positive Pay Format Guide
Positive Pay Format Guide Check File Import Contents Contents ........................................................................................................................................................ 1 I. Supported File Types ............................................................................................................................. 2 A. Delimited Text Files ........................................................................................................................... 2 B. Microsoft Excel Files.......................................................................................................................... 2 C. Fixed-width Text Files ....................................................................................................................... 2 D. Header and Trailer Records .............................................................................................................. 2 II. File Data Requirements ......................................................................................................................... 3 A. Required Columns ............................................................................................................................. 3 B. Optional Columns.............................................................................................................................. 3 Positive Pay 1 of 3 BankFinancial, NA Format Guide 11-2016-1 I. Supported File Types Positive Pay supports the following three types of issued files: A. Delimited