33SPAC E and DEFENSE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

LEGAL MEMORANDUM No
LEGAL MEMORANDUM No. 218 | OCTOBER 3, 2017 The Costs of Early Voting Hans A. von Spakovsky Abstract Although voters may find early voting convenient, turnout data show Key Points that early voting may actually decrease turnout, not increase it. Early voting raises the costs of political campaigns, since expensive get-out- n Contrary to what might be expect- the-vote efforts must be spread out over a longer period of time. There ed, studies show that early voting is also no question that when voters cast their ballots weeks before Elec- not only does not increase turn- out, it may actually decrease it. tion Day, they do so without the same access to knowledge about the can- didates and the issues as those who vote on Election Day. When there n This practice spreads out the vot- are late-breaking developments in campaigns that could be important ing period over a longer period of time during which voters may be to the choices made by voters, those who have voted early cannot change casting their ballots without all of their votes. the information about candidates and issues that may become avail- ntil the late 1980s, Americans had two ways to vote: (1) in per- able by Election Day. son on Election Day, or (2) absentee ballots sent through the U n Early voting periods also increase mail or voted in person at county election departments prior to the cost of political campaigns Election Day. Early voting—in-person voting in a limited number because any candidate who limits of locations prior to Election Day—was first implemented by a state spending on voter mobilization to (Texas) almost 30 years ago and has been pushed by proponents as a the last few days before Election way of increasing turnout by making voting more convenient. -

I Read It on Reddit: Exploring the Role of Online Communities in the 2016 US Elections News Cycle
I read it on Reddit: Exploring the role of online communities in the 2016 US elections news cycle Jon Roozenbeek1 and Adri`aSalvador Palau2 1 Department of Slavonic Studies, Faculty of Modern and Medieval Languages, University of Cambridge, Cambridge, CB3 9DA, UK [email protected], 2 Department of Engineering, Institute for Manufacturing, University of Cambridge, Cambridge, CB3 0FS, UK Abstract. Reddit has developed into a significant platform for political discussion among Mil- lennials. In this exploratory study, we examine subscription trends on three political sub-forums on Reddit during the 2016 US presidential elections: /The Donald, /SandersForPresident, and /HillaryClinton. As a theoretical framework, we draw from work on online communities' group identity and cohesion. Concretely, we investigate how subscription dynamics relate to positive, negative and neutral news events occurring during the election cycle. We classify news events using a sentiment analysis of event-related news headlines. We observe that users who supported Sanders displayed no consolidation of support for Clinton after she won the Democratic Party's presidential nomination. Secondly, we show that negative news events affected Sanders and Clintons subscrip- tion trends negatively, while showing no effect for Donald Trump. This gives empirical credence to Trump's controversial claim that he could "stand in the middle of 5th Avenue and shoot somebody and not lose any voters". We offer a number of explanations for the observed phenomena: the nature of the content of the three subreddits, their cultural dynamics, and changing dynamics of parti- sanship. We posit that the 'death of expertise' expresses itself on Reddit as a switch in persuasion tactics from a policy-based to an emotions-based approach, and that group members' agreement on policy proved a weak marker for online communities' group identity and cohesion. -

H-Diplo Roundtable Review, Vol. X, No. 2
2009 h-diplo H-Diplo Roundtable Reviews www.h-net.org/~diplo/roundtables Volume X, No. 2 (2009) 27 January 2009 Thomas M. Nichols. Eve of Destruction: The Coming Age of Preventive War. Philadelphia: University of Pennsylvania Press, 2008. ISBN: 978-0-8122-4066-5 (cloth, $39.95). Roundtable Editor: Thomas Maddux Reviewers: Stephen A. Bourque, Jeffrey D. McCausland, Jonathan Reed Winkler Stable URL: http://www.h-net.org/~diplo/roundtables/PDF/Roundtable-X-2.pdf Contents Introduction by Thomas Maddux, California State University, Northridge.............................. 1 Review by Stephen A. Bourque, Department of Military History, U. S. Army Command and General Staff College ................................................................................................................ 7 Review by Jeffrey D. McCausland, Penn State Dickinson School of Law and School of International Affairs................................................................................................................ 11 Review by Jonathan Reed Winkler, Wright State University.................................................. 15 Author’s Response by Thomas Nichols, U.S. Naval War College............................................ 18 Introduction by Thomas Maddux, California State University, Northridge Copyright © 2009 H-Net: Humanities and Social Sciences Online. H-Net permits the redistribution and reprinting of this work for non-profit, educational purposes, with full and accurate attribution to the author(s), web location, date of publication, H-Diplo, and H-Net: Humanities & Social Sciences Online. For other uses, contact the H-Diplo editorial staff at [email protected]. H-Diplo Roundtable Reviews, Vol. X, No. 2 (2009) homas Nichols’ Eve of Destruction: The Coming Age of Preventive War (2008) adds an important and somewhat different perspective to the 2008 H-Diplo roundtables Ton the topic of the 1990s and George W. Bush’s strategy in the “War on Terror”. -
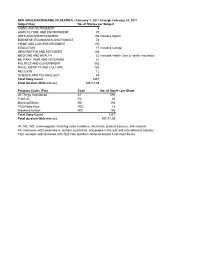
NPR ISSUES/PROGRAMS (IP REPORT) - February 1, 2017 Through February 28, 2017 Subject Key No
NPR ISSUES/PROGRAMS (IP REPORT) - February 1, 2017 through February 28, 2017 Subject Key No. of Stories per Subject AGING AND RETIREMENT 6 AGRICULTURE AND ENVIRONMENT 70 ARTS AND ENTERTAINMENT 159 includes Sports BUSINESS, ECONOMICS AND FINANCE 74 CRIME AND LAW ENFORCEMENT 100 EDUCATION 17 includes College IMMIGRATION AND REFUGEES 145 MEDICINE AND HEALTH 52 includes Health Care & Health Insurance MILITARY, WAR AND VETERANS 21 POLITICS AND GOVERNMENT 392 RACE, IDENTITY AND CULTURE 106 RELIGION 12 SCIENCE AND TECHNOLOGY 63 Total Story Count 1217 Total duration (hhh:mm:ss) 101:17:53 Program Codes (Pro) Code No. of Stories per Show All Things Considered AT 592 Fresh Air FA 40 Morning Edition ME 386 TED Radio Hour TED 13 Weekend Edition WE 186 Total Story Count 1217 Total duration (hhh:mm:ss) 101:17:53 AT, ME, WE: newsmagazine featuring news headlines, interviews, produced pieces, and analysis FA: interviews with newsmakers, authors, journalists, and people in the arts and entertainment industry TED: excerpts and interviews with TED Talk speakers centered around a common theme Key Pro Date Duration Segment Title Aging and Retirement WEEKEND EDITION SATURDAY 02/25/2017 0:07:00 Benefits In Jeopardy For Retired Coal Miners Aging and Retirement MORNING EDITION 02/22/2017 0:03:34 Trump Moving To Delay Rule That Protects Workers From Bad Financial Advice Aging and Retirement ALL THINGS CONSIDERED 02/21/2017 0:03:05 Does Testosterone Improve Older Men's Health? It Depends Aging and Retirement ALL THINGS CONSIDERED 02/21/2017 0:03:54 In A Film Industry -

H-Diplo Review Essay on George Shultz. Issues on My Mind: Strategies for the Future
H20-Diplo Review14 Essay H-Diplo H-Diplo Review Essays Editor: Diane Labrosse H-Diplo Review ESSAY H-Diplo Web and Production Editor: George Fujii http://www.h-net.org/~diplo/essays/ Commissioned for H-Diplo by Diane Labrosse Published on 19 March 2014 H-Diplo Review Essay on George Shultz. Issues on My Mind: Strategies for the Future. Stanford: Hoover Institution Press, 2103. URL: http://www.h-net.org/~diplo/essays/PDF/Nichols-Schultz.pdf Reviewed for H-Diplo by Tom Nichols, Naval War College ew people have earned the right to give a book a title as simple as Issues on My Mind, but George Shultz, America’s 60th Secretary of State, is one of them. (He also headed F the departments of Treasury and Labor, and the Office of Management and Budget, among other posts.) As the title implies, the book is an exploration of Shultz’s thoughts in six areas: governance, economic policy, energy, drug policy, diplomacy, and nuclear weapons. The book is not structured around a conventional narrative. Rather, Shultz has some introductory materials in each section, and then he adds various speeches and articles, as a kind of intellectual scrapbooking of his views and those of others whom he respects. As Shultz modestly says at the outset, he has collected his thoughts on issues “of critical importance that [have] been on my mind for many years,” and he hopes that his “observations...based on the insights I have gained through personal experiences” may be “useful.” (7) The former Secretary of State is a formidable and experienced diplomat and academic, and his views are always worth considering. -

H-Dipl Roundtable, Vol. IX No. 23
2008 h-diplo H-Diplo Roundtable Reviews www.h-net.org/~diplo/roundtables Volume IX, No. 23 (2008) 24 November 2008 Joan Hoff. A Faustian Foreign Policy from Woodrow Wilson to George W. Bush: Dreams of Perfectibility. Cambridge and New York: Cambridge University Press, 2008. 316 pp. ISBN: 978-0-521-87905-7 (hardback, $80.00); 978-0-521-71404-4 (paperback, $24.99); 978-0-511- 36793-9 (Adobe eBook Reader, $20.00). Roundtable Editor: Thomas Maddux Reviewers: Carolyn Eisenberg, Catherine Forslund, Erika Kuhlman, Tom Nichols Author’s Response from Joan Hoff H-Diplo Roundtable Reviews Managing Editor: Diane N. Labrosse H-Diplo Roundtable Reviews General Editor and Web Editor: George Fujii Stable URL: http://www.h-net.org/~diplo/roundtables/PDF/Roundtable-IX-23.pdf Contents Introduction by Thomas Maddux, California State University, Northridge.............................. 2 Review by Carolyn Eisenberg, Hofstra University..................................................................... 9 Review by Catherine Forslund, Rockford College................................................................... 12 Review by Erika Kuhlman, Idaho State University.................................................................. 14 Review by Tom Nichols, Naval War College ........................................................................... 18 Author’s Response by Joan Hoff, Montana State University, Bozeman................................. 30 Copyright © 2008 H-Net: Humanities and Social Sciences Online. H-Net permits the redistribution and reprinting of this work for non-profit, educational purposes, with full and accurate attribution to the author(s), web location, date of publication, H-Diplo, and H-Net: Humanities & Social Sciences Online. For other uses, contact the H-Diplo editorial staff at [email protected]. H-Diplo Roundtable Reviews, Vol. IX, No 23 (2008) Introduction by Thomas Maddux, California State University, Northridge he theme of American exceptionalism and its many contradictions from the time of the Puritans to George W. -

Russia's Actions Are a Direct Attack on US and Allied Democracies
DECEMBER 2018 Russia’s Actions Are a Direct Attack on US and Allied Democracies This talk was delivered at a panel event at the Macdonald-Laurier Institute on October 5, 2018. Tom Nichols The first thing I should tell you is that I don’t represent the views of the United States government. I’m here speaking in my own capacity and from my own views. With that out of the way, the first thing I would say about Russia’s challenge – it’s not just a challenge to the United States or the Baltic States, it is an all front attack on the West. But I’m sorry to say that I think there is no single view from America. There are several views from America about this issue. Some Americans see this whole issue of a Russian attack against the West as nonsense, as politically motivated, primarily as a means of trying to undermine the Trump administration. The President himself encourages this thinking, when he says, “Would it be so bad if I got along with Russia and Putin?” Right off the bat, there is a segment of the American public that just does not take this threat very seriously, and I think that’s unfortunate. There’s a second view that sees this as somewhat important but not crucial. Talking with this segment of Americans, you will get an answer like, “Well, of course the Russians meddled, but that’s just Russians doing what Russians do. It wasn’t particularly effective or important. It’s just another day in the big jungle.” There are concerns here that you can never separate this from the extremely sharp and divided partisan situation in the United States right now. -

November 2017 | Volume 53, Number 4 the Magazine of the National
The Magazine of the National Communication Association November 2017 | Volume 53, Number 4 ABOUT Spectra, the magazine of the National Communication Association 2017 NCA EXECUTIVE COMMITTEE (NCA), features articles on topics that are relevant to In this issue Communication scholars, teachers, and practitioners. Spectra is President one means through which NCA works toward accomplishing its Stephen J. Hartnett, University of Colorado, Denver mission of advancing Communication as the discipline that studies First Vice President all forms, modes, media, and consequences of communication Ronald L. Jackson II, University of Cincinnati through humanistic, social scientific, and aesthetic inquiry. MESSAGE FROM 2 THE PRESIDENT NCA serves its members by enabling and supporting their Second Vice President professional interests. Dedicated to fostering and promoting Star Muir, George Mason University Fake News, Startling Truths, free and ethical communication, NCA promotes the widespread and the Power of Trust in Immediate Past President appreciation of the importance of communication in public and 7 an Age of Disbelief private life, the application of competent communication to Christina S. Beck, Ohio University AN INTRODUCTION By Stephen J. Hartnett, Ph.D. improve the quality of human life and relationships, and the use Educational Policies Board Director FAKE NEWS of knowledge about communication to solve human problems. Scott A. Myers, West Virginia University SPOTLIGHT The views and opinions expressed in Spectra articles are those 4 of the authors and do not necessarily reflect those of the National Publications Board Director Data About the Discipline: Communication Association. Bonnie J. Dow, Vanderbilt University 8 Journal Citation Metrics WHAT DO WE MEAN for NCA Journals All NCA members receive a Spectra subscription. -

Center for Unconventional Weapons Studies (CUWS) Outreach Journal
USAF Center for Unconventional Weapons Studies (CUWS) Outreach Journal CUWS Outreach Journal 1236 7 October 2016 Feature Item: “Is North Korea Building a New Submarine?” A 38 North exclusive by Joseph S. Bermudez Jr.; Published by 38 North.com; 30 September 2016. http://38north.org/2016/09/sinpo093016/?utm_source=38+North+Bulletin+093016&utm_camp aign=38+North&utm_medium=email Commercial satellite imagery strongly suggests that a naval construction program is underway at North Korea’s Sinpo South Shipyard, possibly to build a new submarine. While there is no direct evidence that the program is for a boat to carry the ballistic missile currently under development, the presence of an approximately 10-meter-in-diameter circular component outside the facility’s recently renovated fabrication hall may be intended as a construction-jig[1] or as a component for the pressure hull of a new submarine. However, it is also possible the ring may be related to another construction project. If this activity is indeed to build a new submarine, it would appear to be larger than North Korea’s GORAE-class experimental ballistic missile submarine (SSBA), which has a beam of approximately 7 meters.[2] U.S. Nuclear Weapons 1. NNSA Head: ‘All Bets Are Off for Warhead Modernization Under Sequestration’ 2. US Carries Out Two Successful Flight Tests Using Mock Nuke Bombs 3. Sled Track Simulates High-Speed Accident in B61-12 Test U.S. Counter-WMD 1. THAAD Battery from Texas to Be Deployed in Seongju: Sources 2. DOD IG Auditing BMDS Supply Chain Risk Management U.S. Arms Control 1. -

Finding the Truth in a Post-Truth World
How Do You Know?: Finding the Truth in a Post-Truth World (Moderated by Ray Suarez) July 7-10, 2017 Aspen, Colorado Table of Contents Whether you want to deliver information that is objectively true, or simply do the work of being a citizen in the 21st century, how do you know what’s true? Content is coming at your eyeballs and eardrums nearly non-stop, from a vast array of sources. Can you tell the difference between good information and bad information? Fact versus fiction? If it is true that anyone with a smartphone can be a journalist, who then determines journalistic standards? What happens when no one gets to define those standards? Who determines truth? Is this a good place to be an information consumer? What can/should we do differently? Session I: Setting the Table: Feelings Over Facts Andrew Calcutt, “The Surprising Origin of ‘Post-Truth’ and How It Was Spawned by the Liberal Left,” The Conversation, November 18, 2016 Jay Ogilvy, “Alternative Facts in a Post-Truth World?” Forbes, February 2, 2017 Nancy Gibb, “When a President Can’t Be Taken at His Word,” TIME, March 23, 2017 Tim Harford, “The Problem With Facts,” The Financial Times, March 9, 2017 Tom Nichols, “How America Lost Faith in Expertise,” Foreign Affairs, March/April 2017 Jay Ogilvy, “Why So Few Thought Trump Would Win,” Stratfor Intelligence, December 7, 2016 1 Session II: Getting Through the Day. Of Wheat and Chaff Amanda Hoover, “Competing Polls: Does Handpicked Data Deepen Political Divides?” Christian Science Monitor, February 9, 2017 Daniel Engber, “Who Will -

Tom Nichols, the Death of Expertise
POL S 334 A - Tom Nichols, The Death of Expertise [00:00:06.38] - For tonight's event I'm happy to be welcoming Tom Nichols to the store to discuss his new book, The Death Of Expertise-- The Campaign Against Established Knowledge and Why it Matters. [00:00:17.70] In this information age it's more easy than ever to get answers you're seeking to questions about your health, or consumer reviews, or product information. But how do you know where that information is coming from? In his impassioned cautionary tale about the perils of un- vetted information, Tom argues that credentials are still important and that giving experts their due is not undemocratic. [00:00:43.44] Ian Bremmer, president and founder of Eurasia Group, said of the book, "We live in a post-fact age, one that's dangerous for a whole host of reasons. Here's a book that not only acknowledges this reality but takes it head-on. Persuasive and well-written, The Death of Expertise is exactly the book needed for our times. [00:01:02.48] A professor of national security affairs at the US Naval War College, and an adjunct professor at the Harvard Extension School, and a former aide to the US Senate, Tom is the author of several other works on foreign policy and international security affairs including The Sacred Cause, No Use-- Nuclear Weapons and US National Security; Eve of Destruction-- The Coming Age of Preventative War; and The Russian Presidency. [00:01:31.89] And his real credential for this evening is that he is a five time undefeated Jeopardy champion and one of the all time top players of the game. -

I Read It on Reddit: Exploring the Role of Online Communities in the 2016 US Elections News Cycle
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Apollo I read it on Reddit: Exploring the role of online communities in the 2016 US elections news cycle Jon Roozenbeek1 and Adri`aSalvador Palau2 1 Department of Slavonic Studies, Faculty of Modern and Medieval Languages, University of Cambridge, Cambridge, CB3 9DA, UK [email protected], 2 Department of Engineering, Institute for Manufacturing, University of Cambridge, Cambridge, CB3 0FS, UK Abstract. Reddit has developed into a significant platform for political discussion among Mil- lennials. In this exploratory study, we examine subscription trends on three political sub-forums on Reddit during the 2016 US presidential elections: /The Donald, /SandersForPresident, and /HillaryClinton. As a theoretical framework, we draw from work on online communities' group identity and cohesion. Concretely, we investigate how subscription dynamics relate to positive, negative and neutral news events occurring during the election cycle. We classify news events using a sentiment analysis of event-related news headlines. We observe that users who supported Sanders displayed no consolidation of support for Clinton after she won the Democratic Party's presidential nomination. Secondly, we show that negative news events affected Sanders and Clintons subscrip- tion trends negatively, while showing no effect for Donald Trump. This gives empirical credence to Trump's controversial claim that he could "stand in the middle of 5th Avenue and shoot somebody and not lose any voters". We offer a number of explanations for the observed phenomena: the nature of the content of the three subreddits, their cultural dynamics, and changing dynamics of parti- sanship.