Big Data Prologue Linking Cloud Computing to Ascertain The
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Work Package (Wp) 2 “Web Development”
WORK PACKAGE (WP) 2 “WEB DEVELOPMENT” Project “Youth networking for economic exchange in the cross-border region” Project No. CB007.2.22.078 The project is co-funded by EU through the Interreg-IPA CBC Bulgaria–Serbia Programme This publication has been produced with the assistance of the European Union through the Interreg-IPA CBC Bulgaria-Serbia Programme, CCI No 2014TC16I5CB007. The contents of this publication are the sole responsibility of National Association Legal Initiative for Open Government and can in no way be taken to reflect the views of the European Union or the Managing Authority of the Programme. CONTENTS: L. WEB DEVELOPMENT BASICS, PRINCIPLES, APPROACHES .............................................................................. 3 2. FRONT-END WEB DEVELOPMENT: HTML, CSS, JAVASCRIPT, JQUERY, BOOTSTRAP ....................................... 9 WHAT YOU ALREADY NEED TO KNOW ......................................................................................................................... 18 3. BACK-END WEB DEVELOPMENT: JAVA, MYSQL .......................................................................................... 21 4. AJAX ANGULAR.JS PROGRAMMING ........................................................................................................... 25 5. WEBSITE DEVELOPMENT AND MODIFICATION VIA CMS............................................................................. 31 6. DEVELOPMENT ENVIRONMENTS: INTEGRATED DEBUGGING ENVIRONMENT (IDE), DEVELOPMENT TOOLS, TOOLS TO SUPPORT METHODOLOGICAL CONTROL -

Scientific Tools for Linux
Scientific Tools for Linux Ryan Curtin LUG@GT Ryan Curtin Getting your system to boot with initrd and initramfs - p. 1/41 Goals » Goals This presentation is intended to introduce you to the vast array Mathematical Tools of software available for scientific applications that run on Electrical Engineering Tools Linux. Software is available for electrical engineering, Chemistry Tools mathematics, chemistry, physics, biology, and other fields. Physics Tools Other Tools Questions? Ryan Curtin Getting your system to boot with initrd and initramfs - p. 2/41 Non-Free Mathematical Tools » Goals MATLAB (MathWorks) Mathematical Tools » Non-Free Mathematical Tools » MATLAB » Mathematica Mathematica (Wolfram Research) » Maple » Free Mathematical Tools » GNU Octave » mathomatic Maple (Maplesoft) »R » SAGE Electrical Engineering Tools S-Plus (Mathsoft) Chemistry Tools Physics Tools Other Tools Questions? Ryan Curtin Getting your system to boot with initrd and initramfs - p. 3/41 MATLAB » Goals MATLAB is a fully functional mathematics language Mathematical Tools » Non-Free Mathematical Tools You may be familiar with it from use in classes » MATLAB » Mathematica » Maple » Free Mathematical Tools » GNU Octave » mathomatic »R » SAGE Electrical Engineering Tools Chemistry Tools Physics Tools Other Tools Questions? Ryan Curtin Getting your system to boot with initrd and initramfs - p. 4/41 Mathematica » Goals Worksheet-based mathematics suite Mathematical Tools » Non-Free Mathematical Tools Linux versions can be buggy and bugfixes can be slow » MATLAB -

Introducción a Linux Equivalencias Windows En Linux Ivalencias
No has iniciado sesión Discusión Contribuciones Crear una cuenta Acceder Página discusión Leer Editar Ver historial Buscar Introducción a Linux Equivalencias Windows en Linux Portada < Introducción a Linux Categorías de libros Equivalencias Windows en GNU/Linux es una lista de equivalencias, reemplazos y software Cam bios recientes Libro aleatorio análogo a Windows en GNU/Linux y viceversa. Ayuda Contenido [ocultar] Donaciones 1 Algunas diferencias entre los programas para Windows y GNU/Linux Comunidad 2 Redes y Conectividad Café 3 Trabajando con archivos Portal de la comunidad 4 Software de escritorio Subproyectos 5 Multimedia Recetario 5.1 Audio y reproductores de CD Wikichicos 5.2 Gráficos 5.3 Video y otros Imprimir/exportar 6 Ofimática/negocios Crear un libro 7 Juegos Descargar como PDF Versión para im primir 8 Programación y Desarrollo 9 Software para Servidores Herramientas 10 Científicos y Prog s Especiales 11 Otros Cambios relacionados 12 Enlaces externos Subir archivo 12.1 Notas Páginas especiales Enlace permanente Información de la Algunas diferencias entre los programas para Windows y y página Enlace corto GNU/Linux [ editar ] Citar esta página La mayoría de los programas de Windows son hechos con el principio de "Todo en uno" (cada Idiomas desarrollador agrega todo a su producto). De la misma forma, a este principio le llaman el Añadir enlaces "Estilo-Windows". Redes y Conectividad [ editar ] Descripción del programa, Windows GNU/Linux tareas ejecutadas Firefox (Iceweasel) Opera [NL] Internet Explorer Konqueror Netscape / -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Metadefender Core V4.17.3
MetaDefender Core v4.17.3 © 2020 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of MetaDefender Core 14 1. Quick Start with MetaDefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Process Files with MetaDefender Core 21 2. Installing or Upgrading MetaDefender Core 22 2.1. Recommended System Configuration 22 Microsoft Windows Deployments 22 Unix Based Deployments 24 Data Retention 26 Custom Engines 27 Browser Requirements for the Metadefender Core Management Console 27 2.2. Installing MetaDefender 27 Installation 27 Installation notes 27 2.2.1. Installing Metadefender Core using command line 28 2.2.2. Installing Metadefender Core using the Install Wizard 31 2.3. Upgrading MetaDefender Core 31 Upgrading from MetaDefender Core 3.x 31 Upgrading from MetaDefender Core 4.x 31 2.4. MetaDefender Core Licensing 32 2.4.1. Activating Metadefender Licenses 32 2.4.2. Checking Your Metadefender Core License 37 2.5. Performance and Load Estimation 38 What to know before reading the results: Some factors that affect performance 38 How test results are calculated 39 Test Reports 39 Performance Report - Multi-Scanning On Linux 39 Performance Report - Multi-Scanning On Windows 43 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. -

Gputils 0.13.3
gputils 0.13.3 October 27, 2007 1 James Bowman and Craig Franklin July 31, 2005 Contents 1 Introduction 4 1.1 ToolFlows ....................................... ... 4 1.1.1 AbsoluteAsmMode ............................... .. 4 1.1.2 RelocatableAsmMode. .... 4 1.1.3 WhichToolFlowisbest?. ..... 5 1.2 Supportedprocessors . ........ 5 2 gpasm 7 2.1 Runninggpasm .................................... .... 7 2.1.1 Usinggpasmwith“make” . .... 8 2.1.2 Dealingwitherrors.. ... .... .... .... ... .... .... ..... 9 2.2 Syntax.......................................... ... 9 2.2.1 Filestructure ................................. .... 9 2.2.2 Expressions................................... ... 9 2.2.3 Numbers ....................................... 11 2.2.4 Preprocessor .................................. ... 12 2.2.5 Processorheaderfiles. ...... 12 2.3 Directives ...................................... ..... 13 2.3.1 Codegeneration ................................ ... 13 2.3.2 Configuration.................................. ... 13 2.3.3 Conditionalassembly. ...... 13 2.3.4 Macros ........................................ 13 2.3.5 $ ........................................... 14 2.3.6 Suggestionsforstructuringyourcode . ........... 14 2.3.7 Directivesummary .............................. .... 15 2.3.8 Highlevelextensions. ...... 24 2.4 Instructions .................................... ...... 27 2.4.1 Instructionsetsummary . ...... 28 2.5 Errors/Warnings/Messages . .......... 30 2.5.1 Errors........................................ 31 2.5.2 Warnings ..................................... -

$Date:: 2020-09-20#$ Contents
gpsim $Date:: 2020-09-20#$ Contents 1 gpsim - An Overview 6 1.1 Makingtheexecutable ......................... 6 1.1.1 MakeDetails-./configureoptions . 6 1.1.2 RPMs.............................. 7 1.1.3 Windows ............................ 7 1.2 Running................................. 7 1.3 Requirements .............................. 8 2 Command Line Interface 9 2.1 attach .................................. 10 2.2 break .................................. 11 2.3 clear................................... 13 2.4 disassemble ............................... 14 2.5 dump .................................. 14 2.6 echo................................... 15 2.7 frequency ................................ 15 2.8 help ................................... 15 2.9 icd.................................... 15 2.10list ................................... 15 2.11load ................................... 16 2.12macros.................................. 16 2.13module ................................. 18 2.14node................................... 19 2.15processor ................................ 20 2.16quit ................................... 20 2.17run.................................... 20 2.18step ................................... 20 1 CONTENTS 2 2.19symbol.................................. 21 2.20stimulus................................. 21 2.21 stopwatch1 ............................... 22 2.22trace................................... 23 2.23version.................................. 23 2.24x..................................... 23 3 Graphical User Interface -

Gnome E KDE: Nemiciamici
Gnome e KDE: nemiciamici Introduzione ai due desktop manager più diffusi per Linux Diego Rondini Gnome e KDE 28 set 2007 - Montebelluna 1 Licenza d'utilizzo Copyright c 2007, Diego Rondini Questo documento viene rilasciato secondo i termini della licenza Creative Commons (http://creativecommons.org). L’utente è libero di: distribuire, comunicare al pubblico, rappresentare o esporre in pubblico la presente opera alle seguenti condizioni: Attribuzione Deve riconoscere la paternità dell’opera all’autore originario. Non commerciale Non può utilizzare quest’opera per scopi commerciali. No opere derivate Non può alterare, trasformare o sviluppare quest’opera. In occasione di ogni atto di riutilizzazione o distribuzione, deve chiarire agli altri i termini della licenza di quest’opera. Se ottiene il permesso dal titolare del diritto d’autore, è possibile rinunciare a ciascuna di queste condizioni. Le utilizzazioni libere e gli altri diritti non sono in nessun modo limitati da quanto sopra. Questo è un riassunto in lingua corrente dei concetti chiave della licenza completa (codice legale), reperibile sul sito Internet http://creativecommons.org/licenses/by-nc-nd/2.0/legalcode Diego Rondini Gnome e KDE 28 set 2007 - Montebelluna 2 Sommario Introduzione ai desktop manager Gnome “ma Linux è semplice!” nascita, evoluzione, obiettivi caratteristiche, applicazioni e strumenti di configurazione KDE “il coltellino svizzero” storia, folklore, pregi e difetti l'”ecosistema” di KDE Diego Rondini Gnome e KDE 28 set 2007 - Montebelluna 3 Gnome: le origini Il progetto Gnome viene avviato nel 1997 da Miguel de Icaza e Federico Mena per fornire un desktop grafico con licenza libera per Linux. Caratteristiche scritto in linguaggio C librerie grafiche GTK+ progetto ufficiale GNU Diego Rondini Gnome e KDE 28 set 2007 - Montebelluna 4 Gnome: evoluzione Durante i primi anni rimane solamente una “brutta copia” di KDE. -

ICT Mediation in Teaching Learning
DEd. syllabus Review -2012 Department of State Education Research and Training Karnataka Position Paper ICT mediation in teaching-learning Chairperson Dr. E.R. Ekbote Professor, Dean of Education Department of Education, Gulbarga University Gulbarga Coordinator Geetha S Members Gurumurthy K Director, IT for Change, #393, 17th Main, 35th Cross, Jayanagar, 4th T Block, Bengaluru 560 041 Rekha Naik - DIET Kumta (PSTE) Savita Naik - DIET Kumta (IFIC) Shylaja SN - EDC and ICTs for Teacher Education 2 Table of Contents 1 Executive Summary......................................................................................................................................4 2 Introduction and background........................................................................................................................4 3 Objectives of ICT mediation in teaching-learning (PSTE)...........................................................................5 4 Enumeration of specific concerns.................................................................................................................8 5 Underlying principles guiding ICT mediation in teaching-learning..............................................................9 6 Critiquing the existing system....................................................................................................................13 7 Suggesting practical alternatives with justification / Broad contents, methodologies proposed..................15 8 ICTs for planning........................................................................................................................................18 -

An Open Source Approach for ASIC Design Flow Kesari Ananda Samhitha Y
Journal of Interdisciplinary Cycle Research ISSN NO: 0022-1945 An Open Source approach for ASIC Design Flow Kesari Ananda Samhitha Y. David Solomon Raju M.Tech Associate Professor Holy Mary Institute of Technology Holy Mary Institute of Technology and ScienceAffiliated to JNTU, and Science Affiliated to JNTU, Hyderabad. Hyderabad. Email: [email protected] Email: davidsolomonraju.y@ gmail.com Abstract: In this paper, we are going to study In this paper, number of open-source and the process of implementation of ASIC freeware CAD tools are presented and design flow with the help of open source evaluated. Based on the objectives of the EDA tools. In order to design our own user, this paper furnishes guidelines that circuitry without any other expensive help in selecting the most appropriate licenced tools, we apt the open source open-source and freeware VLSI CAD tool tools. The design of electronic circuits can for teaching a VLSI design course. be achieved at many different refinement Keywords: VLSI, CAD Tools, Electric, levels from the most detailed layout to the Magic, Alliance, Comparative Study most abstract architectures. Introduction: Given the complexity of Very Large Scaled Integrated Circuits (VLSI) ASIC design flow is a very mature which is far beyond human ability, process in silicon turnkey design. The computers are increasingly used to aid in ASIC design flow and its various steps in the design and optimization processes. It is VLSI engineering that we describe below no longer efficient to use manual design are based on best practices and proven techniques, in which each layer is hand methodologies in ASIC chip designs. -
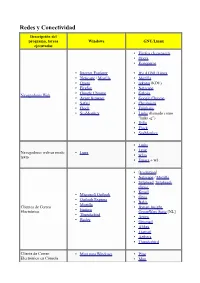
Redes Y Conectividad Descripción Del Programa, Tareas Windows GNU/Linux Ejecutadas • Firefox (Iceweasel) • Opera • Konqueror
Redes y Conectividad Descripción del programa, tareas Windows GNU/Linux ejecutadas • Firefox (Iceweasel) • Opera • Konqueror • Internet Explorer • IEs 4 GNU/Linux • Netscape / Mozilla • Mozilla • Opera • rekonq (KDE) • Firefox • Netscape • Google Chrome • Galeón Navegadores Web • Avant Browser • Google Chrome • Safari • Chromium • Flock • Epiphany • SeaMonkey • Links (llamado como "links -g") • Dillo • Flock • SeaMonkey • Links • • Lynx Navegadores web en modo Lynx • texto w3m • Emacs + w3. • [Evolution] • Netscape / Mozilla • Sylpheed , Sylpheed- claws. • Kmail • Microsoft Outlook • Gnus • Outlook Express • Balsa • Mozilla Clientes de Correo • Bynari Insight • Eudora Electrónico GroupWare Suite [NL] • Thunderbird • Arrow • Becky • Gnumail • Althea • Liamail • Aethera • Thunderbird Cliente de Correo • Mutt para Windows • Pine Electrónico en Cónsola • Mutt • Gnus • de , Pine para Windows • Elm. • Xemacs • Liferea • Knode. • Pan • Xnews , Outlook, • NewsReader Lector de noticias Netscape / Mozilla • Netscape / Mozilla. • Sylpheed / Sylpheed- claws • MultiGet • Orbit Downloader • Downloader para X. • MetaProducts Download • Caitoo (former Kget). Express • Prozilla . • Flashget • wxDownloadFast . • Go!zilla • Kget (KDE). Gestor de Descargas • Reget • Wget (console, standard). • Getright GUI: Kmago, QTget, • Wget para Windows Xget, ... • Download Accelerator Plus • Aria. • Axel. • Httrack. • WWW Offline Explorer. • Wget (consola, estándar). GUI: Kmago, QTget, Extractor de Sitios Web Teleport Pro, Webripper. Xget, ... • Downloader para X. •