Automated Malware Analysis Report for Recovered Bin2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

RACF Tips Volume 3, Issue 1, January 2009
Volume 3 Issue 1 IPS RSH RACF T January For Administrators, Auditors, and Analysts 2009 Specifying a Replacement ID used to change a file's attributes for Program Control, APF Authorized, and Shared Library. with IRRRID00 . To generate commands to delete an ID and all references to it, use RACF's IRRRID00 utility. You simply enter the ID in the SYSIN DD Temporary Access with statement of the IRRRID00 job like so: CONNECT REVOKE(date) //SYSIN DD * USERX You may occasionally need to permit a user temporary access to a resource. One way to do If USERX is the owner of a profile or connect, so is to grant a group access to the resource IRRRID00 generates commands like: and connect the user to that group with a revoke date. The command to set the connect revoke CONNECT RDSADM GROUP(RACFSTC) OWNER(?USERX) date would look something like this: In these cases, you need to change ?USERX to CONNECT USERA GROUP(TEMPACC) REVOKE(1/20/09) a valid replacement ID. This can be done manually or with ISPF EDIT CHANGE. On the date specified with the revoke, RACF will no longer allow the user to have the access Alternatively, you can tell IRRRID00 which permitted to the group. If you want to remove the replacement ID to use when it builds the revoke date but leave the connect intact, enter: commands. If, for instance, you want to replace every occurrence of USERX with USERJ, enter CONNECT USERA GROUP(TEMPACC) NOREVOKE the following in the SYSIN DD: A banking client of ours used this capability to //SYSIN DD * govern access to APF-authorized libraries. -

December 8, 2017 NOTICE to BIDDERS Sealed
December 8, 2017 NOTICE TO BIDDERS Sealed proposals will be received by the Board of Water and Light (BWL) up to 2:00 P.M., local time, Tuesday, 01/16/18, for furnishing: RFP Specification: L-5402a REFURBISHED COMBUSTION TURBINE GENERATOR (RCTG) Proposals must be in full accordance with the enclosed Request for Proposal. You are hereby invited to submit a firm fixed Price Proposal (not subject to economic price adjustment) on or before the Bid Due Date listed above, to furnish all design, engineering, labor, supervision, materials, supplies, equipment, and all other services necessary for the REBURBISHED COMBUSTION TURBINE GENERATOR as defined in this request. Proposals shall be submitted in a non-protected, Adobe format and e-mailed to [email protected]. For ease of identification, enter “RFP Title- Bidder’s Name” in the subject line of your e-mail proposal. You will receive an automatic reply to your submittal which confirms the BWL has received your emailed message. Any electronic Proposals must be received by due date/time deadline to be accepted. Electronic Proposals received after deadline will be rejected. ELECTRONIC PROPOSALS SUBMITTED TO OTHER EMAIL ADDRESSES WILL NOT BE ACCEPTED. DO NOT CARBON-COPY (CC) OTHER BWL, KRAMER MANAGEMENT, OR SARGENT & LUNDY REPRESENTATIVES ON PROPOSALS SUBMITTED TO THE SEALED BIDS INBOX. Hard copy proposals are required to be submitted by the next business day after the bid due date and in accordance with the following requirements: “ORIGINAL” Proposal, seven (7) copies and two (2) CD’s containing all proposal documents. Do not include copies of the other BWL RFP documents in your proposal package. -

LS-09EN. OS Permissions. SUID/SGID/Sticky. Extended Attributes
Operating Systems LS-09. OS Permissions. SUID/SGID/Sticky. Extended Attributes. Operating System Concepts 1.1 ys©2019 Linux/UNIX Security Basics Agenda ! UID ! GID ! Superuser ! File Permissions ! Umask ! RUID/EUID, RGID/EGID ! SUID, SGID, Sticky bits ! File Extended Attributes ! Mount/umount ! Windows Permissions ! File Systems Restriction Operating System Concepts 1.2 ys©2019 Domain Implementation in Linux/UNIX ! Two types domain (subjects) groups ! User Domains = User ID (UID>0) or User Group ID (GID>0) ! Superuser Domains = Root ID (UID=0) or Root Group ID (root can do everything, GID=0) ! Domain switch accomplished via file system. ! Each file has associated with it a domain bit (SetUID bit = SUID bit). ! When file is executed and SUID=on, then Effective UID is set to Owner of the file being executed. When execution completes Efective UID is reset to Real UID. ! Each subject (process) and object (file, socket,etc) has a 16-bit UID. ! Each object also has a 16-bit GID and each subject has one or more GIDs. ! Objects have access control lists that specify read, write, and execute permissions for user, group, and world. Operating System Concepts 1.3 ys©2019 Subjects and Objects Subjects = processes Objects = files (regular, directory, (Effective UID, EGID) devices /dev, ram /proc) RUID (EUID) Owner permissions (UID) RGID-main (EGID) Group Owner permissions (GID) +RGID-list Others RUID, RGID Others ID permissions Operating System Concepts 1.4 ys©2019 The Superuser (root) • Almost every Unix system comes with a special user in the /etc/passwd file with a UID=0. This user is known as the superuser and is normally given the username root. -

Towards an Open Collaboration Service Framework Liu, Sandy; Spencer, Bruce; Du, Weichang; Chi, Chihung
NRC Publications Archive Archives des publications du CNRC Towards an open collaboration service framework Liu, Sandy; Spencer, Bruce; Du, Weichang; Chi, Chihung This publication could be one of several versions: author’s original, accepted manuscript or the publisher’s version. / La version de cette publication peut être l’une des suivantes : la version prépublication de l’auteur, la version acceptée du manuscrit ou la version de l’éditeur. For the publisher’s version, please access the DOI link below./ Pour consulter la version de l’éditeur, utilisez le lien DOI ci-dessous. Publisher’s version / Version de l'éditeur: https://doi.org/10.1109/CTS.2011.5928668 2011 International Conference on Collaboration Technologies and Systems (CTS), pp. 77-85, 2011-06-01 NRC Publications Record / Notice d'Archives des publications de CNRC: https://nrc-publications.canada.ca/eng/view/object/?id=d3ac87ef-c3aa-4dd7-be83-af00e5338270 https://publications-cnrc.canada.ca/fra/voir/objet/?id=d3ac87ef-c3aa-4dd7-be83-af00e5338270 Access and use of this website and the material on it are subject to the Terms and Conditions set forth at https://nrc-publications.canada.ca/eng/copyright READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THIS WEBSITE. L’accès à ce site Web et l’utilisation de son contenu sont assujettis aux conditions présentées dans le site https://publications-cnrc.canada.ca/fra/droits LISEZ CES CONDITIONS ATTENTIVEMENT AVANT D’UTILISER CE SITE WEB. Questions? Contact the NRC Publications Archive team at [email protected]. If you wish to email the authors directly, please see the first page of the publication for their contact information. -

Version 7.8-Systemd
Linux From Scratch Version 7.8-systemd Created by Gerard Beekmans Edited by Douglas R. Reno Linux From Scratch: Version 7.8-systemd by Created by Gerard Beekmans and Edited by Douglas R. Reno Copyright © 1999-2015 Gerard Beekmans Copyright © 1999-2015, Gerard Beekmans All rights reserved. This book is licensed under a Creative Commons License. Computer instructions may be extracted from the book under the MIT License. Linux® is a registered trademark of Linus Torvalds. Linux From Scratch - Version 7.8-systemd Table of Contents Preface .......................................................................................................................................................................... vii i. Foreword ............................................................................................................................................................. vii ii. Audience ............................................................................................................................................................ vii iii. LFS Target Architectures ................................................................................................................................ viii iv. LFS and Standards ............................................................................................................................................ ix v. Rationale for Packages in the Book .................................................................................................................... x vi. Prerequisites -

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -
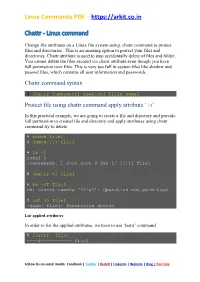
Chattr Linux Command
Linux Commands PDF – https://arkit.co.in Chattr - Linux command Change file attributes on a Linux file system using, chattr command to protect files and directories. This is an amazing option to protect your files and directories. Chattr attribute is used to stop accidentally delete of files and folder. You cannot delete the files secured via chattr attribute even though you have full permission over files. This is very use full in system files like shadow and passwd files, which contains all user information and passwords. Chattr command syntax # chattr [operator] [switch] [file name] Protect file using chattr command apply attribute ‘+i’ In this practical example, we are going to create a file and directory and provide full permission to created file and directory and apply attributes using chattr command try to delete. # touch file1 # chmod 777 file1 # ls -l total 0 -rwxrwxrwx. 1 root root 0 Jan 17 17:11 file1 # chattr +i file1 # rm -rf file1 rm: cannot remove ‘file1’: Operation not permitted # cat >> file1 -bash: file1: Permission denied List applied attributes In order to list the applied attributes, we have to use ‘lsattr’ command # lsattr file1 ----i----------- file1 Follow Us on social media: Facebook | Twitter | Reddit | LinkedIn | Website | Blog | YouTube Linux Commands PDF – https://arkit.co.in Apply attributes and append the file As we see above example when we apply an attribute ‘+i’ we cannot append, modify and delete file. Apply attribute ‘+a’ then we can append the file but we cannot delete the file. Let us see the example -

Basic Linux Security
Basic Linux Security Roman Bohuk University of Virginia What is Linux? • An open source operating system • Project started by Linus Torvalds kernel • Kernel: core program that controls everything else (controls processes, i/o between applications) • Not to be confused with Unix – commercial OS • Unix-like / *nix – broad term encompassing both Unix and Linux “Flavors” • Timeline: https://tinyurl.com/LinuxDT VM Setup • Get the VM from a flashdrive or install your own version • Login with user:UV@cnsR0cks! • 2 ways to connect it to the internet and give SSH access. In the VM network settings, select • NAT • The machine “proxies” the traffic through your NIC • Add port 22 in the port forwarding settings, and SSH to localhost • Bridged Connection • The machine has its own IP on the LAN, and you can connect to it remotely • If you want to set up a bridged connection, type ifconfig to find the MAC address, and add it at https://netreg.itc.virginia.edu/ (Register a device for network access)i VM Setup What happens when Linux boots? • BIOS looks for and executes a Master Boot Record (MBR) • MBR loads GRUB, the Linux bootloader which loads and runs the kernel • Kernel mounts the filesystem, executes the programs in /sbin/init • The init file runs the Linux at a specific “runlevel” • The runlevel-specific programs are executed from /etc/rc.d/rc*.d/ • 0 – halt • 1 – single-user mode • 2 – multiuser mode (no networking) • 3 – full multiuser mode • 5 – GUI • 6 – reboot Runlevels • Practice: who -r # prints out the current runlevel init * # changes the runlevel to * who -Ha # lists the users who are logged in Breaking Into Things Why? So you can defend it. -

Linux Pocket Guide.Pdf
3rd Edition Linux Pocket Guide ESSENTIAL COMMANDS Daniel J. Barrett 3RD EDITION Linux Pocket Guide Daniel J. Barrett Linux Pocket Guide by Daniel J. Barrett Copyright © 2016 Daniel Barrett. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebasto‐ pol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promo‐ tional use. Online editions are also available for most titles (http://safaribook‐ sonline.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editor: Nan Barber Production Editor: Nicholas Adams Copyeditor: Jasmine Kwityn Proofreader: Susan Moritz Indexer: Daniel Barrett Interior Designer: David Futato Cover Designer: Karen Montgomery Illustrator: Rebecca Demarest June 2016: Third Edition Revision History for the Third Edition 2016-05-27: First Release See http://oreilly.com/catalog/errata.csp?isbn=9781491927571 for release details. The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Linux Pocket Guide, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. While the publisher and the author have used good faith efforts to ensure that the information and instructions contained in this work are accurate, the publisher and the author disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work. Use of the information and instructions contained in this work is at your own risk. If any code samples or other technology this work contains or describes is subject to open source licenses or the intellec‐ tual property rights of others, it is your responsibility to ensure that your use thereof complies with such licenses and/or rights. -

Common Administrative Commands in Red Hat Enterprise Linux 5, 6, 7, and 8
Common administrative commands in Red Hat Enterprise Linux 5, 6, 7, and 8 System basics Kernel, boot, and hardware Basic configuration File systems, volumes, and disks TASK RHEL TASK RHEL TASK RHEL TASK RHEL /etc/sysconfig/rhn/systemid 5 6 append 1 or s or init=/bin/bash Graphical system-config-* 5 6 ext3 5 View 5 6 subscription to kernel cmdline configuration Default file information subscription-manager identity 6 7 8 Single user/ tools gnome-control-center 7 8 ext4 6 system rescue mode append 1 or s or rd.break or rhnreg_ks 6 init=/bin/bash to kernel 7 8 Text-based xfs 7 8 cmdline configuration system-config-*-tui 5 6 Configure 1, 3 tools rhn_register 5 6 7 8 ssm create 7 subscription Shut down shutdown 5 6 7 8 2 system system-config-printer 5 6 7 subscription-manager 6 7 8 Configure gdisk 7 8 printer Create/modify systemctl poweroff 7 8 gnome-control-center 8 hwbrowser 5 Power off disk partitions ssm_create 8 system system-config-date 5 6 sosreport poweroff 5 6 7 8 fdisk 5 6 7 8 5 6 7 8 dmidecode parted timedatectl 7 8 View system systemctl halt 7 8 Configure time Halt system profile lstopo and date ssm create 7 8 6 7 8 date 5 6 7 8 lscpu halt 5 6 7 8 Format disk partition mkfs.filesystem_type (ext4, xfs) gnome-control-center 8 5 6 7 8 cat/proc/cpuinfo systemctl reboot 7 8 8 mkswap lshw Reboot system /etc/ntp.conf 5 6 reboot 5 6 7 8 xfs_fsr 6 7 8 View RHEL ntpdate 5 6 7 Defragment version /etc/redhat-release 5 6 7 8 Configure /etc/inittab 5 6 disk space copy data to new file system information default run Synchronize timedatectl fsck (look for ‘non-contiguous 5 6 7 8 level/target time and date 7 8 systemctl set-default 7 8 /etc/chrony.conf inodes’) 1 Be aware of potential issues when using subscription-manager on Red Hat Enterprise Linux 5: https://access.redhat.com/solutions/129003. -

Understanding Stakeholders' Objectives in Software Product Line
From Intentions to Decisions: Understanding Stakeholders’ Objectives in Software Product Line Configuration Mahdi Noorian1, Ebrahim Bagheri2, Weichang Du1 University of New Brunswick, Fredericton,Canada1 Ryerson University, Toronto, Canada2 [email protected], [email protected], [email protected] Abstract—Software Product Line (SPL) engineering promotes undesirable ones from the perspective of stakeholders [4]. the systematic and large-scale reuse of design and implementation The software product line research community has developed artifacts. Feature models are one of the main artefact of SPLE effective methods for configuring product line models such approach which essentially characterize the similar and variant functional and operational specifications of the product family. as feature models. The basic assumption of these methods and Given the complexity of the variabilities represented by feature tools is that the set of initial desirable features is already known models, it is often hard for the stakeholders to analyze a feature to the stakeholders or at least to the software product designers model and identify the features that are most important for their [5]. However in reality regardless of the configuration process purpose. So, given large-scale software product families, one of itself, the selection of the initial set of desirable features is the important questions is how and what features should be selected for the target software product from the product family. both important and very difficult to do for the stakeholders and To address this problem, we adopt concepts from the domain of product designers. The selection of these features depends on goal-oriented requirement engineering and base feature selection the restrictions placed by and objectives of the stakeholders and decisions on software stakeholders’ intentions and expectations. -

Access Control Topics
CIT 480: Securing Computer Systems Access Control Topics 1. Access Control Matrix 2. ACLs and Capabilities 3. Role-Based Access Control (RBAC) 4. Discretionary Access Control (DAC) 5. Examples: UNIX, Windows, Android, SQL 6. Mandatory Access Control (MAC) 7. Hardware Protection Access Control Access control is the selective restriction of access to an information, computational, or physical resource. Access Control is Pervasive Application Middleware Operating System Hardware Access Control is Pervasive 1. Application • Complex, custom security policy. • Ex: Amazon account: wish list, reviews, CC 2. Middleware • Database, system libraries, 3rd party software • Ex: Credit card authorization center 3. Operating System • File ACLs, IPC, Android permissions system, SELinux 4. Hardware • Memory management, hardware device access. Access Control Matrices A table that defines permissions. – Each row of this table is associated with a subject, which is a user, group, or system that can perform actions. – Each column of the table is associated with an object, which is a file, directory, document, device, resource, or any other entity for which we want to define access rights. – Each cell of the table is then filled with the access rights for the associated combination of subject and object. – Access rights can include actions such as reading, writing, copying, executing, deleting, and annotating. – An empty cell means that no access rights are granted. Example Access Control Matrix Access Control Lists (ACLs) An ACL defines, for each object, o, a list, L, called o’s access control list, which enumerates all the subjects that have access rights for o and, for each such subject, s, gives the access rights that s has for object o.