TB169 (Rev1) - Using Centroid Linux
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
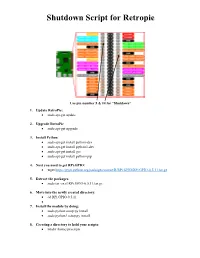
Shutdown Script for Retropie
Shutdown Script for Retropie Use pin number 5 & 14 for “Shutdown” 1. Update RetroPie: • sudo apt-get update 2. Upgrade RetroPie • sudo apt-get upgrade 3. Install Python • sudo apt-get install python-dev • sudo apt-get install python3-dev • sudo apt-get install gcc • sudo apt-get install python-pip 4. Next you need to get RPi.GPIO: • wget https://pypi.python.org/packages/source/R/RPi.GPIO/RPi.GPIO-0.5.11.tar.gz 5. Extract the packages: • sudo tar -zxvf RPi.GPIO-0.5.11.tar.gz 6. Move into the newly created directory: • cd RPi.GPIO-0.5.11 • 7. Install the module by doing: • sudo python setup.py install • sudo python3 setup.py install 8. Creating a directory to hold your scripts: • mkdir /home/pi/scripts 9. Call our script shutdown.py (it is written in python). Create and edit the script by doing: • sudo nano /home/pi/scripts/shutdown.py The content of the script: Paste it in the blank area #!/usr/bin/python import RPi.GPIO as GPIO import time import subprocess # we will use the pin numbering to match the pins on the Pi, instead of the # GPIO pin outs (makes it easier to keep track of things) GPIO.setmode(GPIO.BOARD) # use the same pin that is used for the reset button (one button to rule them all!) GPIO.setup(5, GPIO.IN, pull_up_down = GPIO.PUD_UP) oldButtonState1 = True while True: #grab the current button state buttonState1 = GPIO.input(5) # check to see if button has been pushed if buttonState1 != oldButtonState1 and buttonState1 == False: subprocess.call("shutdown -h now", shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE) oldButtonState1 = buttonState1 time.sleep(.1) Press CRTL X Then Y and Enter 10. -

RACF Tips Volume 3, Issue 1, January 2009
Volume 3 Issue 1 IPS RSH RACF T January For Administrators, Auditors, and Analysts 2009 Specifying a Replacement ID used to change a file's attributes for Program Control, APF Authorized, and Shared Library. with IRRRID00 . To generate commands to delete an ID and all references to it, use RACF's IRRRID00 utility. You simply enter the ID in the SYSIN DD Temporary Access with statement of the IRRRID00 job like so: CONNECT REVOKE(date) //SYSIN DD * USERX You may occasionally need to permit a user temporary access to a resource. One way to do If USERX is the owner of a profile or connect, so is to grant a group access to the resource IRRRID00 generates commands like: and connect the user to that group with a revoke date. The command to set the connect revoke CONNECT RDSADM GROUP(RACFSTC) OWNER(?USERX) date would look something like this: In these cases, you need to change ?USERX to CONNECT USERA GROUP(TEMPACC) REVOKE(1/20/09) a valid replacement ID. This can be done manually or with ISPF EDIT CHANGE. On the date specified with the revoke, RACF will no longer allow the user to have the access Alternatively, you can tell IRRRID00 which permitted to the group. If you want to remove the replacement ID to use when it builds the revoke date but leave the connect intact, enter: commands. If, for instance, you want to replace every occurrence of USERX with USERJ, enter CONNECT USERA GROUP(TEMPACC) NOREVOKE the following in the SYSIN DD: A banking client of ours used this capability to //SYSIN DD * govern access to APF-authorized libraries. -

LS-09EN. OS Permissions. SUID/SGID/Sticky. Extended Attributes
Operating Systems LS-09. OS Permissions. SUID/SGID/Sticky. Extended Attributes. Operating System Concepts 1.1 ys©2019 Linux/UNIX Security Basics Agenda ! UID ! GID ! Superuser ! File Permissions ! Umask ! RUID/EUID, RGID/EGID ! SUID, SGID, Sticky bits ! File Extended Attributes ! Mount/umount ! Windows Permissions ! File Systems Restriction Operating System Concepts 1.2 ys©2019 Domain Implementation in Linux/UNIX ! Two types domain (subjects) groups ! User Domains = User ID (UID>0) or User Group ID (GID>0) ! Superuser Domains = Root ID (UID=0) or Root Group ID (root can do everything, GID=0) ! Domain switch accomplished via file system. ! Each file has associated with it a domain bit (SetUID bit = SUID bit). ! When file is executed and SUID=on, then Effective UID is set to Owner of the file being executed. When execution completes Efective UID is reset to Real UID. ! Each subject (process) and object (file, socket,etc) has a 16-bit UID. ! Each object also has a 16-bit GID and each subject has one or more GIDs. ! Objects have access control lists that specify read, write, and execute permissions for user, group, and world. Operating System Concepts 1.3 ys©2019 Subjects and Objects Subjects = processes Objects = files (regular, directory, (Effective UID, EGID) devices /dev, ram /proc) RUID (EUID) Owner permissions (UID) RGID-main (EGID) Group Owner permissions (GID) +RGID-list Others RUID, RGID Others ID permissions Operating System Concepts 1.4 ys©2019 The Superuser (root) • Almost every Unix system comes with a special user in the /etc/passwd file with a UID=0. This user is known as the superuser and is normally given the username root. -
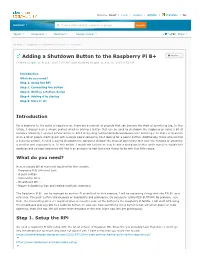
Adding a Shutdown Button to the Raspberry Pi B+ Version 1
Welcome, Guest Log in Register Activity Translate Content Search within content, members or groups Search Topics Resources Members Design Center Store All Places > Raspberry Pi > Raspberry Pi Projects > Documents Adding a Shutdown Button to the Raspberry Pi B+ Version 1 Created by ipv1 on Aug 4, 2015 3:05 AM. Last modified by ipv1 on Aug 18, 2015 9:52 AM. Introduction What do you need? Step 1. Setup the RPi Step 2. Connecting the button Step 3. Writing a Python Script Step 4. Adding it to startup Step 5. More to do Introduction For a beginner to the world of raspberry pi, there are a number of projects that can become the start of something big. In this article, I discuss such a simple project which is adding a button that can be used to shutdown the raspberry pi using a bit of software tinkering. I wrote a similar article in 2013 at my blog “embeddedcode.wordpress.com” and its got its share of attention since a lot of people starting out with a single board computer, kept looking for a power button. Additionally, those who wanted a headless system, needed a way to shutdown the computer without the mess of connecting to it over the network or attaching a monitor and keyboard to it. In this article, I revisit the tutorial on how to add a shutdown button while trying to explain the workings and perhaps beginners will find it an amusing to add find more things to do with this little recipe. What do you need? Here is a basic bill of materials required for this exercise. -

Shutdown Policies with Power Capping for Large Scale Computing Systems Anne Benoit, Laurent Lefèvre, Anne-Cécile Orgerie, Issam Raïs
Shutdown Policies with Power Capping for Large Scale Computing Systems Anne Benoit, Laurent Lefèvre, Anne-Cécile Orgerie, Issam Raïs To cite this version: Anne Benoit, Laurent Lefèvre, Anne-Cécile Orgerie, Issam Raïs. Shutdown Policies with Power Capping for Large Scale Computing Systems. Euro-Par: International European Conference on Parallel and Distributed Computing, Aug 2017, Santiago de Compostela, Spain. pp.134 - 146, 10.1109/COMST.2016.2545109. hal-01589555 HAL Id: hal-01589555 https://hal.archives-ouvertes.fr/hal-01589555 Submitted on 18 Sep 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Shutdown policies with power capping for large scale computing systems Anne Benoit1, Laurent Lef`evre1, Anne-C´ecileOrgerie2, and Issam Ra¨ıs1 1 Univ. Lyon, Inria, CNRS, ENS de Lyon, Univ. Claude-Bernard Lyon 1, LIP 2 CNRS, IRISA, Rennes, France Abstract Large scale distributed systems are expected to consume huge amounts of energy. To solve this issue, shutdown policies constitute an appealing approach able to dynamically adapt the resource set to the actual workload. However, multiple constraints have to be taken into account for such policies to be applied on real infrastructures, in partic- ular the time and energy cost of shutting down and waking up nodes, and power capping to avoid disruption of the system. -

Version 7.8-Systemd
Linux From Scratch Version 7.8-systemd Created by Gerard Beekmans Edited by Douglas R. Reno Linux From Scratch: Version 7.8-systemd by Created by Gerard Beekmans and Edited by Douglas R. Reno Copyright © 1999-2015 Gerard Beekmans Copyright © 1999-2015, Gerard Beekmans All rights reserved. This book is licensed under a Creative Commons License. Computer instructions may be extracted from the book under the MIT License. Linux® is a registered trademark of Linus Torvalds. Linux From Scratch - Version 7.8-systemd Table of Contents Preface .......................................................................................................................................................................... vii i. Foreword ............................................................................................................................................................. vii ii. Audience ............................................................................................................................................................ vii iii. LFS Target Architectures ................................................................................................................................ viii iv. LFS and Standards ............................................................................................................................................ ix v. Rationale for Packages in the Book .................................................................................................................... x vi. Prerequisites -

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -
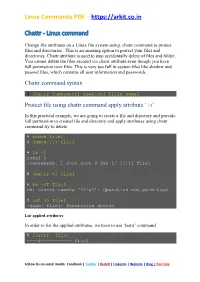
Chattr Linux Command
Linux Commands PDF – https://arkit.co.in Chattr - Linux command Change file attributes on a Linux file system using, chattr command to protect files and directories. This is an amazing option to protect your files and directories. Chattr attribute is used to stop accidentally delete of files and folder. You cannot delete the files secured via chattr attribute even though you have full permission over files. This is very use full in system files like shadow and passwd files, which contains all user information and passwords. Chattr command syntax # chattr [operator] [switch] [file name] Protect file using chattr command apply attribute ‘+i’ In this practical example, we are going to create a file and directory and provide full permission to created file and directory and apply attributes using chattr command try to delete. # touch file1 # chmod 777 file1 # ls -l total 0 -rwxrwxrwx. 1 root root 0 Jan 17 17:11 file1 # chattr +i file1 # rm -rf file1 rm: cannot remove ‘file1’: Operation not permitted # cat >> file1 -bash: file1: Permission denied List applied attributes In order to list the applied attributes, we have to use ‘lsattr’ command # lsattr file1 ----i----------- file1 Follow Us on social media: Facebook | Twitter | Reddit | LinkedIn | Website | Blog | YouTube Linux Commands PDF – https://arkit.co.in Apply attributes and append the file As we see above example when we apply an attribute ‘+i’ we cannot append, modify and delete file. Apply attribute ‘+a’ then we can append the file but we cannot delete the file. Let us see the example -

Basic Linux Security
Basic Linux Security Roman Bohuk University of Virginia What is Linux? • An open source operating system • Project started by Linus Torvalds kernel • Kernel: core program that controls everything else (controls processes, i/o between applications) • Not to be confused with Unix – commercial OS • Unix-like / *nix – broad term encompassing both Unix and Linux “Flavors” • Timeline: https://tinyurl.com/LinuxDT VM Setup • Get the VM from a flashdrive or install your own version • Login with user:UV@cnsR0cks! • 2 ways to connect it to the internet and give SSH access. In the VM network settings, select • NAT • The machine “proxies” the traffic through your NIC • Add port 22 in the port forwarding settings, and SSH to localhost • Bridged Connection • The machine has its own IP on the LAN, and you can connect to it remotely • If you want to set up a bridged connection, type ifconfig to find the MAC address, and add it at https://netreg.itc.virginia.edu/ (Register a device for network access)i VM Setup What happens when Linux boots? • BIOS looks for and executes a Master Boot Record (MBR) • MBR loads GRUB, the Linux bootloader which loads and runs the kernel • Kernel mounts the filesystem, executes the programs in /sbin/init • The init file runs the Linux at a specific “runlevel” • The runlevel-specific programs are executed from /etc/rc.d/rc*.d/ • 0 – halt • 1 – single-user mode • 2 – multiuser mode (no networking) • 3 – full multiuser mode • 5 – GUI • 6 – reboot Runlevels • Practice: who -r # prints out the current runlevel init * # changes the runlevel to * who -Ha # lists the users who are logged in Breaking Into Things Why? So you can defend it. -

Linux Pocket Guide.Pdf
3rd Edition Linux Pocket Guide ESSENTIAL COMMANDS Daniel J. Barrett 3RD EDITION Linux Pocket Guide Daniel J. Barrett Linux Pocket Guide by Daniel J. Barrett Copyright © 2016 Daniel Barrett. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebasto‐ pol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promo‐ tional use. Online editions are also available for most titles (http://safaribook‐ sonline.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editor: Nan Barber Production Editor: Nicholas Adams Copyeditor: Jasmine Kwityn Proofreader: Susan Moritz Indexer: Daniel Barrett Interior Designer: David Futato Cover Designer: Karen Montgomery Illustrator: Rebecca Demarest June 2016: Third Edition Revision History for the Third Edition 2016-05-27: First Release See http://oreilly.com/catalog/errata.csp?isbn=9781491927571 for release details. The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Linux Pocket Guide, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. While the publisher and the author have used good faith efforts to ensure that the information and instructions contained in this work are accurate, the publisher and the author disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work. Use of the information and instructions contained in this work is at your own risk. If any code samples or other technology this work contains or describes is subject to open source licenses or the intellec‐ tual property rights of others, it is your responsibility to ensure that your use thereof complies with such licenses and/or rights. -

LAB MANUAL for Computer Network
LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design, troubleshooting, modeling and evaluation of computer networks. In this course, students are going to experiment in a real test-bed networking environment, and learn about network design and troubleshooting topics and tools such as: network addressing, Address Resolution Protocol (ARP), basic troubleshooting tools (e.g. ping, ICMP), IP routing (e,g, RIP), route discovery (e.g. traceroute), TCP and UDP, IP fragmentation and many others. Student will also be introduced to the network modeling and simulation, and they will have the opportunity to build some simple networking models using the tool and perform simulations that will help them evaluate their design approaches and expected network performance. S.No Experiment 1 Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. 2 Study of Network Devices in Detail. 3 Study of network IP. 4 Connect the computers in Local Area Network. 5 Study of basic network command and Network configuration commands. 6 Configure a Network topology using packet tracer software. 7 Configure a Network topology using packet tracer software. 8 Configure a Network using Distance Vector Routing protocol. 9 Configure Network using Link State Vector Routing protocol. Hardware and Software Requirement Hardware Requirement RJ-45 connector, Climping Tool, Twisted pair Cable Software Requirement Command Prompt And Packet Tracer. EXPERIMENT-1 Aim: Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. -

Common Administrative Commands in Red Hat Enterprise Linux 5, 6, 7, and 8
Common administrative commands in Red Hat Enterprise Linux 5, 6, 7, and 8 System basics Kernel, boot, and hardware Basic configuration File systems, volumes, and disks TASK RHEL TASK RHEL TASK RHEL TASK RHEL /etc/sysconfig/rhn/systemid 5 6 append 1 or s or init=/bin/bash Graphical system-config-* 5 6 ext3 5 View 5 6 subscription to kernel cmdline configuration Default file information subscription-manager identity 6 7 8 Single user/ tools gnome-control-center 7 8 ext4 6 system rescue mode append 1 or s or rd.break or rhnreg_ks 6 init=/bin/bash to kernel 7 8 Text-based xfs 7 8 cmdline configuration system-config-*-tui 5 6 Configure 1, 3 tools rhn_register 5 6 7 8 ssm create 7 subscription Shut down shutdown 5 6 7 8 2 system system-config-printer 5 6 7 subscription-manager 6 7 8 Configure gdisk 7 8 printer Create/modify systemctl poweroff 7 8 gnome-control-center 8 hwbrowser 5 Power off disk partitions ssm_create 8 system system-config-date 5 6 sosreport poweroff 5 6 7 8 fdisk 5 6 7 8 5 6 7 8 dmidecode parted timedatectl 7 8 View system systemctl halt 7 8 Configure time Halt system profile lstopo and date ssm create 7 8 6 7 8 date 5 6 7 8 lscpu halt 5 6 7 8 Format disk partition mkfs.filesystem_type (ext4, xfs) gnome-control-center 8 5 6 7 8 cat/proc/cpuinfo systemctl reboot 7 8 8 mkswap lshw Reboot system /etc/ntp.conf 5 6 reboot 5 6 7 8 xfs_fsr 6 7 8 View RHEL ntpdate 5 6 7 Defragment version /etc/redhat-release 5 6 7 8 Configure /etc/inittab 5 6 disk space copy data to new file system information default run Synchronize timedatectl fsck (look for ‘non-contiguous 5 6 7 8 level/target time and date 7 8 systemctl set-default 7 8 /etc/chrony.conf inodes’) 1 Be aware of potential issues when using subscription-manager on Red Hat Enterprise Linux 5: https://access.redhat.com/solutions/129003.