Cryptsim: Simulators for Classic Rotor Ciphers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Historical Ciphers • A
ECE 646 - Lecture 6 Required Reading • W. Stallings, Cryptography and Network Security, Chapter 2, Classical Encryption Techniques Historical Ciphers • A. Menezes et al., Handbook of Applied Cryptography, Chapter 7.3 Classical ciphers and historical development Why (not) to study historical ciphers? Secret Writing AGAINST FOR Steganography Cryptography (hidden messages) (encrypted messages) Not similar to Basic components became modern ciphers a part of modern ciphers Under special circumstances modern ciphers can be Substitution Transposition Long abandoned Ciphers reduced to historical ciphers Transformations (change the order Influence on world events of letters) Codes Substitution The only ciphers you Ciphers can break! (replace words) (replace letters) Selected world events affected by cryptology Mary, Queen of Scots 1586 - trial of Mary Queen of Scots - substitution cipher • Scottish Queen, a cousin of Elisabeth I of England • Forced to flee Scotland by uprising against 1917 - Zimmermann telegram, America enters World War I her and her husband • Treated as a candidate to the throne of England by many British Catholics unhappy about 1939-1945 Battle of England, Battle of Atlantic, D-day - a reign of Elisabeth I, a Protestant ENIGMA machine cipher • Imprisoned by Elisabeth for 19 years • Involved in several plots to assassinate Elisabeth 1944 – world’s first computer, Colossus - • Put on trial for treason by a court of about German Lorenz machine cipher 40 noblemen, including Catholics, after being implicated in the Babington Plot by her own 1950s – operation Venona – breaking ciphers of soviet spies letters sent from prison to her co-conspirators stealing secrets of the U.S. atomic bomb in the encrypted form – one-time pad 1 Mary, Queen of Scots – cont. -

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -

The the Enigma Enigma Machinemachine
TheThe EnigmaEnigma MachineMachine History of Computing December 6, 2006 Mike Koss Invention of Enigma ! Invented by Arthur Scherbius, 1918 ! Adopted by German Navy, 1926 ! Modified military version, 1930 ! Two Additional rotors added, 1938 How Enigma Works Scrambling Letters ! Each letter on the keyboard is connected to a lamp letter that depends on the wiring and position of the rotors in the machine. ! Right rotor turns before each letter. How to Use an Enigma ! Daily Setup – Secret settings distributed in code books. ! Encoding/Decoding a Message Setup: Select (3) Rotors ! We’ll use I-II-III Setup: Rotor Ring Settings ! We’ll use A-A-A (or 1-1-1). Rotor Construction Setup: Plugboard Settings ! We won’t use any for our example (6 to 10 plugs were typical). Setup: Initial Rotor Position ! We’ll use “M-I-T” (or 13-9-20). Encoding: Pick a “Message Key” ! Select a 3-letter key (or indicator) “at random” (left to the operator) for this message only. ! Say, I choose “M-C-K” (or 13-3-11 if wheels are printed with numbers rather than letters). Encoding: Transmit the Indicator ! Germans would transmit the indicator by encoding it using the initial (daily) rotor position…and they sent it TWICE to make sure it was received properly. ! E.g., I would begin my message with “MCK MCK”. ! Encoded with the daily setting, this becomes: “NWD SHE”. Encoding: Reset Rotors ! Now set our rotors do our chosen message key “M-C-K” (13-3-11). ! Type body of message: “ENIGMA REVEALED” encodes to “QMJIDO MZWZJFJR”. -

Historical Cryptography 2
Historical cryptography 2 CSCI 470: Web Science • Keith Vertanen Overview • Historical cryptography – WWI • Zimmerman telegram – WWII • Rise of the cipher machines • Engima • Allied encryption 2 WWI: Zimmermann Telegram • 1915, U-boat sinks Lusitania – 1,198 drown including 128 US – Germany agrees to surface 1st • 1916, new Foreign Minister – Arthur Zimmermann • 1917, unrestricted submarine warfare – Zimmermann hatches plan • Keep American busy at home • Persuade Mexico to: invade US and invite Japan to attack US as well Arthur Zimmermann 3 4 Mechanization of secret writing • Pencil and paper – Security limited by what humans can do quickly and accurately in the heat of battle • Enter the machine Thomas Jefferson's wheel cipher Captain Midnight's Code-o-Graph 5 Enigma machine • Enigma cipher machine – 1918, patented by German engineer Arthur Scherbius Arthur Scherbius – A electrical/mechanical implementation of a polyalphabetic substitution cipher 6 7 Enigma rotors • Rotor (wheel, drum) – Monoalphabetic substitution cipher implemented via complex wiring pattern – One of 26 initial positions – Geared: rotates after each letter • Rotor set – 3 rotors in 3!=6 possible orders • Eventually increased to 3 out of 5 • Navy used even more – Possible keys: • 3! * 263 = 6 * 17,576 = 105,456 8 Enigma plugboard • Plugboard – Operator inserts cables to swap letters – Initially 6 cables • Swaps 6 pairs of letters • Leaves 14 letters unswapped – Possible configurations: • 100,391,791,500 • Total keys: – 17,576 * 6 * 100,391,791,500 ≈ 10,000,000,000,000,000 -

CHAPTER 8 a History of Communications Security in New Zealand
CHAPTER 8 A History of Communications Security in New Zealand By Eric Morgon Early Days “Admiralty to Britannia Wellington. Comence hostilities at once with Germany in accordance with War Standing Orders.” This is an entry in the cipher log of HMS Philomel dated 5 August, 1914. HMS Philomel was a cruiser of the Royal Navy and took part in the naval operations in the Dardanelles during the ill-fated Gallipoli campaign. Philomel’s cipher logs covering the period 1914 to 1918 make interesting reading and show how codes and ciphers were used extensively by the Royal Navy during World War 1. New Zealand officers and ratings served on board Philomel and thus it can be claimed that the use of codes and ciphers by Philomel are part of the early history of communications security in New Zealand. Immediately following the codes to Navy Office, the Senior Naval Officer New Zealand was advised that Cypher G and Cypher M had been compromised and that telegrams received by landline in these ciphers were to be recoded in Code C before transmission by Wireless Telegraphy (W/T) Apparently Cypher G was also used for cables between the Commonwealth Navy Board in Melbourne and he British Consul in Noumea. The Rear Admiral Commanding Her Majesty’s Australian Fleet instructed that when signalling by WT every odd numbered code group was to be a dummy. It is interesting to note that up until the outbreak of hostilities no provision had been made for the storage of code books or for precautions to prevent them from falling into enemy hands. -

History and Modern Cryptanalysis of Enigma's Pluggable Reflector
History and Modern Cryptanalysis of Enigma’s Pluggable Reflector Olaf Ostwald and Frode Weierud ABSTRACT: The development history of Umkehrwalze Dora (UKWD), Enigma's pluggable reflector, is presented from the first ideas in the mid-1920s to the last development plans and its actual usage in 1945. An Enigma message in three parts, enciphered with UKWD and intercepted by the British on 11 March 1945, is shown. The successful recovery of the key of this message is described. Modern computer-based cryptanalysis is used to recover the wiring of the unknown “Uncle Dick,” which the British called this field-rewirable reflector. The attack is based on the known ciphertext and plaintext pair from the first part of the intercept. After recovery of the unknown reflector wiring and the daily key the plaintext of the second part of the message is revealed. KEYWORDS: Enigma, cryptanalysis, Uncle Dick, Umkehrwalze Dora, UKWD, unsolved ciphers Address correspondence to Frode Weierud, Bjerkealleen 17, 1385 Asker, Norway. Email: [email protected] 1. Introduction Uncle Dick,1 as it was called by the codebreakers of Bletchley Park (BP), or Umkehrwalze Dora (UKWD), as designated by the Germans, was the nickname of a special pluggable reflector,2 used as the leftmost wheel within the scrambler 3 of the Enigma. The electro-mechanical cipher machine Enigma (from Greek αίνιγµα for “riddle”) was the backbone of the German Wehrmacht during World War II. Arthur Scherbius, a German promoted electrical engineer and inventor of considerable standing, invented Enigma in 1918 [14]. Subsequently it was improved and then used by all three parts of the German armed forces, namely army (Heer), air force (Luftwaffe), and military navy (Kriegsmarine), for enciphering and deciphering of their secret messages. -
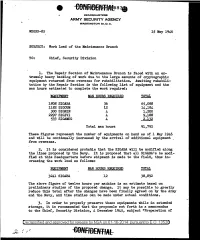
Work Load of the Maintenance Branch
HEADQUARTERS ARMY SECURITY AGENCY WASHINGTON 25, D. C. WDGSS-85 15 May 1946 SUBJECT: Work Load of the Maintenance Branch TO: Chief, Security Division 1. The Repair Section of Maintenance Branch is .faced with an ex tremely heavy backlog of' work due to the large amounts of' cryptographic equipment returned from overseas for rehabilitation. Awaiting rehabili tation by the Repair Section is the followi~g list of equipment and the man hours estimated to complete the work required.: EQUIPMENT MAN HOURS REQUIRED TOTAL 1808 SIGABA 36 65,088 1182 SIGCUM 12 14,184 300 SIGNIN 4 1,200 2297 SIGIVI 4 9,188 533 SIGAMUG 4, 2,132 Total man hours 91,792 These figures represent the number of equipments on hand as of 1 May 1946 and will be continually increased by the arrival of additional equipment . from overseas. 2. It is considered probable that the SIGABA will be modified along the lines proposed by the Navy. It is proposed that all SIGABA 1s be modi fied at this Headquarters before shipment is made to the field, thus in creasing the work load as follows: EQUIPMENT MAN HOURS REQUIRED 3241 SIGABA 12 The above figure of' twelve hours per machine is an estimate based on preliminary studies of' the proposed change. It may be possible to greatly reduce this total af'ter the changes have been f inaJ.ly agreed on by the .Army and the Navy, and time studies can be made under actual conditions. ,3. In order to properly preserve these equipments while in extended storage, it is recommended that the proposals set .forth in a memorandum to the Chief, Security Division, 4 December 1945, subject "Preparation of Declassified and approved for release by NSA on 01-16-2014 pursuantto E .0. -

The Mathematics of the Enigma Machine Student: Emily Yale Supervisor: Dr Tariq Jarad
The Mathematics of the Enigma Machine Student: Emily Yale Supervisor: Dr Tariq Jarad The Enigma Machine is a mechanical encryption device used mainly by the German Forces during WWII to turn plaintext into complex ciphertext, the same machine could be used to do the reverse (Trappe and Washington, 2006). Invented by the German engineer Arthur Scherbius at the end of World War I the cipher it produced was marketed as ‘unbreakable’ (Trappe and Washington, 2006). Adopted by the German military forces, it worked by layering a number of substitution ciphers that were decided by an excess of 1.589x1021 machine settings. With help from Polish and French mathematicians, the cryptographer named Alan Turing created a machine known as the ‘Bombe’ which helped to reduce the time taken to ‘break’ an Enigma cipher (Imperial War Museums, 2015). The report this poster is based on focuses on the mathematics of the Enigma machine as well as the methods used to find the settings for a piece of ciphertext. Advantages and disadvantages of the Enigma code will be explored, alternative cipher machines are considered. Aims and Objective Bombe (Group Theory) • A brief insight into Cryptography The Bombe was a machine that could be used to find the key to an • The history of the Enigma Machine Enigma cipher. It was modelled on the Polish machine, Bomba, which • The mechanism of the Enigma Machine could also do same before Enigma was enhanced. Bombe could find the • The mathematics of the Bombe settings on an Enigma machine that had been used to encrypt a • Understanding Group Theory ciphertext. -

National Security Agency (NSA) Document: a History of U.S
Description of document: National Security Agency (NSA) document: A History of U.S. Communications Security Post World-War II – released under Mandatory Declassification Review (MDR) Released date: February 2011 Posted date: 07-November-2011 Source of document: National Security Agency Declassification Services (DJ5) Suite 6884, Bldg. SAB2 9800 Savage Road Ft. George G. Meade, MD, 20755-6884 Note: Although the titles are similar, this document should not be confused with the David G. Boak Lectures available: http://www.governmentattic.org/2docs/Hist_US_COMSEC_Boak_NSA_1973.pdf The governmentattic.org web site (“the site”) is noncommercial and free to the public. The site and materials made available on the site, such as this file, are for reference only. The governmentattic.org web site and its principals have made every effort to make this information as complete and as accurate as possible, however, there may be mistakes and omissions, both typographical and in content. The governmentattic.org web site and its principals shall have neither liability nor responsibility to any person or entity with respect to any loss or damage caused, or alleged to have been caused, directly or indirectly, by the information provided on the governmentattic.org web site or in this file. The public records published on the site were obtained from government agencies using proper legal channels. Each document is identified as to the source. Any concerns about the contents of the site should be directed to the agency originating the document in question. GovernmentAttic.org is not responsible for the contents of documents published on the website. -----------------------------------------------------------------------~~) '; I .:· ! _k:::._,.l COMitfll A HISTORY OF U.S. -

A Review Analysis of Two Fish Algorithm Cryptography Quantum Computing
IJCSN International Journal of Computer Science and Network, Volume 6, Issue 1, February 2017 ISSN (Online) : 2277-5420 www.IJCSN.org Impact Factor: 1.5 A Review Analysis of Two Fish Algorithm Cryptography Quantum Computing 1 Sukhvandna Abhi, 2 Umesh Sehgal 1, 2 GNA University Phagwara Abstract - In this analysis paper we tend to describe the evolution of cryptography ranging from the start of the twentieth century and continued into this day. Last 10 years quantum computing can begin to trounce everyday computers, resulting in breakthroughs in computer science. Specifically within the cryptography used from 1900 till the tip of war II.Quantum technologies supply immoderate secure communication sensors of unprecedented exactness and computers that square measure exponentially a lot of powerful than any mainframe for a given task. We compare the performance of the 5 AES finalists one kind of common software package platforms current 32-bit CPUs and high finish sixty four bit CPUs. Our intent is to indicate roughly however the algorithm’s speeds compare across a range of CPUs.The future of cryptography primarily based within the field of natural philosophy and by analyzing the hope to supply a allot of complete image of headed the 2 mail algorithms utilized in cryptography world. Keywords - Cryptography ancient secret writing system 1. Introduction regulated wherever the primary letter is substituted by the last letter, the second letter by the second to last letter then ryptography may be a subject that has been studied on. as a result of it's a monoalphabetic cipher and may and applied since ancient Roman times, and have only 1 doable key, this cipher is comparatively weak; Canalysis into higher coding ways continues to the but this wasn't a viable concern throughout its time as current day. -

TICOM: the Last Great Secret of World War II Randy Rezabek Version of Record First Published: 27 Jul 2012
This article was downloaded by: [Randy Rezabek] On: 28 July 2012, At: 18:04 Publisher: Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Intelligence and National Security Publication details, including instructions for authors and subscription information: http://www.tandfonline.com/loi/fint20 TICOM: The Last Great Secret of World War II Randy Rezabek Version of record first published: 27 Jul 2012 To cite this article: Randy Rezabek (2012): TICOM: The Last Great Secret of World War II, Intelligence and National Security, 27:4, 513-530 To link to this article: http://dx.doi.org/10.1080/02684527.2012.688305 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.tandfonline.com/page/terms-and- conditions This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae, and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. Intelligence and National Security Vol. 27, No. 4, 513–530, August 2012 TICOM: The Last Great Secret of World War II RANDY REZABEK* ABSTRACT Recent releases from the National Security Agency reveal details of TICOM, the mysterious 1945 operation targeting Germany’s cryptologic secrets. -

SIS and Cipher Machines: 1930 – 1940
SIS and Cipher Machines: 1930 – 1940 John F Dooley Knox College Presented at the 14th Biennial NSA CCH History Symposium, October 2013 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 United States License. 1 Thursday, November 7, 2013 1 The Results of Friedman’s Training • The initial training regimen as it related to cipher machines was cryptanalytic • But this detailed analysis of the different machine types informed the team’s cryptographic imaginations when it came to creating their own machines 2 Thursday, November 7, 2013 2 The Machines • Wheatstone/Plett Machine • M-94 • AT&T machine • M-138 and M-138-A • Hebern cipher machine • M-209 • Kryha • Red • IT&T (Parker Hitt) • Purple • Engima • SIGABA (M-134 and M-134-C) • B-211(and B-21) 3 Thursday, November 7, 2013 3 The Wheatstone/Plett Machine • polyalphabetic cipher disk with gearing mechanism rotates the inner alphabet. • Plett’s improvement is to add a second key and mixed alphabet to the inner ring. • Friedman broke this in 1918 Principles: (a) The inner workings of a mechanical cryptographic device can be worked out using a paper and pencil analog of the device. (b) if there is a cycle in the mechanical device (say for particular cipher alphabets), then that cycle can be discovered by analysis of the paper and pencil analog. 4 Thursday, November 7, 2013 4 The Army M-94 • Traces its roots back to Jefferson and Bazieres • Used by US Army from 1922 to circa 1942 • 25 mixed alphabets. Disk order is the key.