Report on the Evolution of Co-Engineering Standards
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

20-24 Buffalo Main Street: Smart Corridor Plan
Buffalo Main Street: Smart Corridor Plan Final Report | Report Number 20-24 | August 2020 NYSERDA Department of Transportation Buffalo Main Street: Smart Corridor Plan Final Report Prepared for: New York State Energy Research and Development Authority New York, NY Robyn Marquis Project Manager and New York State Department of Transportation Albany, NY Mark Grainer Joseph Buffamonte, Region 5 Project Managers Prepared by: Buffalo Niagara Medical Campus, Inc. & WSP USA Inc. Buffalo, New York NYSERDA Report 20-24 NYSERDA Contract 112009 August 2020 NYSDOT Project No. C-17-55 Notice This report was prepared by Buffalo Niagara Medical Campus, Inc. in coordination with WSP USA Inc., in the course of performing work contracted for and sponsored by the New York State Energy Research and Development Authority (hereafter “NYSERDA”). The opinions expressed in this report do not necessarily reflect those of NYSERDA or the State of New York, and reference to any specific product, service, process, or method does not constitute an implied or expressed recommendation or endorsement of it. Further, NYSERDA, the State of New York, and the contractor make no warranties or representations, expressed or implied, as to the fitness for particular purpose or merchantability of any product, apparatus, or service, or the usefulness, completeness, or accuracy of any processes, methods, or other information contained, described, disclosed, or referred to in this report. NYSERDA, the State of New York, and the contractor make no representation that the use of any product, apparatus, process, method, or other information will not infringe privately owned rights and will assume no liability for any loss, injury, or damage resulting from, or occurring in connection with, the use of information contained, described, disclosed, or referred to in this report. -

Iso/Iec/Ieee 29148:2011(E)
INTERNATIONAL ISO/IEC/ STANDARD IEEE 29148 First edition 2011-12-01 Systems and software engineering — Life cycle processes — Requirements engineering Ingénierie des systèmes et du logiciel — Processus du cycle de vie — Ingénierie des exigences Reference number ISO/IEC/IEEE 29148:2011(E) © ISO/IEC 2011 © IEEE 2011 ISO/IEC/IEEE 29148:2011(E) PDF disclaimer This PDF file may contain embedded typefaces. In accordance with Adobe's licensing policy, this file may be printed or viewed but shall not be edited unless the typefaces which are embedded are licensed to and installed on the computer performing the editing. In downloading this file, parties accept therein the responsibility of not infringing Adobe's licensing policy. The ISO Central Secretariat, the IEC Central Office and IEEE do not accept any liability in this area. Adobe is a trademark of Adobe Systems Incorporated. Details of the software products used to create this PDF file can be found in the General Info relative to the file; the PDF-creation parameters were optimized for printing. Every care has been taken to ensure that the file is suitable for use by ISO member bodies and IEEE members. In the unlikely event that a problem relating to it is found, please inform the ISO Central Secretariat or IEEE at the address given below. COPYRIGHT PROTECTED DOCUMENT © ISO/IEC 2011 © IEEE 2011 All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm, without permission in writing from ISO, IEC or IEEE at the respective address below. -

Concept of Operations
MAASTO TPIMS Project CONCEPT OF OPERATIONS July 15, 2016 MAASTO TPIMS Project Concept of Operations Table of Contents Introduction....................................................................................................................................1 1.0 Purpose and Overview .......................................................................................................2 2.0 Scope .................................................................................................................................5 3.0 Referenced Documents......................................................................................................5 4.0 Background ........................................................................................................................8 4.1 National Truck Parking Issues ........................................................................................8 4.1.1 Safety Concerns ......................................................................................................8 4.1.2 Economic Concerns...............................................................................................10 4.2 National Research Programs........................................................................................11 4.3 Current Systems ...........................................................................................................12 5.0 User-Oriented Project Development.................................................................................12 5.1 TPIMS Partnership -

Building Functional Safety Into Industrial Robotics
BUILDING FUNCTIONAL SAFETY INTO INDUSTRIAL ROBOTICS Rian Whitton Principal Analyst EXECUTIVE SUMMARY TABLE OF CONTENTS Functional safety is critical to many modern robotic applications and will become more so. In the near future, many robots will run in areas where they interact directly Executive Summary ................................1 and indirectly with workers, and the tasks they perform will disproportionately relate The Market for Industrial Robotics ...........2 The Potential of the Robotics Industry .....................2 to production logistics and moving goods for the general public. If a robot malfunctions, New Robots, New Demands ...................................4 there is a risk to the surrounding workers, to product safety, and to public safety. This Functional Safety Is Crucial for the Industry to Meet risk amplifies as robots are increasingly required to handle multiple tasks and navigate Its Potential ............................................................5 Regulations .............................................................6 crowded environments. So, mitigating safety risks under these conditions will become Embedded Systems for Robotics ..............7 a fundamental requirement that cannot be addressed without considering security as RTOS and the Benefits of Microkernel an integral part of robot design. Architecture ............................................................8 Hypervisors-as-a-Solution .......................................9 This is where functional safety of the underlying software and -

Concept of Operations for C-ITS Core Functions
Research Report AP-R479-15 Concept of Operations for C-ITS Core Functions Concept of Operations for C-ITS Core Functions Prepared by Publisher Freek Faber and David Green Austroads Ltd. Level 9, 287 Elizabeth Street Sydney NSW 2000 Australia Project Manager Phone: +61 2 9264 7088 [email protected] Stuart Ballingall www.austroads.com.au Abstract About Austroads This document defines the core functions of the C-ITS platform Austroads’ purpose is to: including their objectives and capabilities. It identifies user needs • promote improved Australian and New Zealand transport and describes how the system will operate. outcomes • provide expert technical input to national policy The Concept of Operations is intended to be an input to future development on road and road transport issues decision making and system engineering documents, including • promote improved practice and capability by road system requirements and design documentation. agencies • promote consistency in road and road agency operations. Austroads membership comprises the six state and two territory road transport and traffic authorities, the Commonwealth Department of Infrastructure and Regional Development, the Australian Local Government Association, and NZ Transport Agency. Austroads is governed by a Board consisting of the chief executive officer (or an alternative senior executive officer) of each of its eleven member organisations: • Roads and Maritime Services New South Wales Keywords • Roads Corporation Victoria Cooperative ITS, C-ITS, Concept of Operations, ConOps, core • Department of Transport and Main Roads Queensland system, core functions. • Main Roads Western Australia ISBN 978-1-925294-13-2 • Department of Planning, Transport and Infrastructure South Australia Austroads Project No. -

Concept of Operations
PART TWO: CONCEPT OF OPERATIONS SECTION 1.0 - EMERGENCY MANAGEMENT Introduction The process of preventing, preparing for, responding to, and recovering from hazardous materials incidents employs the traditional emergency management principles utilized in addressing any emergency or disaster. For these efforts to be successful, a wide variety of government agencies (from all levels), as well as the private sector, must cooperate and integrate their response capabilities. Phases of Part Two of the Tool Kit describes how this overall concept of operations is employed Emergency within California. The four phases of emergency management employed before, Management during, and after an incident are identified as Preparedness, Response, Recovery, and Mitigation (as illustrated below). PREPAREDNESS MITIGATION RESPONSE RECOVERY The four phases, as used within California's emergency management system, are described briefly below and in more detail in the following sections. Preparedness: The key to effective emergency management is rapid, well planned responses. The preparedness phase consists of conducting hazard or risk analyses; identification of agency roles and responsibilities; developing emergency response plans and procedures; mutual aid or assistance agreements; response resources; and conducting training, drills, and exercises to test the plans, procedures, and training. It also includes a medical surveillance program to protect the health and safety of hazardous materials responders. Preparedness also includes the development of -

AP 210 Domain Specific Entities (Subtypes of Generic Resource Entities) and Rules Are Added to Meet the Domain Requirements
NISTIR 7677 AP210 Edition 2 Concept of Operations Jamie Stori SFM Technology, Inc. Urbana, Illinois Kevin Brady National Institute of Standards and Technology Electronics and Electrical Engineering Laboratory Thomas Thurman Rockwell Collins, Cedar Rapids, Iowa 1 NISTIR 7677 AP210 Edition 2 Concept of Operations Jamie Stori SFM Technology, Inc. Urbana, Illinois Kevin Brady National Institute of Standards and Technology Electronics and Electrical Engineering Laboratory Thomas Thurman Rockwell Collins, Cedar Rapids, Iowa April 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Director 2 AP210 Edition 2 Concept of Operations This document provides information to support organizations wishing to develop data exchange and sharing implementations using AP 210. Contents 1. Background..................................................................................................................................... 5 2. Product types that are supported by AP 210 ..................................................................................... 6 3. Life cycle stages that are supported by AP 210 ................................................................................ 7 4. Disciplines that are supported by AP 210 ........................................................................................ 8 5. Product data types that are supported by AP 210 ............................................................................. 9 5.1 Information Rights Data ........................................................................................... -
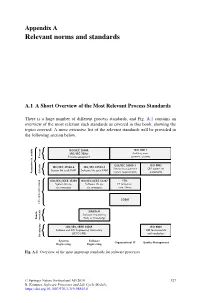
Relevant Norms and Standards
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

Standards Action Layout SAV3438.Fp5
PUBLISHED WEEKLY BY THE AMERICAN NATIONAL STANDARDS INSTITUTE 25 West 43rd Street, NY, NY 10036 VOL. 34, #38 September 19, 2003 Contents American National Standards Call for Comment on Standards Proposals................................................. 2 Call for Comment Contact Information........................................................ 5 Initiation of Canvasses.................................................................................. 7 Final Actions .................................................................................................. 8 Project Initiation Notification System (PINS) .............................................. 10 International Standards ISO Draft Standards ...................................................................................... 13 ISO Newly Published Standards .................................................................. 15 Registration of Organization Names in the U.S. ........................................... 18 Proposed Foreign Government Regulations ................................................ 18 Information Concerning.................................................................................. 19 Standards Action is now available via the World Wide Web For your convenience Standards Action can now be down- loaded from the following web address: http://www.ansi.org/news_publications/periodicals/standard s_action/standards_action.aspx?menuid=7 American National Standards Call for comment on proposals listed This section solicits your comments on proposed -

System Concept of Operations (CONOPS) for the Automated Computer Network Defence (ARMOUR) Technology Demonstration (TD) Contract
System Concept of Operations (CONOPS) for the Automated Computer Network Defence (ARMOUR) Technology Demonstration (TD) Contract Author: D. Tremblay General Dynamics Prepared By: General Dynamics Mission Systems–Canada Land and Joint Solutions 1020–68th Avenue N.E. Calgary, Alberta T2E 8P2 Contractor's Document Number: 740928 Contractor’s date of publication: 21 April 2017 CDRL: SD0049 PWGSC Contract Number: W7717-115274/001/SV Contract Project Manager: Darcy Simmelink Technical Authority: Natalie Nakhla Disclaimer: The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2017-C169 July 2017 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2017. © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2017. 740928F System Concept of Operations (CONOPS) for the Automated Computer Network Defence (ARMOUR) Technology Demonstration ((TD) Contract Contract No. W7714-115274/001/SV CDRL SD009 This document was prepared by General Dynamiccs Mission Systems – Canada under Public Works and Government Service Canada Contract No. W7714- 115274/001/SV. Use and dissemination of the information herein shall be in accordance with the Terms and Conditions Contracct No. W7714-115274/001/SV. © HER MAJESTY THE QUEEN IN RIGHT OF CANADA (2017) Prepared For: Defence Research & Development Caanada (DRDC) - Ottawa 3701 Carling Avenue Ottawa, Ontario K1A 0Z4 Prepared By: General Dynamics Mission Systems – Canada Land and Joint Soluttions 1020-68th Avenue N.E. -

Concept of Operations Versus Operations Concept: How Do You Choose?
PROCEEDINGS OF SPIE SPIEDigitalLibrary.org/conference-proceedings-of-spie Concept of operations versus operations concept: how do you choose? Hill, Alexis, Flagey, Nicolas, Barden, Sam, Erickson, Darren, Sivanandam, Suresh, et al. Alexis Hill, Nicolas Flagey, Sam Barden, Darren Erickson, Suresh Sivanandam, Kei Szeto, "Concept of operations versus operations concept: how do you choose?," Proc. SPIE 11450, Modeling, Systems Engineering, and Project Management for Astronomy IX, 114502U (13 December 2020); doi: 10.1117/12.2563469 Event: SPIE Astronomical Telescopes + Instrumentation, 2020, Online Only Downloaded From: https://www.spiedigitallibrary.org/conference-proceedings-of-spie on 26 Jan 2021 Terms of Use: https://www.spiedigitallibrary.org/terms-of-use Concept of Operations versus Operations Concept: How do you choose? Alexis Hill*a,b, Nicolas Flagey b, Sam Barden b, Darren Ericksona, Suresh Sivanandamc,d, Kei Szeto b,a aNational Research Council of Canada, Herzberg Astronomy and Astrophysics, Victoria, BC, Canada bCFHT Corporation, Corporation, 65-1238 Mamalahoa Hwy, Kamuela, Hawaii 96743, USA cDepartment of Astronomy and Astrophysics, University of Toronto, 50 St. George St. Toronto, ON, Canada dDunlap Institute for Astronomy and Astrophysics, University of Toronto, 50 St. George St., Toronto, ON, Canada ABSTRACT Systems engineering as a discipline is relatively new in the ground-based astronomy community and is becoming more common as projects become larger, more complex and more geographically diverse. Space and defense industry projects have been using systems engineering for much longer, however those projects don’t necessarily map well onto ground- based astronomy projects, for various reasons. Fortunately, many of the processes and tools have been documented by INCOSE, NASA, SEBoK and other organizations, however there can be incomplete or conflicting definitions within the process and implementation is not always clear. -

Iso/Iec/Ieee 29148:2011(E)
Important Notice This document is a copyrighted IEEE Standard. IEEE hereby grants permission to the recipient of this document to reproduce this document for purposes of standardization activities. No further reproduction or distribution of this document is permitted without the express written permission of IEEE Standards Activities. Prior to any use of this standard, in part or in whole, by another standards development organization, permission must first be obtained from the IEEE Standards Activities Department ([email protected]). IEEE Standards Activities Department 445 Hoes Lane Piscataway, NJ 08854, USA INTERNATIONAL ISO/IEC/ STANDARD IEEE 29148 First edition 2011-12-01 Systems and software engineering — Life cycle processes — Requirements engineering Ingénierie des systèmes et du logiciel — Processus du cycle de vie — Ingénierie des exigences Reference number ISO/IEC/IEEE 29148:2011(E) © ISO/IEC 2011 © IEEE 2011 ISO/IEC/IEEE 29148:2011(E) PDF disclaimer This PDF file may contain embedded typefaces. In accordance with Adobe's licensing policy, this file may be printed or viewed but shall not be edited unless the typefaces which are embedded are licensed to and installed on the computer performing the editing. In downloading this file, parties accept therein the responsibility of not infringing Adobe's licensing policy. The ISO Central Secretariat, the IEC Central Office and IEEE do not accept any liability in this area. Adobe is a trademark of Adobe Systems Incorporated. Details of the software products used to create this PDF file can be found in the General Info relative to the file; the PDF-creation parameters were optimized for printing.