Master of Ceremony Summit MC
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AGCO Opens Nominations for 11Th Annual Operator of the Year
August 25, 2016 AGCO Opens Nominations for 11th Annual Operator of the Year DULUTH, Ga. (Aug. 25, 2016) – AGCO Corporation (NYSE:AGCO) is now accepting nominations for 2016 Operator of the Year, which recognizes hard-working applicators across the country. These professionals spend long hours in the field every season, using technologically advanced application machinery like a RoGator® or a TerraGator® to accurately and efficiently apply fertilizer and crop protection products on millions of crop acres, helping farmers achieve their best possible yield. This year’s winner will receive a grand prize of a brand new Harley-Davidson® motorcycle. “We’re proud to have recognized the industry’s top application professionals for 10 years, and look forward to meeting even more of them this year. This award highlights the important part these professionals play in helping farmers meet the challenge of providing food, fiber and fuel to the world,” stated Richard Kohnen, director of tactical marketing at AGCO. The company is now in its 11th year as the sole sponsor of the program. The Operator of the Year program is open to all ag retailers and custom applicators in the United States, regardless of the machine brands in their application fleets.** A panel of judges from AGCO will evaluate nominees based on their performance — both on and off the field — including criteria such as skill, dedication and customer service as well as community involvement. “While we can select only one winner, everyone in agriculture succeeds with the expertise and effort these professionals contribute to our industry. In the past, managers and customers of applicator finalists told us their nominee had extensive knowledge of their customers’ operations and the willingness to do whatever it takes to accomplish the job,” Kohnen stated. -

AGCO Dealer Scholarship Program
Ford Fund and Ford Trucks Built Ford Tough – FFA Scholarship Program ELIGIBILITY: Students who are pursuing a two-year or four-year degree in any major. Applicants must apply online and then visit their local participating Ford Truck dealer for signature and dealer code. Qualified students will be considered for all FFA scholarships, but in order to be considered for the Built Ford Tough – FFA Scholarship they must have a Ford dealer signature and dealer code on the required Signature Page. To find a participating dealer who has identified a local FFA Chapter, visit www.ffa.org. Applicants unable to find a participating dealer online may obtain a signature and dealer code from their local Ford dealer to make them eligible for one of five national scholarships. AWARD: Up to 500 scholarships available at $1,000 each to be awarded on behalf of participating Ford Truck dealers. Five additional national scholarships at $1,000 each will be available to students who do not have a participating Ford Truck dealer in their area but did obtain a Ford dealer signature and dealer code. In addition to scholarships, Ford Trucks will provide grants to FFA chapters in each of the six (6) NAAE regions. Qualifying chapters must have a local Ford dealer participating in the scholarship program and a minimum of three (3) applicants for the Built Ford Tough – FFA Scholarship. Visit www.naae.org for more details. SPONSOR BIO: Ford has been building tough trucks that move and service America since 1908. 2012 marks the 64th year of FFA support by Ford Trucks, Ford Motor Company Fund and participating Ford Truck dealers, and 35 years as the best-selling line of trucks for F-Series. -

AGCO Corporation (Exact Name of Registrant As Specified in Its Charter)
Table of Contents As filed with the Securities and Exchange Commission on June 4, 2004 Registration No. 333-113560 UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 PRE-EFFECTIVE AMENDMENT NO. 1 to Form S-3 REGISTRATION STATEMENT UNDER THE SECURITIES ACT OF 1933 AGCO Corporation (Exact name of registrant as specified in its charter) Delaware 58-1960019 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 4205 River Green Parkway Duluth, Georgia 30096 (770) 813-9200 (Address, including zip code, and telephone number, including area code, of registrant’s principal executive offices) Stephen D. Lupton Senior Vice President of Corporate Development and General Counsel AGCO Corporation 4205 River Green Parkway Duluth, Georgia 30096 (770) 813-9200 (Name, address, including zip code, and telephone number, including area code, of agent for service) With copies to: W. Brinkley Dickerson, Jr. Troutman Sanders LLP 600 Peachtree Street, Suite 5200 Atlanta, Georgia 30308-2216 (404) 885-3000 Approximate date of commencement of proposed sale to the public: From time to time after the effective date of this registration statement. If the only securities being registered on this form are being offered pursuant to dividend or interest reinvestment plans, please check the following box. [ ] If any of the securities being registered on this form are to be offered on a delayed or continuous basis pursuant to Rule 415 under the Securities Act of 1933, as amended, other than securities offered only in connection with dividend or interest reinvestment plans, check the following box. [X] If this form is filed to register additional securities for an offering pursuant to Rule 462(b) under the Securities Act, please check the following box and list the Securities Act registration statement number of the earlier effective registration statement for the same offering. -

The Motor Vehicle Assembly and Component Sector Anthony Black
An Industrial Strategy for the Motor Vehicle Assembly and Component Sector Anthony Black ARCHIV 113599 jy Project IDRO - Li1. AN INDUSTRIAL S TRA TEGY FOR THE MOTOR VEHICLE ASSEMBLY AND COMPONENTSECTORS Anthony Black Industrial Strategy Project Development Policy Research Unit School of Economics University of Cape Town 1994 I UCT] rNEsJ / UCT Press(Pty) Ltd Universityof Cape Town PrivateBag Rondebosch 7700 SouthAfrica All rights are reserved.No part of this publicationmay be reproduced, stored in a retrieval system, or transmittedin any form or by any means, electronic, mechanical, photocopying, icording or otherwise, without priorpermission of thepublisher. Cover illustration: Taken from Gavin Young's sculpture, "Hoerrikwagga", standing near JamesonHall on the University of Cape Towncampus. Typesetting: Hayley Viljoen Coverdesign: KarrenVisser Printed and bound by CredaPress Copyright: IndustrialStrategy Project First published: 1994 ISBN: 0-7992-1575-9 EDITORIAL COMMENT This report is one ofa seriesproduced by the Industrial StrategyProject. The ISP has its origins in the Economic Trends Research Group, a collective of economists and other social scientists convenedby the Congress of South African Trade Unions in 1986. COSATU, under attack for its support for sanctions, initially asked these researchers to examinethe impact ofenforced isolation on the South African economy. It soon became clear that sanctions were a small aspect of the problems besetting the South African economy, and the work of the Economic Trends Research Group expanded into a full-blown analysis of South Africa's economiccrisis. The poor performance of South Africa's manufacturing sector loomed large in the litany of problems bedeviling the South African economy. The 1980s had been, in economic terms, something of a lost decade. -

HARYANA April 2010 HARYANA April 2010
HARYANA April 2010 HARYANA April 2010 Investment climate of a state is determined by a mix of factors • Skilled and cost-effective labour • Procedures for entry and exit of firms • Labour market flexibility • Industrial regulation, labour regulation, other • Labour relations government regulations • Availability of raw materials and natural • Certainty about rules and regulations resources • Security, law and order situation Resources/Inputs Regulatory framework Investment climate of a state Incentives to industry Physical and social infrastructure • Condition of physical infrastructure such as • Tax incentives and exemptions power, water, roads, etc. • Investment subsidies and other incentives • Information infrastructure such as • Availability of finance at cost-effective terms telecom, IT, etc. • Incentives for foreign direct investment (FDI) • Social infrastructure such as educational and • Profitability of the industry medical facilities 2 HARYANA April 2010 Contents Advantage Haryana State economy and socio-economic profile Infrastructure status State policies and incentives Business opportunities Doing business in Haryana 3 ADVANTAGE HARYANA Haryana April 2010 Haryana – State profile • Covering an area of 44,212 sq km, Haryana surrounds the national capital city, New Delhi, from three sides. • Chandigarh is Haryana’s capital city. Punjab also has its administrative capital in Chandigarh. Haryana has 21 administrative districts. • The Yamuna river flows along Haryana’s eastern boundary. Other important seasonal rivers flowing through the state are the Ghaggar and Markanda. • Haryana has, predominantly, extreme and dry climatic conditions, with temperature reaching up to a high of 45- 50ºC in the summer months (April-June) and falling to about 1ºC in winter (December-January). • Gurgaon, Faridabad, Karnal, Ambala, Panipat and Kurukshetra are the key districts of the state. -

We Know Agriculture Annual Report 2010 2 AGCO // Annual Report 2010
We Know Agriculture ANNUAL REPORT 2010 2 AGCO // Annual Report 2010 AGCO AT A GLANCE As the world’s largest manufacturer focused purely on agricultural equipment, AGCO is uniquely positioned to increase farm productivity through high-tech solutions for professional farmers feeding the world. KEY BUSINESS FIGURES in million $ – except per share amounts 2010 2009 Change Net sales 6,896.6 6,516.4 5.8% Income from operations 324.2 218.7 48.2% Net income attributable to AGCO Corporation and subsidiaries 220.5 135.7 62.5% Total assets 5,436.9 4,998.9 8.8% Stockholders’ equity 2,659.2 2,394.4 11.1% Earnings per share(1) 2.29 1.44 59.0% Adjusted earnings per share(2) 2.32 1.55 49.7% (1) On a diluted basis. (2) For a reconciliation of adjusted earnings per share, see footnote 2 on page 37. SALES BY PRODUCT in % Tractors 15% Parts Combines 68% 6% Application equipment 4% 4% Implements and other 3% Hay and forage SALES BY GEOGRAPHIC REGION ADJUSTED EARNINGS PER SHARE in million $ in $ (1) NA 22% 2010 2.32 SA(2) 25% 2009 1.55 EAME(3) 49% ROW(4) 4% 2008 3.95 (1) North America (3) Europe, Africa, Middle East (2) South America (4) Rest of World: Asia, Australia/New Zealand, Eastern Europe ON THE COVER In 2010, AGCO made solid progress toward meeting its long-term growth objectives. Among other things, it was a year marked by numerous combine launches and the announcement of a strategic acquisition of a state-of-the-art combine facility, proof of our accelerated commitment towards improving harvesting productivity. -

Product Design 2021 Award for Massey Ferguson MF 8S Series Tractors April 01, 2021
2021 Red Dot Product Design Award winner, commercial vehicle category, MF 8S Series of tractors Prestigious Red Dot: Product Design 2021 Award for Massey Ferguson MF 8S Series tractors April 01, 2021 Massey Ferguson, a worldwide brand of AGCO (NYSE:AGCO), is delighted to announce it is honoured to receive a Red Dot Award: Product Design 2021 for Product design, in the commercial vehicle category, for the innovative MF 8 S Series of tractors. This latest accolade follows the MF 8S.265 Dyna E-Power Exclusive winning the prestigious Tractor of the Year 2021 as well as Best Global Digital launch 2020. An international jury selected the MF 8S from thousands of entries from more than 60 countries for the Red Dot Award: Product Design 2021 Award, which is only presented to products that feature outstanding design. “We are honoured the MF 8S has been chosen to receive this special award,” says Thierry Lhotte, Vice President & Managing Director Massey Ferguson, Europe & Middle East. “With the MF 8S Series, we are defining a new era in tractor design, which the jury has distinguished with the Red Dot: Product Design 2021 Award. “Developed for farmers by farmers, following seven years of thorough testing and extensive customer consultation, the MF 8S Series combines radical designs with a practical purpose. While equipped to a superb specification, it also introduces a completely new and enhanced user experience,” adds Mr Lhotte. “The MF 8S launch was just the first milestone of our fully rejuvenated tractor range offensive. We are thrilled to have received such industry leading awards for the MF 8S together with farmers’ recognition through their choice for their new tractor. -

Massey Ferguson Introduces 5700 Global Series Tractors Equipped with Dyna-4 Transmission
Oct 15, 2019, 6:00:00 AM Massey Ferguson Introduces 5700 Global Series Tractors Equipped with Dyna-4 Transmission Livestock and hay operations will now enjoy greater efficiency from these durable workhorses New MF5710D (100 HP) and MF5711D (110 hp) mid-range tractors from Massey Ferguson feature the high-end performance of the rugged, reliable Dyna-4 transmission in a handy tractor designed for efficient loader work, hay production and general on-the-farm use. • Two Massey Ferguson® 5700 Global Series mid-range tractors are now available with the convenience of the popular Dyna-4 transmission, making them even better-suited for loader work, hay production and general on-the-farm chores. • The Dyna-4 transmission shifts smoothly through 16 forward and 16 reverse speeds without clutching, making speed and direction changes easy and efficient. Auto-Drive™ adds even more convenience during transport or field work by speed-matching the transmission to the job, while the Brake to Neutral feature lets the operator stop the tractor by merely pressing the brake pedal. • The two new models, the MF5710D (100 HP) and MF5711D (110 HP), come standard with the largest, quietest cab in their class and are loader-ready from the factory with an integrated joystick to operate any of the four available Massey Ferguson loaders. • Standard features that optimize the work they can handle and set them apart from the competition include an easy-to-read digital system information screen, advanced cab suspension for a smooth ride, three hydraulic remotes and a 540E/540/1000 PTO, plus radial tires for better traction and ride. -

The Ohio Motor Vehicle Industry
Research Office A State Affiliate of the U.S. Census Bureau The Ohio Motor Vehicle Report February 2019 Intentionally blank THE OHIO MOTOR VEHICLE INDUSTRY FEBRUARY 2019 B1002: Don Larrick, Principal Analyst Office of Research, Ohio Development Services Agency PO Box 1001, Columbus, Oh. 43216-1001 Production Support: Steven Kelley, Editor; Jim Kell, Contributor Robert Schmidley, GIS Specialist TABLE OF CONTENTS Page Executive Summary 1 Description of Ohio’s Motor Vehicle Industry 4 The Motor Vehicle Industry’s Impact on Ohio’s Economy 5 Ohio’s Strategic Position in Motor Vehicle Assembly 7 Notable Motor Vehicle Industry Manufacturers in Ohio 10 Recent Expansion and Attraction Announcements 16 The Concentration of the Industry in Ohio: Gross Domestic Product and Value-Added 18 Company Summaries of Light Vehicle Production in Ohio 20 Parts Suppliers 24 The Composition of Ohio’s Motor Vehicle Industry – Employment at the Plants 28 Industry Wages 30 The Distribution of Industry Establishments Across Ohio 32 The Distribution of Industry Employment Across Ohio 34 Foreign Investment in Ohio 35 Trends 40 Employment 42 i Gross Domestic Product 44 Value-Added by Ohio’s Motor Vehicle Industry 46 Light Vehicle Production in Ohio and the U.S. 48 Capital Expenditures for Ohio’s Motor Vehicle Industry 50 Establishments 52 Output, Employment and Productivity 54 U.S. Industry Analysis and Outlook 56 Market Share Trends 58 Trade Balances 62 Industry Operations and Recent Trends 65 Technologies for Production Processes and Vehicles 69 The Transportation Research Center 75 The Near- and Longer-Term Outlooks 78 About the Bodies-and-Trailers Group 82 Assembler Profiles 84 Fiat Chrysler Automobiles NV 86 Ford Motor Co. -

General and Bilateral Brief Hesse
1 Consulate General of India Frankfurt *** General and Bilateral Brief: 0 Hessen-India Hesse (German: Hessen) is home to one of the largest European airports (Frankfurt Airport) and also offers an excellent transport network. The state capital is Wiesbaden and the largest city is Frankfurt am Main. Frankfurt, as an international financial centre, has a strong influence on Hesse as a service region. Similarly, well-known international industrial companies define Hesse as a technology location at the heart of European markets. The important industries are automotive and supply industries, Biotechnology, Cultural and creative industries, Financial services, Aerospace, Mechanical and plant engineering, Medical technology, Tourism. Hesse also boasts beautiful nature reserves, historical castles and palaces, as well as the Rheingau vineyards which are renowned for its excellent wines all over the world. Salient Features of Hesse 1. Geography: Hesse is situated in west-central Germany, with state borders the German states of Lower Saxony, Thuringia, Bavaria, Baden-Württemberg, Rhineland-Palatinate, and North Rhine- Westphalia. It is the greenest state in Germany, as forest covers 42% of the state. Most of the population of Hessen is in the southern part in the Rhine Main Area. The principal cities of the area include Frankfurt am Main, Wiesbaden, Darmstadt, Offenbach, Hanau, Gießen, Wetzlar, and Limburg. Other major towns in Hesse are Fulda , Kassel and Marburg. The densely populated Rhine-Main region is much better developed than the rural areas in the middle and northern parts of Hesse. The most important rivers in Hesse are the Fulda and Eder rivers in the north, the Lahn in the central part of Hesse, and the Main and Rhine in the south. -
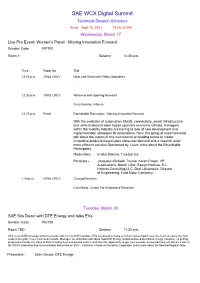
SAE WCX Digital Summit
SAE WCX Digital Summit Technical Session Schedule As of April 15, 2021 19:40:33 PM Wednesday, March 17 Live Pre Event: Women's Panel - Moving Innovation Forward Session Code WP100 Room 1 Session 12:30 p.m. Time Paper No. Title 12:15 p.m. ORAL ONLY Meet and Greet with Fellow Attendees . 12:30 p.m. ORAL ONLY Welcome and Opening Remarks Terry Barclay, Inforum 12:35 p.m. Panel Roundtable Discussion - Moving Innovation Forward With the evolution of automation, MaaS, connectivity, smart Infrastructure and vehicle electrification based upon the economic climate, managers within the mobility industry are having to look at new development and implementation strategies for innovations. Hear this group of expert panelist talk about the impact of this new normal on leading teams to create innovative products based upon consumer demand and a need for safer more efficient vehicles.Sponsored by Learn more about the Roundtable Participants Moderators - Kristin Slanina, TrueCar Inc. Panelists - Jacquelyn Birdsall, Toyota; Karen Folger, VP Automations, Bosch USA; Raelyn Holmes, R.L. Holmes Consulting LLC; Desi Ujkashevic, Director of Engineering, Ford Motor Company; 1:40 p.m. ORAL ONLY Closing Remarks Carla Bailo, Center For Automotive Research Tuesday, March 30 SAE Sits Down with DTE Energy and talks EVs Session Code WC100 Room TBD Session 11:30 a.m. With recent OEM strategy announcements and the CA 2035 mandate, EVs are posed to make a critical market impact over the next few years, but how ready is the grid? Come hear Sean Gouda, Manager, electrification -

An Evaluation of Changes in Capital Investment by Automotive Companies in Preparation for the Automotive Production and Development Programme (Apdp)
AN EVALUATION OF CHANGES IN CAPITAL INVESTMENT BY AUTOMOTIVE COMPANIES IN PREPARATION FOR THE AUTOMOTIVE PRODUCTION AND DEVELOPMENT PROGRAMME (APDP) B.S. BACELA 2012 AN EVALUATION OF CHANGES IN CAPITAL INVESTMENT BY AUTOMOTIVE COMPANIES IN PREPARATION FOR THE AUTOMOTIVE PRODUCTION AND DEVELOPMENT PROGRAMME (APDP) BY BANDILE SAKHEKILE BACELA Treatise submitted in partial fulfilment of the requirements for the degree Magister in Business Administration at the Nelson Mandela Metropolitan Business School December 2012 Promoter: DR S SIMAYI ii TABLE OF CONTENTS DECLARATION .............................................................................................................. V ABSTRACT ................................................................................................................... VI ACKNOWLEDGEMENTS ............................................................................................. VII CHAPTER 1 .................................................................................................................... 1 INTRODUCTION TO THE RESEARCH STUDY ............................................................ 1 1.1 INTRODUCTION ....................................................................................................... 1 1.2 PROBLEM STATEMENT ............................................................................................. 2 1.3 IMPORTANCE OF STUDY .......................................................................................... 3 1.4 CONCEPTUAL FRAMEWORK .....................................................................................