Mass Discovery of Android Malware Behavioral Characteristics for Detection Consideration
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Power System Zone Partitioning Based on Transmission Congestion Identification Using an Improved Spectral Clustering Algorithm
electronics Article Power System Zone Partitioning Based on Transmission Congestion Identification Using an Improved Spectral Clustering Algorithm Yifan Hu 1 , Peng Xun 1 , Wenjie Kang 2,3,4,* , Peidong Zhu 5,* , Yinqiao Xiong 1,5 and Weiheng Shi 6 1 College of Computer, National University of Defense Technology, Changsha 410073, China; [email protected] (Y.H.); [email protected] (P.X.); [email protected] (Y.X.) 2 Hunan Provincial Key Laboratory of Network Investigational Technology, Hunan Police Academy, Changsha 410138, China 3 Key Laboratory of Police Internet of Things Application Ministry of Public Security, Beijing 100089, China 4 College of Systems Engineering, National University of Defense Technology, Changsha 410073, China 5 Department of Electronic Information and Electrical Engineering, Changsha University, Changsha 410022, China 6 College of Meteorology and Oceanography, National University of Defense Technology, Nanjing 211101, China; [email protected] * Correspondence: [email protected] (W.K.); [email protected] (P.Z.) Abstract: The ever-expanding power system is developed into an interconnected pattern of power grids. Zone partitioning is an essential technique for the operation and management of such an interconnected power system. Owing to the transmission capacity limitation, transmission congestion may occur with a regional influence on power system. If transmission congestion is considered when the system is decomposed into several regions, the power consumption structure can be optimized and power system planning can be more reasonable. At the same time, power resources can be Citation: Hu, Y.; Xun, P.; Kang, W.; properly allocated and system safety can be improved. In this paper, we propose a power system zone Zhu, P.; Xiong, Y.; Shi, W. -

Genomic Surveillance: Inside China's DNA Dragnet
Genomic surveillance Inside China’s DNA dragnet Emile Dirks and James Leibold Policy Brief Report No. 34/2020 About the authors Emile Dirks is a PhD candidate in political science at the University of Toronto. Dr James Leibold is an Associate Professor and Head of the Department of Politics, Media and Philosophy at La Trobe University and a non-resident Senior Fellow at ASPI. Acknowledgements The authors would like to thank Danielle Cave, Derek Congram, Victor Falkenheim, Fergus Hanson, William Goodwin, Bob McArthur, Yves Moreau, Kelsey Munro, Michael Shoebridge, Maya Wang and Sui-Lee Wee for valuable comments and suggestions with previous drafts of this report, and the ASPI team (including Tilla Hoja, Nathan Ruser and Lin Li) for research and production assistance with the report. ASPI is grateful to the Institute of War and Peace Reporting and the US State Department for supporting this research project. What is ASPI? The Australian Strategic Policy Institute was formed in 2001 as an independent, non-partisan think tank. Its core aim is to provide the Australian Government with fresh ideas on Australia’s defence, security and strategic policy choices. ASPI is responsible for informing the public on a range of strategic issues, generating new thinking for government and harnessing strategic thinking internationally. ASPI International Cyber Policy Centre ASPI’s International Cyber Policy Centre (ICPC) is a leading voice in global debates on cyber and emerging technologies and their impact on broader strategic policy. The ICPC informs public debate and supports sound public policy by producing original empirical research, bringing together researchers with diverse expertise, often working together in teams. -

Stable Green and Red Dual-Emissions in the Single All-Inorganic Halide
Electronic Supplementary Material (ESI) for RSC Advances. This journal is © The Royal Society of Chemistry 2020 Supporting Information for Stable green and red dual-emissions in the single all-inorganic halide-mixed perovskites microsheet Manyi Zhong1, Zhuang Zhao1, Yuan Luo1, Fang Zhou3,*, Yuehua Peng1, Yanling Yin1, Weichang Zhou1,2,*, Dongsheng Tang1,2 1 School of Physics and Electronics, Key Laboratory of Low-dimensional Quantum Structures and Quantum Control of Ministry of Education, Hunan Normal University, Changsha 410081, People’s Republic of China 2 Key Laboratory for Matter Microstructure and Function of Hunan Province, Synergetic Innovation Center for Quantum Effects and Application, Hunan Normal University, Changsha 410081, People’s Republic of China 3 Department of Basic Course, Hunan Police Academy, Changsha 410138, People’s Republic of China * Corresponding Author. E-mail: [email protected] (F. Z.), [email protected] (W. Z.) Fig. S1 (a) Synthesis schematic diagram of CsPbBrxI3-x microsheets. (b) Optical image of as-synthesized CsPbBrxI3-x microsheets. (c-d) SEM of single CsPbBrxI3-x microsheet with different magnification. (a) 1 min 2 min 3 min 5 min 7 min 10 min Experiment date of Br-rich peak Lorentz peak 1 contribution Lorentz peak 2 contribution ) . u Lorentz function fit . a ( y t i s n e t n I Photon Energy (eV) (b) 1 min 2 min 3 min 5 min 7 min 10 min Experiment date of I-rich peak Gaussian peak 1 contribution Gaussian peak 2 contribution ) . u . Gaussian function fit a ( y t i s n e t n I Ph oton Energy (eV) Fig. -

Application of Aldrichina Grahami (Diptera, Calliphoridae) for Forensic Investigation in Central-South China
Rom J Leg Med [19] 55-58 [2011] DOI: 10.4323/rjlm.2011.55 © 2011 Romanian Society of Legal Medicine Application of Aldrichina grahami (Diptera, Calliphoridae) for forensic investigation in central-south China Guo Yadong1, Cai Jifeng1*, Tang Zhenchu2, Feng Xiong1, Lin Zhang1, Yong Fu3, Li Jianbo3, Chen Yaoqing4, Meng Fanming1, Wen Jifang1 _________________________________________________________________________________________ Abstract: Insect larvae and adult insects found on human corpses provide important clues for the estimation of the postmortem interval (PMI). We conducted postmortem interval (PMI) experiments in Changsha County by disposing animal carcasses for 3 consecutive years (2007 to 2009). In February 2010, a male corpse was found at wilderness of Changsha County. The larvae found on the corpse were identified only to be Aldrichina grahami (Aldrich, 1930) by morphologic observation and were then confirmed by mitochondrial DNA sequence. A PMI of 320±10 hours was concluded for the human body, based on the experimentally obtained entomological evidence. According to the murderer’s statement, the elapsed time since death was calculated to have been 308 hours. In this case, the PMI was estimated successfully and it was almost precise. The presence of the only species is related to the climatic and micro-environmental conditions in the urban habitat of Changsha, central-south China. It would appear that the knowledge of local fauna is very useful in forensic investigations. Key Words: Forensic science, Forensic entomology, Species identification, Aldrichina grahami, Postmortem interval arcosaphagous flies thatfi rst colonize a human corpse usually belong to the families Calliphoridae S[1, 2], and often play an essential role in the accurate estimation of postmortem interval (PMI) [3-5], especially when information on the postmortem phenomena is not available [2]. -

Original File Was Jvis Final.Tex
KSII TRANSACTIONS ON INTERNET AND INFORMATION SYSTEMS VOL. 11, NO. 3, Mar. 2017 1510 Copyright ⓒ2017 KSII PPNC: Privacy Preserving Scheme for Random Linear Network Coding in Smart Grid Shiming He1,2, Weini Zeng3, Kun Xie4, Hongming Yang1, Mingyong Lai1 and Xin Su2 1 School of Computer and Communication Engineering, Hunan Provincial Key Laboratory of Intelligent Processing of Big Data on Transportation, Hunan Provincial Engineering Research Center of Electric Transportation and Smart Distribution Network, Changsha University of Science and Technology, Changsha, 410114 - China [e-mail: [email protected], [email protected], [email protected]] 2 Hunan Provincial Key Laboratory of Network Investigational Technology, Hunan Police Academy, Changsha, 410138 – China [e-mail: [email protected]] 3 The 716th Research Institute, China Shipbuilding Industry Corporation, Lianyungang, 222061 – China [e-mail: [email protected]] 4 Department of Electrical and Computer Engineering, State University of New York at Stony Brook, New York, 30301 – USA [e-mail:[email protected]] *Corresponding author: Shiming He Received September 19, 2016; revised December 2, 2016; revised January 9, 2017; accepted January 29, 2017; published March 31, 2017 Abstract In smart grid, privacy implications to individuals and their families are an important issue because of the fine-grained usage data collection. Wireless communications are utilized by many utility companies to obtain information. Network coding is exploited in smart grids, to enhance network performance in terms of throughput, delay, robustness, and energy consumption. However, random linear network coding introduces a new challenge for privacy preserving due to the encoding of data and updating of coefficients in forwarder nodes. -

University of Leeds Chinese Accepted Institution List 2021
University of Leeds Chinese accepted Institution List 2021 This list applies to courses in: All Engineering and Computing courses School of Mathematics School of Education School of Politics and International Studies School of Sociology and Social Policy GPA Requirements 2:1 = 75-85% 2:2 = 70-80% Please visit https://courses.leeds.ac.uk to find out which courses require a 2:1 and a 2:2. Please note: This document is to be used as a guide only. Final decisions will be made by the University of Leeds admissions teams. -
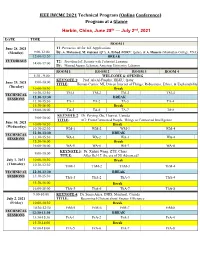
Technical Program for IWCMC 2020
IEEE IWCMC 2021 Technical Program (Online Conference) Program at a Glance Harbin, China, June 28th — July 2nd, 2021 DATE TIME ROOM 1 June 28, 2021 T1: Pervasive AI for IoT Applications (Monday) 9:00-12:00 By: A. Mohamed, M. Guizani (QU), A. Erbad (HBKU, Qatar), & A. Hussein (Manhattan College, USA) 12:00-13:30 BREAK TUTORIALS T2: Providing IoT Security with Federated Learning 14:00-17:00 By: Mourad Azzam, Lebanese American University, Lebanon ROOM 1 ROOM 2 ROOM 3 ROOM 4 8:30 - 9:00 WELCOME & OPENING KEYNOTE 1: Prof. Ala Al-Fuqaha, HBKU, Qatar 9:00-10:00 June 29, 2021 TITLE: Human-Centric ML Driven Internet of Things: Robustness, Ethics, & Explainability (Tuesday) 10:00-10:30 Break 10:30-12:30 TM-1 TM-2 TM-3 TM-4 TECHNICAL 12:30-13:30 BREAK SESSIONS 13:30-15:30 TA-1 TA-2 TA-3 TA-4 15:30-16:00 Break 16:00-18:00 TA-5 TA-6 TA-7 TA-8 KEYNOTE 2: Dr. Peiying Zhu, Huawei, Canada 9:00-10:00 TITLE: 6G: From Connected People, Things to Connected Intelligence June 30, 2021 10:00-10:30 Break (Wednesday) 10:30-12:30 WM-1 WM-2 WM-3 WM-4 12:30-13:30 BREAK TECHNICAL 13:30-15:30 WA-1 WA-2 WA-3 WA-4 SESSIONS 15:30-16:00 Break 16:00-18:00 WA-5 WA-6 WA-7 WA-8 KEYNOTE 3: Dr. Xinhui Wang, ZTE, China 9:00-10:00 TITLE: After Rel-17, the era of 5G Advanced? July 1, 2021 10:00-10:30 Break (Thursday) 10:30-12:30 ThM-1 ThM-2 ThM-3 ThM-4 TECHNICAL 12:30-13:30 BREAK SESSIONS 13:30-15:30 ThA-1 ThA-2 ThA-3 ThA-4 15:30-16:00 Break 16:00-18:00 ThA-5 ThA-6 ThA-7 ThA-8 9:00-10:00 KEYNOTE 4: Dr. -

Specific Application of the Principle of Criminal Action Preceding Civil Action in Juridical Practice and Its Reasonableness
[Type text] ISSN : [Type0974 -text] 7435 Volume 10[Type Issue text] 14 2014 BioTechnology An Indian Journal FULL PAPER BTAIJ, 10(14), 2014 [8152-8158] Specific application of the principle of criminal action preceding civil action in juridical practice and its reasonableness Zhenhua Zhu Hunan Police Academy, Changsha, Hunan, 410138, (CHINA) ABSTRACT The principle of criminal action proceeding civil action can effectively save the litigation resources and is significant to improve the litigation efficiency. With the application of the principle of criminal action preceding civil action as the research basis, by starting from the principle of criminal action preceding civil action, the reasonableness and applicability of this principle are introduced. KEYWORDS Principle of criminal action preceding; Juridical practice; Reasonableness. © Trade Science Inc. BTAIJ, 10(14) 2014 Zhenhua Zhu 8153 INTRODUCTION The so-called criminal action proceeding civil action is no more than a legal concept, which is a juridical principle that is always complied with in the judgment practice. The principle of criminal action proceeding civil action means that during the treatment of civil action, when discovering the behavior involved in criminal offence, first, the investigation organ should clearly investigate the criminal facts, the court judges the criminal offence, and then the court within the jurisdiction judges the civil liabilities or makes the court judge the criminal offence with civil cases attached. The principle of criminal action proceeding civil action is a method to deal with the cases with criminal and civil actions crossing, so as to play an important role to improve the litigation efficiency and save cost. Due to different factors, this principle still has some difficulties in the actual movement process, and more seriously, it will hinder the reasonable channel of civil juridical relief, without protecting the rights and interests of the victims maximally. -

High-Fidelity Hyperentangled Cluster States of Two-Photon Systems and Their Applications
S S symmetry Article High-Fidelity Hyperentangled Cluster States of Two-Photon Systems and Their Applications Liu Tan 1, Fang Zhou 1,2,3,* , Lingxia Zhang 1, Shaohua Xiang 1 and Kehui Song 1 and Yujing Zhao 1,* 1 College of Mechanical Engineering and Photoelectric Physics, Hunan Engineering Laboratory for Preparation Technology of Polyvinyl Alcohol Fiber Material, Huaihua University, Huaihua 418008, China 2 Department of Basic Course, Hunan Police Academy, Changsha 410138, China 3 Synergetic Innovation Center for Quantum Effects and Application, Key Laboratory of Low-dimensional Quantum Structures and Quantum Control of Ministry of Education, School of Physics and Electronics, Hunan Normal University, Changsha 410081, China * Correspondence: [email protected] (F.Z.); [email protected] (Y.Z.) Received: 12 August 2019; Accepted: 26 August 2019; Published: 28 August 2019 Abstract: An efficient scheme is proposed in this study to prepare four symmetric hyperentangled cluster states in the polarization degrees of freedom (DOF) and spatial DOF with a two-photon system. This system consists of two nitrogen-vacancy (NV) centers which are coupled to two microtoroidal resonators. The two-photon polarization-spatial hyperentangled cluster states can be generated with our system by virtue of the input and output process. Compared with previous works, our quantum circuit for preparing the hyperentangled cluster states is simple and economic. Moreover, our scheme works deterministically and does not need any extra qubits, making it applicable to existing technologies. Our calculations show that our scheme has high fidelity with current technology, which can help hyperentangled cluster states to play a very useful role in quantum communication networks with long distances and high capacity. -

Construction of the Mode of Training Innovation and Entrepreneur
2019 9th International Conference on Education and Social Science (ICESS 2019) Construction of the Mode of Training Innovation and Entrepreneur Talents Based on School-enterprise Cooperation Network Engineering Qing Lu 1,a, Jun Lu 2 and Xin Chen 3 1.Hunan Police Academy Changsha, Hunan, China 2. China Academy of Launch Vehicle Technology, beijing, China 3.Yueyang Housing Fund Management Cent , Hunan, China [email protected] Keywords: Network engineering major; Innovation and entrepreneurship education; School-enterprise cooperation Abstract. In recent years, due to the saturation of the low-end network talent market, the general phenomenon of "difficult employment of network engineering students and employers not to be recruited by employers" has emerged in the employment market of undergraduate students, which leads to the shrinking or stopping of the network engineering major in some applied universities. In view of the characteristics of the colleges and the needs of the social and economic development for innovative and entrepreneurial talents, this paper analyzes and studies the shortcomings of the current innovation and entrepreneurship education, and puts forward the basic frame of the innovative and entrepreneurial education mode of the network engineering professionals from the aspects of education policy, the Department of innovation and entrepreneurship, the social intermediary, the service platform and the students' work. Set forth the functions and cooperation of all parties in this model, and provide guidance for the construction of the educational theory system and the educational management mechanism focusing on the cultivation of innovative spirit and entrepreneurial practice ability. Introduction In recent years, the network engineering major, as a professional with the characteristics of practical skills training, adheres to the road of innovation and entrepreneurship education, and increases students' practical training opportunities. -

11 April 2019 File Ref: T3/30/344 Mr Kai Chen Sent by Email: Request-560909- [email protected] Dear Mr Chen Freedom O
11 April 2019 RECORDS MANAGEMENT SECTION The University of Edinburgh File ref: T3/30/344 Old College South Bridge Mr Kai Chen Edinburgh EH8 9YL Direct Dial 0131 651 4099 Sent by email: request-560909- Switchboard 0131 650 1000 [email protected] Email [email protected] Dear Mr Chen Freedom of information request Thank you for your email of 14 March 2019 requesting information about postgraduate taught admissions from 2016/17 to 2018/19. The University of Edinburgh is a global university, rooted in Scotland. We are globally recognised for our research, development and innovation and we have provided world- class teaching to our students for more than 425 years. We are the largest university in Scotland and in 2017/18 our annual revenue was £984 million, of which over £279 million was research income. We have over 41,000 students and over 10,200 full-time equivalent staff. We are a founding member of the UK’s Russell Group of leading research universities and a member of the League of European Research Universities. In 2018/19 the University has 15,854 taught and research postgraduate students studying full-time and part-time. We are committed to providing a wealth of resources and opportunities to enable our postgraduates to benefit from our inspiring research culture. Our academics are leaders in their fields and the University is also committed to delivering high-quality, innovative teaching. The latest report from the Quality Assurance Agency awarded us the highest rating possible for the quality of the student learning experience. More information on our postgraduate degree programmes is available on our website. -

2021 ICM Contest
2021 Interdisciplinary Contest in Modeling® Press Release—April 23, 2021 COMAP is pleased to announce the results of the 23nd annual influence between artists, and to identify revolutionaries. The E Interdisciplinary Contest in Modeling (ICM). This year 16,059 teams Problem asked teams to create a more equitable and sustainable food representing institutions from sixteen countries/regions participated in system. Students were also required to consider the timeline of the contest. Nineteen teams were designated as OUTSTANDING implementation and the obstacles to change for a region. The F representing the following schools: Problem considered the future of higher education by asking students to create a model to measure the health and sustainability of a national Beijing Normal University, China system of higher education. This problem required actionable policies Northwestern Polytechnical University, China to move a country to a healthier and more sustainable system based on Fudan University, China (AMS Award) the components they chose to include in their model and the country Shenzhen University, China (AMS Award) being considered. For all three problems, teams used pertinent data and South China University of Technology, China grappled with how phenomena internal and external to the system Shanghai Jiao Tong University, China (2) needed to be considered and measured. The student teams produced (INFORMS Award 2103649, INFORMS Award 2106028) creative and relevant solutions to these complex questions and built China University of Petroleum (East China), China models to handle the tasks assigned in the problems. The problems (Vilfredo Pareto Award) also required data analysis, creative modeling, and scientific Xidian University, China methodology, along with effective writing and visualization to Renmin University, China (SIAM Award) communicate their teams' results in a 25-page report.