Tiago Manuel Ribeiro Gomes a Sensor Node Soc Architecture For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Cisco Telepresence TC Software Licensing Information (TC4.1)
Cisco TelePresence TC Software License information guide TC Software FEBRUARY 2011 Legal information and third party copyright and licenses For Cisco TelePresence products using TC software D14767.02 License Information for products using TC Software, TC4 February 2011. 1 © 2010-2011 Cisco Systems, Inc. All rights reserved. www.cisco.com Cisco TelePresence TC Software License information guide ipcalc-1.3, ipcalc-license ...................................................................................... 16 TA - ToC - Hidden Table of Contents iproute-2.6.26, GPLv2 .......................................................................................16 What’stext anchor in iptables-1.4.28, GPLv2......................................................................................16 About this guide ..............................................................................................................4 iputils-s20071127, iputils-bsd-license .................................................... 16 The products covered by this guide: .....................................................4 jpeg lib, jpeg-license ................................................................................................ 17 this guide? User documentation .............................................................................................4 Kmod-*, GPLv2 ........................................................................................................19 Software download ................................................................................................4 -

2018 Enabling Technology Leadership Award
2018 Global In-Vehicle Infotainment Enabling Technology Leadership Award 2018 BEST PRACTICES RESEARCH Contents Background and Company Performance ........................................................................ 3 Industry Challenges .............................................................................................. 3 Technology Leverage and Customer Impact ............................................................. 4 Significance of Enabling Technology Leadership ............................................................. 8 Understanding Enabling Technology Leadership ............................................................. 8 Key Benchmarking Criteria .................................................................................... 9 Best Practices Award Analysis for Automotive Grade Linux .............................................. 9 Decision Support Scorecard ................................................................................... 9 Technology Leverage .......................................................................................... 10 Customer Impact ............................................................................................... 10 Decision Support Matrix ...................................................................................... 11 Best Practices Recognition: 10 Steps to Researching, Identifying, and Recognizing Best Practices ................................................................................................................. 12 The Intersection -

AMNESIA 33: How TCP/IP Stacks Breed Critical Vulnerabilities in Iot
AMNESIA:33 | RESEARCH REPORT How TCP/IP Stacks Breed Critical Vulnerabilities in IoT, OT and IT Devices Published by Forescout Research Labs Written by Daniel dos Santos, Stanislav Dashevskyi, Jos Wetzels and Amine Amri RESEARCH REPORT | AMNESIA:33 Contents 1. Executive summary 4 2. About Project Memoria 5 3. AMNESIA:33 – a security analysis of open source TCP/IP stacks 7 3.1. Why focus on open source TCP/IP stacks? 7 3.2. Which open source stacks, exactly? 7 3.3. 33 new findings 9 4. A comparison with similar studies 14 4.1. Which components are typically flawed? 16 4.2. What are the most common vulnerability types? 17 4.3. Common anti-patterns 22 4.4. What about exploitability? 29 4.5. What is the actual danger? 32 5. Estimating the reach of AMNESIA:33 34 5.1. Where you can see AMNESIA:33 – the modern supply chain 34 5.2. The challenge – identifying and patching affected devices 36 5.3. Facing the challenge – estimating numbers 37 5.3.1. How many vendors 39 5.3.2. What device types 39 5.3.3. How many device units 40 6. An attack scenario 41 6.1. Other possible attack scenarios 44 7. Effective IoT risk mitigation 45 8. Conclusion 46 FORESCOUT RESEARCH LABS RESEARCH REPORT | AMNESIA:33 A note on vulnerability disclosure We would like to thank the CERT Coordination Center, the ICS-CERT, the German Federal Office for Information Security (BSI) and the JPCERT Coordination Center for their help in coordinating the disclosure of the AMNESIA:33 vulnerabilities. -

RT-ROS: a Real-Time ROS Architecture on Multi-Core Processors
Future Generation Computer Systems 56 (2016) 171–178 Contents lists available at ScienceDirect Future Generation Computer Systems journal homepage: www.elsevier.com/locate/fgcs RT-ROS: A real-time ROS architecture on multi-core processors Hongxing Wei a,1, Zhenzhou Shao b, Zhen Huang a, Renhai Chen d, Yong Guan b, Jindong Tan c,1, Zili Shao d,∗,1 a School of Mechanical Engineering and Automation, Beihang University, Beijing, 100191, PR China b College of Information Engineering, Capital Normal University, Beijing, 100048, PR China c Department of Mechanical, Aerospace, and Biomedical Engineering, The University of Tennessee, Knoxville, TN, 37996-2110, USA d Department of Computing, The Hong Kong Polytechnic University, Hong Kong, China article info a b s t r a c t Article history: ROS, an open-source robot operating system, is widely used and rapidly developed in the robotics Received 6 February 2015 community. However, running on Linux, ROS does not provide real-time guarantees, while real-time tasks Received in revised form are required in many robot applications such as robot motion control. This paper for the first time presents 20 April 2015 a real-time ROS architecture called RT-RTOS on multi-core processors. RT-ROS provides an integrated Accepted 12 May 2015 real-time/non-real-time task execution environment so real-time and non-real-time ROS nodes can be Available online 9 June 2015 separately run on a real-time OS and Linux, respectively, with different processor cores. In such a way, real-time tasks can be supported by real-time ROS nodes on a real-time OS, while non-real-time ROS nodes Keywords: Real-time operating systems on Linux can provide other functions of ROS. -

Performance Study of Real-Time Operating Systems for Internet Of
IET Software Research Article ISSN 1751-8806 Performance study of real-time operating Received on 11th April 2017 Revised 13th December 2017 systems for internet of things devices Accepted on 13th January 2018 E-First on 16th February 2018 doi: 10.1049/iet-sen.2017.0048 www.ietdl.org Rafael Raymundo Belleza1 , Edison Pignaton de Freitas1 1Institute of Informatics, Federal University of Rio Grande do Sul, Av. Bento Gonçalves, 9500, CP 15064, Porto Alegre CEP: 91501-970, Brazil E-mail: [email protected] Abstract: The development of constrained devices for the internet of things (IoT) presents lots of challenges to software developers who build applications on top of these devices. Many applications in this domain have severe non-functional requirements related to timing properties, which are important concerns that have to be handled. By using real-time operating systems (RTOSs), developers have greater productivity, as they provide native support for real-time properties handling. Some of the key points in the software development for IoT in these constrained devices, like task synchronisation and network communications, are already solved by this provided real-time support. However, different RTOSs offer different degrees of support to the different demanded real-time properties. Observing this aspect, this study presents a set of benchmark tests on the selected open source and proprietary RTOSs focused on the IoT. The benchmark results show that there is no clear winner, as each RTOS performs well at least on some criteria, but general conclusions can be drawn on the suitability of each of them according to their performance evaluation in the obtained results. -

Android Before Ios in The
Vol. 27, No. 1 u hansenreport.com u February 2014 Microsoft Windows Android before iOS in the Car As technology giants Google and Apple baked” and Apple’s approach to the indus- Not Part of Sync 3 focus on extending their reach into the car, try as arrogant. In contrast Google is said Google has made far more progress than its to be more accommodating, indicating it is rival. Both companies have efforts under- willing to adapt Android to make it more Ford Goes with Panasonic and QNX way to make devices based on their respec- useful to carmakers. The software devel- Sync 3, Ford’s third-generation Sync tive operating systems more compatible oped by the OAA is expected to debut in a infotainment system, will be based on with vehicle head units. Google has gone a production vehicle as early as the end of QNX from Blackberry, not Windows Em- step further by showing a willingness to 2014. Nobody is saying if and when iOS in bedded Automotive from Microsoft as adapt its Android operating system to run the Car will find production. with Sync 1 and Sync 2. According to Ford, the vehicle’s head unit, potentially replac- the QNX operating system makes more ing QNX, Linux or Windows. Open Automotive Alliance efficient use of memory and computing At the January 2014 Consumer Elec- Drivers would love to be able to safely power. When an infotainment design goes tronics Show, Google, along with Audi, and easily use smartphones in their cars, to production, carmakers like to have no GM, Honda, Hyundai and Nvidia, and carmakers are keen to offer cars that more than 60% utilization of microproces- announced the founding of the Open let them do that. -

A Tutorial on Performance Evaluation and Validation Methodology for Low-Power and Lossy Networks
A Tutorial on Performance Evaluation and Validation Methodology for Low-Power and Lossy Networks Kosmas Kritsis, Georgios Papadopoulos, Antoine Gallais, Periklis Chatzimisios, Fabrice Theoleyre To cite this version: Kosmas Kritsis, Georgios Papadopoulos, Antoine Gallais, Periklis Chatzimisios, Fabrice Theoleyre. A Tutorial on Performance Evaluation and Validation Methodology for Low-Power and Lossy Networks. Communications Surveys and Tutorials, IEEE Communications Society, Institute of Electrical and Electronics Engineers, 2018, 20 (3), pp.1799 - 1825. 10.1109/COMST.2018.2820810. hal-01886690 HAL Id: hal-01886690 https://hal.archives-ouvertes.fr/hal-01886690 Submitted on 23 Apr 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. 1 A Tutorial on Performance Evaluation and Validation Methodology for Low-Power and Lossy Networks Kosmas Kritsis, Georgios Z. Papadopoulos, Member, IEEE, Antoine Gallais, Periklis Chatzimisios, Senior Member, IEEE, and Fabrice Theoleyre,´ Senior Member, IEEE, Abstract—Envisioned communication densities in Internet of may be used for counting the number of vehicles, such to Things (IoT) applications are increasing continuously. Because control optimally the street traffic lights and to reduce the these wireless devices are often battery powered, we need waiting time [3]. specific energy efficient (low-power) solutions. -
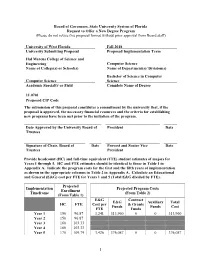
Attachment A
Board of Governors, State University System of Florida Request to Offer a New Degree Program (Please do not revise this proposal format without prior approval from Board staff) University of West Florida Fall 2018 University Submitting Proposal Proposed Implementation Term Hal Marcus College of Science and Engineering Computer Science Name of College(s) or School(s) Name of Department(s)/ Division(s) Bachelor of Science in Computer Computer Science Science Academic Specialty or Field Complete Name of Degree 11.0701 Proposed CIP Code The submission of this proposal constitutes a commitment by the university that, if the proposal is approved, the necessary financial resources and the criteria for establishing new programs have been met prior to the initiation of the program. Date Approved by the University Board of President Date Trustees Signature of Chair, Board of Date Provost and Senior Vice Date Trustees President Provide headcount (HC) and full-time equivalent (FTE) student estimates of majors for Years 1 through 5. HC and FTE estimates should be identical to those in Table 1 in Appendix A. Indicate the program costs for the first and the fifth years of implementation as shown in the appropriate columns in Table 2 in Appendix A. Calculate an Educational and General (E&G) cost per FTE for Years 1 and 5 (Total E&G divided by FTE). Projected Implementation Projected Program Costs Enrollment Timeframe (From Table 2) (From Table 1) E&G Contract E&G Auxiliary Total HC FTE Cost per & Grants Funds Funds Cost FTE Funds Year 1 150 96.87 3,241 313,960 0 0 313,960 Year 2 150 96.87 Year 3 160 103.33 Year 4 160 103.33 Year 5 170 109.79 3,426 376,087 0 0 376,087 1 Note: This outline and the questions pertaining to each section must be reproduced within the body of the proposal to ensure that all sections have been satisfactorily addressed. -

OPERATING SYSTEMS.Ai
Introduction Aeroflex Gaisler provides LEON and ERC32 users with a wide range of popular embedded operating systems. Ranging from very small footprint task handlers to full featured Real-Time Operating System (RTOS). A summary of available operating systems and their characteristics is outlined below. VxWorks The VxWorks SPARC port supports LEON3/4 and LEON2. Drivers for standard on-chip peripherals are included. The port supports both non-MMU and MMU systems allowing users to program fast and secure applications. Along with the graphical Eclipse based workbench comes the extensive VxWorks documentation. • MMU and non-MMU system support • SMP support (in 6.7 and later) • Networking support (Ethernet 10/100/1000) • UART, Timer, and interrupt controller support • PCI, SpaceWire, CAN, MIL-STD-1553B, I2C and USB host controller support • Eclipse based Workbench • Commercial license ThreadX The ThreadX SPARC port supports LEON3/4 and its standard on-chip peripherals. ThreadX is an easy to learn and understand advanced pico-kernel real-time operating system designed specifically for deeply embedded applications. ThreadX has a rich set of system services for memory allocation and threading. • Non-MMU system support • Bundled with newlib C library • Support for NetX, and USBX ® • Very small footprint • Commercial license Nucleus Nucleus is a real time operating system which offers a rich set of features in a scalable and configurable manner. • UART, Timer, Interrupt controller, Ethernet (10/100/1000) • TCP offloading and zero copy TCP/IP stack (using GRETH GBIT MAC) • USB 2.0 host controller and function controller driver • Small footprint • Commercial license LynxOS LynxOS is an advanced RTOS suitable for high reliability environments. -

Author Guidelines for 8
Proceedings of the 52nd Hawaii International Conference on System Sciences | 2019 A New Approach to the Evolution of Collaboration Platforms: The Case of South Korea’s Convergence Alliances Heeyoung Jang Minsun Kim Sungmin Cho Korea Institute of Industrial Technology Korea Institute of Industrial Technology Korea Institute of Industrial Technology [email protected] [email protected] [email protected] Jongho Lee Hongbum Kim* Korea Institute of Industrial Technology Korea Institute of Industrial Technology [email protected] [email protected] * Corresponding author Abstract since 2000, there have been no new industries that can generate economy leverage in Korea. While organizations and alliances for collaboration Many studies have demonstrated that among the have been promoted by governments for many years, various factors affecting Korea’s rapid economic their performance has not been very meaningful in growth in the twentieth century, government-led terms of activation or outcome, particularly in South industrial policies were the main cause of the economic Korea. Thus, as a tool for creating new industries and development (e.g., [1]). However, in the current growth engines, a new form of collaboration complex economic environment, arguments for platform—convergence alliances—is being promoted maintaining government-led industrial policies are now in South Korea. In order to explore the distinct not appropriate and this is why a new type of economic characteristics and advantages of convergence growth paradigm is necessary. alliances, this research compares this new type of The government, media, scholars, and practitioners platform with existing collaboration platforms. By now emphasize that new strategies for economic using a case analysis framework with in-depth growth must be developed that will help Korea adapt to interviews, this research suggests several implications the era of the Fourth Industrial Revolution. -

A Comparative Study Between Operating Systems (Os) for the Internet of Things (Iot)
VOLUME 5 NO 4, 2017 A Comparative Study Between Operating Systems (Os) for the Internet of Things (IoT) Aberbach Hicham, Adil Jeghal, Abdelouahed Sabrim, Hamid Tairi LIIAN, Department of Mathematic & Computer Sciences, Sciences School, Sidi Mohammed Ben Abdellah University, [email protected], [email protected], [email protected], [email protected] ABSTRACT Abstract : We describe The Internet of Things (IoT) as a network of physical objects or "things" embedded with electronics, software, sensors, and network connectivity, which enables these objects to collect and exchange data in real time with the outside world. It therefore assumes an operating system (OS) which is considered as an unavoidable point for good communication between all devices “objects”. For this purpose, this paper presents a comparative study between the popular known operating systems for internet of things . In a first step we will define in detail the advantages and disadvantages of each one , then another part of Interpretation is developed, in order to analyze the specific requirements that an OS should satisfy to be used and determine the most appropriate .This work will solve the problem of choice of operating system suitable for the Internet of things in order to incorporate it within our research team. Keywords: Internet of things , network, physical object ,sensors,operating system. 1 Introduction The Internet of Things (IoT) is the vision of interconnecting objects, users and entities “objects”. Much, if not most, of the billions of intelligent devices on the Internet will be embedded systems equipped with an Operating Systems (OS) which is a system programs that manage computer resources whether tangible resources (like memory, storage, network, input/output etc.) or intangible resources (like running other computer programs as processes, providing logical ports for different network connections etc.), So it is the most important program that runs on a computer[1]. -

TCP/IP Enabled Legos
TCP/IP enabled legOS Student research project University of applied sciences Hamburg March 3, 2002 Olaf Christ [email protected] 1 Abstract In recent years, the interest for connecting small devices such as sensors or embedded systems into an existing network infrastructure (such as the global Internet) has steadily increased. Such devices often have very limited CPU and memory resources and may not be able to run an instance of the TCP/IP protocol suite. This document describes how to use the uIP TCP/IP stack, written by Adam Dunkels, on LEGO’s RCX Mindstorm platform, a very small device / toy powered by a h8300 Hitachi microcontroller with very limited RAM (32K) and processing power. Still, it is powerful enough to run alternative operating systems such as LegOS or even a tiny Java VM as a replacement of the original firmware. The advanced user is usually not satisfied with the original firmware due to its extremely limited capabilities in terms of executing complex code and the very limited number of variables. The uIP TCP/IP stack is intended for embedded systems running on low-end 8 or 16-bit microcontrollers. The code size of uIP is an order of a magnitude smaller than similar generic TCP/IP stacks available today. The uIP code and an up-to-date version of the uIP documentation can be downloaded from the uIP homepage maintained by Adam Dunkels. 2 3 Preface This work has been carried out as a student research project at the University of applied sciences Hamburg in Hamburg, Germany. The proposal was given to me by my supervisor Prof.