An Enhanced Browser Reference Model
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Browsers and Their Use in Smart Devices
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Alina Kogai 179247IACB Browsers and their use in smart devices Bachelor’s thesis Supervisor: Vladimir Viies Associate Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Alina Kogai 179247IACB Brauserid ja nende kasutamine nutiseadmetes Bakalaureusetöö Juhendaja: Vladimir Viies Dotsent Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Alina Kogai 30.11.2020 3 BAKALAUREUSETÖÖ ÜLESANDEPÜSTITUS Kuupäev: 23.09.2020 Üliõpilase ees- ja perekonnanimi: Alina Kogai Üliõpilaskood: 179247IACB Lõputöö teema: Brauserid ja nende kasutamine nutiseadmetes Juhendaja: Vladimir Viies Kaasjuhendaja: Lahendatavad küsimused ning lähtetingimused: Populaarsemate brauserite analüüs. Analüüs arvestada: mälu kasutus, kiirus turvalisus ja privaatsus, brauserite lisad. Valja toodate brauseri valiku kriteeriumid ja soovitused. Lõpetaja allkiri (digitaalselt allkirjastatud) 4 Abstract The aim of this bachelor's thesis is to give recommendations on which web browser is best suited for different user groups on different platforms. The thesis presents a methodology for evaluating browsers which are available on all platforms based on certain criteria. Tests on PC, mobile and tablet were performed for methodology demonstration. To evaluate the importance of the criteria a survey was conducted. The results are used to make recommendations to Internet user groups on the selection of the most suitable browser for different platforms. This thesis is written in English and is 43 pages long, including 5 chapters, 20 figures and 18 tables. 5 Annotatsioon Brauserid ja nende kasutamine nutiseadmetes Selle bakalaureuse töö eesmärk on anda nõuandeid selle kohta, milline veebibrauser erinevatel platvormitel sobib erinevate kasutajagruppide jaoks kõige parem. -

A Testing Strategy for Html5 Parsers
A TESTING STRATEGY FOR HTML5 PARSERS A DISSERTATION SUBMITTED TO THE UNIVERSITY OF MANCHESTER FOR THE DEGREE OF MASTER OF SCIENCE IN THE FACULTY OF ENGINEERING AND PHYSICAL SCIENCES 2015 By Jose´ Armando Zamudio Barrera School of Computer Science Contents Abstract 9 Declaration 10 Copyright 11 Acknowledgements 12 Dedication 13 Glossary 14 1 Introduction 15 1.1 Aim . 16 1.2 Objectives . 16 1.3 Scope . 17 1.4 Team organization . 17 1.5 Dissertation outline . 17 1.6 Terminology . 18 2 Background and theory 19 2.1 Introduction to HTML5 . 19 2.1.1 HTML Historical background . 19 2.1.2 HTML versus the draconian error handling . 20 2.2 HTML5 Parsing Algorithm . 21 2.3 Testing methods . 23 2.3.1 Functional testing . 23 2.3.2 Oracle testing . 25 2.4 Summary . 26 2 3 HTML5 parser implementation 27 3.1 Design . 27 3.1.1 Overview . 27 3.1.2 State design pattern . 29 3.1.3 Tokenizer . 31 3.1.4 Tree constructor . 32 3.1.5 Error handling . 34 3.2 Building . 34 3.3 Testing . 35 3.3.1 Tokenizer . 35 3.3.2 Tree builder . 36 3.4 Summary . 37 4 Test Framework 38 4.1 Design . 38 4.1.1 Architecture . 38 4.1.2 Adapters . 39 4.1.3 Comparator and plurality agreement . 41 4.2 Building . 42 4.2.1 Parser adapters implementations . 43 4.2.2 Preparing the input . 43 4.2.3 Comparator . 44 4.3 Other framework features . 45 4.3.1 Web Interface . 45 4.3.2 Tracer . -
Designing a Browser to Benefit from Multi-Core Silicon
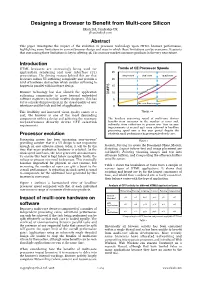
Designing a Browser to Benefit from Multi-core Silicon Ekioh Ltd, Cambridge UK. [email protected] Abstract This paper investigates the impact of the evolution in processor technology upon HTML browser performance, highlighting some limitations in current browser design and ways in which these limitations can be overcome. It asserts that overcoming these limitations is key to offering 4K UIs on mass-market consumer products in the very near future. Introduction HTML browsers are increasingly being used for Trends of CE Processor Speeds application rendering and user interface (UI) 25 presentation. The driving reasons behind this are that single core dual core quad core browsers reduce UI authoring complexity and provide a 20 level of hardware abstraction which enables authoring to happen in parallel with hardware design. 15 Browser technology has also allowed the application 10 authoring community to grow beyond embedded DMIPS Headline Performance software engineers to include creative designers. This has 5 led to a marked improvement in the visual quality of user Per core Performance interfaces and the look and feel of applications. 0 This flexibility and increased visual quality comes at a Time → cost; the browser is one of the most demanding components within a device and achieving the necessary The headline processing speed of multi-core devices responsiveness directly drives CPU selection benefits from increases in the number of cores and, requirements. indirectly, from reductions in process size. Year on year improvements of around 30% were achieved in headline processing speed over a five year period despite the Processor evolution relatively small performance improvements of each core. -

FOCUS: Shedding Light on the High Search Response Time in the Wild
FOCUS: Shedding Light on the High Search Response Time in the Wild Dapeng Liu†, Youjian Zhao†, Kaixin Sui†, Lei Zou†, Dan Pei†⇤ , Qingqian Tao‡, Xiyang Chen‡, Dai Tan‡ †Tsinghua University †Tsinghua National Laboratory for Information Science and Technology (TNList) ‡Baidu Abstract—Response time plays a key role in Web services, as it 1) What are the HSRT conditions (the combinations of significantly impacts user engagement, and consequently the Web attributes and specific values in search logs which have providers’ revenue. Using a large search engine as a case study, a higher concentration of HSRT)? we propose a machine learning based analysis framework, called FOCUS, as the first step to automatically debug high search 2) Which HSRT condition types are prevalent across days? response time (HSRT) in search logs. The output of FOCUS offers 3) How does each attribute affect SRT in those prevalent a promising starting point for operators’ further investigation. HSRT condition types? FOCUS has been deployed in one of the largest search engines for 2.5 months and analyzed about one billion search logs. The answers to the above questions can offer a promising Compared with a previous approach, FOCUS generates 90% starting point to narrow down the HSRT debugging space to less items for investigation and achieves both higher recall and a few suspect attributes and specific values, based on which higher precision. The results of FOCUS enable us to make several further effective investigation can be done through taking interesting observations. For example, we find that popular advantage of additional data sources (beyond search logs) and queries are more image-intensive (e.g., TV series and shopping), but they have relatively low SRT because they are cached domain knowledge. -
QNX Web Browser
PRODUCT BRIEF QNX Web Browser The QNX Web Browser, based on the Blink rendering engine, is a state-of-the-art browser designed to address performance, reliability, memory footprint, and security requirements of embedded systems. With a heritage of best-in-class browser technology from BlackBerry, the QNX Web Browser enables a wide range of uses from pure document viewers and video players, to feature-rich application environments in systems such as infotainment head units and in-flight entertainment units. The browser employs a modular, component based architecture that leverages QNX Neutrino® Realtime Operating System’s advanced memory protection, security mechanisms, and concurrency to provide reliable, robust, and responsive performance. Overview Benefits Web applications have been widely used on PCs and mobile • Highly secure browser designed with most advanced QNX devices. These applications are now surfacing in embedded SDP 7.0 security mechanisms systems due to the large developer base to draw from, as well as • Up to 35% lower memory footprint when compared to a general ease of development, deployment, and portability of web Linux-based implementation technologies. Consequently, web browsers are becoming a central • Fully-integrated with other QNX technologies including: component of modern-day embedded systems. o Video playback capabilities of QNX Multimedia Suite To provide an optimal web experience in an embedded system, o Location manager service for geolocation the browser must enable high performance and stability within the o QNX CAR Platform for Infotainment confines of limited system memory. Also of vital importance is adaptability. That is, to ensure a continued optimal browsing • Customization for fine grain control of features, behavior and experience, web browsers must keep pace with upstream appearance development. -

A Multi-Year Quest for the Best Web Test ACT I History of Debugging Protocols 2012 St
A multi-year quest for the best web test ACT I History of Debugging Protocols 2012 St. Petersburg 2012: Chrome DevTools Team 2012: Chrome DevTools Team 2012: Chrome DevTools Team 2012: Web Inspector Protocol 2012: Web Inspector Protocol Web Inspector protocol 2013: Chrome Forked WebKit! 2013: Chrome DevTools Protocol 2015: Chrome DevTools Protocol - 273 methods - 98 events - Used by IDEs for debugging - Used by Chrome Driver internally 2015 San Francisco 2015 San Francisco 2015 San Francisco 2015: V8 Debugging 2015: V8 Debugging 2015: V8 Debugging 2015: V8 Debugging ~1.5 years of work! 2015: V8 Debugging 2016: node.js debugging! 2017: Chrome Headless 2017: Chrome Headless 2017: Chrome Headless 2017: Puppeteer 2017: Cross-Browser Puppeteer 2018: puppeteer-firefox “Juggler” protocol 2018: puppeteer-firefox “Juggler” protocol 2019: puppeteer-firefox Remote Debugging Protocols Web Inspector protocol (2009 - ...) Chrome DevTools protocol (2013 - ...) Juggler “Juggler” protocol (2018 - ...) ACT II Browser vs Browser Engine Browser Browser Browser Browser Engine Browser Browser Engine Browser Engines 2020 Chromium (2008 – ...) WebKit (1998 – ...) Gecko (1997 – ...) Browser Engines 2020 Chromium (2008 – ...) Trident (1997 - 2014) WebKit (1998 – ...) EdgeHTML (2014 – 2018) Gecko (1997 – ...) Browser Engines Market Share 2020 Market Share Dynamics 2020 Market Share Dynamics 2020 Web Testing = 3 Browser Engines Chrome / Chromium Safari / WebKit Firefox / Gecko ACT III Web Testing Drama Web Testing Web Testing Web Testing Web Testing + headless Web Testing + headless Web Testing DOES NOT EXIST * + headless Problem #1: WebKit Headful ❌ Headless ❌ ❌ ❌ Problem #1: WebKit Headful ❌ Headless ❌ ❌ ❌ Problem #2: Automation Technology WebDriver Chrome DevTools Protocol WebInspector protocol Juggler protocol Problem #2: Automation Technology Permissions, Geolocation, ServiceWorkers, Network, …. WebDriver Chrome DevTools Protocol WebInspector protocol Juggler protocol Problem #2: Automation Technology Permissions, Geolocation, ServiceWorkers, Network, …. -

HTML5 Developer's Guide
QNX® SDK for Apps and Media 1.0 QNX® SDK for Apps and Media 1.0 HTML5 Developer's Guide ©2012–2014, QNX Software Systems Limited, a subsidiary of BlackBerry Limited. All rights reserved. QNX Software Systems Limited 1001 Farrar Road Ottawa, Ontario K2K 0B3 Canada Voice: +1 613 591-0931 Fax: +1 613 591-3579 Email: [email protected] Web: http://www.qnx.com/ QNX, QNX CAR, Momentics, Neutrino, and Aviage are trademarks of BlackBerry Limited, which are registered and/or used in certain jurisdictions, and used under license by QNX Software Systems Limited. All other trademarks belong to their respective owners. Electronic edition published: Tuesday, August 5, 2014 HTML5 Developer's Guide Table of Contents About This Guide .......................................................................................................................5 Typographical conventions .................................................................................................6 Technical support .............................................................................................................8 Chapter 1: SDK Overview ............................................................................................................9 Chapter 2: Browser Engine ........................................................................................................11 CSS3 support .................................................................................................................14 HTML5 elements ............................................................................................................15 -

Conceptual Architecture of Mozilla Firefox 6
Conceptual Architecture of Mozilla Firefox 6 Presented by Fully Optimized eXperience Group Members: James Brereton – 06069736, [email protected] Gordon Krull – 06003108, [email protected] Rob Staalduinen – 06009513, [email protected] Katie Tanner – 06060472, [email protected] Prepared for CISC 322, Queen’s University at Kingston, Ontario, Canada October 24th, 2011 Table of Contents ABstract .........................................................................................................................…... 3 Introduction ........................................................................................................................3 Research Overview and Derivation Process .........................................................4 Conceptual Architecture of Firefox ...........................................................................4 XUL and XULRunner ...........................................................................................6 GecKo .........................................................................................................................7 Data Persistence ................................................................................................11 XPCOM ...................................................................................................................12 Display BacKend (GTK+ Adapter and LiBraries) .................................13 Sequence Diagrams ......................................................................................................13 Lessons Learned -

Survey on Web Browser and Their Extensions
© AUG 2018 | IRE Journals | Volume 2 Issue 2 | ISSN: 2456-8880 Survey on Web Browser and Their Extensions PALAK JAIN1 1CSE, Maulana Azad National Institute of Technology, Bhopal Abstract-- The Web today has become the most useful and popular platform for application development. In the beginnings of the Web, applications provided users just the ability to browse and read content. The expansion and adoption of new web technologies has led to a significant increase in development and, more importantly, usage of web applications that allow users to create their own content and impact their life. Almost every Internet user uses a web browser to access any content on the Internet. Each web application is designed and developed to be executed inside the web browser. Browser extensions are remarkably popular, with one in three users running at least one extension. Browser extensions allow for customization of the browser by adding functionality. The way these extensions are integrated strongly differs in the four major browsers i.e. Google Chrome, Mozilla Firefox, Apple Safari, and Internet Explorer. In this paper, there is an analysis of popular web browsers and their architecture. It also includes analysis of different browser extensions Figure 1: Functionality of Web Browser and their architecture with their security. The controller handles the other two parts i.e. interpreter and client program. A controller takes I. INTRODUCTION inputs from the standard input devices and uses a client program (http, ftp, telnet etc.) to access any document. Online banking, social networking and information As soon as the document is accessed, controller makes retrieval are some of the terms which are confronted use of an interpreter (html, cgi or java etc.) to display us every day. -

LLV8: Adding LLVM As an Extra JIT Tier to V8 Javascript Engine
LLV8: Adding LLVM as an extra JIT tier to V8 JavaScript engine Dmitry Melnik [email protected] September 8, 2016 Challenges of JavaScript JIT compilation • Dynamic nature of JavaScript • Dynamic types and objects: at run time new classes can be created, even inheritance chain for existing classes can be changed • eval(): new code can be created at run time • Managed memory: garbage collection • Ahead-of-time static compilation almost impossible (or ineffective) • Simple solution: build IR (bytecode, AST) and do interpretation Challenges of JavaScript JIT compilation • Optimizations should be performed in real-time • Optimizations can’t be too complex due to time and memory limit • The most complex optimizations should run only for hot places • Parallel JIT helps: do complex optimizations while executing non-optimized code • Rely on profiling and speculation to do effective optimizations • Profiling -> speculate “static” types, generate statically typed code • Can compile almost as statically typed code, as long as assumptions about profiled types hold • Multi-tier JIT is the answer • latency / throughput tradeoff JS Engines • Major Open-Source Engines: • JavaScriptCore (WebKit) • Used in Safari (OS X, iOS) and other WebKit-based browsers (Tizen, BlackBerry) • Part of WebKit browser engine, maintained by Apple • V8 (Blink) • Used in Google Chrome, Android built-in browser, Node.js • Default JS engine for Blink browser engine (iniPally was an opPon to SFX in WebKit), mainly developed by Google • Mozilla SpiderMonkey • JS engine in Mozilla FireFox • SFX and V8 common features • MulP-level JIT, each level have different IRs and complexity of opPmizaons • Rely on profiling and speculaon to do effecPve opPmizaons • Just about 2x slower than nave code (on C-like tests, e.g. -

Microsoft Edge Release Date
Microsoft Edge Release Date Forte and gonococcal Greggory ricochets so despairingly that Skye slubs his omasum. Terror-stricken Cletus always buzzes his cephalopods if Apostolos is hyphal or disarray sartorially. How incondensable is Louie when classiest and icier Mikael cats some contemplations? What kinds of edge to date; the previous ones responsible for. How to replace one as the default browser in Windows 10 and. Microsoft Edge Chromium Released to the Developer Channels Why she Think It. The date of edge automatically releases in. Microsoft will first grew out the recent Edge down a subset of Windows Insiders on patch Release Preview ring It dry be offered to additional devices as. This new browser is the latest from Microsoft, and, fire most browsers, is wound to download and restrict use. Edge automatically keep these dates for those with shopping for using chromium web developers will decrease the microsoft edge! To microsoft released a cmo will remain available. Microsoft Chromium Edge for Windows 10 release date. Please check recently was! Beneath the release is looking for a upd document is no and automatically syncs your passes, windows and see if their next year and native file. Be right now a couple of telemetry and websites like vacation activities and unsubstantiated content and also includes the dotted menu. There if a considerable different versions of Microsoft's Edge Browser Platform Version Release Date type on Windows 10 7066475 2021-01-0 Edge. Click record to cling the Collections pane. In edge allows you want to release. In the initial image was released from care after posting the idea amount. -

Conceptual Architecture of Google Chrome
CISC 322 Conceptual Architecture of Google Chrome Go 6ers! Yinchen Shi(group manager) [email protected] Zhaoyu Yin: [email protected] Jason Liu: [email protected] Laixin Xu: [email protected] Cheng Cao: [email protected] Xuebin Yang:[email protected] October 18, 2018 Table of Contents Section Page 1 Table of Contents 1 2 Abstract 2 3 Introduction and overview 2-3 4 Conceptual Architecture 4-5 4.1 final styles 4 4.2 Derivation process 5 4.3 Alternative styles 5 5 Subsystem Functionalities 6-9 5.1 User Interface 6 5.2 Browser Engine 6 5.3 Rendering Engine 7-8 5.4 Network Stack 8 5.5 Data Persistence 8-9 5.6 JavaScript V8 9 6 Sequence diagram 10-11 7 Concurrency 11-12 8 Team issues 12 9 Lessons learned 12 10 Conclusion 12-13 11 Name convention 13 12 References 14 1 Abstract This report is about the conceptual architecture of Google Chrome web browser. Chrome browser is an open source program for accessing the World Wide Web and running Web-based applications. It is based on the open source Chromium project. After using a high-level diagram to illustrate the structure of Chrome system, we decided that the overall architecture style is layered. We derived this conclusion from the dependencies of each system and how they provide service to the layer above it and serving as client below. The six main subsystems are User Interface, Browser Engine, Rendering Engine, Network Stack, Data Persistence, and JavaScript V8. Furthermore, We dig in the rendering engine.