Internet of Things Digital Tools and Uses Set Coordinated by Imad Saleh
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Phd Thesis-Masimohammadi
EMPOWERING SENIORS THROUGH DOMOTIC HOMES Integrating intelligent technology in senior citizens’ homes by merging the perspectives of demand and supply EMPOWERING SENIORS THROUGH DOMOTIC HOMES Integrating intelligent technology in senior citizens’ homes by merging the perspectives of demand and supply PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Technische Universiteit Eindhoven, op gezag van de rector magnifi cus, prof.dr.ir. C.J. van Duijn, voor een commissie aangewezen door het College voor Promoties in het openbaar te verdedigen op woensdag 31 maart 2010 om 16.00 uur door Masoumeh Mohammadi geboren te Masjed Soleyman, Iran Dit proefschrift is goedgekeurd door de promotoren: prof.dr.ir. J.J.N. Lichtenberg en prof.ir. J.M. Post Copromotor: dr.ir. P.A. Erkelens * en opgedragen aan Bert ———————— * to the rock and to the sea, to my father, the proud steady rock to my mother, the affectionate deep sea Samenstelling van de promotiecommissie Prof.ir. J. Westra Technische Universiteit Eindhoven, voorzitter Prof.dr.ir. J.J.N. Lichtenberg Technische Universiteit Eindhoven, promotor Prof.ir. J.M. Post Technische Universiteit Eindhoven, 2de promotor Dr.ir. P.A. Erkelens Technische Universiteit Eindhoven, co-poromtor Prof.dr.ir. W.A. Poelman Universiteit Twente Prof.dr. D. Verté Vrije Universiteit Brussel Prof.dr.ir. P.G.M. Baltus Technische Universiteit Eindhoven Empowering Seniors through Domotics Homes Integrating intelligent technology in senior citizens’ homes by merging the perspec- tives of demand and supply M. Mohammadi Printed by The Eindhoven University Press ISBN 978-90-6814-627-1 Copyright 2010 First edition – M. Mohammadi Copyright 2011 Second edition – M. -

Final Thesis 3.29 MB
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA STAVEBNÍ FACULTY OF CIVIL ENGINEERING ÚSTAV STAVEBNÍ EKONOMIKY A ŘÍZENÍ INSTITUTE OF STRUCTURAL ECONOMICS AND MANAGEMENT ANALÝZA NÁKLADŮ INTELIGENTNÍHO DOMU COST ANALYSIS OF A SMART HOUSE BAKALÁŘSKÁ PRÁCE BACHELOR'S THESIS AUTOR PRÁCE Jan Vacek AUTHOR VEDOUCÍ PRÁCE Ing. PETR AIGEL, Ph.D. SUPERVISOR BRNO 2019 VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ FAKULTA STAVEBNÍ Studijní program B3607 Stavební inženýrství Typ studijního programu Bakalářský studijní program s prezenční formou studia Studijní obor 3607R038 Management stavebnictví Pracoviště Ústav stavební ekonomiky a řízení ZADÁNÍ BAKALÁŘSKÉ PRÁCE Student Jan Vacek Název Analýza nákladů inteligentního domu Vedoucí práce Ing. Petr Aigel, Ph.D. Datum zadání 30. 11. 2018 Datum odevzdání 24. 5. 2019 V Brně dne 30. 11. 2018 doc. Ing. Jana Korytárová, Ph.D. prof. Ing. Miroslav Bajer, CSc. Vedoucí ústavu Děkan Fakulty stavební VUT PODKLADY A LITERATURA HARGREAVES, Tom. WILSON, Charlie. Smart Homes and Their Users. Cham: Springer, 2017. 121s. ISBN 978-3-319-68017-0 MEHDI, Gulnar. MIKHAL, Roshchin. Electricity Consumption Constraints for Smart-home Automation: An Overview of Models and Applications [online]. Copyright © 2015 The Authors. Published by Elsevier Ltd. [cit. 25.11.2018]. HARGREAVES, Tom. WILSON, Charlie. Benefits and risks of smart home technologies [online]. Copyright © 2017 The Authors. Published by Elsevier Ltd. [cit. 25.11.2018]. Louis, Jean-Nicolas. CALO, Antonio. LEIVISKÄ, Kauko. PONGRÁCZ, Eva. Environmental Impacts and Benefits of Smart Home Automation: Life Cycle Assessment of Home Energy Management [online]. Copyright © 2015. Published by Elsevier Ltd. [cit. 25.11.2018]. ZÁSADY PRO VYPRACOVÁNÍ Cílem práce je posouzení nákladů inteligentního domu 1. -

State of Wyoming Ed Murray Secretary of State * Business Division
STATE OF WYOMING * SECRETARY OF STATE ED MURRAY BUSINESS DIVISION 2020 Carey Avenue, Cheyenne, WY 82002-0020 Phone 307-777-7311 · Fax 307-777-5339 Website: http://soswy.state.wy.us · Email: [email protected] Domestic Entity Charters As of July 5, 2016 Date Range Includes: 04/01/2016 through 06/30/2016 Filing ID Name Filing Date Mailing Address County General Partnership 2016-000714755 Kern River Gas Transmission Company 05/16/2016 666 Grand Ave 500 Des Moines, IA 50309 2016-000712331 Tata Chemicals (Soda Ash) Partners 04/20/2016 100 Enterprise Dr Ste 701 Rockway, NJ 07866 General Partnership Count: 2 County Count: 2 Albany County Profit Corporation 2016-000711043 Clear Skies Planning 04/07/2016 34 Bobcat Rd Laramie, WY 82072 2016-000718009 JB Homes, Inc. 06/21/2016 PO Box 597 Laramie, WY 82073 2016-000713636 Nord Engineering, Inc. 05/04/2016 170 Katie Canyon Loop Laramie, WY 82072 2016-000718162 PEGGY J. HARRIS, APRN, P.C. 06/22/2016 954 N McCue 182 Laramie, WY 82072 2016-000712443 Red Rock Data Inc. 04/21/2016 4121 Cliff St Laramie, WY 82070 2016-000712427 TIE SIDING GENERAL STORE, INC. 04/21/2016 3400 NIGHTHAWK CT PUNTA GORDA, FL 33950 Page 1 of 583 Domestic Entity Charters As of July 5, 2016 Date Range Includes: 04/01/2016 through 06/30/2016 Filing ID Name Filing Date PUNTAMailing GORDA,Address FL 33950 2016-000715329 Van Aken Performance Horses Corporation 05/20/2016 950 Hwy 287 Laramie, WY 82071 2016-000711407 Western States Management, Inc 04/11/2016 PO Box 971 Laramie, WY 82073 Profit Corporation Count: 8 Nonprofit Corporation 2016-000714833 Laramie Girls Softball Association, Inc. -

People-Centered Initiatives for Increasing Energy Savings
People-Centered Initiatives for Increasing Energy Savings Karen Ehrhardt-Martinez John A. “Skip” Laitner People-Centered Initiatives for Increasing Energy Savings Editors: Karen Ehrhardt-Martinez* John A. “Skip” Laitner† November 2010 ©American Council for an Energy-Efficient Economy 529 14th Street, Suite 600, Washington, D.C. 20045 Phone: 202-507-4000, Fax: 202-429-2248, www.aceee.org * Formerly with ACEEE. Presently with University of Colorado, Renewable and Sustainable Energy Institute † American Council for an Energy-Efficient Economy CONTENTS Foreword iii Acknowledgments iv About ACEEE v Introduction: An Opening Context for People-Centered Insights 1 John A. “Skip” Laitner and Karen Ehrhardt-Martinez Section 1: The Social and Behavior Wedge Household Actions Can Provide a Behavioral Wedge to Rapidly Reduce U.S. Carbon 9 Emissions Thomas Dietz, Gerald T. Gardner, Jonathan Gilligan, Paul C. Stern, and Michael P. Vandenbergh Examining the Scale of the Behavior Energy Efficiency Continuum 20 John A. “Skip” Laitner and Karen Ehrhardt-Martinez A 30% Reduction in Electricity Use Is Not Only Possible but Actually Occurred in Juneau, 32 Alaska Alan Meier Section 2: Behavior-Savvy Policy Adding a Behavioral Dimension to Residential Construction and Retrofit Policies 43 Marilyn A. Brown, Jess Chandler, Melissa V. Lapsa, and Moonis Ally Towards a Policy of Progressive Efficiency 60 Jeffrey Harris, Rick Diamond, Carl Blumstein, Chris Calwell, Maithili Iyer, Christopher Payne, and Hans-Paul Siderius Rebound, Technology, and People: Mitigating -

SMART HOME Digital Planet: How Digital Technology Is Changing the World
SMART HOME Digital Planet: how digital technology is changing the world SUBMITTED ON 19th OF AUGUST, 2011 Yvonne Schwenk BEUTH LANGUAGE AWARD 2011 YVONNE SCHWENK | s7739900 | Course of Studies : BIOTECHNOLOGY A short story about Janes day in a smart home Telephone “An amazing invention - but who would ever want to use one?” RUTHERFORD B. HAYES , 1877 Computers “I think there is a world market for about five computers“ THOMAS J. WATSON, 1943 Television “[...] won‘t be able to hold on to any market it captures after the first six months. People will soon get tired of staring at a plywood box every night.“ DARRYL ZANUCK, 1946 Computers “[...] in the future may weigh no more than 1.5 tons” POPUAR MACHICHES MAGAZINE, 1949 Satellites “There is no chance communications space satellites will be used to provide better telephone, telegraph, television, or radio service inside the United States.‘“ FCC ENGINEER T.A.M. CRAVEN, 1961 Telephone “Transmission of documents via telephone wires is possible in principle, but the apparatus required is so expensive that it will never become a practical proposition.” DENNIS GABOR, 1962 BEUTH LANGUAGE AWARD 2011 / YVONNE SCHWENK / PREFACE PREFACE A short story about Jane‘s day in a smart home The alarm bell rings. The roller and should be thrown out. After hello by intercom and pushes blinds open. Her bed gently Breakfast, Jane is automatically the icon to open the door. They places her in a comfortable informed by voice message plan to meet after lunch. After sitting position. The room be- that her son has tried to call her lunch, Jane leaves the house to comes illuminated. -

Zukunftskonzepte: Zukunftskonzepte
Zukunftskonzepte: Wohnkomfort dank Technik „Hauswirtschaft und Dienstleistungen“ Tagung am 4.10.2016 im WABE-Zentrum Klaus Bahlsen Prof. Dr. Jörg Andreä, HAW Hamburg Wohnkomfort dank Technik THEMEN Geschichte des Smart Home Möglichkeiten durch Vernetzung im Haus Technische Grundlagen und Lösungen Das Smart Home vor dem Durchbruch? Robotik im Haushalt Nutzen und Risiken für den Verbraucher Ausblick: Die Küche 2030 Prof. Dr. J. Andreä Folie Nr. 2 Wohnkomfort dank Technik Geschichte des Smart Homes Monsanto House of the Future (1957) Disneyland in Anaheim, Kalifornien Xanadu Houses (1980) Kissimmee, Florida; Wisconsin Dells, Wisconsin; Gatlinburg, Tennessee House of the Future (1995), Amsterdam FutureLife (2000), Hünenberg / Schweiz Fraunhofer InHaus-Zentrum (2003), Duisburg Das Mediale Haus (2006), Nürnberg Prof. Dr. J. Andreä Folie Nr. 3 Wohnkomfort dank Technik Das „Smart Home“… ist ein privat genutztes Heim (z. B. Eigenheim, Mietwohnung), in dem die zahlreichen Geräte der Hausautomation, Haushaltstechnik, Konsumelektronik und Kommunikationseinrichtungen zu intelligenten Gegenständen werden, die sich an den Bedürfnissen der Bewohner orientieren. Durch Vernetzung dieser Gegenstände untereinander können neue Assistenzfunktionen und Dienste zum Nutzen des Bewohners bereitgestellt werden und einen Mehrwert generieren, der über den einzelnen Nutzen der im Haus vorhandenen Anwendungen hinausgeht. Quelle: Kurzstudie „Smart Home in Deutschland“, Institut für Innovation und Technik (2010) Prof. Dr. J. Andreä Folie Nr. 4 Wohnkomfort -

Blight Ideas
VOLUME 9 ISSUE 8 Aug. 23 – Sept. 26, 2019 Follow us on social media Get up to date on sdnews.com exciting local events Page 17 INSIDE Adult-use THIS ISSUE cannabis B FEATURE Sculpting La Mesa draft plan released By JEFF CLEMETSON | La Mesa Courier On Aug. 15, the city of La Mesa held a public workshop to discuss its draft plan to legal- James Porter shaped bronze statues ize recreational cannabis sales. and city government. Page 9 The new adult-use plan is a final step to decriminalize marijuana that began with B FOOD & DRINK Measure U, the citizens’ ini- Brigantine turns 50 Blight ideas tiative that made medical can- nabis use legal in the city, fol- Erik Egelko brokered the sale of The Light Bulb Centre building to developers that are turning it into loft apartments. lowed by Proposition V, which (Photo courtesy Erik Egelko) set up a taxation framework for both medical- and adult-use Local broker proposes ways to clean up west La Mesa cannabis. Although the plan present- By JEFF CLEMETSON | La Mesa Courier will turn them into businesses or and brokering a deal to turn a for- ed at the workshop is similar to housing. The real estate broker mer retail building into a housing the rules set out in Measure U, West La Mesa resident Erik has found some recent success in project. there are some key differences Mt. Helix restaurant celebrates history Egelko has found a niche business this department, finding buyers Revitalizing La Mesa’s west side — and one that cannabis indus- of fine seafood dining.Page 11 in his home neighborhood —tak- for an El Cajon Boulevard proper- and replacing blighted properties try members who attended the ing run-down properties and mar- ty that had most recently housed event said would adversely af- keting them to developers who an illegal marijuana dispensary SEE BLIGHT IDEAS, Page 2 fect dispensaries that the city B ART has already approved. -

Connected Buildings
the u-blox technology magazine No. 7 May 2019 Connected buildings The Internet of Buildings → 7 Connecting the workplace - tomorrow? → 22 Experimenting with Bluetooth mesh, inside and out → 50 Foreword Dear Readers, Do you talk to your home? And more importantly, does it listen? Just a decade ago, these questions would have seemed absurd. Today, they reflect reality in millions of households around the world, as the Internet of Things expands into – and enables – a new generation of smart, connected buildings. In this seventh edition of our u-blox magazine, we ex- amine how connectivity is transforming our homes, our workplaces, and the other buildings we inhabit, as well as the business opportunities that these new technologies create. But there’s more to this transformation than increasing our comfort, convenience, safety, and productivity. Ac- cording to The Global Alliance for Buildings and Construc- tion, in partnership with UN Environment, buildings are responsible for 40 percent of our CO2 emissions and 36 percent of our total energy consumption. That’s why they need to be front and center in our efforts to reduce our environmental impact while improving the quality of life of the growing, aging, and urbanizing world population. It’s a sector that plays to our strengths at u-blox, as pro- viders of wireless communication and positioning tech- nologies – key enablers of connected building solutions. That’s why we’d like to invite you to join us in exploring this Imprint rapidly evolving world – the great digital indoors. u - The u-blox technology magazine Published by: Thomas Seiler Chief Editor: Sven Etzold Senior Editor: Natacha Seitz We wish you an informative and enjoyable read. -

La Domotica Possibile
POLITECNICO DI MILANO Facoltà di Architettura e Società LA DOMOTICA POSSIBILE Caratteristiche, esperienze e stato dell’arte dell’ultima fase evolutiva dell’abitare RELATORE: Prof. OLIVIERO TRONCONI Tesi di Laurea di : DANIELA MEROLLA Matricola : 170216 ANNO ACCADEMICO 2008-2009 «Quello che infonde coraggio ai nostri sogni è la convinzione di poterli realizzare […] Non si rivoluziona facendo rivoluzioni, si rivoluziona portando soluzioni» Le Corbusier, Urbanisme (1967) Ringraziamenti Desidero ringraziare tutti coloro che mi sono stati vicini nel percorso finale di studi e che mi hanno dato la forza e lo stimolo per raggiungere questo importante traguardo. In modo particolare desidero dedicare questo lavoro a Cinzia, per la sua costante e amorevole presenza, lo spirito, le idee e l’incoraggiamento, ingredienti che sono stati decisivi per non perdere mai di vista il mio obiettivo. Un ringraziamento sentito va al Prof. Oliviero Tronconi che, accompagnandomi nell’intero lavoro, è stato una guida paziente, disponibile e fonte di continue sagge riflessioni. Ringrazio, quindi, mia sorella Milena per il gran cuore e la disponibilità totale, i miei genitori e tutti gli amici che mi hanno sempre sostenuta moralmente nell’ultimo anno. Molti approfondimenti sono stati possibili grazie al confronto con referenti di diverse aziende, consulenti - system integrator e installatori specializzati; in particolare desidero citare la collaborazioni con Daniele Leonardi dello staff di Vividomotica™ (Easydom) e con Diego Marchente della AVD Consulting (Home innovation). Grazie anche al mio amico Fabrizio, che ha collaborato più volte, con acume e senso critico, a conversazioni amene, ma fondamentalmente preziose nella comprensione dei temi tecnici per me più gravosi; infine un grazie speciale a Roberta, amica e paziente lettrice del mio lavoro. -
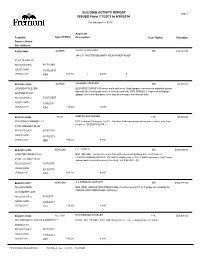
BUILDING ACTIVITY REPORT ISSUED from 7/1/2013 to 6/30/2014
BUILDING ACTIVITY REPORT page 1 ISSUED From 7/1/2013 to 6/30/2014 For Valuation >= $0.00 Applicant Permit #: Type of Work Description Case Status Valuation Owner's Name: Site Address: A-B9301844 ALTRES JERRY TERPENING ISS $16,163.00 244 S.F. MASTER BED/BATH ADDN W/NEW ROOF 41413 DENISE ST RECEIVED DATE: 8/17/1993 ISSUED DATE: 10/16/2013 CENSUS CAT: 434 # BLDG: 1 # UNIT: 0 BLD2008-04108 ALTRES LOLOHEA FOLELENI ISS $5,055.00 LOLOHEA FOLELENI BLDG/SITE SURVEY- Remove walls and revert illegal garage conversion to standard garage and add 262.5 sq ft patio cover in the rear yard (htl). SITE SURVEY-- Inspection to legalize 5667 MERIT WAY garage conversion and patio cover and all necessary conversions (htl). RECEIVED DATE: 12/27/2007 ISSUED DATE: 1/30/2014 CENSUS CAT: 434 # BLDG: # UNIT: BLD2010-06646 PLUM DEEPAK BHATRAGER FNL $5,000.00 IRVINGTON COMMON LLC BLD -Irvington Commons, Lot 13 - Building, Underground plumbing and electrical only (byc); for p/s see BLD2007-02700. je 41786 FREMONT BLVD RECEIVED DATE: 6/18/2010 ISSUED DATE: 9/11/2013 CENSUS CAT: 999 # BLDG: # UNIT: BLD2011-02976 NEWCOM LEE HARRIS ISS $570,400.00 LH ENTERPRISES II LLC BLD - MAJOR - Construct a new 6,830 sq ft commercial building (htl). For Prelim ref PLN2010-00046/BLD2010-01136 (4007 Irvington Ave.) 7/25/13 Add temp power. (rgs) Scope 41093 FREMONT BLVD Added- add 4 new bathrooms to the shell - val $ 24,000/-. (tj) RECEIVED DATE: 12/7/2010 ISSUED DATE: 6/12/2014 CENSUS CAT: 324 # BLDG: # UNIT: BLD2011-05311 NEWCOM A & E EMAAR COMPANY ISS $825,891.00 DHILLON RENU BLD (DES) GENIUS KIDS PRESCHOOL Construct new 4917 sq ft single story building for GENIUS KIDS PRESCHOOL (htl/byc/je). -

Multimedia Traffic Modeling and Bandwidth Allocation in Home Networks
MULTIMEDIA TRAFFIC MODELING AND BANDWIDTH ALLOCATION IN HOME NETWORKS By MINKYU LEE A DISSERTATION PRESENTED TO THE GRADUATE SCHOOL OF THE UNIVERSITY OF FLORIDA IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF DOCTOR OF PHILOSOPHY UNIVERSITY OF FLORIDA 2004 Copyright 2004 by Minkyu Lee To my parents and to Bokyung ACKNOWLEDGMENTS I would like to express my gratitude to all those who gave me the opportunity to work on this thesis. I am deeply indebted to my supervisor Dr. Haniph A. Latchman for his stimulating suggestions and encouragement. He treated me like family, and helped me throughout the researching and writing of this thesis. I also want to thank my cochair Dr. Newman and my committee members Dr. Arroyo, Dr. McNair, and Dr. Crisalle, who guided me in many ways. My wonderful colleagues from The Laboratory for Information Systems & Telecommu- nications (LIST) supported me in my research work as brothers and sisters. I want to thank them for all their help, support, interest and valuable hints. I especially thank Mr. Suman Srinivasan, Mr. Dave Tingling, Mr. Saleh Al-Shamali, Mr. Kartikeya Tidpathi, Mr. Baowei Ji, Mr. Yu-Ju Lin, and whose encouragement and friendship was invaluable to me. I wish to thank my parents and brother in Korea for their heartfelt love and support. Finally, I would like to express my deepest gratitude to my wife Bokyung, my daughter Eungie, and son Yehwan for their patience, consideration, and encouragement while I worked on this dissertation. IV TABLE OF CONTENTS Page ACKNOWLEDGMENTS iv LIST OF -

Construction of a Gsm Based Home Automation Using
CONSTRUCTION OF A GSM BASED HOME AUTOMATION USING AVR BY OKORAFOR CHINED HENRY EE/2008/281 DEPARTMENT OF ELECTRICAL AND ELECTRONIC ENGINEERING FACULTY OF ENGINEERING CARITAS UNIVERSITY AMORJI-NIKE, ENUGU. AUGUST, 2013. P a g e | i TITLTE PAGE A GSM BASED HOME AUTOMATION USING AVR BY OKORAFOR CHINEDU HENRY EE/2008/281 BEING A PROJECT SUBMITTED TO THE DEPARTMENT OF ELECTRICAL AND ELECTRONIC ENGINEERING FACULTY OF ENGINEERING CARITAS UNIVERSITY AMORJI-NIKE, ENUGU IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE BACHELOR OF ENGINEERING (B.ENG) IN ELECTRICAL AND ELECTRONIC ENGINEERING AUGUST, 2013. P a g e | ii CERTIFICATION This is to certify that this project research work from the department of Electrical/Electronic Engineering, Caritas University, Amorji-Nike, Emene, Enugu was solely carried out by OKORAFOR CHINEDU HENRY with Registration Number EE/2008/281 _________________________ ______________________ Engr. E. C. Aneke Date (Supervisor) _________________________ _______________________ Engr. C. O. Ejimofor Date (Head of Department) _________________________ ______________________ Date (EXTERNAL EXAMINER) P a g e | iii DEDICATION This report is dedicated to God Almighty who is the ultimate giver of wisdom and to my beloved parents for their financial support and encouragement throughout my stay in school. P a g e | iv ACKNOWLEDGEMENT I wish to express my profound thanks and appreciation to God for his unending mercy, blessing and protection throughout this period. A tree cannot make forests, without some special people this project may not work well for us. This is why I’m pleased to acknowledge the following people; My head of department, Engr. C. O. Ejimofor, My project supervisor, Engr.