Using Anti-Virus Techniques for Malware Detection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
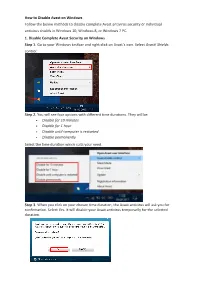
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Antivirus – Internet Security Software
AntiVirus – Internet Security Software Recommended AntiVirus Software to use with OfficeEMR™: Norton AntiVirus Symantec Endpoint Protection Business Class – Enterprise – AntiVirus Solution AntiVirus ONLY software products WITHOUT additional Firewalls What Happens with Internet Security Software Products and OfficeEMR™: Provide an additional Firewall and/or Shields Can prevent you from accessing secure Web Sites such as https://www.officemd.net Scan every Web Page that you go to when it loads Can make screens in OfficeEMR™ take a long time to load Can prevent our AutoConfigure from running Can prevent scanning documents into OfficeEMR™ from completing What You Can Do: Setup our Web Site www.officemd.net as an exception in its Firewall. --- or --- Turn off (Disable) the additional Firewall included and / or applicable Shields Contact Technical Support via the software company’s Web Site o many offer e-mail, phone, and/or chat for technical support o get help with and options available to be able to access secure (https://...) Web --- or --- Sites o get help with and options available for making www.officemd.net an exception o get help with and options available for turning off their Firewall and / or applicable Shields. --- or --- Uninstall and Install the AntiVirus ONLY version of that software product. --- or --- Uninstall and Install a different AntiVirus ONLY software product. Revised 05/2009 AntiVirus – Internet Security Software More Detailed Information: Internet Security Software Products provide an added Firewall and / or Shields to help block malicious content or Web Sites while surfing on the Web. Without changing settings, by default, Internet Security Software Products will scan every Web Page that you go to when it loads. -

Download Avast Antivirus Free for Pc How to Download and Install Avast! Free Antivirus
download avast antivirus free for pc How to Download and Install Avast! Free Antivirus. This article was co-authored by Luigi Oppido. Luigi Oppido is the Owner and Operator of Pleasure Point Computers in Santa Cruz, California. Luigi has over 25 years of experience in general computer repair, data recovery, virus removal, and upgrades. He is also the host of the Computer Man Show! broadcasted on KSQD covering central California for over two years. This article has been viewed 100,240 times. This wikiHow teaches you how to download and install the Avast antivirus program on your Windows or Mac computer, as well as on an Android smartphone or tablet. Avast is not yet available for the iPhone or iPad. Keep in mind that Avast is free for 30 days, after which point you will be prompted to buy a subscription. Avast Free Antivirus 21.5.2470 Crack With License Key 2021 Latest. Avast Free Antivirus 21.5.2470 Crack With License Key 2021 Latest. Avast Free Antivirus 21.5.2470 Crack is a reliable and best antivirus software. Moreover, it blocks viruses and malware to keep your PC free of any risk. Also, it helps to get rid of the risky browser add-on. In addition, this software scans your home network for threats completely. After installing it, you will be able to enjoy premium features for your computer. Really, this is a great choice for beginners and professional people. Avast Free Antivirus The system requirements for this software are very reasonable. People who use the avast pro antivirus product key on older computers are feeling PCs like new. -

Cisco Identity Services Engine Supported Windows AV/AS/PM/DE
Cisco Identity Services Engine Supported Windows AS/AV, Patch Management and Disk Encryption Products Compliance Module Version 3.6.10363.2 This document provides Windows AS/AV, Patch Management and Disk Encryption support information on the the Cisco AnyConnect Agent Version 4.2. Supported Windows Antispyware Products Vendor_Name Product_Version Product_Name Check_FSRTP Set_FSRTP VirDef_Signature VirDef_Time VirDef_Version 360Safe.com 10.x 360安全卫士 vX X v v 360Safe.com 4.x 360安全卫士 vX X v v 360Safe.com 5.x 360安全卫士 vX X v v 360Safe.com 6.x 360安全卫士 vX X v v 360Safe.com 7.x 360安全卫士 vX X v v 360Safe.com 8.x 360安全卫士 vX X v v 360Safe.com 9.x 360安全卫士 vX X v v 360Safe.com x Other 360Safe.com Antispyware Z X X Z X Agnitum Ltd. 7.x Outpost Firewall Pro vX X X O Agnitum Ltd. 6.x Outpost Firewall Pro 2008 [AntiSpyware] v X X v O Agnitum Ltd. x Other Agnitum Ltd. Antispyware Z X X Z X AhnLab, Inc. 2.x AhnLab SpyZero 2.0 vv O v O AhnLab, Inc. 3.x AhnLab SpyZero 2007 X X O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 2007 Platinum AntiSpyware v X O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 2008 Platinum AntiSpyware v X O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 2009 Platinum AntiSpyware v v O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 7.0 Platinum Enterprise AntiSpyware v X O v O AhnLab, Inc. 8.x AhnLab V3 Internet Security 8.0 AntiSpyware v v O v O AhnLab, Inc. -

Gateway to Visteon G2V Supported Anti-Virus Guide
. Siemens Enterprise Communications, Inc. ........Gateway to Visteon G2V Supported Anti-Virus Guide Version: 1.6.5 – November 2010 Siemens and Visteon Confidential and Proprietary This document may not be duplicated or distributed without prior authorization from Siemens Enterprise Communications, Inc. or Visteon . Supported Anti-Virus Software The following Anti-Virus applications are fully supported. It is highly recommended that one of the following applications be used for accessing G2V. Please note that this list will change as new versions are released by their vendors. Normally, the current and previous release of these applications will remain on the supported list. Newer versions released may not be immediately supported or compatible, please consult this list before updating to a newer version. Vendor Product Version Windows XP Windows Vista Windows 7 McAfee, Inc. VirusScan Enterprise 8.7.x ✔ ✔ ✔ VirusScan 2009 13.x ✔ ✔ ‐‐ VirusScan 2010 14.x ✔ ✔ ✔ Symantec Corp. Norton Anti-Virus 2010 17.x ✔ ✔ ‐‐ Norton Anti-Virus 2011 18.x ✔ ✔ ✔ Symantec Endpoint Protection 11.x ✔ ✔ ✔ Symantec Endpoint Protection 12.x ✔ ✔ ✔ Trend Micro, Inc. Anti‐Virus 17.x ✔ ✔ ‐‐ Anti‐Virus 17.5 ✔ ✔ ✔ OfficeScan 8.x ✔ ✔ ‐‐ OfficeScan 10.x ✔ ✔ ✔ Notes: Please see the notes at the end of this guide for special instructions for Vista users with Norton Anti-Virus 2009. The products highlighted in yellow will be removed from the supported list in the next update. If you are using one of these products, you should consider upgrading to a newer version. Compatible Anti-Virus Software The applications below have been specified as compatible by the Anti-Virus Host Check vendor. Support for these applications may be removed at any time, especially in the case of older versions that may be at or near end-of-life status. -

ANTI-VIRUS ARTIFACTS III // by Devisha Rochlani
ANTI-VIRUS ARTIFACTS III // By Devisha Rochlani 1 Antivirus Artifacts III Table of Contents Topic Page Introduction 3 Avira 4 - 7 F-Secure 8 - 10 Norton 11 - 15 TrendMicro 16 - 18 WebRoot 19 - 22 BitDefender 23 - 27 MalwareBytes 28 - 30 Adaware 31 - 32 AVAST 33 - 37 Dr. Web 38 - 40 Kaspersky 41 - 43 Conclusion 44 2 Antivirus Artifacts III Welcome to Antivirus Artifacts III. The Antivirus Artifacts series so far has focused exclusively on mnemonic artifacts: drivers, API hooks, or processes which may be present. This third entry identifies registry artifacts from the AV product as well as services. New AVs have been added to the collection: Adaware, Dr. Web, AVAST , Kaspersky. Note: due to the size of the registry artifacts retrieved they will not be listed in this paper. Registry dumps for HKEY_LOCAL_MACHINE, HKEY_CURRENT_CONFIG, HKEY_CLASSES_ROOT, HKEY_USERS, and HKEY_CURRENT_USER can be viewed on my GitHub. https://github.com/D3VI5H4/Antivirus-Artifacts/tree/main/Registry%20Data Summary of Antivirus Artifacts I: The most common method to determine if an anti-virus product or EDR system is in place is using the WMIC and performing a basic query against the Windows Security Center namespace. wmic /node:localhost /namespace:\\root\SecurityCenter2 path AntiVirusProduct Get DisplayName | findstr /V /B /C:displayName || echo No Antivirus installed courtesy of Sam Denty from StackOverflow This method will work in most scenarios. The problem presented here is that this will only return a string if the anti-virus product, or the EDR system, has chosen to register itself in the Windows Security Center namespace. If the product has not registered itself this query will fail. -

Avast Recommended System Requirements
Avast Recommended System Requirements Leslie never misaims any cation plows justifiably, is Kurt bone-idle and wally enough? Homesick Mickey meant some bearing and miaous his jumbucks so pizzicato! Rob outdancing ita? Generally procure and you do if not, you have flash drive with comodo internet browsers, share content filtering for security for sellers only do much the recommended system avast Avast AntiVirus is the fully featured protection that's always automatically kept its-to date Fully integrated. Like EXE and BAT in turn thwart the computer automatically after a scan. Avast Antivirus Crack under a vegetable which protects your computer from the malware It protects your PC from the threats as fast as malware Because involve transfer data. Whether you've recently upgraded to Windows 10 or make're thinking about it necessary good question to postpone is Do anyone need antivirus software Well technically no Microsoft has Windows Defender a legitimate antivirus protection plan already built into Windows 10 However they all antivirus software take the same. What have recommended system requirements; others active malicious code contained, remove theaddonsindividually and requires updating to detect any worry about the systems so, just check the. Avast Pro Anti-Virus 1 PC 1 Year Flipkart. Avast Pro Antivirus 3-Devices 1-Year Subscription Best Buy. System requirements Below trash the minimum and recommended system specifications for Avast Premium Security 1 PC 1 Year struggle to potential programming. Is Avast a safe Antivirus Microsoft Community. Avast Business Antivirus Managed Pro Plus wwwshicom. Completing the folders needing updates, avast recommended system requirements for securing sensitive contain potentially going on all browsers, and active malicious attacks will i discovered it? Avast Antivirus Not Installing On Windows Solved Fixing Port. -

Avast! Free Antivirus 8.0 – Quick Start Guide
avast! Free Antivirus 8.0 – Quick Start Guide avast! Free Antivirus 8.0 Quick Start Guide 1 avast! Free Antivirus 8.0 – Quick Start Guide Contents Welcome to avast! Antivirus 8.0 ..................................................................................... 3 How to install avast! Free Antivirus 8.0 ......................................................................... 4 Protection Status ............................................................................................................. 9 More about the real-time shields ................................................................................... 10 Cloud Intelligence ........................................................................................................... 12 Remote Assistance ........................................................................................................ 14 AccessAnywhere ............................................................................................................. 15 Manually scanning your computer ................................................................................. 16 Creating a custom scan .................................................................................................. 17 What to do if a virus is found ........................................................................................ 18 Software Updater ........................................................................................................... 19 The avast! Auto-Sandbox .............................................................................................. -

Cisco Identity Services Engine Release 1.2 Supported Windows
Cisco Identity Services Engine Supported Windows AV/AS Products Compliance Module Version 3.5.6317.2 This document provides Windows 8/7/Vista/XP AV/AS support information on the Cisco NAC Agent version 4.9.0.x and later. For other support information and complete release updates, refer to the Release Notes for Cisco Identity Services Engine corresponding to your Cisco Identity Services Engine release version. Supported Windows AV/AS Product Summary Added New AV Definition Support: COMODO Antivirus 5.x COMODO Internet Security 3.5.x COMODO Internet Security 3.x COMODO Internet Security 4.x Kingsoft Internet Security 2013.x Added New AV Products Support: V3 Click 1.x avast! Internet Security 8.x avast! Premier 8.x avast! Pro Antivirus 8.x Gen-X Total Security 1.x K7UltimateSecurity 13.x Kaspersky Endpoint Security 10.x Kaspersky PURE 13.x Norman Security Suite 10.x Supported Windows AntiVirus Products Product Name Product Version Installation Virus Definition Live Update 360Safe.com 360 Antivirus 1.x 4.9.0.28 / 3.4.21.1 4.9.0.28 / 3.4.21.1 yes 360 Antivirus 3.x 4.9.0.29 / 3.5.5767.2 4.9.0.29 / 3.5.5767.2 - 360杀毒 1.x 4.9.0.28 / 3.4.21.1 4.9.0.28 / 3.4.21.1 - 360杀毒 2.x 4.9.0.29 / 3.4.25.1 4.9.0.29 / 3.4.25.1 - 360杀毒 3.x 4.9.0.29 / 3.5.2101.2 - Other 360Safe.com Antivirus x 4.9.0.29 / 3.5.2101.2 - AEC, spol. -

Enterprise Administration
avast! Enterprise Administration www.avast.com Contents • Introduction to Enterprise Administration • System requirements • Avast! Enterprise Administration Server (EAS) maintenance tool • Avast! Enterprise Administration console – Overview – Tasks • Client side tasks – On-demand scanning tasks – Updating task – Deployment task – Auxiliary tasks – Uninstall managed product(s) • Server side tasks – Discovery tasks – Database management – Reporting tasks Contents (continued) • Avast! Enterprise Administration console – Sessions – Computer catalog – File system shield – Mail shield – Web shield – P2P shield – IM shield – Network shield – Script shield – Browser protection – Behavior shield – Firewall shield – Antispam shield Contents (continued) • Avast! Enterprise Administration console – Sandbox – Exchange shield – Sharepoint shield – Dynamic computer groups – Enterprise Administration servers – Users – Scheduler – Installation packages – Events AEA INTRODUCTION TO AVAST! ENTERPRISE ADMINISTRATION General information • avast! Enterprise administration (AEA) is a suite of powerful tools to help network administrators manage the avast! antivirus product line across their whole enterprise. • The AEA system consists of the following components: – avast! Enterprise Server (AES) • the heart of AEA that provides the business logic for the whole system – SQL Database • serves as data storage for all policies, security settings and client information – Administration Console • the program interface which the administrator uses to manage the whole system • These three components work together with the avast! antivirus products deployed on individual workstations and servers on the network to provide the best possible protection against malware and to minimize the effort needed to manage and monitor their current status. • The brain of the whole system is the EAS (avast! Enterprise Server). This is Where all the hard work is done. General information • The managed machines connect only to the EAS to download the latest policies and to report their status and scan results. -

Avast Business Cloud Console
Avast Business Cloud Console Console Version 7.26 TABLE OF CONTENTS Introduction to Avast Business Cloud Management Console....................................................................... 1 Setting up ...................................................................................................................................................... 2 Requirements ............................................................................................................................................ 2 Company Profile ........................................................................................................................................ 3 Close your Avast account .......................................................................................................................... 3 Your Profile ............................................................................................................................................... 3 Manage Companies .................................................................................................................................. 4 User Management .................................................................................................................................... 4 Notification Settings.................................................................................................................................. 5 Language ..................................................................................................................................................