Avast! Antivirus Home Edition 4.8 – User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A the Hacker
A The Hacker Madame Curie once said “En science, nous devons nous int´eresser aux choses, non aux personnes [In science, we should be interested in things, not in people].” Things, however, have since changed, and today we have to be interested not just in the facts of computer security and crime, but in the people who perpetrate these acts. Hence this discussion of hackers. Over the centuries, the term “hacker” has referred to various activities. We are familiar with usages such as “a carpenter hacking wood with an ax” and “a butcher hacking meat with a cleaver,” but it seems that the modern, computer-related form of this term originated in the many pranks and practi- cal jokes perpetrated by students at MIT in the 1960s. As an example of the many meanings assigned to this term, see [Schneier 04] which, among much other information, explains why Galileo was a hacker but Aristotle wasn’t. A hack is a person lacking talent or ability, as in a “hack writer.” Hack as a verb is used in contexts such as “hack the media,” “hack your brain,” and “hack your reputation.” Recently, it has also come to mean either a kludge, or the opposite of a kludge, as in a clever or elegant solution to a difficult problem. A hack also means a simple but often inelegant solution or technique. The following tentative definitions are quoted from the jargon file ([jargon 04], edited by Eric S. Raymond): 1. A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary. -

Undergraduate Report
UNDERGRADUATE REPORT Attack Evolution: Identifying Attack Evolution Characteristics to Predict Future Attacks by MaryTheresa Monahan-Pendergast Advisor: UG 2006-6 IINSTITUTE FOR SYSTEMSR RESEARCH ISR develops, applies and teaches advanced methodologies of design and analysis to solve complex, hierarchical, heterogeneous and dynamic problems of engineering technology and systems for industry and government. ISR is a permanent institute of the University of Maryland, within the Glenn L. Martin Institute of Technol- ogy/A. James Clark School of Engineering. It is a National Science Foundation Engineering Research Center. Web site http://www.isr.umd.edu Attack Evolution 1 Attack Evolution: Identifying Attack Evolution Characteristics To Predict Future Attacks MaryTheresa Monahan-Pendergast Dr. Michel Cukier Dr. Linda C. Schmidt Dr. Paige Smith Institute of Systems Research University of Maryland Attack Evolution 2 ABSTRACT Several approaches can be considered to predict the evolution of computer security attacks, such as statistical approaches and “Red Teams.” This research proposes a third and completely novel approach for predicting the evolution of an attack threat. Our goal is to move from the destructive nature and malicious intent associated with an attack to the root of what an attack creation is: having successfully solved a complex problem. By approaching attacks from the perspective of the creator, we will chart the way in which attacks are developed over time and attempt to extract evolutionary patterns. These patterns will eventually -

Parker Review
Ethnic Diversity Enriching Business Leadership An update report from The Parker Review Sir John Parker The Parker Review Committee 5 February 2020 Principal Sponsor Members of the Steering Committee Chair: Sir John Parker GBE, FREng Co-Chair: David Tyler Contents Members: Dr Doyin Atewologun Sanjay Bhandari Helen Mahy CBE Foreword by Sir John Parker 2 Sir Kenneth Olisa OBE Foreword by the Secretary of State 6 Trevor Phillips OBE Message from EY 8 Tom Shropshire Vision and Mission Statement 10 Yvonne Thompson CBE Professor Susan Vinnicombe CBE Current Profile of FTSE 350 Boards 14 Matthew Percival FRC/Cranfield Research on Ethnic Diversity Reporting 36 Arun Batra OBE Parker Review Recommendations 58 Bilal Raja Kirstie Wright Company Success Stories 62 Closing Word from Sir Jon Thompson 65 Observers Biographies 66 Sanu de Lima, Itiola Durojaiye, Katie Leinweber Appendix — The Directors’ Resource Toolkit 72 Department for Business, Energy & Industrial Strategy Thanks to our contributors during the year and to this report Oliver Cover Alex Diggins Neil Golborne Orla Pettigrew Sonam Patel Zaheer Ahmad MBE Rachel Sadka Simon Feeke Key advisors and contributors to this report: Simon Manterfield Dr Manjari Prashar Dr Fatima Tresh Latika Shah ® At the heart of our success lies the performance 2. Recognising the changes and growing talent of our many great companies, many of them listed pool of ethnically diverse candidates in our in the FTSE 100 and FTSE 250. There is no doubt home and overseas markets which will influence that one reason we have been able to punch recruitment patterns for years to come above our weight as a medium-sized country is the talent and inventiveness of our business leaders Whilst we have made great strides in bringing and our skilled people. -

CONTENTS in THIS ISSUE Fighting Malware and Spam
MARCH 2008 Fighting malware and spam CONTENTS IN THIS ISSUE 2 COMMENT EVASIVE ACTION Home (page) renovations Pandex has attracted very little attention from the media and generated little 3 NEWS discussion between malware Botherders herded researchers and among the 29A folds general populace. Chandra Prakash and Adam Thomas provide an overview of the Pandex operation and take an in-depth look at VIRUS PREVALENCE TABLE 3 the underlying code that has allowed this malware to evade detection for so long. 4 MALWARE ANALYSIS page 4 Pandex: the botnet that could PACKING A PUNCH In the fi nal part of the series on exepacker 9 FEATURE blacklisting, Robert Neumann takes a look at how all the processing and analysis techniques are put Exepacker blacklisting part 3 into practice in a real-life situation. page 9 15 CONFERENCE REPORT AVG TURNS 8 Black Hat DC and CCC 24C3 John Hawes gets his hands on a preview version of the latest offering from AVG. 18 PRODUCT REVIEW page 18 AVG Internet Security 8 22 END NOTES & NEWS This month: anti-spam news and events, and Ken Simpson considers the implications of rising spam volume despite increasing accuracy of content fi lters. ISSN 1749-7027 COMMENT ‘It is hoped that within all sizes of business. It is hoped that the comment facility will promote discussion among visitors and that the comment facility in some cases the more knowledgeable of VB’s readers will promote will be able to guide and assist those less well versed in discussion among the complexities of anti-malware technologies. -
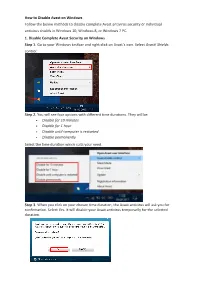
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

GTC-ONE-Minute-Brief-117.Pdf
Equity | Currencies & Commodities | Corporate & Global Economic News | Economic Calendar 16 September 2020 Economic and political news Key indices The National Economic Development and Labour Council (Nedlac) As at 15 1 Day 1 D % WTD % MTD % Prev. month YTD % chaired by President Cyril Ramaphosa has agreed to an economic recovery plan for South Africa (SA) and a social compact to mobilise Sept 2020 Chg Chg Chg Chg % Chg Chg JSE All Share 56130.78 -196.27 -0.35 0.08 1.18 -0.44 -1.67 funding to address Eskom's financial crisis. (ZAR) The Matjhabeng Municipality in Free State has agreed to hand over 139 JSE Top 40 (ZAR) 51795.70 -181.12 -0.35 0.16 1.11 -0.28 1.93 farms worth about ZAR2.5bn belonging to the administrative region as FTSE 100 (GBP) 6105.54 79.29 1.32 1.22 2.38 1.12 -19.05 security on the ZAR3.4bn debt it owes to Eskom. DAX 30 (EUR) 13217.67 24.01 0.18 0.11 2.10 5.13 -0.24 According to the Automobile Association (AA), petrol price in SA will CAC 40 (EUR) 5067.93 16.05 0.32 0.67 2.44 3.42 -15.22 drop by between 26 cents and 36 cents per litre and diesel by 88 cents S&P 500 (USD) 3401.20 17.66 0.52 1.80 -2.83 7.01 5.27 per litre in October. Nasdaq 11190.32 133.67 1.21 3.10 -4.97 9.59 24.72 Democratic Alliance (DA) leader John Steenhuisen has requested Composite (USD) President Cyril Ramaphosa to end the curfew imposed in a bid to curb DJIA (USD) 27995.60 2.27 0.01 1.19 -1.53 7.57 -1.90 MSCI Emerging the spread of COVID-19, open all sectors of the South African economy, 1112.62 8.35 0.76 1.91 1.01 2.09 -0.18 and allow for international travel and reintroduce a normal school week. -

Antivirus – Internet Security Software
AntiVirus – Internet Security Software Recommended AntiVirus Software to use with OfficeEMR™: Norton AntiVirus Symantec Endpoint Protection Business Class – Enterprise – AntiVirus Solution AntiVirus ONLY software products WITHOUT additional Firewalls What Happens with Internet Security Software Products and OfficeEMR™: Provide an additional Firewall and/or Shields Can prevent you from accessing secure Web Sites such as https://www.officemd.net Scan every Web Page that you go to when it loads Can make screens in OfficeEMR™ take a long time to load Can prevent our AutoConfigure from running Can prevent scanning documents into OfficeEMR™ from completing What You Can Do: Setup our Web Site www.officemd.net as an exception in its Firewall. --- or --- Turn off (Disable) the additional Firewall included and / or applicable Shields Contact Technical Support via the software company’s Web Site o many offer e-mail, phone, and/or chat for technical support o get help with and options available to be able to access secure (https://...) Web --- or --- Sites o get help with and options available for making www.officemd.net an exception o get help with and options available for turning off their Firewall and / or applicable Shields. --- or --- Uninstall and Install the AntiVirus ONLY version of that software product. --- or --- Uninstall and Install a different AntiVirus ONLY software product. Revised 05/2009 AntiVirus – Internet Security Software More Detailed Information: Internet Security Software Products provide an added Firewall and / or Shields to help block malicious content or Web Sites while surfing on the Web. Without changing settings, by default, Internet Security Software Products will scan every Web Page that you go to when it loads. -

Annex 1: Parker Review Survey Results As at 2 November 2020
Annex 1: Parker Review survey results as at 2 November 2020 The data included in this table is a representation of the survey results as at 2 November 2020, which were self-declared by the FTSE 100 companies. As at March 2021, a further seven FTSE 100 companies have appointed directors from a minority ethnic group, effective in the early months of this year. These companies have been identified through an * in the table below. 3 3 4 4 2 2 Company Company 1 1 (source: BoardEx) Met Not Met Did Not Submit Data Respond Not Did Met Not Met Did Not Submit Data Respond Not Did 1 Admiral Group PLC a 27 Hargreaves Lansdown PLC a 2 Anglo American PLC a 28 Hikma Pharmaceuticals PLC a 3 Antofagasta PLC a 29 HSBC Holdings PLC a InterContinental Hotels 30 a 4 AstraZeneca PLC a Group PLC 5 Avast PLC a 31 Intermediate Capital Group PLC a 6 Aveva PLC a 32 Intertek Group PLC a 7 B&M European Value Retail S.A. a 33 J Sainsbury PLC a 8 Barclays PLC a 34 Johnson Matthey PLC a 9 Barratt Developments PLC a 35 Kingfisher PLC a 10 Berkeley Group Holdings PLC a 36 Legal & General Group PLC a 11 BHP Group PLC a 37 Lloyds Banking Group PLC a 12 BP PLC a 38 Melrose Industries PLC a 13 British American Tobacco PLC a 39 Mondi PLC a 14 British Land Company PLC a 40 National Grid PLC a 15 BT Group PLC a 41 NatWest Group PLC a 16 Bunzl PLC a 42 Ocado Group PLC a 17 Burberry Group PLC a 43 Pearson PLC a 18 Coca-Cola HBC AG a 44 Pennon Group PLC a 19 Compass Group PLC a 45 Phoenix Group Holdings PLC a 20 Diageo PLC a 46 Polymetal International PLC a 21 Experian PLC a 47 -

Constituents & Weights
2 FTSE Russell Publications 19 August 2021 FTSE 100 Indicative Index Weight Data as at Closing on 30 June 2021 Index weight Index weight Index weight Constituent Country Constituent Country Constituent Country (%) (%) (%) 3i Group 0.59 UNITED GlaxoSmithKline 3.7 UNITED RELX 1.88 UNITED KINGDOM KINGDOM KINGDOM Admiral Group 0.35 UNITED Glencore 1.97 UNITED Rentokil Initial 0.49 UNITED KINGDOM KINGDOM KINGDOM Anglo American 1.86 UNITED Halma 0.54 UNITED Rightmove 0.29 UNITED KINGDOM KINGDOM KINGDOM Antofagasta 0.26 UNITED Hargreaves Lansdown 0.32 UNITED Rio Tinto 3.41 UNITED KINGDOM KINGDOM KINGDOM Ashtead Group 1.26 UNITED Hikma Pharmaceuticals 0.22 UNITED Rolls-Royce Holdings 0.39 UNITED KINGDOM KINGDOM KINGDOM Associated British Foods 0.41 UNITED HSBC Hldgs 4.5 UNITED Royal Dutch Shell A 3.13 UNITED KINGDOM KINGDOM KINGDOM AstraZeneca 6.02 UNITED Imperial Brands 0.77 UNITED Royal Dutch Shell B 2.74 UNITED KINGDOM KINGDOM KINGDOM Auto Trader Group 0.32 UNITED Informa 0.4 UNITED Royal Mail 0.28 UNITED KINGDOM KINGDOM KINGDOM Avast 0.14 UNITED InterContinental Hotels Group 0.46 UNITED Sage Group 0.39 UNITED KINGDOM KINGDOM KINGDOM Aveva Group 0.23 UNITED Intermediate Capital Group 0.31 UNITED Sainsbury (J) 0.24 UNITED KINGDOM KINGDOM KINGDOM Aviva 0.84 UNITED International Consolidated Airlines 0.34 UNITED Schroders 0.21 UNITED KINGDOM Group KINGDOM KINGDOM B&M European Value Retail 0.27 UNITED Intertek Group 0.47 UNITED Scottish Mortgage Inv Tst 1 UNITED KINGDOM KINGDOM KINGDOM BAE Systems 0.89 UNITED ITV 0.25 UNITED Segro 0.69 UNITED KINGDOM -

Computer Viruses, in Order to Detect Them
Behaviour-based Virus Analysis and Detection PhD Thesis Sulaiman Amro Al amro This thesis is submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy Software Technology Research Laboratory Faculty of Technology De Montfort University May 2013 DEDICATION To my beloved parents This thesis is dedicated to my Father who has been my supportive, motivated, inspired guide throughout my life, and who has spent every minute of his life teaching and guiding me and my brothers and sisters how to live and be successful. To my Mother for her support and endless love, daily prayers, and for her encouragement and everything she has sacrificed for us. To my Sisters and Brothers for their support, prayers and encouragements throughout my entire life. To my beloved Family, My Wife for her support and patience throughout my PhD, and my little boy Amro who has changed my life and relieves my tiredness and stress every single day. I | P a g e ABSTRACT Every day, the growing number of viruses causes major damage to computer systems, which many antivirus products have been developed to protect. Regrettably, existing antivirus products do not provide a full solution to the problems associated with viruses. One of the main reasons for this is that these products typically use signature-based detection, so that the rapid growth in the number of viruses means that many signatures have to be added to their signature databases each day. These signatures then have to be stored in the computer system, where they consume increasing memory space. Moreover, the large database will also affect the speed of searching for signatures, and, hence, affect the performance of the system. -

AVAST Free for Education Program
AVAST Free for Education Program What AVAST offers for free Free-of-charge security solutions for small, unmanaged networks or single installations for avast! Endpoint avast! Free avast! Free avast! Free Mobile Product name Windows, Mac, or Android OS, as well as managed avast! Endpoint Protection Suite for larger Protection Suite Antivirus Antivirus for Mac Security endpoint and server deployments. Managed a r r r Who is eligible Operation Systems Windows / Mac*) Windows Mac Android Any public or non-profit educational institution / education organization (this includes Network deployment Single installs or Single installs or Usage Single installs grades K-12 or higher, vocational / trade schools, head start programs or other entities with 5 - 30,000 devices SOHO network SOHO network educational purposes under 501(c) of the IRS Publication 557 - Organization Reference Chart section) or public library, operating in the United States (includes all 50 states, the District of System requirements Datasheet Datasheet Datasheet Datasheet Columbia, and the territories of American Samoa, Guam, Marianas, Puerto Rico, and the U.S. Virgin Islands). Learn more in The Eligibility and Participation Requirements. *) Mac OS X included in Q1 2013 How to apply for avast! Endpoint Protection Suite 1. Apply on www.avast.com/en-us/education via online Application Form 2. Specify number of computers and servers to be protected under the license 3. Receive the license to specified email Duration As long as there is ample interest, we intend to provide the AVAST Free for Education Program. Of course, AVAST reserves the right to discontinue the Program, with at least a one-year notice given to the Educational Institution, to provide sufficient time to execute any changes resulting from the Program‘s discontinuation.