How to Configure Anti-Virus to Permit Softminer Binaries
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton Antivirus™ 2009 Feature Comparison Chart
Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton AntiVirus™ 2009 Feature Comparison Chart Feature Norton 360 Norton Internet Norton Explanation Version 3.0 Security 2009 AntiVirus 2009 Core Protection Antivirus ✔ ✔ ✔ Detects and removes viruses, Internet worms, and Trojan horses Antispyware ✔ ✔ ✔ Prevents spyware from infecting the PC Email and instant messaging protection ✔ ✔ ✔ Monitors email and instant messaging so users can exchange files without exchanging threats Antispam ✔ ✔ Automatically filters out annoying and fraudulent or phishing email from the user’s email inbox Advanced Protection Botnet detection ✔ ✔ ✔ Detects and prevents others from taking control of the PC, accessing private information, or using the computer to host an attack Rootkit detection ✔ ✔ ✔ Finds and removes threats that are hidden deep in the operating system Norton™ Insight ✔ ✔ ✔ Includes innovative, intelligence-driven technology for faster, fewer, shorter scans Norton™ Pulse Updates ✔ ✔ ✔ Delivers rapid pulse updates every 5 to 15 minutes for protection against new threats Smart, two-way firewall ✔ ✔ Makes intelligent incoming and outgoing security decisions without interrupting users to ask them each time Enhanced browser protection ✔ ✔ ✔ Secures against Web-based attacks that use browser vulnerabilities to infect PCs with malware Real-time behavioral protection ✔ ✔ ✔ Provides enhanced, real-time protection (SONAR™) Wireless network security protection ✔ ✔ Checks the status of wireless network security and provides expert advice on managing -

Testing Anti-Virus in Linux: How Effective Are the Solutions Available for Desktop Computers?
Royal Holloway University of London ISG MSc Information Security thesis series 2021 Testing anti-virus in Linux: How effective are the solutions available for desktop computers? Authors Giuseppe Raffa, MSc (Royal Holloway, 2020) Daniele Sgandurra, Huawei, Munich Research Center. (Formerly ISG, Royal Holloway.) Abstract Anti-virus (AV) programs are widely recognized as one of the most important defensive tools available for desktop computers. Regardless of this, several Linux users consider AVs unnec- essary, arguing that this operating system (OS) is “malware-free”. While Windows platforms are undoubtedly more affected by malicious software, there exist documented cases of Linux- specific malware. In addition, even though the estimated market share of Linux desktop sys- tems is currently only at 2%, it is certainly possible that it will increase in the near future. Considering all this, and the lack of up-to-date information about Linux-compatible AV solutions, we evaluated the effectiveness of some anti-virus products by using local installations, a well- known on-line malware scanning service (VirusTotal) and a renowned penetration testing tool (Metasploit). Interestingly, in our tests, the average detection rate of the locally-installed AV programs was always above 80%. However, when we extended our analysis to the wider set of anti-virus solutions available on VirusTotal, we found out that the average detection rate barely reached 60%. Finally, when evaluating malicious files created with Metasploit, we verified that the AVs’ heuristic detection mechanisms performed very poorly, with detection rates as low as 8.3%.a aThis article is published online by Computer Weekly as part of the 2021 Royal Holloway informa- tion security thesis series https://www.computerweekly.com/ehandbook/Royal-Holloway-Testing-antivirus- efficacy-in-Linux. -

Webroot Secureanywhere User Guide Complete Edition
User Guide for the Complete Edition Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Version 8.0.1 Webroot SecureAnywhere User Guide for the Complete Edition Version 8.0.1; May, 2012 © 2011- 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is a trademark of Webroot Software, Inc. All other product and company names mentioned may be trademarks or registered trademarks of their respective owners. Contents 1: Getting Started . .1 Installing the software. .2 Using the main interface. .5 Using the system tray menu. .6 Viewing the protection status . .7 Creating a Webroot account. .8 Adding PCs to your account . .9 Adding mobile devices to your account . .10 Viewing the PC security status online . .11 2: Scans . .15 About scans . .16 Running an immediate scan. .17 Running a custom scan . .19 Changing the scan schedule . .21 Changing scan settings . .23 3: Shields . .25 About shields . .26 Changing Realtime shield settings . .27 Changing Behavior shield settings . .29 Changing Core System shield settings . .31 Changing Web Threat shield settings . .33 4: Firewall. .35 About the firewall . .36 Changing firewall alert settings . .37 Managing network applications . .38 5: Quarantine . .41 About quarantine . .42 Managing quarantined items . .43 Managing file detection . .45 Using antimalware tools . .47 Saving a threat log . .49 6: Identity Protection. .51 About the Identity shield. .52 Changing Identity shield settings . .53 Managing protected applications . .55 Managing protected websites. .57 7: Password Management . .61 About Password Management . .62 Downloading the Passwords component . .63 Capturing login credentials in a website. -

Mcafee Epolicy Orchestrator DATA SHEET
DATA SHEET McAfee ePolicy Orchestrator Centrally get, visualize, share, and act on security insights Security management requires cumbersome juggling between tools and data. This puts the adversary at an advantage by offering more time to exploit the gap not seen between the tools and do damage. In addition, the cybersecurity workforce is limited and needs to be empowered to manage cybersecurity complexity. The McAfee® ePolicy Orchestrator® (McAfee ePO™) management platform removes the time-consuming and potential human error effort and inspires those responsible to manage security quicker and with higher efficacy. Fundamental Security Proven Advanced Security Management Start with the fundamentals. Core to any security More than 30,000 businesses and organizations trust architecture is the ability to monitor and control the the McAfee ePO console to manage security, streamline health of endpoints and systems. Industry standards and automate compliance processes, and increase such as Center for Internet Security (CIS) Controls and overall visibility across endpoint, network, and security National Institute of Standards Technology (NIST) SP operations. Big companies rely on the McAfee ePO 800 153 security and privacy controls call this out as console’s highly scalable architecture, allowing large a must. The McAfee ePO console allows you to gain enterprises to manage hundreds and thousands of critical visibility and set and automatically enforce nodes from a single console. The McAfee ePO console policies to ensure a healthy security posture across provides an enterprise security administrator with the your enterprise. Policy management and enforcement opportunity to simplify policy maintenance, pull in third- across security products for your entire enterprise party threat intelligence leveraging Data Exchange Layer is accomplished from a single console, removing the (DXL), and integrate policies bi-directionally with an array complexity of managing multiple products. -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -
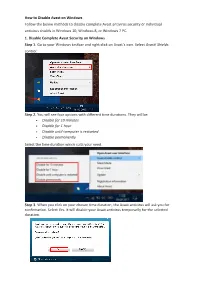
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Eset Endpoint Security
ESET ENDPOINT SECURITY User Guide Microsoft® Windows® 8 / 7 / Vista / XP / 2000 / Home Server Click here to download the most recent version of this document ESET ENDPOINT SECURITY Copyright ©2013 by ESET, spol. s r. o. ESET Endpoint Security was developed by ESET, spol. s r. o. For more information visit www.eset.com. All rights reserved. No part of this documentation may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise without permission in writing from the author. ESET, spol. s r. o. reserves the right to change any of the described application software without prior notice. Worldwide Customer Support: www.eset.com/support REV. 17. 4. 2013 Contents 4.2.1 Filt..e..r.i.n...g.. m....o..d..e..s............................................................44 1. ES.E..T. .E..n.d..p..o.i.n..t. .S.e..c.u..r.i.t.y.......................5 4.2.2 Fir.e..w...a..l.l. .p..r.o...f.i.l.e..s...........................................................45 4.2.3 Co.n..f..i.g..u..r.i.n...g.. a..n...d.. .u..s..i.n..g.. .r.u..l.e..s........................................46 1.1 Syste.m... .r.e..q.u..i.r.e..m...e.n..t.s..................................................5 4.2.3.1 Rules.. .s.e..t..u..p...................................................................47 1.2 Preve.n..t.i.o..n.................................................................5 4.2.3.2 Editin...g.. r..u..l.e..s.................................................................47 4.2.4 Co.n..f..i.g..u..r.i.n...g. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet -

Antivirus – Internet Security Software
AntiVirus – Internet Security Software Recommended AntiVirus Software to use with OfficeEMR™: Norton AntiVirus Symantec Endpoint Protection Business Class – Enterprise – AntiVirus Solution AntiVirus ONLY software products WITHOUT additional Firewalls What Happens with Internet Security Software Products and OfficeEMR™: Provide an additional Firewall and/or Shields Can prevent you from accessing secure Web Sites such as https://www.officemd.net Scan every Web Page that you go to when it loads Can make screens in OfficeEMR™ take a long time to load Can prevent our AutoConfigure from running Can prevent scanning documents into OfficeEMR™ from completing What You Can Do: Setup our Web Site www.officemd.net as an exception in its Firewall. --- or --- Turn off (Disable) the additional Firewall included and / or applicable Shields Contact Technical Support via the software company’s Web Site o many offer e-mail, phone, and/or chat for technical support o get help with and options available to be able to access secure (https://...) Web --- or --- Sites o get help with and options available for making www.officemd.net an exception o get help with and options available for turning off their Firewall and / or applicable Shields. --- or --- Uninstall and Install the AntiVirus ONLY version of that software product. --- or --- Uninstall and Install a different AntiVirus ONLY software product. Revised 05/2009 AntiVirus – Internet Security Software More Detailed Information: Internet Security Software Products provide an added Firewall and / or Shields to help block malicious content or Web Sites while surfing on the Web. Without changing settings, by default, Internet Security Software Products will scan every Web Page that you go to when it loads. -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10
Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10 January 2020 Document: Consumer Security Products Performance Benchmarks (Edition 2) Authors: J. Han, D. Wren Company: PassMark Software Date: 13 January 2020 Edition: 2 File: Consumer_Security_Products_Performance_Benchmarks_2020_Ed_2.docx Consumer Security Performance Benchmarks 2019 PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 REVISION HISTORY ............................................................................................................................................ 3 REFERENCES ...................................................................................................................................................... 3 EXECUTIVE SUMMARY ...................................................................................................................................... 4 OVERALL SCORE ................................................................................................................................................ 5 PRODUCTS AND VERSIONS ............................................................................................................................... 6 PERFORMANCE METRICS SUMMARY ................................................................................................................ 7 TEST RESULTS ................................................................................................................................................